Superluminal Quantum Models of the Photon and Electron
... Vision Value The transluminal quantum models of the photon and electron are anchored in the physics and mathematics of Dirac and Schroedinger. This model may be of heuristic value in suggesting new qualitative and quantitative approaches to: – Explaining Elementary (SM) particles ...
... Vision Value The transluminal quantum models of the photon and electron are anchored in the physics and mathematics of Dirac and Schroedinger. This model may be of heuristic value in suggesting new qualitative and quantitative approaches to: – Explaining Elementary (SM) particles ...
By confining electrons in three dimensions inside semiconductors, quantum dots... recreate many of the phenomena observed in atoms and nuclei,...
... Measurements of the distribution in peak heights can be made by altering the shape of the quantum dot to collect data on large numbers of different - but similar - quantum systems. Distributions measured in this way agree well with theory (figures 6b). As long as the dot generates chaotic dynamics, ...
... Measurements of the distribution in peak heights can be made by altering the shape of the quantum dot to collect data on large numbers of different - but similar - quantum systems. Distributions measured in this way agree well with theory (figures 6b). As long as the dot generates chaotic dynamics, ...
Topologically Ordered States and their Hamiltonians
... 3. In the WZWN case, the colored generalization is given by el=Σm=lkA(k,m,l)Pm, (eik)2 = (k+1)eik. It means in particular that standard TL algebra corresponds in the continuous limit to theories which are defined on coset spaces. ...
... 3. In the WZWN case, the colored generalization is given by el=Σm=lkA(k,m,l)Pm, (eik)2 = (k+1)eik. It means in particular that standard TL algebra corresponds in the continuous limit to theories which are defined on coset spaces. ...
Quantum mechanics and reality
... among physicists, the majority would vector, and even the state vector itself, profess membership in the conventional- is all in the mind. If this impression is ist camp, just as most Americans would correct, then what becomes of reality? claim to believe in the Bill of Rights, How can one treat SO ...
... among physicists, the majority would vector, and even the state vector itself, profess membership in the conventional- is all in the mind. If this impression is ist camp, just as most Americans would correct, then what becomes of reality? claim to believe in the Bill of Rights, How can one treat SO ...
Detection of Quantum Critical Points by a Probe Qubit
... observed in heavy fermion systems [4], common metals [5], and in Bose-Einstein condensates [6]. QPTs occur as a result of competing interactions and the different phases often show different types of correlations between the constituents, with correlation lengths that can become arbitrarily large. W ...
... observed in heavy fermion systems [4], common metals [5], and in Bose-Einstein condensates [6]. QPTs occur as a result of competing interactions and the different phases often show different types of correlations between the constituents, with correlation lengths that can become arbitrarily large. W ...
Analysis of the wave packet interference pattern in the Young experiment K. C
... There are two possible ways of evolution of the quantum state of a system, which is completely predictable and reversible, called unitary evolution, as well as the irreversible rapid process connected with measurements [1]. There have been a few attempts of bringing these two possible ways of evolut ...
... There are two possible ways of evolution of the quantum state of a system, which is completely predictable and reversible, called unitary evolution, as well as the irreversible rapid process connected with measurements [1]. There have been a few attempts of bringing these two possible ways of evolut ...
The classical entropy of quantum states=110ptJoint work with Elliott
... (’79) suggested a definition of their classical entropy based on the coherent state transform. He conjectured that this classical entropy is minimized by states that also minimize the Heisenberg uncertainty inequality, i.e., Gaussian coherent states. Lieb (’78) proved this conjecture and conjectured ...
... (’79) suggested a definition of their classical entropy based on the coherent state transform. He conjectured that this classical entropy is minimized by states that also minimize the Heisenberg uncertainty inequality, i.e., Gaussian coherent states. Lieb (’78) proved this conjecture and conjectured ...
QUANTUM HETERODOXY: REALISM AT THE PLANK LENGTH Q
... It is obvious that this probability will be less than one iff Ω is a proper subset of the support of the original ψ(x). We have already noted that the momentum wave function is the Fourier transform of the position wave function. We now point out an important fact about the supports of the two funct ...
... It is obvious that this probability will be less than one iff Ω is a proper subset of the support of the original ψ(x). We have already noted that the momentum wave function is the Fourier transform of the position wave function. We now point out an important fact about the supports of the two funct ...
notes
... Drawback: source must maintain two structures, hence needs additional complexity and overhead to maintain extra ...
... Drawback: source must maintain two structures, hence needs additional complexity and overhead to maintain extra ...
PROCESS PHYSICS:
... So measure speed in different directions relative to apparatus, which is on earth and surely moving through 3space. Earth orbit speed about sun is 30km/s Expect differences in speed to be very small and very difficult to detect: 1/100,000 Michelson used an interferometer which exploits wave natu ...
... So measure speed in different directions relative to apparatus, which is on earth and surely moving through 3space. Earth orbit speed about sun is 30km/s Expect differences in speed to be very small and very difficult to detect: 1/100,000 Michelson used an interferometer which exploits wave natu ...
1203.3054v2
... Impossibility of faster than light communication based on quantum correlations [7] led to the discovery of the no-cloning theorem [8, 9]. However, the NS principle leaves room for an approximate cloning. Imperfect or approximate 1-to-2 optimal quantum cloners have been shown to exist [10, 11] and th ...
... Impossibility of faster than light communication based on quantum correlations [7] led to the discovery of the no-cloning theorem [8, 9]. However, the NS principle leaves room for an approximate cloning. Imperfect or approximate 1-to-2 optimal quantum cloners have been shown to exist [10, 11] and th ...
SU(3) Multiplets & Gauge Invariance
... SU(2)- Spin added a new variable to the parameter space defining all state functions - it introduced a degeneracy to the states already identified; each eigenstaten became associated with a 2+1 multiplet of additional states - the new eigenvalues were integers, restricted to a range (- to + ) a ...
... SU(2)- Spin added a new variable to the parameter space defining all state functions - it introduced a degeneracy to the states already identified; each eigenstaten became associated with a 2+1 multiplet of additional states - the new eigenvalues were integers, restricted to a range (- to + ) a ...
Relativistic quantum field theory Nobel Lecture, December 11, 1965
... energy and momentum. But this is just the effect of the coordinate transformation that reflects all four coordinates. It is indeed true that the action principle does not retain its general form under either of the two transformations, the replacement of i with - i, and the reflection of all coordin ...
... energy and momentum. But this is just the effect of the coordinate transformation that reflects all four coordinates. It is indeed true that the action principle does not retain its general form under either of the two transformations, the replacement of i with - i, and the reflection of all coordin ...
Artificial Intelligence and Nature’s Fundamental Process Peter Marcer and Peter Rowlands
... know the detailed structure of how the environment is constructed, we know exactly what its totality must be. The series of potentials used to construct the operator may be iterative but the immediate zeroing gives us recursivity as well. A single fermion can only be ‘created’ if we simultaneously c ...
... know the detailed structure of how the environment is constructed, we know exactly what its totality must be. The series of potentials used to construct the operator may be iterative but the immediate zeroing gives us recursivity as well. A single fermion can only be ‘created’ if we simultaneously c ...
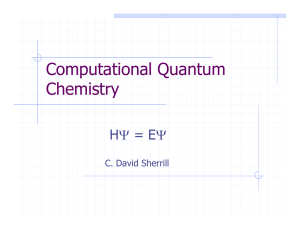
Computational Quantum Chemistry
... of O(N4) … things get much worse for larger molecules! The integral (µν|ρσ) is small unless the pairs (µ,ν) and (ρ,σ) have non-negligible overlap: leads to O(N2) scaling. (Advances in 1980’s). Recent work (1990’s) using multipole expansions is bringing the cost down to linear! ...
... of O(N4) … things get much worse for larger molecules! The integral (µν|ρσ) is small unless the pairs (µ,ν) and (ρ,σ) have non-negligible overlap: leads to O(N2) scaling. (Advances in 1980’s). Recent work (1990’s) using multipole expansions is bringing the cost down to linear! ...
Quantum key distribution
Quantum key distribution (QKD) uses quantum mechanics to guarantee secure communication. It enables two parties to produce a shared random secret key known only to them, which can then be used to encrypt and decrypt messages. It is often incorrectly called quantum cryptography, as it is the most well known example of the group of quantum cryptographic tasks.An important and unique property of quantum key distribution is the ability of the two communicating users to detect the presence of any third party trying to gain knowledge of the key. This results from a fundamental aspect of quantum mechanics: the process of measuring a quantum system in general disturbs the system. A third party trying to eavesdrop on the key must in some way measure it, thus introducing detectable anomalies. By using quantum superpositions or quantum entanglement and transmitting information in quantum states, a communication system can be implemented which detects eavesdropping. If the level of eavesdropping is below a certain threshold, a key can be produced that is guaranteed to be secure (i.e. the eavesdropper has no information about it), otherwise no secure key is possible and communication is aborted.The security of encryption that uses quantum key distribution relies on the foundations of quantum mechanics, in contrast to traditional public key cryptography which relies on the computational difficulty of certain mathematical functions, and cannot provide any indication of eavesdropping at any point in the communication process, or any mathematical proof as to the actual complexity of reversing the one-way functions used. QKD has provable security based on information theory, and forward secrecy.Quantum key distribution is only used to produce and distribute a key, not to transmit any message data. This key can then be used with any chosen encryption algorithm to encrypt (and decrypt) a message, which can then be transmitted over a standard communication channel. The algorithm most commonly associated with QKD is the one-time pad, as it is provably secure when used with a secret, random key. In real world situations, it is often also used with encryption using symmetric key algorithms like the Advanced Encryption Standard algorithm. In the case of QKD this comparison is based on the assumption of perfect single-photon sources and detectors, that cannot be easily implemented.