* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Network Environments - Advanced
Deep packet inspection wikipedia , lookup
Net neutrality law wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Distributed firewall wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Network tap wikipedia , lookup
Computer network wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
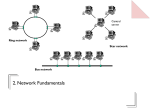
2.9 Network Environments In this section you must be able to: • Describe the characteristics and relative advantages of network and standalone environments • Describe the difference between a Local area and a Wide area network • Describe the elements of network environments Standalone Systems • Everyone has their own PC – processing and data are dispersed throughout the organisation • Lack of centralisation leads to problems: – No standardisation – e.g. shared templates – Data redundancy/integrity problems – multiple copies of data could be changed separately – Communication between departments is not possible What is a network? A network is two or more computers with a common electrical connection! Local Area Network Examples A network in one building or on one site Company, school or home networks Wide Area Network Examples A network covering a larger area than just one site ATM networks, lottery machines, the internet! Advantages and Disadvantages • Shared hardware, software and data – leading to savings? • Easier to install applications, etc. • Improved communications • Centralised management of users, backups, software, etc. • Dependency - server or cable failure affects everyone • Security issues – can be difficult to make secure • Performance - network slows down under load • Difficult to manage – may require a network manager Networking Terminology • A client-server network is one that has one or more file servers storing data and applications and print servers - this is the most common type for anything but very small networks • A peer-to-peer server has no server: – files and peripherals (e.g. printers) are shared between workstations on the network – all workstations may need to be switched on – suitable for small networks due to reduced cost • A gateway is used to link two different networks together, e.g. to connect a LAN to the internet • A bridge links together two similar networks Client-Server or Peer-to-Peer? • Choose client-server if: – you have a large network that can absorb the cost of the server – you want centralised management of users and resources – users are mobile and/or don’t always have their PCs turned on • Choose peer-to-peer if: – the network is small and you can’t justify the expense of a dedicated server – you have a workforce that generally uses the same PC and works the same hours so that all workstations are on at the same time Topologies The topology is how the computers are connected – there are 3 main ways: Bus Star Ring In a bus network, a single cable running the length of the network connects all of the nodes. Each node in a star network is connected to a central computer, usually the file server. In a ring network, the nodes are connected in a circle. In a token ring network, the information travels around the network in one direction only. A “token” travels around the network, like a train, carrying the information. Bus Networks • Any node can try to send a message at any time, but the bus can only carry one at a time The bus is free Nothin g coming ! 1 3 P Boom! 2 S • Before a node sends a message, it must check that the bus isn’t being used – it senses the data carrier • If the bus is not being used, the message can be sent – but two nodes could start at the same time, resulting in a collision of the two messages – the nodes need to detect when this happens and re-send the message • This protocol is called carrier sense multiple access with collision detection – or CSMA/CD Token Ring Network • So-called because a token passes around the ring to carry messages between the nodes • Nodes can only send when the token passes and is empty S 2 3 1 P • There will be no collisions, but a node may have to wait for the empty token to arrive, so may be slower than a bus network under light loads but will slow down less when it gets busier • Any breaks in the cable will affect all users Star Networks • All nodes are connected directly to the server by a dedicated server – this means there are no collisions 1 P S 2 3 • This means that if a cable is cut, only one of the nodes is affected • Messages might be send by the server polling each node in turn to see whether they have a message to send, and if they have, delivering it. • Logically, this is the same as a token ring! Cabling/Connection The type of cable used can also affect the speed at which data travels around the network. There are three main types of cabling used: Twisted pair – this is cable with two wires next to each other, like bell or speaker wire. Slower Co-axial cable – this has one cable in the form of a braid around the outside of the other, with a (usually plastic) spacer in between, like television aerial cable. The wire around the outside shields the inside one from interference, and allows higher transmission rates. Faster Fibre-optic – information is sent down a glass fibre in the form of light. This is obviously faster, as light travels at the speed of light! Light is also less prone to interference and can travel further without amplification. Glossary File server The main computer on the network (although big networks may have several servers) where the files are stored Print server The computer on the network that controls the printing – it will manage the queue where print jobs wait before they are printed Peer-to-peer A type of network that has no file server – files on the workstations can be shared with other users of the network – as long as the computer is on! Intranet Provides web-pages on a local area network, e.g. for company notices. Like a local version of the world-wide web Proxy server A computer that fetches web-pages from the internet and distributes them to the workstations on the network. Security What security measures do networks use? • Training and user awareness • Usernames and passwords • Firewalls • Proxy servers • Auditing / audit logs • Monitoring performance • Access rights for users • Encryption • Physical methods – lock the server away Wide Area Networks • Some large organisations are national or multinational, and data might need to be exchanged globally • Large wide area networks (WANs) therefore exist to make this data transfer: – possible – secure • Examples of WANs include: – – – – airline booking systems credit card payment systems national lottery machines Police National Computer The Internet and the World Wide Web • The internet and the world-wide web are not the same! The internet also supports: – – – – – e-mail newsgroups IRC chat FTP - file transfer telnet - for logging into other computers remotely • Through a variety of protocols, e.g.: – TCP/IP - transfer control protocol/internet protocol – POP3 (post office protocol) and SMTP (simple mail transfer protocol) – HTTP - hyper-text transfer protocol – FTP - file transfer protocol Internet Infrastructure • Consumers connect to Internet Service Providers (ISPs), e.g. Freeserve, AOL, Tiscali • ISPs connect to Network Service Providers (NSPs), e.g. BT • The links between the NSPs is the internet backbone Consumers ISP NSP NSP Internet backbone NSP NSP ISP Other ISPs ISP Connecting to the Internet • PSTN (public service telephone network) – connect using a modem – allows speeds up to 56kbps • ISDN (integrated services digital network) – digital phone line - dialling of number required – 64kbps per channel - usually 2 channels = 128 kbps. – Connect using an ISDN or terminal adapter • ADSL (asymmetric digital subscriber line) – – – – connect using a terminal/network adapter “always on” - no need to dial connection faster to download than to upload (asymmetric!) not charged per minute (unlike PSTN and ISDN) Synchronous and Asynchronous • With synchronous transmission, the bits are sent at regular intervals governed by a clock in the computer. – This is the method usually employed by mainframe computers – The rate of transmission is governed by the speed of the clock • Asynchronous transmission is used by PCs – Messages are preceded by a start message, e.g. “ready to send” – Messages have a stop message at the end – Parity bits or check digits can be added to detect errors in the communication Network Protocol • In general, a protocol is a set of rules governing communication – this term doesn’t only apply to computers, but also to diplomatic communication • If both communicating parties are using the same protocol, communication is much easier • An agreed protocol could include: – The transmission mode – synchronous or asynchronous – How characters are represent, e.g. ASCII or EBCDIC – Any encryption and keys used – Error detection and correction methods used, e.g. parity, check digits Factors Affecting Transmission Rate Transmission rate will be affected by: • The hardware used – e.g. how fast your network card, modem, etc., is • The type of connection you’re using – e.g. PSTN, ADSL, wireless • The type of cable you’re using, e.g. twisted pair, coaxial or fibre-optic • The transmission mode – synchronous or asynchronous • You can also make your transmission rate appear to be higher by using compression techniques to compress the data before you send it