* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Today's Challenges in Lawful Interception
Remote Desktop Services wikipedia , lookup
Net neutrality law wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Wireless security wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Computer network wikipedia , lookup
Deep packet inspection wikipedia , lookup
Distributed firewall wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Airborne Networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
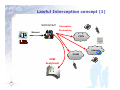
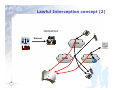
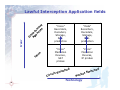
Today’s challenges in Lawful Interception C. Rogialli, October 11°, 2005 RIPE MEETING 51 - Amsterdam 1 Lawful Interception – a Definition Action (based on the law) performed by a network operator / access provider / service provider (NWO/AP/SvP), of making available certain information and providing that information to a law enforcement monitoring facility for investigation purposes. 2 Lawful Interception concept (1) NWO/AP/SvP Interception Provisioning Warrant PSTN Internet PLNM LEMF Assignment 3 Lawful Interception concept (2) NWO/AP/SvP Warrant PSTN PLNM 4 Internet Entities involved in Lawful Intercetion Government Operates in the interests of the nation; Sets the regulatory framework in which Lawful Interception is performed; Defines economical parameters for Lawful Interception activities. Operators Lawfully operate for the sake of their business and profit, almost totally driven by telecommunications; Withstand rules set by the government in terms of lawful interception as an unavoidable; Install proper devices to fulfil the relevant obligations; Law Enforcement Agencies 5 Operate in the name of crime fighting and nation security; Request lawful interception and define the real targets; Receive the communication data extracted by the operators; Need proper devices to playback and decode the intercepted traffic. A triviality… TELecom Companies and Government agencies are NOT created equal ! They have: Different Purposes Different Structure Different Knowledge Different Liabilities Different Activities Different Constraints So they need: Different Systems Different Approaches 6 …but LI requires cooperation ! Different Key Values For the government Agencies Overall solution effectiveness Return on investment (in investigative terms !) Adherence to existing operating procedures Low level of the technicalities to be handled “Surgical precision” For the Telecom operators Reliability Reduced maintenance and management hassles Low installation and running expenses Integration with the existing network Use of proven COTS hardware Possibility to document the obligation fulfilment 7 Lawful Interception Application fields User t n e s m e n i r c e n ov g e G A co l Te “Voice” Recorders, Decoders, Storage, Doc. production “Data” Recorders, Decoders, Storage, Doc. production “Voice” Mediation Devices, SS7 probes “Voice” Mediation Devices, IP probes d d ch e che t t i i Sw t Sw t i e u k Pac Circ Technology 8 LI in Circuit Switched and Packet Switched Networks (that is, why do we face different issues in the two worlds) 9 Once upon a time … … the mass telecommunications were only bound to the fixed PSTN network; no additional functionalities were provided by the handsets; the transport Network was unique in type and technology, it was based upon Circuit Switching, and the only type of payload transported was VOICE. In this “fairy tales” world, the interception: operated over a single network, with good-to-excellent results; had to deal with a single type of payload (typically ISDN voice over 64 kbps; due to the circuit switching technology, may e operated in any point of the network between the end points. PSTN/ISDN Network 10 …then it was the turn of fax, modems and mobiles Fax and Modems still use analog modulation over the CS network in order to transport images, data and internet services. The mass interception was therefore still possible with CS methodologies, with the only complication of demodulation. Internet PSTN/ISDN network Internet Service Provider PLMN GSM cell 11 GSM cell …and, suddenly, the security nightmare !!! A lot of mass telecommunication traffic today doesn’t traverse ANY part of the well-controlled Circuit Switched network ! 9 IP multimedia traffic between GPRS/UMTS mobile phones; 9 the traffic to and from Internet exchanged on high bandwitdh ISPs (ADSL, FTTH, cable…); 9 Telephone traffic between two REAL VoIP terminals, maybe connected to different VoIP operators. PSTN/ISDN network VoIP operator Internet Service Provider GSM/UMTS cell 12 Circuit S. Network 2.5G / 3G Mobile operator IP Network Internet Lawful interception compulsory services Depending on the local legislation, the Operator be requested to provide: may Interception based upon target identity It is requested to replicate ALL the traffic generated by a single, identifiable target among the multitude of users of the Operator itself. Investigative interception based upon parametric search It is requested massive filtering of the transported traffic in order to spot UNKNOWN users showing suspect behaviours (in example, exchanging mails containing specific keywords). Interception over Telecom operator’s services It is requested to replicate IN CLEAR any transaction made by an user towards a Service exercised by the telecom . Free access to the network 13 It is requested to guarantee proper network access to “black boxes” owned by the law enforcement agencies themselves. New issues connected with IP interception User Identification Whilst the correspondence between user credentials and user identity is rarely questioned in the “Voice” world, this is not necessarily true for the IP networks; Traffic dispersion The packet switching world poses new issues in terms of tapping points and capture efficiency; Mass cryptography In the IP world, cryptography is extensively used and at hand of everybody…. 14 User Identification Issues Availability information of reliable user No more anonymous access to the network will be provided by world’s telecom operators; Trusted identity systems Any mean shall be used to guarantee the correlation between user’s credentials and the physical person accessing the network; Availability of the user parameters at the capture point Any network feature hiding user’s identity at the capture point (e.g. NAT) shall be taken into account and suitable workarounds for the authority shall be provided. 15 Traffic dispersion issues Arpanet was originally conceived in order to deploy a military network able to survive huge, nation-level disasters… As a result, IP routing follows BY DESIGN several different routes even towards the same target address. As a consequence, the tapping point is not at all indifferent to the Lawful Interception Activities! 16 Tappin’ around the net 17 E-mail Probing in the access network Last Mile PSTN PSTN users TN PS ADSL users Corporate Users DSLAM 1 Gb overall Traffic; 2% is e-mail; LE ATM / IP WAN = 20 mb of packets to be deeply inspected PRA RAS/NAS ATM/IP switch il Ma 18 er rv Se POP Aggregation Router IP Backbone E-mail Probing in the Central Office Last Mile PSTN PSTN users TN PS ADSL users Corporate Users 1 Gb overall Traffic; DSLAM 98% is e-mail; LE = ATM / IP WAN 980 mb of packets to be deeply inspected (!!!) PRA RAS/NAS ATM/IP switch il Ma 19 er rv Se POP Aggregation Router IP Backbone Mass Cryptography issues Over the PSTN network, communication encryption was at disposal of few users; moreover, the few devices available offered backdoors for the agencies; Over the internet, encryption is at disposal of EVERYBODY. Not in any case backdoors are available; Whilst the operator may not be held responsible for user-level encryption, it may as well be obliged to provide in-clear interception of the services offered by itself. 20 The ISP in front of the authority. Viable options for the IP LI. 21 In-Band and Out-Band interception In-band interception implies the use of IIF inplemented in the network devices; it can be succesfully used with any kind of interception based upon user identity: Circuit based traffic; Packet traffic over mobile networks (es. GPRS); Packet traffic over carrier-grade modern switches in ISPs. Out-band interception imples the use of network probes; it is the only key when: Parametric (keyword) interception is requested; The authority doesn’t trust the operator itself or the operator’s personnel in investigative matters. 22 Typical Out-band Interception 10/100 Ethernet Delivery Router IPP IP-V Delivery NW (1) PMS MD (2) Email Server IPP PoP Web Server FTP Server (3) 10/100 Ethernet RP IPP (2) RADIUS Server Server Farm Core Network Interception of assigned IP Address PoP Warrant POI Access NW killer LIID Protocol No. Reference LEA Interception Duration Interception Criteria (username killer) 23 Transit peer Typical Out-band Interception 10/100 Ethernet Delivery Router IPP PMS Delivery NW IP-V MD IPP PoP Email Server Web Server FTP Server 10/100 Ethernet RP IPP IPP RADIUS Server Server Farm Core Network PoP Warrant POI Access NW killer LIID Protocol No. Reference LEA Interception Duration Interception Criteria (username = killer) 24 Transit peer Parametric Out-band Interception (2) 10/100 Ethernet Delivery Router IPP IP-V Delivery NW (1) PMS MD (2) (2) IPP PoP Email Server Web Server FTP Server (2) 10/100 Ethernet RP IPP RADIUS Server Server Farm Core Network PoP Warrant Access NW LIID Protocol No. Reference LEA Interception Duration Interception Criteria (keyword = bomb) 25 Transit peer Parametric Interception (Interception) 10/100 Ethernet Delivery Router IPP PMS ISDN/VPN IP: 212.127.0.5 write bomb MD IPP PoP VIP Email Server Web Server FTP Server RP IPP IPP 10/100 Ethernet RADIUS Server Server Farm Core Network PoP Warrant POI PSTN / ISDN ..I will place a bomb … 26 Username: tom IP: 212.127.0.5 LIID Protocol No. Reference LEA Interception Duration Interception Criteria (keyword = bomb) Transit peer Tactical probing vs. strategic interception (1) Tactical probes – a definition: devices that are installed at operator’s premises on a “per need” basis. Some “common sense” assertions about Tactical probing devices: small stealthy easily movable typically operated by agencies personnel dedicated to a few specific interception tasks at a time totally extraneous respect to the hosting network by definition 27 Tactical probing vs. strategic interception (2) Strategic Interception – a definition: An interception network permanently deployed at operator’s premises to serve any present or future interception request. Some “common sense” assertions about Strategic probing devices: solid integrated permanently connected to the network typically maintained by telco personnel dedicated to a huge spread of interception tasks at a time may be integrated with the hosting network 28 A duofold option for the ISP 1. Open the door to Agencies for Tactical Activities 9 as a pro, some responsibilities and costs are charged over the Agency rather than over the operator; 9 as a drawback, the operator will need to support (eventually upon network reconfiguration) the agency’s activities, on a per need basis ! 2. Make Room for Strategic interception systems 9 The operator will face some not recurring costs, only eventually covered by the governement; 9 However, the impact over the network will be minimized. 29 An only thing is important… …JUST PUT THE RIGHT PROBE IN THE RIGHT ENVIRONMENT ! 30 A Mixed Approach to LI 31 Classic approach – general principles ADSL users Corporate users PS TN Last Mile PSTN PSTN users DSLAM SGU IP over xxx ATM / IP WAN C.O. boundary PRA POP boundary Radius POP boundary Radius Pb (1x) IP Backbone IP Probe POP Aggregation Router 32 Mediation Device (32x) Classic Approach PROs Extensive capture allows many forms of parametric interception (e.g. Keyword search or e-mail addresses); The solution is totally unobtrusive and is completely impactless on the network architecture; The solution functionalities may be extended to effective network traffic monitoring as an added value. 33 Classic Approach CONs many probes to be placed; large investment needed; a lot of space (with access control requirements) to be reserved in the POP; tapping may be a NIGHTMARE, but the use of span ports may impact network performance; distributed and secure network connectivity between system elements to be provided; Some peering traffic is lost (i.e., the peering traffic closing on the same BRAS). 34 Hijack approach – general principles Last mile PSTN PSTN users TN PS ADSL users Corporate Users DSLAM IP over xxx C.O. boundary ATM / IP WAN POP boundary LI Config LI POP TT Radius Pb POP Aggregation Router IP Backbone PPP tunnel L2TP tunnel 35 (1x) ATM/IP switch Radius RAS/NAS Mediation Device IP Probe Hijack Approach PROs few probes to be placed; low investment needed; Few space with access control requirements may be reserved anywhere in the network; tapping is quite simple; Reduced need of secure network connectivity between system elements; No peering traffic is lost. 36 Hijack Approach CONs The possibility of interception are limited; parametric The solution needs a slight network redesign; Not suitable monitoring. 37 for extensive traffic A Service Approach to LI 38 Service interception approach Any time the telco operator offers some services on its own, it may be obliged to intercept them. Examples are: VoIP services; FTP/mail/webmail services; Videocall over PSTN line; … In ALL those cases, the operator will be asked to get rid of any interception aspect, including traffic encription ! So the solution may lay in Service interception rather than transport interception. 39 Service interception – an example Access Network RAS 40 Internet Service Network Firewall E-mail FTP MMS Autentication LI – A flexible approach 41 A flexible LI architecture is the key The answer to operators interception needs cannot be a “spot” solution for a specific interception issue or a specific service… … but rather an extensive approach covering – at least in perspective - all interception needs at a time. 42 IP Network Probing • Different probing devices are at disposal of the Network Engineer, granting overall coverage of any IP LI needs: • General-purpose IP Probes: • IP probes performing parametric interception may be placed in front of a network server (e.g. e-mail); • The interception is triggered basing upon service access, regardless the location of the network site accessing the “batch” service. • IP probes performing typical interception may be used to capture generic IP transactions basing upon IP address, CLI, or keyword; • A specific access probe may be needed to trigger the interception; • Access (RADIUS) Probes: • access probes are able to detect a “known” user accessing the network; • they provide trigger to IP probes as well as access logging capabilities. 43 Mediation Device It is the central server performing LI information handover from the provider’s domain to the LEA’s domain. It allows for a simpler and centralised LI network management, whilst optimising network resources usage. It grants a superior level of control in IP LI activities. It may be extended to support further capture methodologies, both out-band and in-band. 44 45 Ingress Interface Ix VoIP IIFs Ingress Interface Iy GPRS/IP Switching IIFs Ingress Interface Iz IP Probes Ingress Interface In Switching Telephony Probes Ingress Interface Ik IRI (HI2) MEDIATION FUNCTION Ingress Adaptation Layer GSM PSTN Voice IIFs LIID / LEMF and Config. Database CC (HI3) MEDIATION Egress Normalization and Synchrinization Layer Mediation Device flexible architecture Egress Interface Ex Long Term Storage Egress Interface Ey BroadBand IP LEMF Egress Interface Ez IP over ISDN/PSTN LEMF Egress Interface En Leased ISDN LEMF Egress Interface Ek Leased PSTN LEMF Provisioning and Maintenance System It is the central configuration device for the entire LI network. It allows the operation of the LI system using minimum personnel. By supporting different privilege levels, it is the “natural” Man-Machine Interface for: 46 Maintenance Operators (alarms and devices mgmt); LEA Operators (Warrants mgmt); Billing Opertors (where applicable). THANK YOU For any further info: Carlo Rogialli [email protected] 47