* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download View File - UET Taxila
IEEE 802.1aq wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Deep packet inspection wikipedia , lookup
Distributed firewall wikipedia , lookup
Internet protocol suite wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Network tap wikipedia , lookup
Computer network wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Peer-to-peer wikipedia , lookup
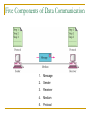
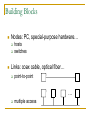
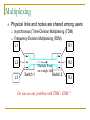
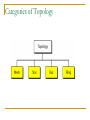
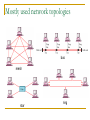
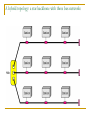
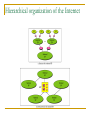
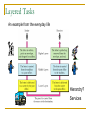
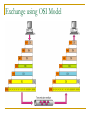
Computer Communication & Networks Lecture # 01 Introduction Nadeem Majeed Choudhary [email protected] Grading Policy Final Exam: Mid term Exam Assignments Quizzes: Labs 40% 20% 05% 10% 25% Quizzes may be announced or unannounced. Exams are closed-book and extremely time limited. Exams consist of design questions, numerical, maybe true-false and short answer questions. Reading Text book: Data Communications and Networking, B.A. Forouzan, McGraw-Hill, (Latest Available Edition) ISBN 0-07-292354-7. Reference books: Computer Networking, a top-down approach featuring the Internet, J.K.Kurose, K.W.Ross,Addison-Wesley, 2005, ISBN 0-321-26976-4. Computer Networks, A Systems Approach L. Peterson & Davie Data and Computer Communication by William Stallings Prentice Hall. Data Communications The term telecommunication means communication at a distance. The word data refers to information presented in whatever form is agreed upon by the parties creating and using the data. Data communications are the exchange of data between two devices via some form of transmission medium such as a wire cable. Fundamental Characteristics The effectiveness of a data communication system depend on four fundamental characteristics: Delivery Accuracy Timelines Jitter Five Components of Data Communication 1. Message 2. Sender 3. Receiver 4. Medium 5. Protocol Direction of data flow Simplex Half Duplex Full Duplex Network design Before looking inside a computer network, first agree on what a computer network is Computer network ? Set of serial lines to attach terminals to mainframe ? Telephone network carrying voice traffic ? Cable network to disseminate video signals ? Specialized to handle: Keystrokes Voice Video What distinguishes a Computer network ? Generality Built from general purpose programmable hardware Supports wide range of applications Not optimized for special purpose application like making phone calls or delivering television signals Information, Computers, Networks Information: anything that is represented in bits Form (can be represented as bits) vs Substance (cannot be represented as bits) Properties: Infinitely replicable Computers can “manipulate” information Networks create “access” to information Networks Potential of networking: move bits everywhere, cheaply, and with desired performance characteristics Network provides “connectivity” What is “Connectivity” ? Direct or indirect access to every other node in the network Connectivity is the magic needed to communicate if you do not have a direct pt-pt physical link. Tradeoff: Performance characteristics worse than true physical link! Building Blocks Nodes: PC, special-purpose hardware… hosts switches Links: coax cable, optical fiber… point-to-point … multiple access Why not connect each node with every other node ? Number of computers that can be connected becomes very limited Number of wires coming out of each node becomes unmanageable Amount of physical hardware/devices required becomes very expensive Solution: indirect connectivity using intermediate data forwarding nodes A Network A network can be defined recursively as two or more nodes connected by a physical link Or two or more networks connected by one or more nodes Switched Networks A network can be defined recursively as... two or more nodes connected by a link white nodes (switches) implement the network colored nodes (hosts) use the network Switched Networks A network can be defined recursively as... two or more networks connected by one or more nodes: internetworks white nodes (router or gateway) interconnects the networks a cloud denotes “any type of independent network” Switching Strategies Circuit switching: carry bit streams a. b. c. d. establishes a dedicated circuit links reserved for use by communication channel send/receive bit stream at constant rate example: original telephone network • Packet switching: storeand-forward messages a. operates on discrete blocks of data b. utilizes resources according to traffic demand c. send/receive messages at variable rate d. example: Internet What next ? Hosts are directly or indirectly connected to each other Can we now provide host-host connectivity ? Nodes must be able to say which host it wants to communicate with Addressing and Routing Address: byte-string that identifies a node Routing: forwarding decisions usually unique process of determining how to forward messages to the destination node based on its address Types of addresses unicast: node-specific broadcast: all nodes on the network multicast: some subset of nodes on the network Wrap-up A network can be constructed from nesting of networks An address is required for each node that is reachable on the network Address is used to route messages toward appropriate destination What next ? Hosts know how to reach other hosts on the network How should a node use the network for its communication ? All pairs of hosts should have the ability to exchange messages: cost-effective resource sharing for efficiency Multiplexing Physical links and nodes are shared among users (synchronous) Time-Division Multiplexing (TDM) Frequency-Division Multiplexing (FDM) L1 R1 L2 L3 Switch 1 Multiple flows on a single link Switch 2 R2 R3 Do you see any problem with TDM / FDM ? What Goes Wrong in the Network? Reliability at stake Bit-level errors (electrical interference) Packet-level errors (congestion) distinction between lost and late packet Link and node failures distinction between broken and flaky link distinction between failed and slow node What Goes Undesirable in the Network? Required performance at stake Messages are delayed Messages are delivered out-of-order Third parties eavesdrop The challenge is to fill the gap between application expectations and hardware capabilities Networks: key issues Network criteria Performance Reliability Throughput Delay Data transmitted are identical to data received. Measured by the frequency of failure The time it takes a link to recover from a failure Security Protecting data from unauthorized access Terminology The throughput or bandwidth of a channel is the number of bits it can transfer per second The latency or delay of a channel is the time that elapses between sending information and the earliest possible reception of it Network topologies Topology defines the way hosts are connected to the network Network topology issues a goal of any topology 1. high throughput (bandwidth) 2. low latency Bandwidth and Latency Bandwidth 1. telecommunications: range of radio frequencies: a range of radio frequencies used in radio or telecommunications transmission and reception 2. computing: communications capacity: the capacity of a communications channel, for example, a connection to the Internet, often measured in bits per second 3. a data transmission rate; the maximum amount of information (bits/second) that can be transmitted along a channel Latency A synonym for delay, is an expression of how much time it takes for transmission from one designated point to another Categories of Topology Mostly used network topologies bus mesh star ring A hybrid topology: a star backbone with three bus networks Hierarchical organization of the Internet LAN, WAN & MAN Network in small geographical Area (Room, Building or a Campus) is called LAN (Local Area Network) Network in a City is call MAN (Metropolitan Area Network) Network spread geographically (Country or across Globe) is called WAN (Wide Area Network) Layering & Protocol Stacks What’s a protocol? human protocols: “what’s the time?” “I have a question” introductions … specific msgs sent … specific actions taken when msgs received, or other events network protocols: machines rather than humans all communication activity in Internet governed by protocols Protocol protocols define format, order of msgs sent and received among network entities, and actions taken on msg transmission, receipt a human protocol and a computer network protocol: Hi Hi Got the time? 2:00 time TCP connection req. TCP connection reply. Get http://gaia.cs.umass.edu/index.htm <file> Standard Essential in creating and maintaining an open and competitive market for equipment manufacturers Guaranteeing national & international interoperability of data & telecommunication technology & process. Layered Tasks An example from the everyday life Hierarchy? Services Why layered communication? To reduce complexity of communication task by splitting it into several layered small tasks Functionality of the layers can be changed as long as the service provided to the layer above stays unchanged makes easier maintenance & updating Each layer has its own task Each layer has its own protocol Reference Models OSI reference model TCP/IP OSI Reference model 1. 2. 3. 4. Open System Interconnection 7 layers Crate a layer when different abstraction is needed Each layer performs a well define function Functions of the layers chosen taking internationally standardized protocols Number of layers – large enough to avoid complexity Seven layers of the OSI model Exchange using OSI Model Issues, to be resolved by the layers Larger bandwidth at lower cost Error correction Flow control Addressing Multiplexing Naming Congestion control Mobility Routing Fragmentation Security .... Applications E-mail Searchable Data (Web Sites) E-Commerce News Groups Internet Telephony (VoIP) Video Conferencing Chat Groups Instant Messengers Internet Radio Research areas in Networking Routing Security Ad-hoc networks Wireless networks Protocols Quality of Service … Readings Chapter 1: 1.1, 1.2 Computer Networks, A Systems Approach L. Peterson & Davie Chapter 1 (B. A Forouzan) Section 1.1, 1.2, 1.3,1.4 Chapter 2 (B.A Forouzan) Section 2.1