* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download CSCI 360 Intro To Computer Networks INFS 361 Network
Remote Desktop Services wikipedia , lookup
Computer network wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Distributed firewall wikipedia , lookup
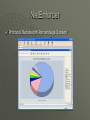
CSCI 360 Intro To Computer Networks INFS 361 Network Administration Bob Bradley Instructor My name is Bob Bradley Office and office hours and web page www.utm.edu/~bbradley See web page for Syllabus and timeline CS 360 Class ? Midterm/test/final/quizes There will be programming projects. More so this semester. How I grade projects… This for a C, this for a B, this for an A… Prereqs: c++ cs221 , cs200/201 Book - Computer Networks and Internets 4th Edition And Workbook - Hands-On-Networking with Internet Technologies 2nd Edition Will be going though most of the book. You will need the latest edition. Will focus on Network Application Protocols and Programming • • c++, c#, Java Free MSDN developer studio - get it from the cs department Will be changing the schedule… Check the web often… This week Overview then Chap 1,2,3. Talk about schedule for class... INFS 361 Book - Business Data Networks and Telecommunications 5th Edition Prereqs: INFS 316 Lots of quizes Several Projects Midterm and Final Will focus on Network Administration Projects • Microsoft Virtual PC 2004 Windows 2003 Server • File Server, IIS Web Server • DHCP, DNS • Mail Linux • Apache Web Server • DHCP, DNS • SendMail Overview Data Transmission Packet Transmission - packets, frames, • • • Sniffers - like radio scanner Privacy and sniffing Networks like cell phones… public can scan/receive transmissions • • TCP/IP IP - arp, bind, ip datagrams, encapsulation, icmp Hardware addresses LANS vs WANS Connection vs Connectionless Internetworking Protocols Network Applications Client server - sockets - DNS – E-Mail (whole weeks) – HTTP (Web), FTP, SMTP p2p file sharing Naptster Network security, firewalls, finals Wireless - 802.11b, firewall security, rfcs, vpns, etc. Dorm Network In 1996 • UTM was one of the first Universities to put two hard-wired network connections in every dorm room • network was very fast 10 MegaBit Ethernet T1 (24 Phone lines/1.5 MegaBit/Sec) connection to internet • web pages were small and simple 1999 Network Slowdown In 1999, UTM’s network (and most University networks) became very, very slow. In 1999, a program called Napster came out! Allowed users to download and share music files (MP3s). When this first came out, it made our whole university network totally unusable. • You could no longer check any web pages, read email, download files or do anything. • The file sharing program ate up all of our bandwidth. Web Page vs Music File Typical web page with small graphics • 3-30KB (Kilo-Bytes) Typical MP3 music file • 3-6MB (Mega-Bytes) • 100s of times bigger Relative width of T1 • • • • 1.5 Mega-bits/sec About 150 Kilo-Bytes/sec About 5-50 web pages/sec About 1 song in 20-40 sec If only one person using the net Difference in download times Note this example is speeded up, but notice the relative differences in time it takes to download web pages vs. the songs. T1 5 Web Pages 100 Web Pages 5 Songs Also note, most file sharing programs typically share out 5 or more songs at a time, so multiply this by every user using a file sharing program. Wanted traffic gets bogged down With a steady stream of large music files coming and going, the “pipe” gets bogged down. Email and web pages have to wait in line and it is a first come first server system. T1 Packet/Traffic Shaper/Filter T1 A packet shaper/traffic filter reserves some of the channels, so that wanted traffic (like web pages and email) can still get though without having to wait on the unwanted traffic (file/music sharing). Dorm Network We now have over 1300 student computers connected in the dorms. We now have a T3/DS3 28 T1s or 672 phone lines 45 MegaBits/Sec Relative size of T1 vs Relative size of T3 Bandwidth of Protocols Even with our DS3 connection, this chart shows what happens to our bandwidth if we turn off our traffic/packet shaper Bandwidth with filter turned on Bandwidth when filter is turned off NetEnforcer The Real-Time Traffic Monitor NetEnforcer Get monthly updated rules used to filter the traffic NetEnforcer Protocol Bandwidth Percentage Screen How Not To Get Sued By The RIAA For File-Sharing (And Other Ideas to Avoid Being Treated Like a Criminal) The Recording Industry Association of America (RIAA) announced on June 25, 2003, that it will begin suing users of peer-to-peer (P2P) file-sharing systems within the next few weeks. According to the announcement, the RIAA will be targeting users who upload/share "substantial" amounts of copyrighted music. The RIAA has stated that it will choose who to sue by using software that scans users' publicly available P2P directories and then identifies the ISP of each user. Then, using the Digital Millennium Copyright Act (DMCA), the RIAA will subpoena the ISP for each user's name, address, and other personal information in order to sue that user. http://www.eff.org/IP/P2P/howto-notgetsued.php