* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download CN 2015 1-2 - DSpace
Wireless security wikipedia , lookup
Distributed firewall wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Deep packet inspection wikipedia , lookup
Network tap wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Computer network wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Internet protocol suite wikipedia , lookup
Airborne Networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
COMMUNICATION NETWORKS
Mr. DEEPAK P.
Associate Professor
ECE Department
SNGCE
1
DEEPAK.P
UNIT 1
2
DEEPAK.P
Objective
At the end of this Unit
You will learn
Network services
Layered architecture
Network topology
DEEPAK.P
3
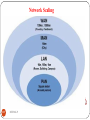
Social relation
In social science, a social relation or social interaction refers to a
relationship between two , three or more individuals (e.g. a
social group).
Normally social network is filled with peoples.
Social networking allow users to share ideas, activities, events,
and interests within their individual networks.
4
DEEPAK.P
Social Network
To protect user privacy, social networks usually have controls
that allow users to choose who can view their profile, contact
them, add them to their list of contacts, and so on.
Popular methods now combine many of these, with Face book
and Twitter widely used worldwide.
5
DEEPAK.P
Pictorial Representation of Social
Networks
Simple
Complex
6
DEEPAK.P
Aim for Networking
The main aim for networking is Communication
Communication means sharing something
7
DEEPAK.P
Fundamental Concepts
Communication
Means Sharing of information.
Sharing may be
Local
Transmits information locally
Remote
Sending information to remote places.
Data
Concepts or information is called data.
Data communication
Sharing of information between two devices
8
DEEPAK.P
FUNDAMENTAL CONCEPTS
Characteristics/Effectiveness of Data Communication
Delivery
Accuracy
Timeless
Components in data communication
Protocol
Sender
9
DEEPAK.P
Protocol
Medium
Receiver
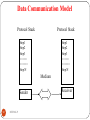
Data Communication Model
Protocol Stack
Protocol Stack
Step1
Step2
Step3
-----------------Step N
Step1
Step2
Step3
-----------------Step N
Medium
Sender
10
DEEPAK.P
Receiver
Data Communication Model
Protocols
Specifies common set of rules and signals which
computers on the network use to communicate.
Protocol suite or protocol stack
The total package of protocols.
11
DEEPAK.P
Fundamental Concepts
Sender
MODEM
MUX
Real Life Data Communication
Medium
Receiver
12
DEEPAK.P
MODEM
De MUX
Transmission Modes
DEEPAK.P
13
Fundamental Concepts
Mode of Transmission
Transmission can be classified into two according to the
direction of data flow.
Unidirectional
Bidirectional
14
DEEPAK.P
Simplex
Half Duplex
Full Duplex
Full – Full Duplex
Mode of Transmission.
Unidirectional (Simplex)
Information is communicated in only one direction.
It can be implemented by single wire.
Examples
One way street
Communication from CPU to monitor.
Communication from Keyboard to CPU.
Communication from Computer to printer.
Communication from Microphone to speaker.
TV or radio broadcasting
15
DEEPAK.P
Mode of Transmission
Simplex
Sender
Receiver
Direction of Data Flow
Half Duplex
Cannot perform two direction at a time
Sender
Receiver
Direction of Data Flow
16
DEEPAK.P
Mode of Transmission.
Half duplex
Information is communicated in both direction, but not
simultaneously.
It requires definite turn around time to change from transmitting
mode to receiving mode.
Due to this delay communication is slower .
It can be implemented by two wire. One for Data and other is
ground
Examples
One line traffic in narrow bridges.
Walkie-talkies.
CB (Citizen’s Band) Radio
17
DEEPAK.P
Mode of Transmission
Full Duplex
It can perform two direction at a time
Sender
Receiver
Direction of Data Flow
Full –Full Duplex
It can perform two direction but not between same two
stations
Receiver
18
DEEPAK.P
Receiver/Sender
Direction of Data Flow
Sender
Mode of Transmission.
Full duplex
Information is communicated in both direction simultaneously.
It can be implemented by as two wire or four wire circuit.
In two wire circuit, total channel capacity is divided in to two.
In four wire circuit , channel capacity can be increased.
Examples
Two way traffic.
Telephone Conversation.
19
DEEPAK.P
Computer Networks
DEEPAK.P
20
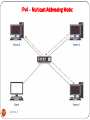
Computer network
In its simplest form, networking is defined as two computers
being linked together, either physically through a cable or
through a wireless device.
Computer network consists of two or more computers linked
together to exchange data and share resources
A computer network is a collection of hardware components
and computers interconnected by communication channels. .
21
DEEPAK.P
What is a Computer network
• A popular example of a computer network is the Internet,
which allows millions of users to share information
22
DEEPAK.P
5/5/2017
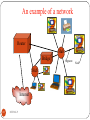
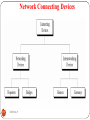
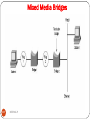
An example of a network
Router
Hub
Bridge
Hub
Internet
23
DEEPAK.P
Segment
Node
Network Goals
DEEPAK.P
24
Networks Fundamentals
Network Goals or aims
1.Resource sharing.---- May be Software of Hardware
2.High reliability.---Alternative Sources of data
Important in banks, military, Air traffic control
3.Saving of money
Money can be saved if we go through Client server model
4.Data Sharing.
5.System performance can be improved.
6.Powerful communication medium.
25
DEEPAK.P
Network Criteria
DEEPAK.P
26
Networks Fundamentals
Network Issues/Criteria
To consider a network is effective and efficient, it must meet
some criteria
I.
Performance
II.
Reliability.
III. Security
I.
Performance can be analyzed by
Transit time
Response Time
27
DEEPAK.P
:Time taken to Transmit
:Time taken to get a response
Network Issues/Criteria
Response Time
It depends on the following factors.
28
1.
No of users. (Traffic Load).
2.
Types of medium
3.
Type of hardware included in the network.
4.
Software were not updated.
5.
Lack of education
6.
Improper instruction
DEEPAK.P
Network Issues/Criteria
II. Reliability
It depends on the following factors.
1.
Frequency of failure.
2.
Recovery time after failure.
3.
Catastrophe----- prevent network from Fire hazards, Earth
quakes, Theft
III. Security
Protecting Data from
29
1.
Un authorized access
2.
Virus
DEEPAK.P
Network Issues/Criteria
Un authorized access
It has two levels
Lower level------Improper/Week password
Higher level------Encryption techniques
30
DEEPAK.P
Network Functions
DEEPAK.P
31
Network Functions
Addressing--- Identify sender and receiver
Routing--- Find the path between sender and receiver
Flow Control----Traffic flow can be controlled
Congestion control
Security
Backup
Failure monitoring
Traffic Monitoring
Accountability
Internetworking
Network Management
32
Error detection and correction
DEEPAK.P
Network Connections
DEEPAK.P
33
Types Of Connections
1.
POINT-TO-POINT
Provides a direct link between two devices.
Eg. Each computer is connected directly to a
printer .
2.
MULTI-POINT/MULTI DROP
Provides a link between three or more devices on a
network.
It will share the link/Channel capacity
34
DEEPAK.P
Types Of Connections
Multi point
It is two types
Time sharing
Sharing the link turn by turn
Spatially shared
Sharing of link simultaneously
Two relationship is possible in multi point connection
Peer- to –peer
All the nodes has equal right to access the link
Primary-Secondary
One will be master and other will be slave
35
DEEPAK.P
What is a Types Of Connections
Peer-to-Peer
Computers on the network are equals
No file server
Users decides which files and peripherals to share
It is not suited for networks with many computers
Easy to set up; Home networks
Network Components
DEEPAK.P
37
Network Components
1.
Physical Media
2.
Interconnecting Devices
3.
Computers
4.
Networking Software
Network Components
Physical media
Cables- Telephone lines, coaxial cable,
microwave, satellites, wireless, and fiber optic
cables
Interconnecting Devices
Routers- Devices that examine the data transmitted and
send it to its destination
Switches- High speed electronic switches
maintain connections between computers
Protocols- Standards that specify how network
components communicate with each other
39
DEEPAK.P
Introduction to Computer Networks
Physical Media
Networking media can be
defined simply as the means
by which signals (data) are
sent from one computer to
another (either by cable or
wireless means).
40
DEEPAK.P
Introduction to Computer Networks
Networking Devices
HUB, Switches, Routers, Wireless
Access Points, Modems etc.
41
DEEPAK.P
Network Topology
DEEPAK.P
42
Topology
A network's topology is comparable to the blueprints of a new
home in which components such as the electrical system,
heating and air conditioning system, and plumbing are
integrated into the overall design.
Taken from the Greek work "Topos" meaning "Place,"
Specifies the geometric arrangement of the network or a
description of the layout of a specific region.
43
DEEPAK.P
Topology
A network topology is the basic design of a computer
network.
It details how the network components such as nodes
and links are interconnected.
Topology, in relation to networking, describes the
configuration of the network; including the location of
the workstations and wiring connections.
44
DEEPAK.P
Network Topology
It is two types
Logical
Physical
The complete physical structure of the cable (or data-
transmission media) is called the physical topology .
The way in which data flows through the network (or data-
transmission media) is called the logical topology.
45
DEEPAK.P
Network Topology
Network topology can be classified in to
BUS
STAR
MESH
TREE
RING
HYBRID
46
DEEPAK.P
Bus Topology
DEEPAK.P
47
Bus Topology
48
DEEPAK.P
Bus Topology
The simplest and one of the most common of all topologies
Bus consists of a single cable, called a Backbone, that connects
all workstations on the network using a single line.
Each workstation has its own individual signal that identifies it
and allows for the requested data to be returned to the correct
originator.
In the Bus Network, messages are sent in both directions from a
single point and are read by the node (computer or peripheral on the
network) identified by the code with the message.
49
DEEPAK.P
Bus Topology
Most Local Area Networks (LANs) are Bus Networks
because the network will continue to function even if one
computer is down.
This topology works equally well for either peer to peer or
client server.
50
DEEPAK.P
Star Topology
DEEPAK.P
51
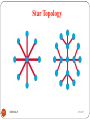
Star Topology
All devices connected with a Star setup communicate
through a central Hub by cable segments.
Signals are transmitted and received through the Hub.
It is the simplest and the oldest and all the telephone
switches are based on this.
In a star topology, each device has separate connection to
the network.
52
DEEPAK.P
Star Topology
53
DEEPAK.P
5/5/2017
Ring Topology
DEEPAK.P
54
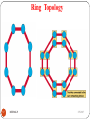
Ring Topology
All the nodes in a Ring Network are connected in a closed
circle of cable.
Messages that are transmitted travel around the ring until
they reach the computer that they are addressed to, the
signal being refreshed by each node.
In a ring topology, the network signal is passed through
each network card of each device and passed on to the
next device.
55
DEEPAK.P
Ring Topology
Each device processes and retransmits the signal, so it is
capable of supporting many devices in a somewhat slow
but very orderly fashion.
Important feature is that everybody gets a chance to send
a packet and it is guaranteed that every node gets to send
a packet in a finite amount of time.
56
DEEPAK.P
Ring Topology
57
DEEPAK.P
5/5/2017
Mesh Topology
DEEPAK.P
58
Mesh Topology
The mesh topology connects all devices (nodes) to each
other for redundancy and fault tolerance
It is used in WANs to interconnect LANs and for
mission critical networks like those used by banks and
financial institutions.
Implementing the mesh topology is expensive and
difficult
59
DEEPAK.P
5/5/2017
Mesh Topology
Full Mesh
60
DEEPAK.P
Partial Mesh
5/5/2017
Tree Topology
DEEPAK.P
61
Tree Topology
62
DEEPAK.P
5/5/2017
Tree Topology
63
DEEPAK.P
5/5/2017
Hybrid Topology
DEEPAK.P
64
Hybrid Topology
Hybrid networks use a combination of any two or more
topologies in such a way that the resulting network does
not exhibit one of the standard topologies
65
DEEPAK.P
5/5/2017
Hybrid Topology
66
DEEPAK.P
5/5/2017
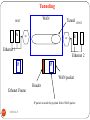
Switching
DEEPAK.P
67
Connecting devices
Switch
HUB
68
DEEPAK.P
Switch
Network consists of a set of inter connected nodes called
switches
From which information is transmitted from source to
destination through different routers.
It operates at layer 2 of OSI model (Data Link Layer)
69
DEEPAK.P
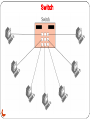
Switch
Switches can be a valuable asset to networking.
Switch can increase the capacity and speed of your
network.
Switches occupy the same place in the network as
hubs.
Unlike hubs, switches examine each packet and process
it accordingly rather than simply repeating the signal
to all ports.
70
DEEPAK.P
Network Switch
71
DEEPAK.P
Network Switch
72
DEEPAK.P
Switch
Some switches have additional features, including the
ability to route packets.
These switches are commonly known as layer-3 or
multilayer switches.
LAN switches come in two basic architectures,
Cut-through and
Store-and-forward.
73
DEEPAK.P
Switch
Cut-through switches only examine the destination
address before forwarding it on to its destination
segment.
A store-and-forward switch, on the other hand, accepts and
analyzes the entire packet before forwarding it to its
destination.
74
DEEPAK.P
Switch
75
DEEPAK.P
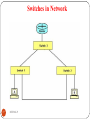
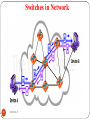
Switches in a Network
DEEPAK.P
76
Switches in Network
77
DEEPAK.P
Switches in Network
78
DEEPAK.P
Switching
DEEPAK.P
79
Switching
Determines when and how packets/messages are forwarded
through the network .
Specifies the granularity and timing of packet progress
Relationship with flow control has a major impact on
performance of a Network
80
DEEPAK.P
Switching
81
DEEPAK.P
Switching
Switching can be classified in to
Circuit switched Networks
2. Packet switched Networks
1.
Datagram Network
Switched virtual circuit
Virtual Circuit Networks
3.
82
Message switched Networks
DEEPAK.P
Permanent virtual circuit
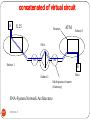
Circuit Switching
DEEPAK.P
83
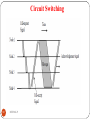
Circuit Switching
It is a methodology of implementing a telecommunications
network in which two network nodes establish a dedicated
communications channel (circuit).
In circuit switching, most of the time line is idle
Circuit switching gives fixed data rate
Once circuit is established , that connection is the path for
transmission.
84
DEEPAK.P
Switch
85
DEEPAK.P
Switch
86
DEEPAK.P
Circuit Switching
Circuit switching is also termed as connection
oriented networks
It has three steps
Connection Establishment
Data Transfer
Circuit Disconnects
87
DEEPAK.P
Circuit Switching
In circuit switching, a caller must first establish a
connection to a called party before any
communication is possible.
It maintain the connection to transfer message
The circuit is terminated when the connection is closed.
88
DEEPAK.P
Circuit Switching
89
DEEPAK.P
Circuit Switching
90
DEEPAK.P
Circuit Switching
Circuit switching uses any of the three technologies
1. Space division switches
2. Time division switches
3. Combination of both
91
DEEPAK.P
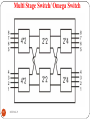
Space division switches
Provide a separate physical connection between inputs
& outputs (separated in space)
Some of the space switches are
Cross bar switch
Crossbar switch: consists of N x N cross-points
( N: number of input lines = number of output lines)
92
Multi stage switch
DEEPAK.P
Cross Bar Switch
93
DEEPAK.P
Cross Bar Switch
94
DEEPAK.P
Multi Stage Switch/ Omega Switch
95
DEEPAK.P
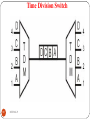
Time Division Switch
96
DEEPAK.P
Time Division Switch
TDM with Switching using TSI
TSI=Time Slot Interchange
97
DEEPAK.P
Packet Switching
DEEPAK.P
98
Packet Switching
Data are send as packets
Packet size can be variable
Packet contains data and header
99
DEEPAK.P
Switch
100
DEEPAK.P
Switching
101
DEEPAK.P
Packet Switching
Network layer offer two services
Connection oriented service
A connection is called virtual circuit
Connectionless service
The independent packets are called Data grams
102
DEEPAK.P
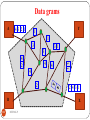
1. Data gram Network
Routes from source to destination are not worked out in
advance.
Packets takes different routes.
It does not maintain a table.
It is the responsibility of transport layer to re order
the Data grams
103
DEEPAK.P
Data grams
A
4 3 2 1
Y
1
1
3
3 1
3
4
4
2
B
104
4
3 1
4
2
2 4 3 1
X
DEEPAK.P
2. Virtual Circuit
Only one route from source to destination
When connection is established, it is used for all the traffic.
When connection is released, the virtual circuit is terminated.
Every router has to maintain a table.
105
DEEPAK.P
i.
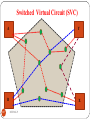
Switched Virtual Circuit (SVC)
It is similar to dial-up lines
A virtual circuit is created whenever it is needed.
106
DEEPAK.P
Switched Virtual Circuit (SVC)
107
A
Y
B
X
DEEPAK.P
ii.
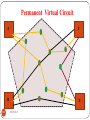
Permanent Virtual Circuit (PVC)
Virtual circuit is provided between two user on a
continuous basis.
108
DEEPAK.P
Permanent Virtual Circuit
109
A
Y
B
X
DEEPAK.P
Data gram Vs Virtual circuit Network
Parameter
VC
Datagram
Circuit setup
Required
Not required
Addressing
Each packet contains a
short VC number
Each packet contains a source ,
destination address
Repairs
Easy to repair
Harder to repair
State
information
Table is required to hold
state information
Table is not required to hold state
information
Routing
Route is fixed. (Static
routing)
Routed independently(dynamic
routing)
Congestion
control
Easy
Difficult
110
DEEPAK.P
Message Switching
DEEPAK.P
111
3. Message switching
message switching is similar to packet switching,
where messages were routed one hop at a time.
No physical path is established in advance in between
sender and receiver.
When the sender has a block of data to be sent, it is
stored in the first switching office (i.e. router)
then forwarded later at one hop at a time.
112
DEEPAK.P
Message switching
113
DEEPAK.P
Layered Architecture
DEEPAK.P
114
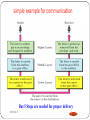
A simple example for communication
We use the concept of layers in our daily life.
As an example, let us consider two friends who
communicate through postal mail.
115
DEEPAK.P
simple example for communication
But 5 Steps are needed for proper delivery
DEEPAK.P
116
simple example for communication
V. Writing letter in a paper ( Raw Data)
IV. Put signature ,Fold the letter and put the letter in a cover
(Adding Header1, Compression etc)
III. Seal the cover& Put signature (Provides security,
Header2)
II. Dropped the letter in to mail box after fixing stamp
(Adding Header3& trailer1)
I. Postman collects the letter to the post office (
TRANSMISSION THROUGH A MEDIUM)
117
DEEPAK.P
simple example for communication
Sorting the letter at the post office (ROUTING)
I. Postman collects the letter from post office to the mail box
(Transmitting data bits)
II. Letter was taken from mail box to Home (Removing
header3& Trailer)
III. Open the cover& signature (Removes Header2)
IV. Take the letter from the cover (Removing Header1)
V. Reading letter ( Raw Data)
118
DEEPAK.P
Network architecture
Network
architecture is the overall design of a
network
The network design is divided into layers, each of
which has a function separate of the other layers
Protocol stack- The vertical (top to bottom)
arrangement of the layers; Each layer is governed by
its own set of protocols
Network architecture
Virtual Communication Between layers
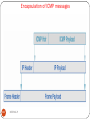
Message is generated by 5th layer
Layer 4 add header in front of message
Header include control information to send the message in the
right order.
Layer 3 breaks up the message in to small units called
packets
Layer 2 add header and trailer to packets.
Layer 1 transmits the raw data.
Issues in Layered Architecture
Design Philosophy of Layered Architecture
The complex task of communication is broken into
simpler sub-tasks or modules
Each layer performs a subset of the required
communication functions
Each layer relies on the next lower layer to perform
more primitive functions
Changes in one layer should not affect the changes
in the other layers
Helps in troubleshooting and identifying the problem
DEEPAK.P
122
Design issues for layers
Addressing
Identify sender and receiver
Direction of transmission
Simplex, half duplex, full duplex
Error control
Error detection and correction algorithms
Avoid loss of sequencing
Sequence number
Ability to receive long messages
Disassemble , transmit, reassemble
Use of multiplexing and de multiplexing
Share the channel
Network Models
DEEPAK.P
124
Need for Network Models
• Network communication is an extremely
complex task.
• Layer architecture simplifies the network design.
• The complex task of communication is broken
into simpler sub-tasks or modules
• Need cooperative efforts from all nodes involved
125
DEEPAK.P
Need for Network Models
• A standard model helps to describe the task of a
networking product or service
• Also help in troubleshooting by providing a
frame of reference.
The network management is easier due to the
layered architecture.
.
126
DEEPAK.P
Need for Layered Architecture
• Each layer works with the layer below and
above it
• Each layer provides services to next layer
127
DEEPAK.P
Who define Network Model?
• Need non-profit making organizations
• ISO - International Standards Organization
IEEE - Institute of Electrical & Electronic
Engineers
ITU - International Telecommunication Union
128
DEEPAK.P
OSI Model
DEEPAK.P
129
OSI Reference Model
The Open Systems Interconnection model is
a theoretical model that shows how
any two different systems can communicate
with each other.
130
DEEPAK.P
OSI Model
OSI Reference Model
The OSI model is now considered the primary Architectural
model for inter-computer communications.
The OSI model describes how information or data makes
its way from application programmes through a network
medium (such as wire) to another application programme
located on another network.
This separation into smaller more manageable functions is
known as layering.
131
DEEPAK.P
OSI Model
To standardize the design of communication system, the
ISO created the OSI model
ISO standard that covers all aspects of network
communications is the Open Systems Interconnection
(OSI) model.
Contains Seven layers
It describes the functions to be performed at each
layer
DEEPAK.P
132
OSI Model
First introduced this model in the late 1970s.
A layer model, Each layer performs a subset of the
required communication functions
Changes in one layer should not require changes in other
layers
DEEPAK.P
133
Important
ISO is the organization.
OSI is the model.
DEEPAK.P
134
OSI Model
Application
Presentation
Session
Transport
Network
Data Link
Physical
DEEPAK.P
135
The OSI 7-layer Model
All
People
Pizza
Seem
Sausage
To
Throw
Need
Not
Data
Do
Processing
136
Away
DEEPAK.P
Please
Peer-to-Peer Process using OSI
DEEPAK.P
137
Relationship of OSI layers
Virtual
Communication
Physical
Communication
138
DEEPAK.P
Data exchange using the OSI model
DEEPAK.P
139
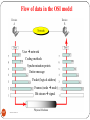
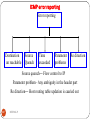
Flow of data in the OSI model
User network
Coding methods
Synchronization points
Entire message
Packet (logical address)
Frames (node node)
Bit stream signal
140
DEEPAK.P
OSI Model
OSI Model
141
DEEPAK.P
Protocols in a layered architecture
• Network communication is possible only if
machines speaking the same languages (protocols)
• Network communication is possible only if the
Protocol Stacks on two machines are the same
142
DEEPAK.P
Functions of Physical layer
DEEPAK.P
143
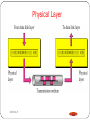
Physical Layer
DEEPAK.P
144
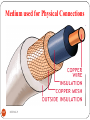
OSI Model – Physical Layer
This layer is the lowest layer in the OSI model.
It helps in the transmission of data between two machines
that are communicating through a physical medium, which
can be optical fibres, copper wire or wireless etc.
Hardware Specification:
The details of the physical cables, network interface cards,
wireless radios, etc are a part of this layer.
145
DEEPAK P
DEEPAK.P
145
5 May 2017
OSI Model – Physical Layer
Physical interface between devices
Handles the transmission of bits over a
communications channel
Choice of Wired / wireless medium
Data is converted into signals
Includes voltage levels, connectors, media choice
modulation techniques
EIA/TIA-232, RJ45, NRZ.
DEEPAK.P
146
Functions of Physical Layer
Make and Break physical connections.
Define voltages and data rate
Convert data bit in to electrical stream
Decide mode of transmission
Define physical topology
Line configuration
147
DEEPAK P
DEEPAK.P
147
5 May 2017
Medium used for Physical Connections
148
DEEPAK.P
Medium used for Physical Connections
149
DEEPAK.P
Note
The physical layer is responsible for movements of
individual bits from one hop (node) to the next.
DEEPAK.P
150
Functions of Data link layer
DEEPAK.P
151
OSI Model – Data Link Layer
• Means of activating, maintaining and deactivating
a reliable link
DEEPAK.P
152
Functions of Data Link Layer
Framing
Physical Addressing
Flow Control
Error Control
Access control
Synchronization.
DEEPAK.P
153
Access control in Data Link Layer
Sharing the access of the link
Based on access control IEEE split the data link layer in
to two is called IEEE project 802
Logical Link Control(LLC)
1.
•
2.
Establish and maintain link
Media Access control(MAC)
Provides shared access and communicates with network
Interface Cards
Establish a logical link between two computers
DEEPAK.P
154
Data Link Sub layers
Logical Link 802.1
Control
802.2
(LLC)
Media Access
Control (MAC)
155
DEEPAK.P
802.3
802.4
802.5
802.12
Note
The data link layer is responsible for moving
frames from one hop (node) to the next.
DEEPAK.P
156
Functions of Network layer
DEEPAK.P
157
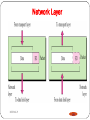
OSI Model – Network Layer
• Transport of information
• Responsible for creating, maintaining and ending network
connections
• Routing
• Transfers a data packet from node to node within the
network.
Examples :- IP, IPX, AppleTalk.
DEEPAK.P
158
Network Layer
DEEPAK.P
159
Functions of Network layer
1.
Routing of signals
2.
Divide outgoing message in to packets
3.
Act as network controller
4.
Logical Addressing
1.
160
Convert logical address to physical address
DEEPAK P
DEEPAK.P
160
5 May 2017
Note
The network layer is responsible for the delivery of
individual packets from the source host to the
destination host.
DEEPAK.P
161
Functions of Transport layer
DEEPAK.P
162
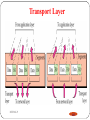
Transport Layer
Transport
– Exchange of data between end systems (end to end flow
control)
•
• Error free
•
• Sequencing
• Quality of service
Layer 4 protocols include TCP (Transmission Control
Protocol) and UDP (User Datagram Protocol).
DEEPAK.P
163
Services offered by Transport Layers
Connection oriented Service
Establish connection
Use the connection
Release the connection
Connection less Service
Similar to postal service
Each message is routed independently
Quality of service
Reliable--- No Data Loss, Using ACK
Un reliable
DEEPAK.P
164
Transport Layer
DEEPAK.P
165
Functions of Transport layer
166
1.
Transmission is parallel or single path
2.
Multiplexing
3.
Segmentation and re assembly
4.
Service point addressing
5.
Connection control
DEEPAK P
DEEPAK.P
166
5 May 2017
Note
The transport layer is responsible for the delivery
of a message from one process to another.
DEEPAK.P
167
Functions of Session layer
DEEPAK.P
168
OSI Model – Session Layer
Session
– Control of dialogues between applications
• Synchronization Points (backup points)
• Examples :- SQL, ASP(AppleTalk Session Protocol),
NETBIOS, RPC, PAP.
DEEPAK.P
169
Functions of Session layer
Controls logging off and logging on
User identification
Billing and session management
170
DEEPAK P
DEEPAK.P
170
5 May 2017
Note
The session layer is responsible for dialog control and
synchronization.
DEEPAK.P
171
Functions of Presentation layer
DEEPAK.P
172
OSI Model – Presentation Layer
1.
2.
3.
Translation
Data compression
Encryption
Examples :- JPEG, MPEG, ASCII, EBCDIC, HTML.
DEEPAK.P
173
Note
The presentation layer is responsible for translation,
compression, and encryption.
DEEPAK.P
174
Functions of Application layer
DEEPAK.P
175
OSI Model – Application Layer
Application
– Layer where the application using the network
resides.
– Common network applications include
remote login
file transfer
e-mail
web page browsing etc.
– Means for applications to access OSI environment
DEEPAK.P
176
Note
The application layer is responsible for providing
services to the user.
DEEPAK.P
177
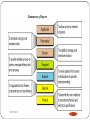
Summary of layers
DEEPAK.P
178
• To identify the language (protocol) of each layer,
identifier (header and trailer) are added to data
179
DEEPAK.P
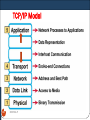
TCP/IP Model
DEEPAK.P
180
TCP/IP Model
It is used earlier by ARPANET
Developed by research foundation by US department of
defense
Later this architecture is known as TCP/IP model
It has two protocols
Transmission control protocol
Message is divided in to packets
Then Put in to IP packet
2. Internet protocol
Provide IP addressing
1.
DEEPAK.P
181
TCP/IP Protocol Suit
TCP/IP suite is the set of protocols that implement the
protocol stack on which the Internet runs.
It is sometimes called the Internet Model.
This model consists of five ordered layers
This model was developed prior to OSI model
DEEPAK.P
182
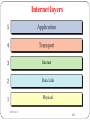
Internet layers
Internet
Data Link
Physical
DEEPAK.P
183
OSI vs TCP/IP
Application
Presentation
Session
Transport
Network
Data Link
Physical
DEEPAK.P
184
TCP/IP Model
185
DEEPAK.P
TCP/IP Model
Networking concept can also explained with the help of 4
layer protocol concept
It is a variation of TCP/IP 5 layer model
DEEPAK.P
186
Variation of TCP/IP
Application
Presentation
Session
Transport
Network
Data Link
Physical
DEEPAK.P
187
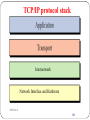
TCP/IP protocol stack
Internetwork
Network Interface and Hardware
DEEPAK.P
188
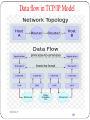
Data flow in TCP/IP Model
DEEPAK.P
189
TCP/IP Protocol Architecture Model
DEEPAK.P
190
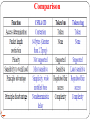
OSI vs TCP/IP
OSI
TCP/IP
7 Layer
4/5 layer
Transport layer guarantees delivery of
packets
Transport layer does not guarantees
delivery of packets
Separate session layer
No session Layer, Characteristics are
provided by transport layer
Separate presentation layer
No presentation Layer, Characteristics
are provided by application layer
Network layer offer connectionless
and connection oriented service
Network layer offer connectionless
service
Easy to replace the protocols
Not easy to replace protocols
General Model
TCP/IP cannot be used for any other
application
Some Protocols in TCP/IP Suite
DEEPAK.P
192
Some Protocols in TCP/IP Suite
DEEPAK.P
193
TCP/IP Frames
Header contains source and
destination IP addresses;
Upper level (i.e. transport)
protocol type
Header contains source and
destination physical addresses;
Upper level (i.e. network)
protocol type
IP
Header
Frame
Check
Sequence
Ethernet
Header
IP datagram is encapsulated in an Ethernet frame
DEEPAK.P
194
TCP/IP Frames
DEEPAK.P
195
TCP/IP Services
Two kinds of services: TCP & UDP.
TCP—Transmission Control Protocol, reliable
connection oriented transfer of a byte stream.
UDP—User Datagram Protocol, best-effort
connectionless transfer of individual messages.
DEEPAK.P
196
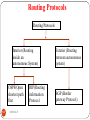
UNIT 2
197
DEEPAK.P
Network Classification/
Network configuration
DEEPAK.P
198
Network Classification
Networks may be classified according to a wide variety of
characteristics such as the
Transmission Technology
Scale
Medium used to transport the data
Topology
Organizational scope.
Communications protocol used
199
DEEPAK.P
Network Classifications
Network categorization according the following are
important
1.
Transmission Technology
2.
Scaling/ According to physical size
According to Transmission technology
200
1.
Broadcast Networks
2.
Point to point Networks
DEEPAK.P
Network Classifications
1.
Broadcast Networks
• Single communication channel shared by all the users
• Packets sent by any machine are received by all the
others (only one sender)
2.
Point to point Networks
• It consists of many connections between all machines
• It consists of dedicated links between each node
201
DEEPAK.P
Network Classifications
• Broadcast Networks
• Point to point Networks
202
DEEPAK.P
Network Classification
according to scaling
DEEPAK.P
203
Main Categories of networks
204
DEEPAK.P
Main Categories of Network
Local area network (LAN)
Metropolitan area network (MAN)
Links computers within a
building or group of buildings
Uses direct cables, radio or
infrared signals
Links computers within a major
metropolitan area
Uses fiber optic cables
Wide area network
Links computers separated by a
few miles or thousands of miles
Uses long-distance transmission
media
205
DEEPAK.P
Network Scaling
206
DEEPAK.P
Network Scaling
207
Inter processor
distance
Processors are located
in
networks
0.1 m
Same circuit board
Data flow machine
1m
Same system
Multi computer
10m
Same room
LAN
100m
Same building
LAN
1km
Same campus
LAN
10km
Same city
MAN
100km
Same country
WAN
1000km
Same continent
WAN
10000km
Same planet
Internet
DEEPAK.P
PAN
PAN
DEEPAK.P
208
Personal Area Networks (PAN)
• A PAN is a network that is used for communicating
among computers and computer devices (including
telephones) in close proximity of around a few meters
within a room.
• It can be used for communicating between the devices
themselves, or for connecting to a larger network such
as the internet.
• PAN’s can be
• Wired
• Wireless
•
209
DEEPAK.P
5/5/2017
Personal Area Networks (PAN)
210
DEEPAK.P
5/5/2017
Personal Area Networks (PAN)
PAN’s can be wired with a computer bus such as a universal
serial bus
USB (a serial bus standard for connecting devices to a
computer, where many devices can be connected
concurrently)
PAN’s can also be wireless through the use of bluetooth (a
radio standard for interconnecting computers and devices
such as telephones, printers or keyboards to the computer) or
IrDA (infrared data association) technologies
•
211
DEEPAK.P
5/5/2017
Personal Area Networks (PAN)
• Wireless PAN
212
DEEPAK.P
5/5/2017
LAN
DEEPAK.P
213
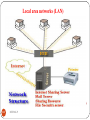
Local area networks (LAN)
A LAN is a network that is used for communicating among
214
computer devices, usually within an office building or group of
buildings or home
LAN’s enable the sharing of resources such as files or hardware
devices that may be needed by multiple users
Is limited in size, typically spanning a few hundred meters, and
no more than a mile
Is fast, with speeds from 10 Mbps to 10 Gbps
Requires little wiring, typically a single cable connecting to
each device
Has lower cost compared to MAN’s or WAN’s
DEEPAK.P
5/5/2017
MAN
DEEPAK.P
215
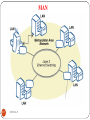
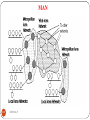
Metropolitan area network
A metropolitan area network (MAN) is a computer network
in which two or more computers or communicating devices
or networks which are geographically separated but in same
metropolitan city.
A MAN is optimized for a larger geographical area than a
LAN
A MAN typically covers an area of between 5 and 10 km
diameter.
216
DEEPAK.P
MAN
217
DEEPAK.P
Metropolitan area network
Network in a City is call MAN
It is larger than a LAN, but smaller than a WAN
It is also used to mean the interconnection of several LANs
by bridging them together.
This network is also referred to as a campus network
218
DEEPAK.P
MAN
219
DEEPAK.P
WAN
DEEPAK.P
220
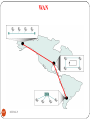
Wide area network (WAN)
A Wide Area Network is a network in which a large
geographical area of around several hundred miles to across
the globe
May be privately owned or leased
Also called “enterprise networks” if they are privately owned
by a large company
It can be leased through one or several carriers (ISPs-
Internet Service Providers) such as AT&T, Sprint, Cable and
Wireless
Can be connected through cable, fiber or satellite
Is typically slower and less reliable than a LAN
221
DEEPAK.P
WAN
222
DEEPAK.P
WAN
223
DEEPAK.P
Types of WANs
Internet
Backbone providers charge fees
to Internet Service Providers (ISP)
ISPs sell subscriptions to users
Public Data Network (PDN)
for-profit data
communications network
Not secure
Fees paid on a per-bytetransferred basis
Not ideal for businesses
Good security
High bandwidth
Private Data Network
Used by corporations, banks and governments
Not open to the public
Most secure type of WAN
224
Virtual private network- Lines are leased to a single
DEEPAK.P
company
LAN STRUCTURE
DEEPAK.P
225
LAN
When you have several computers, it can be convenient to
connect them to each other to create a local area
network (LAN).
A physical network structure is composed mostly of cables,
switches and workstations.
226
DEEPAK.P
LAN
There are two main types of local network architecture:
1.
Wired networks, based on the Ethernet technology, which
represent almost all local area networks.
Given that Ethernet networks generally use RJ45 cables, people
often talk of RJ45 networks;
2.
227
Wireless networks, which generally use the Wi-Fi
technology.
DEEPAK.P
5/5/2017
Local area networks (LAN)
228
DEEPAK.P
LAN Ethernet Structure
Ethernet LAN made up of several desktop systems and a
server attached to a coaxial cable.
229
DEEPAK.P
5/5/2017
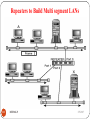
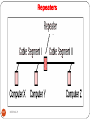
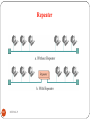
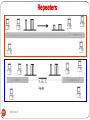
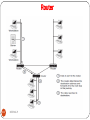
Repeaters to Build Multi segment LANs
230
DEEPAK.P
5/5/2017
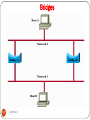
Bridges to Build Multi segment LANs
231
DEEPAK.P
5/5/2017
Local area networks (LAN)
Users can access software, data and peripherals
Require special hardware and software
Computers connected to a LAN are called workstations or
nodes
Different types:
Peer-to-peer
Client-server
232
DEEPAK.P
Local area networks (LAN)
Peer-to-peer
233
DEEPAK.P
Client-server
Introduction to Computer Networks
LAN Clients and Servers
In
a
client/server
network
arrangement, network services are
located in a dedicated computer
whose only function is to respond to
the requests of clients.
The server contains the file, print,
application, security, and other
services in a central computer that is
continuously available to respond to
client requests.
234
DEEPAK.P
Local area networks (LAN)
LAN’s can be either wired or wireless.
Twisted pair, coax or fiber optic cable can be used in wired
LAN’s
Nodes in a LAN are linked together with a certain topology.
These topologies include:
235
1.
Bus
2.
Ring
3.
Star
4.
Branching tree
DEEPAK.P
5/5/2017
LAN Topology
DEEPAK.P
236
LAN Topologies
Topologies resolve the problem of contention or users trying to
access the LAN at the same time
Collisions or corrupt data occurs when computers use the network at
the same time
Bus topology
Called daisy chain
Every workstation connected to a
single bus cable
Resolves collisions through
contention management
Difficult to add workstations
Star topology
Contains a hub or central wiring
concentrator
Easy to add workstations
Resolves collisions through
contention management
Ring topology
All workstations attached in a circular arrangement
A special unit of data called a token travels around the ring
Workstations can only transmit data when it possesses a token
237
DEEPAK.P
LAN Topologies
Bus Topology
Each node is connected one after the other (like christmas
lights)
Nodes communicate with each other along the same path
called the backbone
Backbone
238
DEEPAK.P
LAN Topologies
Ring Topology
The ring network is like a bus network, but the “end” of
the network is connected to the first node
Nodes in the network use tokens to communicate with
each other
Backbone
239
DEEPAK.P
LAN Topologies
Star Topology
Each node is connected to a device in the center of the
network called a hub
The hub simply passes the signal arriving from any
node to the other nodes in the network
The hub does not route the data
Hub
240
DEEPAK.P
LAN Topologies
Branching Tree Topology
241
DEEPAK.P
Components in LAN
DEEPAK.P
242
Components in a Local area networks
A node is defined to be any device connected to the network.
This could be a computer, a printer, a router, etc.
A Hub is a networking device that connects multiple segments
of the network together
A Network Interface Card (NIC) is the circuit board that has
the networking logic implemented, and provides a plug for the
cable into the computer (unless wireless).
In most cases, this is an Ethernet card inserted in a slot of the
computer’s motherboard
243
DEEPAK.P
5/5/2017
Components in a Local area networks
The Network Operating System (NOS) is the software
(typically part of the operating system kernel) that
communicates with the NIC, and enables users to share files
and hardware and communicate with other computers.
Examples of NOS include: Windows XP, Windows NT, Sun
Solaris, Linux, etc..
244
DEEPAK.P
5/5/2017
Hardware and software requirement for LAN
Hardware
Network interface card (NIC)Inserted into computer’s
expansion slot
Software
Operating system that
supports networking (Unix,
Linux, Windows, Mac OS)
Additional system
software
Hardware and software requirement for LAN
File server
A high speed, high capacity computer
Contains the network operating system ( Novell
Netware, Windows NT, XP Server)
Contains network versions of programs and large
data files
Advantage of LAN
1.
File transfers;
2.
Sharing of resources (internet connection sharing, printer
sharing, shared disks, etc.);
247
3.
Mobility (in the case of a wireless network);
4.
Discussion (mainly when the computers are remote);
5.
Network games.
DEEPAK.P
5/5/2017
Multiple Access
Communications
DEEPAK.P
248
Multiple Access Communication
The channel is employed to provide communication media
between a set of geographically distributed terminals.
Channel access method or multiple access method allows
several terminals connected to the same multi-point
transmission medium to transmit over it and to share its
capacity.
Multiple access schemes are used to allow many nodes to
share the link simultaneously.
249
DEEPAK.P
Multiple Access Communication
1.
2.
3.
FDMA
TDMA
CDMA
A channel-access scheme is also based on a multiple
access protocol and control mechanism, also known as
media access control (MAC).
250
DEEPAK.P
Data Link Control
251
DEEPAK.P
Data Link Control( DLC)
In the OSI networking model, Data Link Control (DLC) is
the service provided by the data link layer.
Network interface cards have a DLC address that identifies
each card.
DLC identifier (DLCI) that uniquely identifies the node on
the network.
For networks that conform to the IEEE 802 standards (e.g.,
Ethernet ), the DLC address is usually called the Media
Access Control (MAC) address.
252
DEEPAK.P
Data Link Sub layers
Logical Link 802.1
Control
802.2
(LLC)
Media Access
Control (MAC)
253
DEEPAK.P
802.3
802.4
802.5
802.12
Logical Link Control( LLC)
1. Logical Addressing
2. Provide Control Information
3. Control the Data
254
DEEPAK.P
Media Access Control( MAC)
1. Flow control
Link /Media control
2. Error Control
3. Access control
4. Synchronization
255
DEEPAK.P
Link/ Media Control
256
1.
Flow Control
Restrict the amount of data that the sender can send
2.
Error Control
a. Damaged frames
b. Lost frames
c. Lost Acknowledgement
DEEPAK.P
1.
257
DEEPAK.P
Flow Control
Performance Metrics and Delays
Transmission time (delay)
a. Time taken to emit all bits into medium
2. Propagation time (delay)
a. Time for a bit to traverse the link
3. Processing time (delay)
a. time spent at the recipient or intermediate node for
processing
4. Queuing time (delay)
a. waiting time at the queue to be sent out
1.
Model of Frame Transmission
transmission
time
propagation
time
Flow Control
Necessary when data is being sent faster than it can be
processed by receiver.
If sender sends faster than recipient processes, then
buffer overflow occurs
Flow control prevents buffer overflow
Flow control can be of two types
Stop & Wait
2. Sliding window
1.
260
DEEPAK.P
1. Stop and Wait Flow Control
This flow control mechanism forces the sender after
transmitting a data frame to stop and wait until the
acknowledgement of the data-frame sent is received.
1.
2.
3.
4.
5.
6.
Source transmits frame
Destination receives frame and replies with
acknowledgement (ACK)
Source waits for ACK before sending next frame
Destination can stop flow by not sending ACK
Works well for large frames
Inefficient for smaller frames
Stop and Wait Flow Control
Stop and Wait Flow Control
Generally large block of data split into small frames
Called “Fragmentation” and is used when
1.
2.
3.
4.
Limited buffer size at receiver
Errors detected sooner (when whole frame received)
On error, retransmission of smaller frames is needed
Prevents one station occupying medium for long periods
Channel Utilization is higher when
1.
2.
The transmission time is longer than the propagation time
Frame length is larger than the bit length of the link
2. Sliding Window Flow Control
The problem of “Stop and Wait” is not able to send multiple
packets
Sliding Window Protocol allows multiple frames to be in
transit
In this flow control mechanism both sender and receiver
agrees on the number of data-frames after which the
acknowledgement should be sent.
Sliding Window Flow Control
1.
Receiver has buffer of W (called window size) frames
2.
Transmitter can send up to W frames without ACK
3.
Each frame is numbered
4.
Sequence number bounded by size of the sequence
number field
5.
ACK includes number of next frame expected
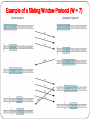
Sliding Window Flow Control (W = 5)
Example of a Sliding Window Protocol (W = 7)
3.
268
DEEPAK.P
Access Control
Access Control
Access Control means controlling the link when
computers transmit.
It is important in situations where more than one
computer wants to send data at the same time
over the same circuit.
The two main MAC approaches are
1. Controlled access
2. Contention Based / Polling
269
DEEPAK.P
1. Controlled Access
Controlled access works like a stop light, controlling
access to the shared resource of the network
circuit.
It is also used by some local area network protocols
(token ring, FDDI).
270
DEEPAK.P
2. Contention Based Access
Contention approaches, such as Ethernet, allow all the
computers to transmit whenever the circuit is
free.
Like two people in a group speaking at the same
time, their messages collide and have to be resent.
This means collisions can occur (more than one
computer transmitting at the same time).
271
DEEPAK.P
Contention Based Access
Contention approaches to media access control need to
have a way to sort out which computer is
allowed to transmit first after a collision occurs.
A mechanism used for this is polling
272
DEEPAK.P
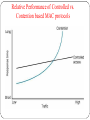
Relative Performance
Contention approaches tend to work better for smaller
networks with relatively low usage.
Since usage is low, the probability of collisions is also
low, but when volume is high their performance
deteriorates.
Controlled access tends to work better for networks
with high traffic volumes where the probability of
collisions is high and controlling access means the network
will be more efficiently used.
273
DEEPAK.P
Relative Performance of Controlled vs.
Contention based MAC protocols
Multiple Access
275
DEEPAK.P
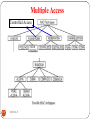
Multiple Access
Broadcast link is called multi access channel.
If two transmitter transmit at the same time , their
signal may interface or collide.
A method is needed to share the broadcast link and
avoid collision is called medium access control (MAC)
276
DEEPAK.P
Multiple Access
CHANNEL
277
DEEPAK.P
Multiple Access
When no: of stations uses a common link, we have to use
multiple access protocol.
Thee techniques or protocols are mainly used to deal with
multiple access problem
Random Access.
2. Controlled Access.
3. Channelization.
1.
278
DEEPAK.P
Multiple Access
Controlled Access
279
DEEPAK.P
1. Random Access Protocols
Random Access
There is no Control station.
Each station has the right to use the common medium.
The will be an increased probability of collision.
Random access protocols are
ALOHA
2. CSMA
3. CSMA/CD
4. CSMA/CA
1.
280
DEEPAK.P
2. Controlled Access Protocols
Controlled access
There will be a Control station.
Control station has the right to allocate the link to the
different users.
The probability of collision will be some what lesser.
Main Controlled access protocols are
a) Reservation
b) Round-Robin
281
DEEPAK.P
2. Controlled Access Protocols
Round Robin
In Round Robin techniques, each and every node is given
the chance to send or transmit by rotation.
282
DEEPAK.P
2. Controlled Access Protocols
Reservation
Centralized
b) Distributed
a)
283
DEEPAK.P
Controlled Access Protocols
Reservation
Centralized
Clients was prioritized so that they are polled more
frequently.
b) Distributed
Permission to access the link is carried out using a special
message called a poll.
a)
284
DEEPAK.P
Polling
285
DEEPAK.P
Polling
Polling, on computer networks, involves a server and
client.
With polling, the server periodically contacts each client
to see if it wants to transmit.
Clients transmit only after being asked by the server if
they want to send something.
286
DEEPAK.P
Polling
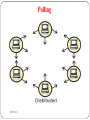
Polling may be
Centralized (often called hub polling)
2. Decentralized(distributed)/Roll call.
1.
In roll call polling, each client is checked in order to see if it
wants to transmit.
Clients can also be prioritized so that they are polled more
frequently.
In a decentralized polling scheme, each station knows its
successor in the polling sequence and send the poll directly to
that station.
287
DEEPAK.P
Polling
288
DEEPAK.P
Polling
Permission to transmit on the network is passed from
station to station using a special message called a poll.
In hub polling (also called token passing) one computer
starts the poll, sending message (if it has one) and then
passes the token on to the next computer.
This continues in sequence until the token reaches the first
computer, which starts the polling cycle all over again.
289
DEEPAK.P
Polling
290
DEEPAK.P
Polling
In hub polling, the polling order is maintained by a single
central station or hub.
When a station finishes its turn transmitting, it sends a
message to the hub, which then forwards the poll to the next
station in the polling sequence.
291
DEEPAK.P
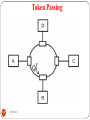
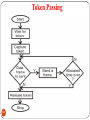
Token Passing
292
DEEPAK.P
Token Passing
293
DEEPAK.P
Token Passing
294
DEEPAK.P
Channelization
295
DEEPAK.P
Multiple Access Protocols
Channelization
Typical channelization methods include
1.
2.
3.
296
Frequency differentiation (FDMA)
Time division multiplexing (TDMA)
Code division multiple access (CDMA)
DEEPAK.P
Random Access
297
DEEPAK.P
Multiple Access
298
DEEPAK.P
Random Access
Random Access
There is no Control station.
Each station has the right to use the common medium.
The will be an increased probability of collision.
Random access protocols are
ALOHA
2. CSMA
3. CSMA/CD
4. CSMA/CA
1.
299
DEEPAK.P
Multiple Access
Multiple Access
Carrier Sense Multiple Access
CSMA/CD
300
DEEPAK.P
CSMA/CA
Multiple Access methods
ALOHA used a simple procedure called multiple access
(MA)
It was improved to develop Carrier Sense Multiple Access
(CSMA)
Carrier Sense" describes the fact that a transmitter uses
feedback from a receiver that detects a carrier wave before
trying to send.
OR
That is, it tries to detect the presence of an encoded signal
from another station before attempting to transmit.
301
DEEPAK.P
Carrier Sense Networks
A Network which adopts carrier sense is called carrier
sense networks
CSMA evolves two methods
1. CSMA/CD
2. CSMA/CA
302
DEEPAK.P
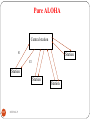
ALOHA
303
DEEPAK.P
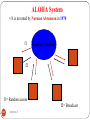
ALOHA System
It is invented by Norman Abramson in 1970
f1
Central Computer
f2
f1= Random access
f2= Broadcast
304
DEEPAK.P
ALOHA System
Contention System
Multiple user share a common link, leads to conflicts are
known as contention systems.
ALOHA is a Contention system
If a collision occurs, wait random amount of time then
retransmit; repeat until successful
Receiver send ACK for data
Detect collisions by timing out for ACK
305
DEEPAK.P
ALOHA System
306
DEEPAK.P
ALOHA System
ALOHA has two version
307
1.
Pure ALOHA/ Un slotted
a) Does not need time synchronization
2.
Slotted ALOHA
b. Need time synchronization
DEEPAK.P
Pure ALOHA
It allows any station to broadcast at any time.
If two signal collides, each station wait a random time
and tries again
Collisions are easily detected
When central station receives a frame it sends an ACK on a
different frequency.
It is very simple
308
DEEPAK.P
Pure ALOHA
Central station
F1
Station
F2
Station
Station
309
DEEPAK.P
Station
Pure ALOHA
Collision
0
310
DEEPAK.P
T
2T
Pure ALOHA System
311
DEEPAK.P
Slotted ALOHA
Developed by Roberts in 1972
Changing the protocol from continuous time to
slotted time
One frame can be sent in each slots.
All transmitters are synchronized so that all
transmissions start at the beginning of a slot
312
DEEPAK.P
Slotted ALOHA
Time is divided in to discrete intervals (T)
Each interval corresponds to one frame
0
313
DEEPAK.P
T
2T
Slotted ALOHA
314
DEEPAK.P
Slotted ALOHA
315
DEEPAK.P
Slotted ALOHA Vs Pure ALOHA
316
DEEPAK.P
CSMA
317
DEEPAK.P
CSMA
Link Utilization can be improved in CSMA
It operates on the principle of Carrier sensing
In this principle , a station listen to see the presence
of fames in the link.
CSMA can be divided in to three
Non Persistent
1- persistent
P- Persistent
318
DEEPAK.P
CSMA
Non Persistent
Station check the link.
If the station is busy, it has to wait for fixed interval of
time
After this time , it again check the status of the channel.
Wait randomly
Channel ?
Busy
Idle
319
DEEPAK.P
CSMA
1- persistent
It continuously monitor the link until it is idle.
It then transmits immediately.
Channel ?
Busy
Idle
320
DEEPAK.P
CSMA
P- persistent
All waiting stations are not allowed to transmit
simultaneously when the channel is idle.
Only P=1/N station can transmit while others will wait.
Channel ?
idle
Channel ?
Busy
321
>p
Wait a slot
Idle
Prob. outcome?
<p
Use back off process
DEEPAK.P
Busy
Station can transmit
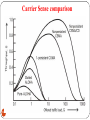
Carrier Sense Comparison
322
DEEPAK.P
CSMA/CD
323
DEEPAK.P
CSMA/CD
Carrier Sense Multiple Access with Collision
Detection (CSMA/CD)
It is widely used on LAN in MAC layer
CSMA/CD protocol can be considered as a refinement over
the CSMA scheme.
This refined scheme is known as Carrier Sensed Multiple Access with
Collision Detection (CSMA/CD) or Listen-While-Talk.
324
DEEPAK.P
CSMA/CD
The nodes continue to monitor the channel while
transmitting a packet and immediately stop
transmission when collision is detected and it transmits
jamming signal for a brief duration to ensure that all
stations know that collision has occurred.
Collision can be detected by comparing TX data with RX
data in Ethernet
325
DEEPAK.P
CSMA/CD
Listen to channel while transmitting data
If collision occurs, immediately stop sending, back-
off and retransmit
Sending a jam signal to all transmitters
Better performance than plain CSMA
Examples: Ethernet, Wi-Fi
326
DEEPAK.P
CSMA/CD
327
DEEPAK.P
Carrier Sense comparison
328
DEEPAK.P
CSMA/CD
CSMA/CD can be in one of three states
Contention, transmission, or idle.
Frame
Transmission
period
329
DEEPAK.P
Frame
Contention
period
Frame
Contention
Slots
Frame
Idle Periods
CSMA/CD Frame format
Pre amble(7Byte)-Alert receiver to coming Frame
SFD-Start Frame de limiter(1)-Beginning of Frame
DA-Destination Address(2 to 6)-Destination address of NIC
SA-Source Address(2 to 6) -Source address of NIC
L-Length of data field(2)-Length or type of PDU
Frame Data (Variable)-Actual Data
FCS/CRC-Frame check status(4)-Error correction
PAD- Adding extra bit to adjust the frame size
PR
330
DEEPAK.P
SFD
DA
SA
L
DATA
PAD
FCS
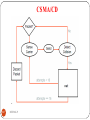
CSMA/CA
331
DEEPAK.P
CSMA/CA
Sender send a request-to-send (RTS) frame to receiver and
indicates the time needed to complete data transmission
Receiver send clear-to-send (CTS) frame, indicates time to
complete data transmission and reserves channel for the sender
Sender transmits the data and receiver responds with an ACK
frame, ensuring reliable transmission
RTS and CTS frames let other stations know of the data
transmission so that collision is avoided
Used by 802.11 wireless LAN
332
DEEPAK.P
CSMA/CA
Unlike CSMA/CD (Carrier Sense Multiple Access/Collision
Detect) which deals with transmissions after a collision has
occurred, CSMA/CA acts to prevent collisions before
they happen.
CSMA/CA differs from CSMA/CD due to the nature of the
medium, the radio frequency spectrum.
RTS-CTS-DATA-ACK to request medium
Random back off after collision is detected
333
DEEPAK.P
CSMA/CA
The main difference is the collision avoidance : on a wire, the
transceiver has the ability to listen before and while
transmitting and so to detect collisions.
Collisions are avoided using three strategies
Inter frame space (IFS)
The contention window
Acknowledgements
334
DEEPAK.P
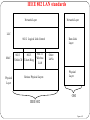
LAN standards
335
DEEPAK.P
LAN standards
LAN uses four architecture
Ethernet
Token Bus
Token Ring
Fiber Distributed Data Interface
These standards are the part of IEEE’s Project 802
336
DEEPAK.P
IEEE 802
IEEE 802 refers to a family of IEEE standards dealing
with local area networks and metropolitan area
networks.
This IEEE project covers the first two layers of the
OSI model and part of the third level.
IEEE 802 splits the OSI Data Link Layer into two
sub-layers named
Logical Link Control (LLC)
Media Access Control (MAC)
337
DEEPAK.P
IEEE 802
More specifically, the IEEE 802 standards are restricted to
networks carrying variable-size packets.
LLC
Upper sub layer
It will take care of Logical address, Control
information and data.
MAC
Lower sub layer
It contains Synchronization, Flag, Flow and Error
control specifications
338
DEEPAK.P
IEEE 802
IEEE 802
OSI Model
Other Layers
Other Network
802.1 Internetworking
Network
802.2 Logical link control
Data Link
802.3
CSMA
802.4
Token Bus
802.5
Token ring
Physical
339
DEEPAK.P
IEEE 802 LAN standards
Network Layer
Network Layer
LLC
802.2 Logical Link Control
MAC
Physical
Layer
802.3
CSMA-CD
802.5
Token Ring
802.11
Wireless
LAN
Various Physical Layers
Data Link
Layer
Other
LANs
Physical
Layer
OSI
IEEE 802
340
Figure 6.11
IEEE 802
PDU (Protocol Data Unit)
The data unit in LLC is called PDU
PDU contains 4 fields
Destination service access point (DSAP)
Source Service Access point (SSAP)
Control field
Information field
DSAP
341
DEEPAK.P
SSAP
Control
Information
IEEE 802 standards
IEEE 802.1
Management and Internetworking
IEEE 802.2
Logical Link Control(LLC)
IEEE 802.3
Ethernet (CSMA/CD)
IEEE 802.4
Token Bus
342
DEEPAK.P
IEEE 802 standards
IEEE 802.5
Token Ring
IEEE 802.6
MAN Networks
IEEE 802.7
Broad Band LAN
IEEE 802.8
Fiber Optic LANS
343
DEEPAK.P
IEEE 802 standards
IEEE 802.9
Integrated Data and Voice Networks
IEEE 802.10
Security
IEEE 802.11
Wireless Networks
344
DEEPAK.P
IEEE 802 standards
In LAN all the stations share common cable
IEEE adopted 3 mechanism for media access control
CSMA/CD(IEEE 802.3)
Token Bus (IEEE 802.4)
Token Ring (IEEE 802.5)
345
DEEPAK.P
IEEE 802.3
346
DEEPAK.P
IEEE 802.3(Ethernet)
The IEEE 802.3 standard is based on the ALOHA
system
IEEE standard 802.3 specifies the following characteristics of
Ethernet.
The medium is normally base band co-axial cable.
Bandwidth is 10Mbps
Cable segment length is 500m.
347
DEEPAK.P
IEEE 802.3(Ethernet)
It is a packet switching LAN technology.
Most widely used LAN protocol.
It uses CSMA/CD
It defines two categories
Base Band
Broad band
348
DEEPAK.P
Baseband &
Broadband LAN
349
DEEPAK.P
Base band LAN
The two ways to allocate the capacity of transmission
media are with
baseband and broadband transmissions.
Baseband devotes the entire capacity of the medium to
one communication channel.
The base band specifies a digital signal
350
DEEPAK.P
Base band LAN
Baseband LAN uses a single-carrier frequency over a
single channel.
Most LANs function in baseband mode.
Ethernet, Token Ring and Arcnet LANs use base band
transmission.
351
DEEPAK.P
Broad band LAN
Broadband enables two or more communication
channels to share the bandwidth of the
communications medium.
Broadband LANs use frequency-division
multiplexing on a coaxial cable to establish a
communications network
352
DEEPAK.P
Broad band Vs Base Band LAN
Baseband transmission is bidirectional but the
broadband is unidirectional.
No any frequency division multiplexing use in
baseband . where as frequency division
multiplexing use in broadband .
In baseband signal travel short distance and in
broadband signal can travel long distance.
Broad band specifies analog signal
353
DEEPAK.P
IEEE 802.3(Ethernet)
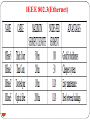
808802.3
802.3
Base Band
10 Base5,10 base 2,10 base
T,10 base F
354
DEEPAK.P
Broad Band
10 broad 36
IEEE 802.3(Ethernet)
The first number (10,1,100) indicates Data rates in MBPS
The last number indicates cable length in meters or type
of cable.
Ethernet uses coaxial cable as medium.
A device called Transceiver is used to establish connection
between computer and cable.
Cable
Transceiver
Hosts
355
DEEPAK.P
IEEE 802.3(Ethernet Generations)
Standard Ethernet
(10 Base 5{Thick Ethernet/Thicknet})
(10 Base 2{Thin Ethernet})
(10 Base T{Twisted Pair Ethernet})
(10 Base F{Fiber Ethernet})
Fast Ethernet
Gigabit Ethernet
10 Gigabit Ethernet
356
DEEPAK.P
Standard Ethernet(10 Base 5)
It uses bus topology
LAN is divided in to segments
Maximum segment length is 500 meters
Total length cannot exceed 2500 meters(5 segments)
Segment 1
Segment 5
………..
2.5m
2.5m
500 m
357
DEEPAK.P
500 m
2500 m
Standard Ethernet(10 Base 2)
It uses bus topology
It reduces cost , Installation is easy
Maximum segment length is 200 meters
Smaller capacity
N
358
DEEPAK.P
Standard Ethernet(10 Base T)
It uses Star topology
It uses Un shielded Twisted Pair cable(UTP)
Data rate is 10MBPS
Maximum length(Hub to station) of 100 meters
359
DEEPAK.P
Standard Ethernet(10 Base F)
It uses Star topology
It uses Fiber optic cables
Data rate is 10MBPS
Maximum length(Hub to station) of 2Km
Fiber optic cables
360
DEEPAK.P
IEEE 802.3(Ethernet)
361
DEEPAK.P
Ethernet Frame Format
Preamble
7 bytes
SFD
1 byte
Destination Address
6 bytes
Source address
6 bytes
P DA = 2 SA = 6
362
DEEPAK.P
L
Length PDU Data and
2 bytes
padding
0-46 bytes
DATA
FCS
CRC
4 bytes
Ethernet Frame Format
• Preamble: For synchronization
• Des. Add: Destination address
• Sour. Add: Source address
• FCS: Frame Check Sequence --- Error control
363
DEEPAK.P
Ethernet Address
Ethernet addresses are 48 bits long.
Ethernet addresses are governed by IEEE and are
usually imprinted on Ethernet cards when the cards
are manufactured.
364
DEEPAK.P
Ethernet Address
00 00 E2 15 1A CA
365
DEEPAK.P
Comparison
366
DEEPAK.P
Scheduling
Approaches to MAC
367
DEEPAK.P
Approaches to Media Sharing
Medium sharing techniques
Static
channelization
Partition medium
Dedicated allocation
to users
Satellite
transmission
Cellular Telephone
Dynamic medium
access control
Scheduling
Polling: take turns
Request for slot in
transmission
schedule
Token ring
Wireless LANs
Random access
Loose coordination
Send, wait, retry if
necessary
Aloha
Ethernet
Scheduling Approaches to MAC
Multiple users share the communication channel so a
scheme (medium sharing technique) must be devised
to prevent collision of packets
1. Reservation Systems
2. Polling Systems
3. Token Passing Systems
4. Static Channelization: TDMA and FDMA
369
DEEPAK.P
Reservation Systems
• Transmissions from stations are organized in cycles that have
variable length.
• Each cycle consists of a reservation interval followed by the
transmitted packets.
370
DEEPAK.P
Reservation Systems
A station uses its mini slot in the reservation interval to
broadcast its intention for transmission
371
DEEPAK.P
Modification in Reservation Systems
Variable length frames be accommodated if the
reservation slot for a station contains information
on the frame length
372
DEEPAK.P
Modification in Reservation Systems
More than one frame can be transmitted by a
station by modifying the reservation slot to
indicate number of frames to be transmitted per
station
373
DEEPAK.P
Network Connecting
Devices
374
DEEPAK.P
Network Connecting Devices
375
DEEPAK.P
Network Connecting Devices
Repeaters and Hubs--- To increase the coverable
distance
Bridges----- Traffic Management
It has some filtering capacity
Routers---- Routing to other networks
Gateway---- Provides security
Switches ---- Fast connecting
376
DEEPAK.P
Connecting Devices and OSI Model
377
DEEPAK.P
Network Connecting Devices
378
DEEPAK.P
Repeaters
379
DEEPAK.P
Repeaters
380
DEEPAK.P
Repeater
381
DEEPAK.P
Repeaters
A repeater is specific hardware designed to overcome
signal attenuation
It usually has only two ports and is designed to pure
boost or amplify a signal.
Ethernet hubs and repeaters operate at the Physical
Layer of the OSI Reference model
382
DEEPAK.P
Repeaters
383
DEEPAK.P
Hubs
384
DEEPAK.P
HUBS
hub are very similar to repeaters and is basically a
multi port repeater.
Repeater is usually used for the extension of the
length while hub is a simple connectivity gadget
that is used to broaden a network.
The central connecting device in a computer network is
known as a hub.
385
DEEPAK.P
HUBS
Hubs are also known as "multi-port repeaters" or "active
star networks”.
386
DEEPAK.P
Working of a HUBS
387
DEEPAK.P
HUB
When data packets arrives at hub, it broadcast them to
all the LAN cards in a network.
There are two types of hub
Active hub--- Repeats or re generate signal
Passive hub--- Used only for connection
388
DEEPAK.P
LAN BRIDGES
389
DEEPAK.P
Bridge
A bridge is a network communication device that is used to
connect one segment of the network with another
that uses the same protocol.
Bridges are fast devices for forwarding the data but
not as fast as the routers and switches.
A bridge when combined with the router, known as a
brouter.
Bridges has now replaced the switches and routers.
390
DEEPAK.P
Bridges
391
DEEPAK.P
Bridge
392
DEEPAK.P
Bridges
393
DEEPAK.P
Bridges
Bridges operate in the Data Link layer
Bridges are two types
Transparent Bridge
Routing Bridge
The duties of Transparent bridges are
Filtering frames
Forwarding
Blocking
394
DEEPAK.P
Bridges
395
DEEPAK.P
Transparent Bridges
396
DEEPAK.P
Transparent Bridges
A transparent bridge is a common type of bridge that
observes incoming network traffic to identify media access
control (MAC) addresses.
These bridges operate in a way that is transparent to all the
network's connected hosts.
Transparent bridges are implemented primarily in Ethernet
networks.
397
DEEPAK.P
Transparent Bridges
There are two types of Transparent Bridge Modes:
Store-and-Forward: Stores the entire frame and verifies the
CRC before forwarding the frame. If a CRC error is
detected, the frame is discarded.
Cut-Through: Forwards the frame just after it reads the
destination MAC address without performing a CRC check.
398
DEEPAK.P
Transparent Bridges
Transparent bridges save and maintain the source-route
addresses of incoming frames by listening to all the
connected bridges and hosts.
They use a transparent bridging algorithm to a accomplish
this. The algorithm has five parts:
Learning
Flooding
Filtering
Forwarding
Avoiding loops
399
DEEPAK.P
Transparent Bridges
Transparent bridges actively listen to traffic on each segment
on which it is attached.
When a transparent bridge encounters a frame that is to be
forwarded to a destination MAC it forwards it out a specific
port that it has associated with that MAC address.
400
DEEPAK.P
Transparent Bridges
If a bridge does not 'know' that MAC address (has no port
associated with that MAC), it sends the frame out all the
other ports on the bridge.
Frames are never forwarded out the port they are received
on.
401
DEEPAK.P
Source Route Bridges
402
DEEPAK.P
Source route Bridges
The route through the LAN internet is determined by the
source (originator) of the traffic hence this bridge is called as
source routing bridge.
The routing information field (RIF) in the LAN frame
header, contains the information of route followed by the
LAN network.
403
DEEPAK.P
Mixed-Media Bridging
404
DEEPAK.P
Mixed Media Bridges
Transparent bridges are found predominantly in
Ethernet networks, and source-route bridges (SRBs)
are found almost exclusively in Token Ring
networks.
Both transparent bridges and SRBs are popular, so it is
reasonable to ask whether a method exists to directly
bridge between them.
405
DEEPAK.P
Mixed Media Bridges
406
DEEPAK.P
LAN Switches
407
DEEPAK.P
Switch
A network switch (sometimes known as a switching hub) is a
computer networking device that is used to connect devices
together on a computer network.
Switches are another fundamental part of many networks
because they speed things up.
Switches allow different nodes (a network connection point,
typically a computer) of a network to communicate directly with
one another in a smooth and efficient manner.
A switch is considered more advanced than a hub because a
switch will only send a message to the device that needs or
requests it, rather than broadcasting the same message out of
each of its ports.
408
DEEPAK.P
Switch
A switch is a multi-port network bridge that processes and
forwards data at the data link layer (layer 2) of the OSI model.
Like a hub, a switch connects multiple segments of a network
together, with one important difference. Whereas a hub
rebroadcasts anything it receives on one port to all the others, a
switch makes a direct link between the transmitting device and
receiving device.
Any party not involved in that communication will not receive
the transmission. The benefit of a switch over a hub is that the
switch increases performance because it doesn’t suffer from the
wasted bandwidth of the extra transmissions.
409
DEEPAK.P
Switch
410
DEEPAK.P
Switch Working
411
DEEPAK.P
Switching Methods
412
DEEPAK.P
Router
413
DEEPAK.P
Router
414
DEEPAK.P
Comparison of Networking Devices
415
DEEPAK.P
Comparison of Networking Devices
416
DEEPAK.P
UNIT 3
Inter Networking
417
DEEPAK.P
Inter network
418
DEEPAK.P
Inter network
Internetworking is the practice of connecting a computer
network with other networks through the use of gateways that
provide a common method of routing information packets between
the networks.
The resulting system of interconnected networks is called an
internetwork.
Internetworking is a combination of the words inter ("between")
and networking;
The most common example of internetworking is the Internet
419
DEEPAK.P
Inter network
Inter networking can be classified in to two
Connection oriented or concatenated of virtual circuit
subnets
Connectionless or Datagram
420
DEEPAK.P
Connection oriented
Virtual circuit
421
DEEPAK.P
virtual circuit
•
422
A virtual network link is a link that does not consist
of a physical (wired or wireless) connection
between two computing devices but is implemented
using methods of network virtualization.
DEEPAK.P
concatenated of virtual circuit
A
X.25
Routers
ATM
Subnet 3
SNA
M
M
Subnet 1
B
Host
Subnet 2
Multi protocol router
(Gateway)
SNA-System Network Architecture
423
DEEPAK.P
virtual circuit Establishment
Subnet shows that the destination is remote destination and
builds a virtual circuit to the router nearest to the destination.
2. It then constructs a virtual circuit from that router to an external
gateway (multi protocol router).
3. This gateway notes down the existence of this virtual circuit in its
table and builds another virtual circuit to a router which is in the
next subnet.
4. This process continues until the destination host has been
reached.
1.
424
DEEPAK.P
virtual circuit Establishment
5. After building the virtual circuit, data packets begin to flow along
the path
425
DEEPAK.P
Advantage& Disadvantage virtual circuit
Advantage
Buffer can be reserved in advance
Shorter header can be used
Sequencing can be guaranteed
Drawbacks
There is no alternate path to avoid congestion
Router failure creates big problems
426
DEEPAK.P
Connection less
427
DEEPAK.P
Datagram Internetworking
Datagram packets
Path 1
M
M
A
Routers
Subnet 3
Datagram packets
M
M
Subnet 1
B
Path 2
Host
Subnet 2
428
DEEPAK.P
Multi protocol router
(Gateway)
Datagram Internetworking
The packets that are forwarded across the Internet are known as IP
datagrams
An IP datagram consists of a header and a payload
The header contains information that allows Internet routers to
forward the datagram from the source host to the destination host
429
DEEPAK.P
Datagram Internetworking
Header contains all information needed to deliver datagrams to
destination computer
Destination address
Source address
Identifier
Other delivery information
Router examines header of each datagram and forwards datagram
along path to destination
430
DEEPAK.P
Advantage& Disadvantage Datagram
Advantage
Higher Bandwidth
Deal with congestion in a better way
It is robust in Router failure
Drawbacks
No guarantee of packets
Addressing is difficult
Longer header is needed
431
DEEPAK.P
Tunneling
432
DEEPAK.P
Tunneling
It is used when source and destination networks of same type
are to be connected through a network of different type.
Consider an ethernet network to be connected to another
ethetnet through a WAN
The task is send on IP packet from host A of Ethernet 1 to the host B of
ehernet 2 wia a WAN.
In this example, the IP packet do not have to deal with WAN.
433
DEEPAK.P
Tunneling
The host A&B do not have to deal with WAN
The multiprotocol routers M1 and M2 will have to understand about IP
and WAN packet.
Therefore WAN can be imagined to be equivalent to a big tunnel
extending between multiprotocol routers M1 and M2.
So this technique is called Tunneling
434
DEEPAK.P
Tunneling
WAN
HOST
A
Tunnel
M1
M2
HOST
B
Ethernet 1
Ethernet 2
IP
IP
WAN packet
Header
Ethenet Frame
IP packet is inside the payload field of WAN packet
435
DEEPAK.P
Sequence of events in Tunneling
436
1.
Host A construct a packet containing the IP address of host B
2.
It then inserts this IP packet in to ethernet frame.
3.
This frame is addressed to the multi protocol router M1.
4.
Host A then puts this frames on Ethernet.
5.
When M1 receives this frames, it removes IP packet, inserts it in the
IP payload packet of the WAN network layer packet and addresses the
WAN packet to M2.
6.
The multi protocol router M2 remeoves the IP packet and send it to
host B in an ethernet frame.
DEEPAK.P
Datagram forwarding
in IP
437
DEEPAK.P
IP forwarding Using Datagram
The IP forwarding algorithm, commonly known as IP
routing, is a specific implementation of routing for IP networks
and gives a more directed approach in forwarding datagram's
over a network.
In order to achieve a successful transfer of data the algorithm
uses a routing table to select a next-hop router as the next
destination for a datagram.
The IP address that is selected is known as the next-hop
address.
438
DEEPAK.P
Delivery of an IP datagram
Internetwork is a collection of LANs or point-to-point
links or switched networks that are connected by
routers.
439
DEEPAK.P
Datagram forwarding in IP
An IP network is a logical entity with a network number
We represent an IP network as a “cloud”
The IP delivery service takes the view of clouds, and ignores the
data link layer view
440
DEEPAK.P
Datagram
Packets at the network layer level are called datagrams
They are encapsulated in frames for delivery across
physical networks
Datagrams are formed by header and payload
Datagrams can have different sizes
– Header is fixed (20 bytes)
– Data area can contain between 1 byte and 65 KB
441
DEEPAK.P
Forwarding Datagrams
Header contains all information needed to deliver datagrams
to destination computer
Destination address
– Source address
– Identifier
– Other delivery information
Router examines header of each datagram and
forwards datagram along path to destination
442
DEEPAK.P
Networks and IP addressing
IP address:
Network part + Host part
Network:
Any host can physically be reached by any other host without
intervening router
All hosts in the same network have the same network
number
443
DEEPAK.P
Networks and IP addressing
444
DEEPAK.P
Routing tables
Each router and each host keeps a routing table which tells the
router how to process an outgoing packet
Main columns:
1. Destination address: where is the IP datagram going
to?
2. Next hop: how to send the IP datagram?
3. Interface: what is the output port?
445
DEEPAK.P
Routing tables
Next hop and interface column can often be
summarized as one column
Routing tables are set so that datagrams gets closer to the its
destination.
446
DEEPAK.P
Delivery with routing tables
447
DEEPAK.P
IP Frame format
Header
Beginning of Data
Payload
448
DEEPAK.P
IP Header
449
DEEPAK.P
IP Header
ProtocolVersion(4 bits) : This is the first field in the protocol
header.
This field occupies 4 bits.
This signifies the current IP protocol version being
used.
Most common version of IP protocol being used is version 4 while
version 6 is out in market and fast gaining popularity.
450
DEEPAK.P
IP Header
Header Length(4 bits) : This field provides the length of the
IP header.
The length of the header is represented in 32 bit words.
Since this field is of 4 bits so the maximum header length
allowed is 60 bytes.
451
DEEPAK.P
IP Header
Type of service(8 bits) :
The first three bits of this field are known as priority bits
and are ignored as of today.
The next 4 bits represent type of service and the last bit is
left unused.
The 4 bits that represent TOS are : minimize delay, maximize
throughput, maximize reliability and minimize
monetary cost.
452
DEEPAK.P
IP Header
Total length(16 bits): This represents the total IP datagram
length in bytes.
Since the header length (described above) gives the length of
header and this field gives total length so the length of data and its
starting point can easily be calculated using these two fields.
Since this is a 16 bit field and it represents length of IP datagram
so the maximum size of IP datagram can be 65535 bytes.
453
DEEPAK.P
IP Header
Identification(16 bits):
This field is used for uniquely identifying the IP datagrams.
This value is incremented every-time an IP datagram is sent from
source to the destination.
This field comes in handy while reassembly of fragmented IP data
grams.
454
DEEPAK.P
IP Header
Flags(3 bits):
This field comprises of three bits.
While the first bit is kept reserved as of now, the next two bits
have their own importance.
The second bit represents the ‘Don’t Fragment’ bit.
The third bit represents the ‘More Fragment’ bit.
455
DEEPAK.P
IP Header
Fragment offset(13 bits):
In case of fragmented IP data grams, this field contains the offset(
in terms of 8 bytes units) from the start of IP datagram.
So again, this field is used in reassembly of fragmented IP
datagrams.
456
DEEPAK.P
IP Header
Time to live(8 bits) :
This value represents number of hops that the IP datagram will go
through before being discarded.
The value of this field in the beginning is set to be around 32 or 64
(lets say) but at every hop over the network this field is
decremented by one.
When this field becomes zero, the data gram is discarded. So, we
see that this field literally means the effective lifetime for a
datagram on network.
457
DEEPAK.P
IP Header
Protocol(8 bits) :
This field represents the transport layer protocol that handed over
data to IP layer.
This field comes in handy when the data is demultiplex-ed at the
destination as in that case IP would need to know which protocol
to hand over the data to.
458
DEEPAK.P
IP Header
Header Checksum(16 bits) : This fields represents a value that is
calculated using an algorithm covering all the fields in header
(assuming this very field to be zero).
This value is calculated and stored in header when IP data gram is
sent from source to destination and at the destination side this
checksum is again calculated and verified against the checksum
present in header.
If the value is same then the datagram was not corrupted else its
assumed that data gram was received corrupted. So this field is
used to check the integrity of an IP datagram.
459
DEEPAK.P
IP Header
Source and destination IP(32 bits each) :
These fields store the source and destination address respectively.
Since size of these fields is 32 bits each so an IP address
os maximum length of 32 bits can be used.
So we see that this limits the number of IP addresses that can be
used.
To counter this problem, IP V6 has been introduced which
increases this capacity.
460
DEEPAK.P
IP Header
Options(Variable length) : This field represents a list of options
that are active for a particular IP datagram.
This is an optional field that could be or could not be present.
If any option is present in the header then the first byte is
represented as follows :
461
DEEPAK.P
IP Header
In the description above, the ‘copy flag’ means that copy this
option to all the fragments in case this IP datagram gets
fragmented.
The ‘option class’ represents the following values : 0 -> control,
1-> reserved, 2 -> debugging and measurement, and 3 ->
reserved. Some of the options are given below :
462
DEEPAK.P
IP Header
463
DEEPAK.P
IP Header
Data: This field contains the data from the protocol layer that has
handed over the data to IP layer. Generally this data field contains
the header and data of the transport layer protocols. Please note
that each TCP/IP layer protocol attaches its own header at the
beginning of the data it receives from other layers in case of source
host and in case of destination host each protocol strips its own
header and sends the rest of the data to the next layer.
464
DEEPAK.P
ARP
465
DEEPAK.P
ARP
Address Resolution Protocol (ARP) is a
telecommunications protocol used for resolution of
network layer addresses into link layer addresses
ARP was defined by RFC (radio Frequency Committee) 826 in
1982
If a machine talks to another machine in the same network, it
requires its physical or MAC address.
ARP is used to convert an IP address to a physical
address such as an Ethernet address
466
DEEPAK.P
ARP
IP address of the destination node is broadcast and the
destination node informs the source of its MAC address.
Assume broadcast nature of LAN
Broadcast IP address of the destination
Destination replies it with its MAC address.
Source maintains a cache of IP and MAC address
bindings
467
DEEPAK.P
ARP
468
DEEPAK.P
ARP
A host wishing to obtain a physical address broadcasts
an ARP request onto the TCP/IP network.
The host on the network that has the IP address in the
request then replies with its physical hardware address.
469
DEEPAK.P
ARP
Send broadcast request
receive unicast response
470
DEEPAK.P
ARP
471
DEEPAK.P
ARP
Problem: Router A needs to forward an IP datagram to
router B (which is on the same Ethernet LAN)
Router A knows the IP address of B.
But the IP datagram must be encapsulated within an
Ethernet frame, whose Ethernet destination address is
the address of B’s NIC
How can A discover the Ethernet Address of B’s NIC?
472
DEEPAK.P
ARP
A uses the Address Resolution Protocol (ARP) to
discover B’s NIC Ethernet address. It goes like this:
A broadcasts an Ethernet frame on the LAN. The
payload of the frame is an ARP request: who has address
148.4.20.10 (B’s IP address).
All computers in the LAN hear the broadcast.
The computer whose IP address is 148.4.20.10 (B) replies
to A: my ethernet address is aa:bb:cc:dd:ee:ff.
473
DEEPAK.P
ARP
Now A has the ethernet address of B ’s NIC, and can send
the IP datagram to B encapsulated within an Ethernet
frame with destination address aa:bb:cc:dd:ee:ff.
474
DEEPAK.P
ARP request/reply In capsulation in Ethernet Frame
475
DEEPAK.P
ARP Header format
476
DEEPAK.P
ARP Header
Hardware type (HTYPE)
This field specifies the network protocol type.
Example: Ethernet is 1.
Protocol type (PTYPE)
This field specifies the internetwork protocol for which the ARP
request is intended.
For IPv4, this has the value 0x0800. The permitted PTYPE values
share a numbering space with those for Eather type
Hardware length (HLEN) Length (in octets) of a hardware
address.
Ethernet addresses size is 6.
477
DEEPAK.P
ARP Header
Protocol length (PLEN)
Length (in octets) of addresses used in the upper layer protocol.
(The upper layer protocol specified in PTYPE.) IPv4 address size
is 4.
Operation Specifies the operation that the sender is performing: 1
for request, 2 for reply.
Sender hardware address (SHA) media address of the sender.
478
DEEPAK.P
ARP Header
Sender protocol address (SPA) internetwork address of the sender.
Target hardware address (THA) media address of the intended
receiver.
This field is ignored in requests.
Target protocol address (TPA) internetwork address of the
intended receiver.
ARP protocol parameter values have been standardized and are
maintained by the Internet Assigned Numbers Authority (IANA).
479
DEEPAK.P
ICMP
480
DEEPAK.P
ICMP
Data delivery using IP datagram is the best delivery scheme
but it has two deficiencies.
Lack of error control
Lack of assistance mechanism.
These ICMP can compensate these deficiencies.
It is a companion to IP protocol
481
DEEPAK.P
ICMP
IGMP
IP
Network Layer
ICMP
ARP
RARP
482
DEEPAK.P
ICMP
Internet Control Message Protocol
It is a network layer protocol
Used mostly for error reporting at the IP level.
But its message is not passed directly to the data link layer
The messages are first encapsulated inside IP datagram before going
to the lower layer
483
DEEPAK.P
Encapsulation of ICMP messages
484
DEEPAK.P
ICMP
ICMP MESSAGE
ERROR REPORTING
485
DEEPAK.P
QUERY
ICMP
The error reporting message reports problems occurred at router
or a host.
The query message , which occurs in pairs , help a host or a network
manager to get specific information from a router or another host
ICMP does not correct errors , it simply reports them.
486
DEEPAK.P
ICMP error reporting
Error reporting
Destination
un reachable
Source
Quench
Time
exceeded
Parameter
problems
Re direction
Source quench--- Flow control to IP
Parameter problem– Any ambiguity in the header part
Re direction--- Host routing table updation is caaried out
487
DEEPAK.P
ICMP
For example, if the TTL of the IP datagram reaches 0
when it reaches a router, the datagram is dropped by the
router, and the router sends an ICMP message back to the
source of the datagram to inform it that the datagram was
dropped because its TTL reached 0 (Time Exceeded)
If a router does not know how to route an IP datagram, it
drops the datagram an send an ICMP message back to
the source (Destination unreachable).
488
DEEPAK.P
ICMP Messages with message number
489
DEEPAK.P
ICMP header
490
DEEPAK.P
ICMP header
Type field defines the type of message
Code field specifies reason for particular message
Checksum for error reporting
491
DEEPAK.P
DHCP
492
DEEPAK.P
DHCP
Dynamic Host Configuration Protocol
Allows a computer to obtain an IP address and other parameters
from a DHCP server
A DHCP server is a program running in some fixed computer in the
LAN that has been configured to assign IP addresses from a given
range to other computers in the LAN that request them
The DHCP server also provides things like default routes, and DNS
server addresses
493
DEEPAK.P
DHCP
DHCP requests are broadcasted within the local LAN (frame dest
ff:ff:ff:ff:ff:ff)
If the DHCP server is in a different LAN, the request won’t reach
that server.
One way around this is to configure some other computer in the
LAN as a dhcp relay agent : the relay will intercept the DHCP
request and forward it to the DHCP server on the other LAN
Simplifies management, as only one DHCP sever needs to be
configured for the entire network, rather than having to configure
separate DHCP servers for each LAN
494
DEEPAK.P
Subnetting
495
DEEPAK.P
Subnet
A sub network, or subnet, is a logically visible subdivision of an IP
network.
The practice of dividing a network into two or more networks is called
subnetting.
All computers that belong to a subnet are addressed with a common,
identical, most-significant bit-group in their IP address
496
DEEPAK.P
Subnet
Subnetting an IP Network can be done for a variety of reasons,
including organization, use of different physical media (such as
Ethernet, FDDI, WAN, etc.), preservation of address space, and
security.
The most common reason is to control network traffic.
497
DEEPAK.P
IP Packet
498
DEEPAK.P
IP Packet
499
DEEPAK.P
IP Packet
An IP packet has two fundamental components:
IP header
1.
Payload
2.
500
IP header contains many fields that are used by routers to forward the packet from
network to network to a final destination.
Contains layer 3 info
Fields within the IP header identify the sender, receiver, and transport protocol
and define many other Parameters.
Represents the information (data) to be delivered to the receiver by the sender.
Contains data & upper-layer info
DEEPAK.P
IP Versions
501
DEEPAK.P
IPV4
502
DEEPAK.P
IPV4
Internet Protocol is one of the major protocol in TCP/IP
protocols suite.
This protocol works at Network layer of OSI model and at
Internet layer of TCP/IP model.
Thus this protocol has the responsibility of identification of
hosts based upon their logical addresses and to route data
between/among them over the underlying network.
IPv4 is a connectionless protocol for use on packet-switched
networks.
503
DEEPAK.P
IPV4
Internet Protocol version 4 (IPv4) is the fourth version in
the development of the Internet Protocol (IP) Internet, and
routes most traffic on the Internet.
However, a successor protocol, IPv6, has been defined and is
in various stages of production deployment.
IPv4 is described in IETF publication RFC 791
It operates on a best effort delivery model, in that it does not
guarantee delivery, nor does it assure proper sequencing or
avoidance of duplicate delivery.
504
DEEPAK.P
IPV4
IPv4 uses 32-bit (four-byte) addresses, which limits the address
space to 4294967296 (232) addresses.
505
DEEPAK.P
IPv4 - Packet Structure
The encapsulated data is referred to as IP Payload.
IP header contains all the necessary information to deliver the
packet at the other end.
506
DEEPAK.P
IPv4 - Packet Structure
507
DEEPAK.P
IPv4 - Addressing
IPv4 supports three different type of addressing modes:
Unicast Addressing Mode:
In this mode, data is sent only to one destined host.
The Destination Address field contains 32- bit IP address of the
destination host.
Here client sends data to the targeted server
508
DEEPAK.P
IPv4 – Unicast Addressing
509
DEEPAK.P
IPv4 – Broadcast Addressing Mode:
In this mode the packet is addressed to all hosts in a network
segment.
The Destination Address field contains special broadcast address i.e.
255.255.255.255.
When a host sees this packet on the network, it is bound to process it.
Here client sends packet, which is entertained by all the Servers:
510
DEEPAK.P
IPv4 – Broadcast Addressing Mode:
511
DEEPAK.P
IPv4 – Multicast Addressing Mode:
This mode is a mix of previous two modes, i.e. the packet
sent is neither destined to a single host nor all the host on
the segment.
In this packet, the Destination Address contains special address which
starts with 224.x.x.x and can be entertained by more than one host.
512
DEEPAK.P
IPv4 – Multicast Addressing Mode:
513
DEEPAK.P
IPV6
514
DEEPAK.P
IPV6
Internet Protocol version 6 (IPv6) is the latest revision of the
Internet Protocol (IP), the communications protocol that
provides an identification and location system for
computers on networks and routes traffic across the
Internet.
IPv6 was developed by the Internet Engineering Task Force
(IETF) to deal with the long-anticipated problem of IPv4 address
exhaustion.
IPv6 is an Internet Layer protocol for packet-switched
internetworking and provides end-to-end datagram transmission
across multiple IP networks,
515
DEEPAK.P
IPV6
516
DEEPAK.P
IPV6 & IP V 4
517
DEEPAK.P
IPV6 & IP V 4
518
DEEPAK.P
Routing
519
DEEPAK.P
Routing
Routing means finding a suitable path for a packet from sender to
destination
520
DEEPAK.P
Routing
Routing is the main function of the network layer.
Network layer protocols responsible for deciding which output
line an incoming packet should be transmitted on.
Routing is usually performed by a dedicated device called a
router.
The path with lowest cost is considered as best.
521
DEEPAK.P
Routing
The routing algorithm is the part of a network layer software responsible
522
for deciding which output line a packet should be transmitted on
Each router stores information about forwarding in a routing table
– Initialized at system initialization
– Must be updated as network topology changes
A routing table contains a list of destination networks and next hop for each
destination
Note that a router has several IP addresses!
– One IP address per interface
DEEPAK.P
Classification of Routing
Routing schemes differ in their delivery semantics:
Unicast: delivers a message to a single specific node.
Broadcast: delivers a message to all nodes in the network.
Multicast: delivers a message to a group of nodes that have
expressed interest in receiving the message.
Anycast: delivers a message to any one out of a group of
nodes, typically the one nearest to the source.
Geocast: delivers a message to a geographic area.
523
DEEPAK.P
Classification of Routing
Routing can be classified in to two
Static Routing or Non adaptive
Do not consider measurement and estimate of current
traffic and topology on their routing decisions
Eg. Flooding, Flow based routing, Shortest path
Dynamic Routing or Adaptive
Change routing decisions to reflect changes in topology
Eg. Distance vector routing , Link state routing
524
DEEPAK.P
Routing Protocols
Routing Protocols
Interior (Routing
inside an
autonomous System)
OSPF(Open
shortest path
first
525
DEEPAK.P
RIP(Routing
information
Protocol
Exterior (Routing
between autonomous
system)
BGP (Border
gateway Protocol)
Desirable Properties of Routing
Algorithms
526
DEEPAK.P
Static Routing
527
DEEPAK.P
Flooding
It is a static algorithm
Every incoming packet is sent out on every
outgoing line except the one it arrived on.
It will generate vast no of duplicate packets.
528
DEEPAK.P
Flooding
529
DEEPAK.P
Application of Flooding
Military application
Distributed database application
Wireless network
530
DEEPAK.P
Selective Flooding
Variation of flooding is selective flooding
Do not send every incoming packet out on every
line.
It sends to the line that are going
approximately in the right direction.
531
DEEPAK.P
Flow-based Routing
Similar in spirit to minimum distance, but takes
traffic flow into consideration.
From the known average amount of traffic and the
average length of a packet you can compute the
mean packet delays using queuing theory.
Flow-based routing then seeks to find a routing
table to minimize the average packet delay
through the subnet.
532
DEEPAK.P
Flow-based Routing
Assume that traffic is huge from A to B
B
C
D
A
E
G
F
H
TAKE THE ROUTE AGEFC INSTEAD OF ABC
533
DEEPAK.P
Shortest path
Links between routers have a cost associated
with them.
In general it could be a function of
Distance
Bandwidth
Average traffic
Communication cost
Mean queue length
Measured delay
Router processing speed
534
DEEPAK.P
Shortest path algorithms
The shortest path algorithm just finds the least expensive
path through the network, based on the cost function.
Dijkstras algorithms
Bellman-ford algorithms
535
DEEPAK.P
Dynamic Routing
536
DEEPAK.P
Distance vector Routing
537
DEEPAK.P
Distance Vector Routing
In this routing each router 'telling the neighbors about the
whole network'.
Each router maintains a table called vector.
Each router periodically shares its knowledge about the
entire network with its neighbors.
The working principle of distance vector routing includes
Knowledge about the whole network
Routing only to neighbors
Information sharing at regular intervals
538
DEEPAK.P
Distance Vector Routing
539
DEEPAK.P
Distance Vector Routing
In distance vector algorithms, each router has to follow the
following steps:
It counts the weight of the links directly connected to it
and saves the information to its table.
In a particular period of time, the router sends its table to its
neighbor routers (not to all routers) and receives the
routing table of each of its neighbors.
Based on the information the router receives from its neighbors'
routing tables, it updates its own.
540
DEEPAK.P
Distance Vector Routing
Distance vector routing is also called
Distributed bellman- ford algorithm
Ford-Fulkerson algorithm
In distance vector routing Cost is based on
Hop count
Time delay
No of packets in a queue.
541
DEEPAK.P
Distance Vector Routing
542
DEEPAK.P
Distance Vector Routing
The cost of each link is set to 1.
Thus, the least cost path is simply the path with the fewer
hops.
The table below represents each node’s knowledge about the
distance to all other nodes:
543
DEEPAK.P
Distance Vector Routing
Initially, each node sets a cost of 1 to its directly connected
neighbors and infinity to all the other nodes.
Below is shown the initial routing table at node A:
544
DEEPAK.P
Distance Vector Routing
During the next step, every node sends a message to its
directly connected neighbors. That message contains the
node's personal list of distances.
545
DEEPAK.P
Distance vector Routing
546
DEEPAK.P
A
H
K
J
0
24
20
21
8
A
12
36
31
28
20
A
25
18
19
36
28
I
40
27
8
24
20
H
14
7
30
22
17
I
23
20
19
40
30
I
18
A
17
31
6
31
18
H
20
0
19
12
H
21
0
14
22
10
I
9
11
7
10
0
-
24
22
22
0
6
K
29
33
9
9
15
K
JA delay is 8
547
I
JI delay is
10
DEEPAK.P
JH delay is
12
JK delay is
6
New Routing Table for J
Distance Vector Routing
Problem (assume that cost is 1 for each link)
548
DEEPAK.P
Link state Routing
549
DEEPAK.P
Link state Routing
Link state algorithms are sometimes characterized informally as
each router 'telling the other router about its
neighbors'.
The concept has 5 parts
Discover it’s neighbors and learn their network address
Measure the delay or cost to each of it’s neighbors.
Construct a packet telling all it has learned.
Send this packet to all other routers.
Compute the shortest path to every other router.
550
DEEPAK.P
Link state Routing
neighbor to all routers
neighbor to all routers
neighbor to all routers
neighbor to all routers
neighbor to all routers
551
DEEPAK.P
neighbor to all routers
Routing for Mobile
Hosts
552
DEEPAK.P
Routing for mobile Hosts
Wireless hosts are often mobile, changing location over time
This mobility of a wireless host may cause the host to connect to
Different networks at different points of time.
553
DEEPAK.P
CIDR
554
DEEPAK.P
CIDR
555
DEEPAK.P
CIDR
556
DEEPAK.P