* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Slides for Chapter 3: Networking and Internetworking
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
TCP congestion control wikipedia , lookup
Wireless security wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Distributed firewall wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Deep packet inspection wikipedia , lookup
Computer network wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Internet protocol suite wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Networking and Internetworking
Jenhui Chen
Assistant Professor
http://www.csie.cgu.edu.tw/jhchen
Networking issues for DS
Performance
Latency
Data transfer rate
Scalability
Reliability
Security
Firewall
Mobility
Quality of service
Multicasting
Types of Network (1/2)
Local Area Networks (LANs)
Wide Area Networks (WANs)
Metropolitan Area Networks (MANs)
Wireless Networks
Internetworks
Network Comparisons
See the following table
Types of Network (2/2)
Range
LAN
1-2 kms
WAN
worldwide
MAN
2-50 kms
Wireless LAN 0.15-1.5 km
Wireless WAN worldwide
Internet
worldwide
Bandwidth (Mbps) Latency (ms)
10-1000
0.010-600
1-150
2-11
0.010-2
0.010-2
1-10
100-500
10
5-20
100-500
100-500
Network Principles
Packet Transmission
Data Streaming
Switching Schemes
Broadcast
Ethernet, wireless networks
Circuit Switching
Packet Switching
Store-and-forward network
Frame Relay
Brings some of the advantages of circuit switching to packet-switching
networks
Protocols
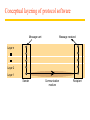
Conceptual layering of protocol software
Message received
Message sent
Layer n
Layer 2
Layer 1
Sender
Communication
medium
Recipient
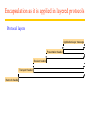
Encapsulation as it is applied in layered protocols
Protocol layers
Applic ation-layer mess age
Pres entation header
Sess ion header
Transport header
Netw ork header
Protocol layers in the ISO Open Systems
Interconnection (OSI) model
Mess age receiv ed
Mess age s ent
Lay ers
Applic ation
Pres entation
Sess ion
Transport
Netw ork
Data link
Phy sical
Sender
Communic ation
medium
Recipient
OSI protocol summary
Layer
Application
Presentation
Session
Transport
Network
Data link
Physical
Description
Protocols that are designed to meet the communication requirements of
specific applications, often defining the interface to a service.
Protocols at this level transmit data in a network representation that is
independent of the representations used in individual computers, which may
differ. Encryption is also performed in this layer, if required.
At this level reliability and adaptation are performed, such as detection of
failures and automatic recovery.
This is the lowest level at which messages (rather than packets) are handled.
Messages are addressed to communication ports attached to processes,
Protocols in this layer may be connection-oriented or connectionless.
Transfers data packets between computers in a specific network. In a WAN
or an internetwork this involves the generation of a route passing through
routers. In a single LAN no routing is required.
Responsible for transmission of packets between nodes that are directly
connected by a physical link. In a WAN transmission is between pairs of
routers or between routers and hosts. In a LAN it is between any pair of hosts.
The circuits and hardware that drive the network. It transmits sequences of
binary data by analogue signalling, using amplitude or frequency modulation
of electrical signals (on cable circuits), light signals (on fibre optic circuits)
or other electromagnetic signals (on radio and microwave circuits).
Examples
HTTP, FTP , SMTP,
CORBA IIOP
Secure Sockets
(SSL),CORBA Data
Rep.
TCP, UDP
IP, ATM virtual
circuits
Ethernet MAC,
ATM cell transfer,
PPP
Ethernet base- band
signalling, ISDN
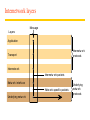
Internetwork layers
Mess age
Lay ers
Applic ation
Internetw ork
protocols
Transport
Internetw ork
Internetw ork pac kets
Netw ork interface
Netw ork-spec ific packets
Underly ing netw ork
Underly ing
netw ork
protocols
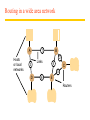
Routing in a wide area network
A
Hosts
or local
networks
1
B
2
3
Links
4
C
5
D
6
E
Routers
Routing tables for the network in Figure 3.7
Routings from A
To
Link
Cost
A
local
0
B
1
1
C
1
2
D
3
1
E
1
2
Routings from B
To
Link
Cost
A
1
1
B
local
0
C
2
1
D
1
2
E
4
1
Routings from D
To
Link
Cost
A
3
1
B
3
2
C
6
2
D
local
0
E
6
1
Routings from C
To
Link
Cost
A
2
2
B
2
1
C
local
0
D
5
2
E
5
1
Routings from E
To
Link
Cost
A
4
2
B
4
1
C
5
1
D
6
1
E
local
0
Pseudo-code for RIP routing algorithm
Send: Each t seconds or when Tl changes, send Tl on each non-faulty
outgoing link.
Receive: Whenever a routing table Tr is received on link n:
for all rows Rr in Tr {
if (Rr.link | n) {
Rr.cost = Rr.cost + 1;
Rr.link = n;
if (Rr.destination is not in Tl) add Rr to Tl;
// add new destination to Tl
else for all rows Rl in Tl {
if (Rr.destination = Rl.destination and
(Rr.cost < Rl.cost or Rl.link = n)) Rl = Rr;
// Rr.cost < Rl.cost : remote node has better route
// Rl.link = n : remote node is more authoritative
}
}
}
Internetworking
Routers
Bridges
Hubs
Switchs
Switches perform a similar function to routers, but for
local networks (normally Ethernet) only.
Tunnelling
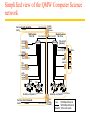
Simplified view of the QMW Computer Science
network
Campus138.37.95.240/29
router subnet
138.37.95.241
router/
firewall
hammer
Staff subnet
compute
server
Student subnet
138.37.88.251
138.37.88
138.37.94.251
Eswitch
Eswitch
bruno
138.37.88.249
%
138.37.94
file server/
gateway
custard
138.37.94.246
dialup
server
henry
138.37.88.230
printers
other
servers
file
server
hotpoint
138.37.88.162
web
server
copper
138.37.88.248
hub
hub
desktop computers138.37.88.xx
Campus138.37.95.248/29
subnet
router
desktop computers138.37.94.xx
sickle
router/
138.37.95.249 firewall
100 Mbps Ethernet
1000 Mbps Ethernet
Eswitch: Ethernet switch
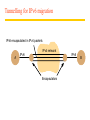
Tunnelling for IPv6 migration
IPv6 encapsulated in IPv4 packets
IPv4 network
A
IPv6
IPv6
Encapsulators
B
TCP/IP layers
Message
Layers
Application
Messages (UDP) or Streams (TCP)
Transport
UDP or TCP packets
Internet
IP datagrams
Network interface
Network-specific frames
Underlying network
Encapsulation in a message transmitted via TCP
over an Ethernet
Application message
TCP header
IP header TCP
Ethernet header IP
Ethernet frame
port
The programmer's conceptual view of a TCP/IP
Internet
Applic ation
Applic ation
TCP
UDP
IP
Internet address structure, showing field sizes in
bits
Clas s A:
Clas s B:
0
7
24
Netw ork ID
Host ID
1 0
14
16
Netw ork ID
Host ID
21
Clas s C:
1 1 0
8
Netw ork ID
Host ID
28
Clas s D (multicast ):
1 1 1 0
Multicast address
27
Clas s E (reserved):
1 1 1 1 0
unused
Decimal representation of Internet addresses
octet 1
octet 2
Netw ork ID
Clas s A:
1 to 127
octet 3
Host ID
0 to 255
0 to 255
Netw ork ID
Clas s B:
128 to 191
192 to 223
0 to 255
1.0.0.0 to
127.255.255.255
0 to 255
128.0.0.0 to
191.255.255.255
Host ID
0 to 255
0 to 255
Netw ork ID
Clas s C:
Range of addres ses
0 to 255
Host ID
0 to 255
1 to 254
192.0.0.0 to
223.255.255.255
Multicast address
Clas s D (multicast):
Clas s E (reserved):
224 to 239
0 to 255
0 to 255
1 to 254
224.0.0.0 to
239.255.255.255
240 to 255
0 to 255
0 to 255
1 to 254
128.0.0.0 to
247.255.255.255
IP packet layout
header
IP addres s of s ource
IP addres s of des tination
up to 64 kiloby tes
data
IPv6 header layout
Version (4 bits) Priority (4 bits )
Pay load length (16 bits )
Flow label (24 bits)
Next header (8 bits)
Sourc e address
(128 bits )
Destination addres s
(128 bits )
Hop limit (8 bits)
IPv6 embodies
Address space: 128 bits (16 bytes)
Routing speed
Real-time and other special services
Future evolution
Multicast and anycast
Security
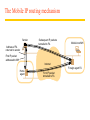
The Mobile IP routing mechanism
Sender
Subsequent IP packets
tunnelled to FA
Mobile host MH
Address of FA
returned to sender
First IP packet
addressed to MH
Internet
Foreign agent FA
Home
agent
First IP packet
tunnelled to FA
TCP and UDP
Use of ports
UDP features
TCP features
Sequencing
Flow control
Retransmission
Buffering
Firewall
Service control
Behavior control
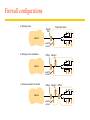
Firewall configurations
a) Filtering router
Router/
filter
Protected intranet
Internet
w eb/ftp
s erv er
b) Filtering router and bastion
R/filter
Bastion
Internet
w eb/ftp
s erv er
c ) Sc reened s ubnet for bas tion
R/filter
Internet
w eb/ftp
s erv er
Bastion
R/filter
IEEE 802 network standards
IEEE No. Title
802.3
802.4
802.5
802.6
802.11
Reference
CSMA/CD Networks (Ethernet) [IEEE 1985a]
Token Bus Networks
[IEEE 1985b]
Token Ring Networks
[IEEE 1985c]
Metropolitan Area Networks
[IEEE 1994]
Wireless Local Area Networks [IEEE 1999]
Wireless LAN configuration
A
B
C
Laptops
radio obs truction
Palmtop
Server
D
E
Wireless
LAN
Base s tation/
acc es s point
LAN
ATM protocol layers
Mess age
Lay ers
Applic ation
Higher-lay er protoc ols
ATM adaption layer
ATM cells
ATM layer
ATM virtual channels
Phy sical
ATM cell layout
Header: 5 by tes
Virtual path id
Virtual channel id
Flags
53 bytes
Data
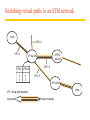
Switching virtual paths in an ATM network
Host
VPI = 2
VPI = 3
VPI = 4
VPI in VPI out
2
3
VP/VC
s w itch
VP sw itch
4
5
VPI = 5
VP sw itch
Host
VPI : virtual path identifier
Virtual path
Virtual channels