* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Network Data Monitoring and Analysis
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Deep packet inspection wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
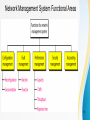
Wake-on-LAN wikipedia , lookup
Computer network wikipedia , lookup
Distributed firewall wikipedia , lookup
Zero-configuration networking wikipedia , lookup
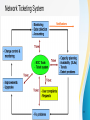
Cracking of wireless networks wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
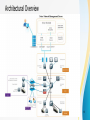
Network Data Monitoring and Analysis Computer Networks Lecture's Seminar Lecturer:Assoc.Prof.Turgay İBRİKÇİ Prepared by Çağla TERLİKCİOĞULLARI 1 2 Presentation Contents What Is Network Monitoring? Importance of Network Monitoring and Analysis Monitoring and Analysis Techniques Router Based Monitoring Techniques I. Simple Network Monitoring Protocol (SNMP) RFC 1157 II. Remote Monitoring (RMON) RFC 1757 III. Netflow RFC 3954 3 Continues on Presentation Contents Non-Router Based MonitoringTechniques I. Active Monitoring II. Passive Monitoring Windows Management Protocols Passive Tool Network Monitoring Application 4 What Is Network Monitoring Monitoring an active communications network in order to diagnose problems and gather statistics for administration and fine tuning The term network monitoring describes the use of a system that constantly monitors a computer network for slow or failing components and that notifies the network administrator in case of outages via email, pager or other alarms. It is a subset of the functions involved in network management. 5 Network Management Network Management System allow Network Administrators to automate configuration tasks and monitor network health ,giving Network Administrators the visibility need to proactively manage network The International Organization for Standardization (ISO) Network Management Forum divided network management into five functional areas: – Fault Management – Configuration Management – Security Management – Performance Management – Accounting Management 6 Network Management Platform • Basic features for any platform to include are: Graphical User Interface (GUI) Network Map Database Management System (DBMS) Standard Method to Query Devices Customizable Menu System Event Log 7 8 Three basic goals of network monitoring is: Performance Monitoring Fault Monitoring Account Monitoring 9 Network Management System Functional Areas 10 Network Ticketing System 11 Importance of Network Monitoring and Analysis Network management systems allow us to research: i. Traffic Measurements and Analysis ii. Network Anomaly Detection iii. Performance Evaluation of Networked Systems iv. Security,Reliability and Resiliciency v. QoS in Heterogeneous Network vi. Analysis and Detection of Network Outages 12 Architectural Overview 13 Monitoring and Analysis Techniques Two Monitoring Techniques are discussed in the my presentation: i. Router Based Monitoring Techniques ii. Non-Router Based Monitoring Techniques Some key terms you shuld know through over presentaion is: Fault:when something is down or unavailable Avaliability:percentage of time stuff is not down and is working NMS:Network Management System Baseline:A measurement of current performance MIB:A virtual database of management information avaliable on a network device that can be queried using SNMP to retrive device 14 Router Based Monitoring Techniques I-Simple Network Monitoring Protocol (SNMP) SNMP is an application layer protocol that is part of the TCP/IP protocol suite. It allows Network Administrators to manage; network performance, detecting and solving network problems, plan for network growth. It gathers traffic statistics through passive sensors that are implemented from router to end host. 15 What Is SNMP SNMP is a tool (protocol) that allows for remote and local management of items on the network including servers, workstations, routers, switches and other managed devices. Comprised of agents and managers Agent :process running on each managed node collecting information about the device it is running on. Manager :process running on a management workstation that requests information about devices on the network 16 SNMP Architectural View Simple Network Management Protocol-polls the Management Information Base(MIB) of network devices An SNMP trap allows a network device to notify a NMS system of an event through an SNMP message System Components Of SNMP 17 Three Parts Of SNMP SNMP protocol Defines format of messages exchanged by management systems and agents. Specifies the Get, GetNext, Set, and Trap operations Structure of Management Information(SMI) Defines format of messages exchanged by management systems and agents. Specifies the Get, GetNext, Set, and Trap operations Management Information Base (MIB) A map of the hierarchical order of all managed objects and how they are accessed 18 SNMP Message SNMP uses User Datagram Protocol (UDP) as the transport mechanism for SNMP messages. Four Basic Operation made by SNMP protocol: GET:Retrieves the value of a MIB variable stored on the agent machine(integer, string, or address of another MIB variable) GETNEXT:Retrieves the next value of the next lexical MIB variable SET:Changes the value of a MIB variable TRAP:An unsolicited notification sent by an agent to a management a notiapplication (typically fication of something unexpected, like an error) 19 SNMP Configuration 20 Distrubuted Network Management Configuration Object Identifier 21 Management Overview of SNMP 22 II- Remote Monitoring (RMON) Basic Concepts RMON enables various network monitors and console systems to exchange network-monitoring data. • Extends the SNMP functionality without changing the protocol • Allows the monitoring of remote networks (internetwork management) • MAC-layer (layer 2 in OSI) monitoring • Defines a Remote MONitoring (RMON) MIB that supplements MIB-II • with MIB-II, the manager can obtain information on individual devices only • with RMON MIB, the manager can obtain information on the LAN as a whole 23 D ata Analyzer SNMP Traffic Router BACKBONE NETWORK R outer SNMP Traffic RMON Probe RMON Components LAN Networks with RMON 24 RMON MIB rmon (mib-2 16) rmonConformance (20) statistics (1) probeConfig (19) history (2) usrHistory (18) a1Matrix (17) alarm (3) a1Host (16) host (4) n1Matrix (15) hostTopN (5) matrix (6) n1Host (14) filter (7) addressMap (13) capture (8) protocolDist ( 12) event (9) protocolDir (11) RMON1 Extension RMON2 RMON1 Token Ring (10) Figure 8.2 RMON Group 25 RMON Groups and Tables 26 III-Netflow Netflow is a feature that was introduced on Cisco routers that give the ability to collect IP network traffic as it enters an interface. Netflow consists of three components: a. Flow caching, b. FlowCollector, c. Data Analyzer. Seven unique fields define a flow 27 How Does NETFLOW Works? Traffic passes through routing/switching device interface Flow created (remember the 7 fields) and stored in NetFlow cache Flows grouped and exported in UDP packets to collector based on active and inactive flow timeout 28 NETFLOW Cache Example 29 NETFLOW Processing Order 30 Non-Router Based Monitoring Techniques Traffic Monitoring Network Monitoring Metrics 31 I-Active Monitoring Internet Control Message Protocol (ICMP) message used for diagnostic or control purposes or generated in response to errors in IP operations. I. TTL field: ping & traceroute use it in attempt to reach a given host computer or to trace a route to that host. II. Traceroute intentionally sends a packet with a low TTL value so that it will be discarded by each successive router in the destination path. III. The time between sending the packet and receiving back the ICMP message that it was discarded is used to calculate each successive hop travel time 32 TCP-UDP Based Active Monitoring TCP based Active Monitoring UDP based Active Monitoring 33 II-Passive Monitoring Passive monitoring unlike active monitoring does not inject traffic into the network or modify the traffic that is already on the network. Also unlike active monitoring, passive monitoring collects information about only one point in the network that is being measured rather than between two endpoints as active monitoring measures Passive monitoring can be achieved with the assistance of any packet sniffing program. 34 How Does Passive Monitoring Works Packets can be captured using Port Mirroring or Network Splitter (Tap) 35 Passive Monitoring tools I. Microsoft Network Monitor II. Wireshark III. Tshark IV. ssldump V. Tcpflow VI. dSniff 36 Windows Management Protocols The Microsoft Windows Operating System(OS) leverages its own suite of protocols for communications between Windows servers and workstations These protocols layer a top core TCP and UDP to enable server and service communication across an IP network Windows Management Protocols: i. Remote Desktop Protocol(RDP) ii. Windows Management Instrumentation(VMI) iii. WS-Management 37 Network Data Analysis TCP Server Listening Port Number Distribution Proportion Of The Internet Applications 38 THANK YOU FOR ATTENDING 39 REFERENCES: A Summary of Network Traffic Monitoring and Analysis Techniques,Alisha Cecil http://www.cse.wustl.edu/~jain/cse56706/ftp/net_monitoring.pdf Introduction to Passive Network Traffic Monitoring http://www.csd.uoc.gr/~hy459/front/passiveMonitoring_2015.pdf The African Network Operator Groups(AfNOG) Workshops SolarWinds Network Management Guide Cisco Nettflow For Accounting Analysis and Attack Simple Network Management Protocol, Chris Francois TCP/IP Protocol Suite Behrouz A.Forouzan 40