CS6302 DATABASE MANAGEMENT SYSTEMS L T P C 3 0 0 3
... DATABASE SECURITY: Data Classification-Threats and risks – Database access Control – Types of Privileges –Cryptography- Statistical Databases.- Distributed Databases-ArchitectureTransaction Processing-Data Warehousing and Mining-Classification-Association rulesClustering-Information Retrieval- Relev ...
... DATABASE SECURITY: Data Classification-Threats and risks – Database access Control – Types of Privileges –Cryptography- Statistical Databases.- Distributed Databases-ArchitectureTransaction Processing-Data Warehousing and Mining-Classification-Association rulesClustering-Information Retrieval- Relev ...
Transactions
... checkpoint) to identify all Xacts that were active, and all dirty pages in the buffer pool at the time of the crash. Redo: Redoes all updates to dirty pages in the buffer pool, as needed, to ensure that all logged updates are in fact carried out and written to disk. Undo: The writes of all Xacts tha ...
... checkpoint) to identify all Xacts that were active, and all dirty pages in the buffer pool at the time of the crash. Redo: Redoes all updates to dirty pages in the buffer pool, as needed, to ensure that all logged updates are in fact carried out and written to disk. Undo: The writes of all Xacts tha ...
BIS 3204 Database DB Programming
... Course Description: By the end of this course, the student will: Understand the use of SQLPlus and the SQL language with a fourth generation general purpose language to generate scripts, reports and database objects; Be able to write server side stored procedures and triggers; Apply the material in ...
... Course Description: By the end of this course, the student will: Understand the use of SQLPlus and the SQL language with a fourth generation general purpose language to generate scripts, reports and database objects; Be able to write server side stored procedures and triggers; Apply the material in ...
IS 331: Introduction to Database Systems
... The aim of the course is to introduce the basics of database systems, as well as the modeling, desgin and manipulation of relational databases. Students will gain the required knowledge to describe databases, their characteristics, functions, pros and cons. The course will also enable students to de ...
... The aim of the course is to introduce the basics of database systems, as well as the modeling, desgin and manipulation of relational databases. Students will gain the required knowledge to describe databases, their characteristics, functions, pros and cons. The course will also enable students to de ...
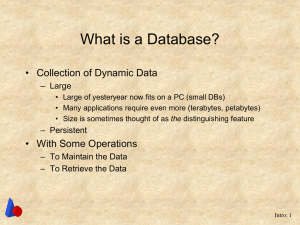
What is a Database? - Brigham Young University
... now fits on a PC (small DBs) Metadata • Many applications require even more (terabytes, petabytes) Datathought through • Query Size is sometimes of as the Metadata distinguishing feature ...
... now fits on a PC (small DBs) Metadata • Many applications require even more (terabytes, petabytes) Datathought through • Query Size is sometimes of as the Metadata distinguishing feature ...
Decentralized Database
... data secure, but this is more difficult on a network. It is the responsibility of the company to put security measures in place which keep their data secure. ...
... data secure, but this is more difficult on a network. It is the responsibility of the company to put security measures in place which keep their data secure. ...
DATA BASE MANAGEMENT SYSTEMS UNIT I Database System
... Overview of Transaction Management: The ACID Properties,Transactions and Schedules, Concurrent Execution of Transactions – Lock Based Concurrency Control,Deadlocks – Performance of Locking – Transaction Support in SQL. Concurrency Control: Serializability, and recoverability – Introduction to Lock M ...
... Overview of Transaction Management: The ACID Properties,Transactions and Schedules, Concurrent Execution of Transactions – Lock Based Concurrency Control,Deadlocks – Performance of Locking – Transaction Support in SQL. Concurrency Control: Serializability, and recoverability – Introduction to Lock M ...
A Database Management System (DBMS) for Monogenean
... Faculty of Science, University of Malaya, 50603 Kuala Lumpur, Malaysia The use of databases to store and manage data has become increasingly important in many fields. A well-designed database system is one of the most important tools for supporting biological data which includes a variety of differe ...
... Faculty of Science, University of Malaya, 50603 Kuala Lumpur, Malaysia The use of databases to store and manage data has become increasingly important in many fields. A well-designed database system is one of the most important tools for supporting biological data which includes a variety of differe ...
Study Guide for Mid
... Existence dependence – give an example of two entities in which one entity is existence dependent on the other Strong and weak relationships / identifying and non-identifying relationships – understand the difference in the way they are represented on an ERD diagram Weak and Strong entities Optional ...
... Existence dependence – give an example of two entities in which one entity is existence dependent on the other Strong and weak relationships / identifying and non-identifying relationships – understand the difference in the way they are represented on an ERD diagram Weak and Strong entities Optional ...
Overview of Databases and DBMS
... central to some enterprise that is managed by a Database Management System (DBMS) • Properties: – Essential to operation of enterprise (contains the only record of enterprise activity) – Valuable to the enterprise (Historical data can guide enterprise strategy, might be of interest to other enterpri ...
... central to some enterprise that is managed by a Database Management System (DBMS) • Properties: – Essential to operation of enterprise (contains the only record of enterprise activity) – Valuable to the enterprise (Historical data can guide enterprise strategy, might be of interest to other enterpri ...
Transaction Management (cont.)
... • If transaction had not committed at failure time, recovery manager has to undo (rollback) any effects of that transaction for atomicity. • Partial undo - only one transaction has to be undone. • Global undo - all transactions have to be undone. ...
... • If transaction had not committed at failure time, recovery manager has to undo (rollback) any effects of that transaction for atomicity. • Partial undo - only one transaction has to be undone. • Global undo - all transactions have to be undone. ...
Multi-user DB lecture
... Describe lost update and inconsistent read problems. List and briefly describe various locking ...
... Describe lost update and inconsistent read problems. List and briefly describe various locking ...
Chapter One (Introduction) Objectives
... No two tuples are the same No two attributes are the same The order of tuples are immaterial The order of attributes are immaterial There is an attribute or a collection of attributes which identifies tuples uniquely called Primary Key Value of attribute must be atomic ...
... No two tuples are the same No two attributes are the same The order of tuples are immaterial The order of attributes are immaterial There is an attribute or a collection of attributes which identifies tuples uniquely called Primary Key Value of attribute must be atomic ...
C O N T A I N E R I... I n t e l l i L a b...
... multiple materials, products or assets at any point in your process. When the IntelliLabel is created, the part number and its attributes are assigned to that IntelliLabel in the database (value, manufacturer, quantity, lot, serial, date, etc.). Drill down into the database; perform queries and run ...
... multiple materials, products or assets at any point in your process. When the IntelliLabel is created, the part number and its attributes are assigned to that IntelliLabel in the database (value, manufacturer, quantity, lot, serial, date, etc.). Drill down into the database; perform queries and run ...
Lecture Note 9
... • Consistent state only if both transactions are fully completed • DBMS doesn’t guarantee transaction represents real-world event ...
... • Consistent state only if both transactions are fully completed • DBMS doesn’t guarantee transaction represents real-world event ...
CSCI 526 001– Database Systems Spring 2013 Instructor:
... Master the technique for team play and teamwork for small scale database projects through brain storming and joint requirement planning. Learn and use effective tools for logical and physical database design and development. Perform data normalization process for effective data management. Write SQL ...
... Master the technique for team play and teamwork for small scale database projects through brain storming and joint requirement planning. Learn and use effective tools for logical and physical database design and development. Perform data normalization process for effective data management. Write SQL ...
Class 2 - Computer Science, NMSU
... – changes in the real-world are reflected correctly in the database – every time a real-world event happens, a transaction occurs to cause the corresponding changes in the database ...
... – changes in the real-world are reflected correctly in the database – every time a real-world event happens, a transaction occurs to cause the corresponding changes in the database ...