* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Hands on Demonstration for Testing Security in Web Applications
Survey
Document related concepts
Transcript
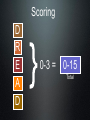
Hands on Demonstration for Testing Security in Web Applications Aaron Weaver August 2010 Agenda • What kind of application security vulnerabilities should be tested? • Methodology for testing • Open source tools available • Prioritizing application security defects In the news... the Solution? AND NO Not in the Cloud! Web Application Security Testing OWASP Top 10 list Top attacks • SQL Injection • Cross Site Scripting • Authentication ATTACK Custom Code App Server Firewall Hardened OS Firewall Network Layer Web Server DB Table Billing Human Resrcs Directories Web Services Legacy Systems Databases HTTP responseSQL query HTTP request APPLICATION "SELECT * FROM accounts WHERE SKU: acct=‘’ OR 1=1-Acct:5424-6066-2134-4334 Acct:4128-7574-3921-0192 ’" Account Summary Account: Communication Knowledge Mgmt E-Commerce Bus. Functions Administration Transactions Accounts Finance Application Layer SQL Injection Acct:5424-9383-2039-4029 Acct:4128-0004-1234-0293 1. Application presents a form to the attacker 2. Attacker sends an attack in the form data 3. Application forwards attack to the database in a SQL query 4. Database runs query containing attack and sends encrypted results back to application 5. Application decrypts data as normal and sends results to the user Cross-Site Scripting Attacker sets the trap – update my profile Victim views page – sees attacker profile Custom Code Script runs inside victim’s browser with full access to the DOM and cookies 3 Script silently sends attacker Victim’s session cookie Communication Knowledge Mgmt E-Commerce Bus. Functions 2 Administration Transactions Attacker enters a malicious script into a web page that stores the data on the server Application with stored XSS vulnerability Accounts Finance 1 Authentication Tools Overview • Proxies Tools • Burp Suite • Paros • WebScarab • Fiddler • FoxyProxy plugin • Open source scanners • Skipfish Burp Suite http://portswigger.net/proxy/ FoxyProxy Browser Plugin https://addons.mozilla.org/en-US/firefox/addon/2464/ Skipfish A fully automated, active web application security reconnaissance tool * Server-side SQL injection (including blind vectors, numerical parameters). * Stored and reflected XSS * Directory listing bypass vectors. * External untrusted embedded content. http://code.google.com/p/skipfish/ Cheat Sheet Quick Cheat Sheet Cheat Sheet AppSec Tools Demonstration Prioritizing Threat Risk D R E A D amage potential eproducibility xploitability ffected users iscoverability Scoring D R E A D 0-3 = 0-15 Total Severity Rating Low 1-7 Medium 8-10 High 11-14 Critical 15 Threat Risk Modeling • STRIDE (Microsoft) • OWASP Risk Ranking • Trike • CVSS Questions? Thanks!