Database - NCNU Moodle 課程
... • Attribute, field, or column: characteristic or property of an entity • Relationship: an association between entities ...
... • Attribute, field, or column: characteristic or property of an entity • Relationship: an association between entities ...
Chapter 1 Slides
... Attribute, field, or column: characteristic or property of an entity Relationship: an association between entities ...
... Attribute, field, or column: characteristic or property of an entity Relationship: an association between entities ...
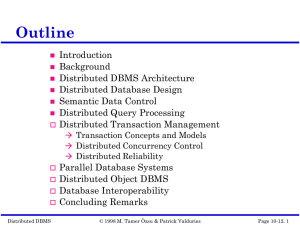
Chapter 1: Introduction
... ©Silberschatz, Korth and Sudarshan See www.db-book.com for conditions on re-use ...
... ©Silberschatz, Korth and Sudarshan See www.db-book.com for conditions on re-use ...
Python MySQL Database Access
... READ Operation on any database means to fetch some useful information from the database. Once our database connection is established, you are ready to make a query into this database. You can use either fetchone method to fetch single record or fetchall method to fetech multiple values from a databa ...
... READ Operation on any database means to fetch some useful information from the database. Once our database connection is established, you are ready to make a query into this database. You can use either fetchone method to fetch single record or fetchall method to fetech multiple values from a databa ...
CS245A3
... then deletes employee e where e.name = employee.name Whenever a new employee is inserted, its action deletes any existing employees with the same name. Rule actions can also be: arbitrary database operations transaction operations rule operations signals for the occurrence of user-defined ev ...
... then deletes employee e where e.name = employee.name Whenever a new employee is inserted, its action deletes any existing employees with the same name. Rule actions can also be: arbitrary database operations transaction operations rule operations signals for the occurrence of user-defined ev ...
Lecture Notes #1
... ● Should we split a table when it is too fat? ● Should we merge tables when they are too thin? Read: Chapter 3. Design Theory for Relational Databases ...
... ● Should we split a table when it is too fat? ● Should we merge tables when they are too thin? Read: Chapter 3. Design Theory for Relational Databases ...
CS211 Lecture: Java Database Connectivity (JDBC) revised 11/9
... (2) This is an example of the bridge design pattern. The purpose of a bridge is “to decouple an abstraction from its implementation so that the two can vary independently” ...
... (2) This is an example of the bridge design pattern. The purpose of a bridge is “to decouple an abstraction from its implementation so that the two can vary independently” ...
Should I Use an Embedded or External Database?
... choosing the right type of database for your specific needs are critical decisions that can have long term impact upon your eDiscovery projects, organization and clients. Hence, it’s key to identify your business, technology and end-user / administrator goals inside and outside of the system, then t ...
... choosing the right type of database for your specific needs are critical decisions that can have long term impact upon your eDiscovery projects, organization and clients. Hence, it’s key to identify your business, technology and end-user / administrator goals inside and outside of the system, then t ...
CIS115-Lecture 7 – MySQL Databases and PHP Integration
... Interacting with Databases We used XML pages statically to act as databases Relational Database: Think of an Excel document where each worksheet is a table within the document (database) ...
... Interacting with Databases We used XML pages statically to act as databases Relational Database: Think of an Excel document where each worksheet is a table within the document (database) ...
Introduction to Database Development
... The network address or name of the computer where the database is located The name of the specific database on that computer (e.g. the gcutours database) Introduction to Database Development ...
... The network address or name of the computer where the database is located The name of the specific database on that computer (e.g. the gcutours database) Introduction to Database Development ...
SQL Coding Best Practices – Focus on Performance
... engine reads procedure cache from the memory and executes the stored procedure faster. In case the stored procedure was written to be force recompile every time it executes, a new plan is generated before execution. Thus takes more time to execute the stored procedure. So avoid explicitly recompilin ...
... engine reads procedure cache from the memory and executes the stored procedure faster. In case the stored procedure was written to be force recompile every time it executes, a new plan is generated before execution. Thus takes more time to execute the stored procedure. So avoid explicitly recompilin ...
- W&L CS Web Application Server
... query); // Put the result in the result cache... This will lock this object // until it is removed from the result set cache. Returns an id that // uniquely identifies this result set in future communication. // NOTE: This locks the roots of the table so that its contents // may not be altered. resu ...
... query); // Put the result in the result cache... This will lock this object // until it is removed from the result set cache. Returns an id that // uniquely identifies this result set in future communication. // NOTE: This locks the roots of the table so that its contents // may not be altered. resu ...
Module 4: Managing Security
... Reanimating Tombstoned AD DS Objects You can reanimate deleted objects manually in AD DS when: • You do not have current AD DS backups in a domain where user accounts or security groups were deleted • The deleted object has not yet been scavenged from the Active Directory database • The deletion oc ...
... Reanimating Tombstoned AD DS Objects You can reanimate deleted objects manually in AD DS when: • You do not have current AD DS backups in a domain where user accounts or security groups were deleted • The deleted object has not yet been scavenged from the Active Directory database • The deletion oc ...
Part 1 Introduction
... And it provides a low-level description of the physical database, and an interface between the operating system's file system and the record structures used in higher levels of abstraction. At this level record types and methods of storage are defined, as well as how stored fields are represented. ...
... And it provides a low-level description of the physical database, and an interface between the operating system's file system and the record structures used in higher levels of abstraction. At this level record types and methods of storage are defined, as well as how stored fields are represented. ...
Part 1 Introduction
... And it provides a low-level description of the physical database, and an interface between the operating system's file system and the record structures used in higher levels of abstraction. At this level record types and methods of storage are defined, as well as how stored fields are represented. ...
... And it provides a low-level description of the physical database, and an interface between the operating system's file system and the record structures used in higher levels of abstraction. At this level record types and methods of storage are defined, as well as how stored fields are represented. ...
h6909.3-EMC Database Performance Tiering Assessment Service
... • Database tables and columns that are the most frequently used, and which are seldom used or dormant • Database objects that are used by which applications and users • The ranges of data values that are most frequently queried by business users, and which are never queried • The data that has the m ...
... • Database tables and columns that are the most frequently used, and which are seldom used or dormant • Database objects that are used by which applications and users • The ranges of data values that are most frequently queried by business users, and which are never queried • The data that has the m ...
Improving SQL Server Database Performance with DotHill
... High-end all-flash storage may have extreme performance figures, but it is expensive and generally unnecessary to support the application needs for small-to-medium business. The Dot Hill AssuredSAN 4824 storage array is intended to be affordable for these sized businesses, and can run enterprise app ...
... High-end all-flash storage may have extreme performance figures, but it is expensive and generally unnecessary to support the application needs for small-to-medium business. The Dot Hill AssuredSAN 4824 storage array is intended to be affordable for these sized businesses, and can run enterprise app ...
Database Trending
... For each table in the current database (including TOAST tables), the table OID, schema and table name, number of sequential scans initiated, number of live rows fetched by sequential scans, number of index scans initiated (over all indexes belonging to the table), number of live rows fetched by inde ...
... For each table in the current database (including TOAST tables), the table OID, schema and table name, number of sequential scans initiated, number of live rows fetched by sequential scans, number of index scans initiated (over all indexes belonging to the table), number of live rows fetched by inde ...
Chapter 1: Introduction
... Atomicity of updates (see page 23) Failures may leave database in an inconsistent state with partial updates carried out Example: Transfer of funds (say $1000) from one account (say $5000) to another (say $2000) should either complete or not happen at all. ...
... Atomicity of updates (see page 23) Failures may leave database in an inconsistent state with partial updates carried out Example: Transfer of funds (say $1000) from one account (say $5000) to another (say $2000) should either complete or not happen at all. ...