* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Firewall and Proxy Server
Server Message Block wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Wireless security wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Remote Desktop Services wikipedia , lookup
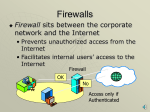
Firewall and Proxy Server Director: Dr. Mort Anvari Name: Anan Chen Date: Summer 2000 Content Firewall Proxy Server Relationship between Proxy Server and Firewall Types of Firewalls Hardware requirements Software requirements Conclusion Firewall 1 A computer firewall is a router or other communications device which filters access to a protected network. Firewall is also a program that screens all incoming traffic and protects the network from unwelcome intruders. Firewall 2 Firewalls can also be used as access control measures to only allow certain people within the organization access to the Internet. Many firewalls now contain features to control, authenticate and secure users who may want to access a company internal data from the Internet or even another company. Proxy Server 1 Proxy Server is a computer program that acts as an intermediary between a web browser and a web server. To give users rapid access to popular web destinations Proxy Server 2 Internet Service Providers use proxy servers as "holding bins" to store frequently requested pages, rather than going out and fetching them repeatedly from the Net Proxy server is also used to control and monitor outbound traffic Relationship between Proxy Server, Firewall Proxy Server is associated with firewall and also caching program The functions of proxy, firewall, and caching can be in separate server programs or combined in a single package. Proxy Server can be installed in the firewall to get a kind of proxy firewall Types of Firewalls Packet Filtering Firewalls Proxy Server Firewalls Packet Filtering Firewalls Packet Filtering is the type of firewall built into the Linux kernel A filtering firewall works at the network level. Data is only allowed to leave the system if the firewall rules allow it. As packets arrive they are filtered by their type, source address, destination address, and port information contained in each packet Many network routers have the ability to perform some firewall services. Filtering firewalls can be thought of as a type of router Proxy Server firewalls Application Proxy SOCKS Proxy Application Proxy As you telnet to the outside world the client send you to the proxy first. The proxy then connects to the server you requested (the outside world) and returns the data to you SOCKS Proxy SOCKS is networking proxy protocol that enables hosts on one side of a SOCKS server to gain full access to hosts on the other side of the SOCKS server without requiring direct IP reachability. SOCKS redirects connection requests from hosts on opposite sides of a SOCKS server. The SOCKS server authenticates and authorizes the requests, establishes a proxy connection, and relays data Hardware requirements Packet Filtering Firewalls Proxy Server Firewalls Hardware requirements-Packet Filtering Firewalls Filtering firewalls don't require fancy hardware. They are little more then simple routers a 486-DX66 with 32 meg of memory a 250m hard disk (500 recommended) network connections (LAN Cards, Serial Ports, Wireless?) monitor and keyboard Hardware requirements-Proxy Server firewalls If you need a proxy server firewall to handle lots of traffic, you should get the largest system you can afford a Pentium II with 64meg of memory a two gig hard disk to store all the logs two network connections monitor and keyboard Software requirements Packet Filtering Firewalls Proxy Server Firewalls Software requirements-Packet Filtering Firewalls To create a filtering firewall, you don't need any special software. Linux will do The built-in Linux firewall has changed several times, for the newer 2.4 kernel there is a new firewall utility with more features Software requirements-Proxy Server Firewalls If you want to setup a proxy server you will need one of these packages Squid The TIS (Trusted Information System) Firewall Toolkit (FWTK) SOCKS Squid Squid is a great package and works with Linux's Proxy feature TIS Trusted Information System's (TIS) is available at http://www.tis.com/research/software/ The TIS Internet Firewall Toolkit is a set of programs and configuration practices designed to facilitate the building of network firewalls. The toolkit software is designed to run on UNIX systems SOCKS The SOCKS proxy server available from http://www.socks.nec.com/ SOCKS can be installed both in NT system and UNIX system Conclusion Both firewall and proxy server are used for net work security and facility Proxy server can be a part of firewall