Red Hat enteRpRise Linux 6 seRveR: FeatuRes
... A new kernel task scheduler algorithm allows all tasks to get their fair share of CPU time, and reduces the amount of time that the kernel needs to schedule tasks. Improved hardware awareness allows the kernel to not only take better advantage of multi-core and NUMA architectures, but, when possible ...
... A new kernel task scheduler algorithm allows all tasks to get their fair share of CPU time, and reduces the amount of time that the kernel needs to schedule tasks. Improved hardware awareness allows the kernel to not only take better advantage of multi-core and NUMA architectures, but, when possible ...
GDLS VHMS Approach - SRI International
... – Provides Defense in Depth – Allows for flexibility in protocol implementation at upper layers – Identify and secure interfaces between layers ...
... – Provides Defense in Depth – Allows for flexibility in protocol implementation at upper layers – Identify and secure interfaces between layers ...
ppt
... SPIN is an experimental operating system that uses a non-traditional structure to provide extensibility, safety and performance. SPIN allows for modules to interact with the OS so as to gain performance benefits of specialization and retain the generalization of a generic OS. ...
... SPIN is an experimental operating system that uses a non-traditional structure to provide extensibility, safety and performance. SPIN allows for modules to interact with the OS so as to gain performance benefits of specialization and retain the generalization of a generic OS. ...
Buffer Overflow
... Buffer Overflow Basics Allocate more data into a program than it was designed to support Data that overflow to another region of the memory could be fatal No outbound checking in C++/C/Fortran ...
... Buffer Overflow Basics Allocate more data into a program than it was designed to support Data that overflow to another region of the memory could be fatal No outbound checking in C++/C/Fortran ...
ppt
... session) which are expensive to re-establish at a fresh server, you may use client IP affinity to insure that requests from the same client are repeatedly satisfied by the same server during this session. The trade off is that the load may be unevenly distributed. This organization is still robust t ...
... session) which are expensive to re-establish at a fresh server, you may use client IP affinity to insure that requests from the same client are repeatedly satisfied by the same server during this session. The trade off is that the load may be unevenly distributed. This organization is still robust t ...
Why write exploits?
... dll.BaseAddress = 0x77f00000 dll.Address['JMP ESP'] = 0x77F32836 dll.Address['JMP EDI'] = 0x77F2D148 dll.Address['CALL EAX'] = 0x77F1A9DD dll.Address['JMP [EBX]'] = 0x77F0174A dll.Address['CALL EBX'] = 0x77F01089 dll.Address['JMP ECX'] = 0x77F05372 dll.Address['JMP [EAX]'] = 0x77F08070 dll.Address[' ...
... dll.BaseAddress = 0x77f00000 dll.Address['JMP ESP'] = 0x77F32836 dll.Address['JMP EDI'] = 0x77F2D148 dll.Address['CALL EAX'] = 0x77F1A9DD dll.Address['JMP [EBX]'] = 0x77F0174A dll.Address['CALL EBX'] = 0x77F01089 dll.Address['JMP ECX'] = 0x77F05372 dll.Address['JMP [EAX]'] = 0x77F08070 dll.Address[' ...
Building an in-depth defense with Vectra and sandbox security
... command-and-control (C&C) servers that the attacker uses to remotely control each phase of the cyber attack. The attacker uses the C&C servers to send commands to and receive responses from hosts under his control as a result of downloading the exploit. Cyber attacks that are targeted differ from bo ...
... command-and-control (C&C) servers that the attacker uses to remotely control each phase of the cyber attack. The attacker uses the C&C servers to send commands to and receive responses from hosts under his control as a result of downloading the exploit. Cyber attacks that are targeted differ from bo ...
Lazy Garbage Collection of Recovery State for Fault – Tolerant
... A buffer is a contiguous allocated chunk of memory, such as an array or a pointer in C Buffer overflow occurs when a program or process tries to store more data in a buffer than it was intended to hold Buffer overflows are exploited to change the flow of a program in execution Buffer overflows are b ...
... A buffer is a contiguous allocated chunk of memory, such as an array or a pointer in C Buffer overflow occurs when a program or process tries to store more data in a buffer than it was intended to hold Buffer overflows are exploited to change the flow of a program in execution Buffer overflows are b ...
Incident Response and Honeypots
... • Problem: if defenders do not know what attacker is after, reduced protection domain may contain what the attacker is after. – Stoll created document that attacker d/led. – Download took several hours, during which the phone call was traced to Germany. ...
... • Problem: if defenders do not know what attacker is after, reduced protection domain may contain what the attacker is after. – Stoll created document that attacker d/led. – Download took several hours, during which the phone call was traced to Germany. ...
Security Considerations for RemotelyAnywhere
... After configuring RemotelyAnywhere, any user or group can be granted access to the remote administration interface. Not all administrators must be given access, and access is not necessarily limited to administrators. It is up to the administrator to configure RemotelyAnywhere to best suit their nee ...
... After configuring RemotelyAnywhere, any user or group can be granted access to the remote administration interface. Not all administrators must be given access, and access is not necessarily limited to administrators. It is up to the administrator to configure RemotelyAnywhere to best suit their nee ...
Chap 3
... trusted host, when in fact the victim is communicating with the attacker Well-known tool ...
... trusted host, when in fact the victim is communicating with the attacker Well-known tool ...
Intrusion Prevention System (IPS)
... I can assist further once you find the computer and perform the tasks listed below. This incident will be tracked through the Remedy system under the ticket listed in the subject line of this email. Please reference this ticket number on all future communication pertaining to the incident. ...
... I can assist further once you find the computer and perform the tasks listed below. This incident will be tracked through the Remedy system under the ticket listed in the subject line of this email. Please reference this ticket number on all future communication pertaining to the incident. ...
System Security - Wright State engineering
... Let us assume that Mallory, a cracker, not only can listen to the traffic between Alice and Bob, but also can modify, delete, and substitute Alice's and Bob's messages, as well as introduce new ones. Mallory can impersonate Alice when talking to Bob and impersonate Bob when talking to Alice. Here is ...
... Let us assume that Mallory, a cracker, not only can listen to the traffic between Alice and Bob, but also can modify, delete, and substitute Alice's and Bob's messages, as well as introduce new ones. Mallory can impersonate Alice when talking to Bob and impersonate Bob when talking to Alice. Here is ...
Windows Rootkit Overview
... User mode rootkits involve system hooking in the user or application space. Whenever an application makes a system call, the execution of that system call follows a predetermined path and a Windows rootkit can hijack the system call at many points along that path. One of the most common user mode te ...
... User mode rootkits involve system hooking in the user or application space. Whenever an application makes a system call, the execution of that system call follows a predetermined path and a Windows rootkit can hijack the system call at many points along that path. One of the most common user mode te ...
Countering Evolving Threats in Distributed Applications
... – Sentiment analysis for determining words conveying sense of change and urgency that attackers attempt to portray to the user ...
... – Sentiment analysis for determining words conveying sense of change and urgency that attackers attempt to portray to the user ...
Network Security - School of Computing and Engineering
... Viruses, trojans, etc. • Check for evidence of programs (and versions) that are susceptible to attack. • Test for outdated (or unchecked) virus ...
... Viruses, trojans, etc. • Check for evidence of programs (and versions) that are susceptible to attack. • Test for outdated (or unchecked) virus ...
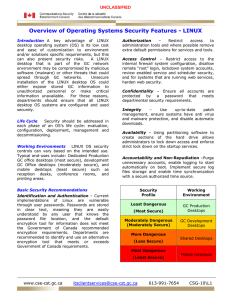
Overview of Operating Systems Security Features
... Overview of Operating Systems Security Features - LINUX Introduction A key advantage of LINUX desktop operating system (OS) is its low cost and ease of customization to environment and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the G ...
... Overview of Operating Systems Security Features - LINUX Introduction A key advantage of LINUX desktop operating system (OS) is its low cost and ease of customization to environment and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the G ...
EE-EmbeddedOperatingSystems-II
... Ref: http://developer.android.com/reference/org/apache/http/package-summary.html http://developer.android.com/reference/javax/net/ssl/package-summary.html http://www.ibm.com/developerworks/opensource/library/x-android/index.html ...
... Ref: http://developer.android.com/reference/org/apache/http/package-summary.html http://developer.android.com/reference/javax/net/ssl/package-summary.html http://www.ibm.com/developerworks/opensource/library/x-android/index.html ...
Curriculum Vitae
... ASM Eternity II puzzle Solver - code generation (using FreePascal) - multi threads to use multi core CPU - Linux kernel interfacing DNA Symantec programming contest – Organica Cell replication – DNA-like programming VBS-WSH Active Directory Query Tool and Application Launcher – Windows ASM, C++ 3D P ...
... ASM Eternity II puzzle Solver - code generation (using FreePascal) - multi threads to use multi core CPU - Linux kernel interfacing DNA Symantec programming contest – Organica Cell replication – DNA-like programming VBS-WSH Active Directory Query Tool and Application Launcher – Windows ASM, C++ 3D P ...
Windows vs.. Linux Security - Montclair State University
... based on (e.g., 2.2, 2.4, and 2.6) and the versions of all the packages each contains. ...
... based on (e.g., 2.2, 2.4, and 2.6) and the versions of all the packages each contains. ...
Section for introduction % \section{Introduction} Over the last several
... 88.6\% from the previous year \cite{Canalys11}. These phones are equipped with a rich set of hardware interfaces and software applications that allow personal and corporate users to interact with both the cyber and physical world through Internet access, email, SMS, and location-based services. To s ...
... 88.6\% from the previous year \cite{Canalys11}. These phones are equipped with a rich set of hardware interfaces and software applications that allow personal and corporate users to interact with both the cyber and physical world through Internet access, email, SMS, and location-based services. To s ...
Intrusion Detection Systems
... An attack that uses a brute-force technique of successively trying all the words in some large, exhaustive list. For example, an attack on an authentication service by trying all possible passwords; or an attack on encryption by encrypting some known plaintext phrase with all possible keys so that t ...
... An attack that uses a brute-force technique of successively trying all the words in some large, exhaustive list. For example, an attack on an authentication service by trying all possible passwords; or an attack on encryption by encrypting some known plaintext phrase with all possible keys so that t ...