* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Slide 1
Data vault modeling wikipedia , lookup
Clusterpoint wikipedia , lookup
Expense and cost recovery system (ECRS) wikipedia , lookup
Semantic Web wikipedia , lookup
Versant Object Database wikipedia , lookup
Relational model wikipedia , lookup
Business intelligence wikipedia , lookup
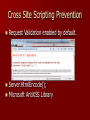
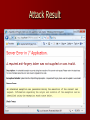
Building Secure Web Applications With ASP.Net MVC What is ASP.Net MVC? An extension to ASP.Net. Implements the MVC software pattern that divides an application's implementation into three component roles: – models – views – controllers. Models "Models" in a MVC based application are the components responsible for: – Maintaining state. – Often a database. Views "Views" in a MVC based application are the components responsible for: – Displaying the application's user interface. – Typically this UI is created off of the model data. Controllers Responsible for: – Handling user interaction – Manipulating the model – Choosing a view to render to display UI. In a MVC application the view is only about displaying information - it is the controller that handles and responds to user input and interaction. Part 1: Form Security Cross Site Scripting (XSS) Injection Flaws Cross Site Scripting (XSS) Common flaw in a web applications Allows attackers to execute script in the victims browser. Caused by improper input validation and encoding. Cross Site Scripting Prevention Request Validation enabled by default. Server.HtmlEncode(); Microsoft AntiXSS Library Injection Flaws Common in web applications. Caused when user input is evaluated as part of a command or query. SQL Injection most common. If _userName = “admin” and _password = “' OR 1 = 1 --” the result would be: SELECT * FROM tblUsers WHERE UserName = 'admin' and Password = '' OR 1 = 1 --' Injection Prevention MVC is built around a data Model Object Relational Mappers (ORM) – Linq to SQL – ADO.Net Entity Framework Handle CRUD commands in an Injection safe way. Part 2: Application Security Malicious File Execution Occurs when an attacker is able to upload and execute code on a server. The ASP.Net MVC Advantage – Classic ASP.Net served pages from their corresponding location on the disk. – ASP.Net MVC routes requests to the appropriate controller and view. – Attacker doesn’t know the applications directory structure. Insecure Direct Object Reference Occurs when an application exposes a direct reference to a resource. – Files – Primary keys for database records Attackers can edit these references to gain access to protected data. Prevention: – Encrypt any reference data when passing it between pages. Cross Site Request Forgery (CSRF) Tricks logged-on victim's browser to send a pre-authenticated request to a vulnerable web application. Can cause a user to perform an action they did not intend to do. Example: CSRF Prevention Avoid updating user data from HTTP Get requests. ASP.Net MVC AntiForgeryToken Attack Result Information Leakage and Improper Error Handling Improper error handling exposes implementation detail. Prevention: – Disable debugging. – Custom error pages. – ASP.Net MVC HandleError Attribute Failure to Restrict URL Access Web application only protects URL by not showing them to unauthorized users. URL can still be accesses manually. Prevention: – ASP.Net MVC [Authorize] Attribute Thank You Kevin Watt www.list2lend.com Chris Brousseau www.windows7ips.com