Noisy Storage talk
... verifiers accept message only if sent from prover’s position weak authentication: if message bit = 0 : perform Position Verification (PV) if message bit = 1 : PV with prob 1-q, send ? otherwise strong authentication by encoding message into balancedrepetition-code (0 00…0011…1 , 1 11…1100…0 ...
... verifiers accept message only if sent from prover’s position weak authentication: if message bit = 0 : perform Position Verification (PV) if message bit = 1 : PV with prob 1-q, send ? otherwise strong authentication by encoding message into balancedrepetition-code (0 00…0011…1 , 1 11…1100…0 ...
Fermionic quantum criticality and the fractal nodal surface
... Hypothesis: phenomenology of fermionic matter can be classified on basis of nodal surface geometry and ...
... Hypothesis: phenomenology of fermionic matter can be classified on basis of nodal surface geometry and ...
6 GU 2007 Quantum Illusions and Time
... Puzzle: how does our perception of travelling in time arise? R1 ...
... Puzzle: how does our perception of travelling in time arise? R1 ...
Wissink P640 – Subatomic Physics I Fall 2007 Problem Set # 1
... (b) We next consider the decay of the ω 0 meson to 2 pions. Because the ω, like the ρ, is a spin-1 particle, all of the angular momentum arguments presented in part a apply here as well for the 2π decay, so we must require the two outgoing pions couple to isospin Itot = 1. But the ω, unlike the ρ, i ...
... (b) We next consider the decay of the ω 0 meson to 2 pions. Because the ω, like the ρ, is a spin-1 particle, all of the angular momentum arguments presented in part a apply here as well for the 2π decay, so we must require the two outgoing pions couple to isospin Itot = 1. But the ω, unlike the ρ, i ...
Quantum Fourier Transform for Shor algorithm. PPT format.
... transform is a linear transformation on quantum bits, and is the quantum analogue of the discrete Fourier transform. 2. The quantum Fourier transform is a part of many quantum algorithms, notably: 1. Shor's algorithm for factoring 2. computing the discrete logarithm, 3. the quantum phase estimation ...
... transform is a linear transformation on quantum bits, and is the quantum analogue of the discrete Fourier transform. 2. The quantum Fourier transform is a part of many quantum algorithms, notably: 1. Shor's algorithm for factoring 2. computing the discrete logarithm, 3. the quantum phase estimation ...
Photon-number state on-demand source by cavity parametric
... resonance serves as storage for signal photons and the idler-wavelength resonance generates time separation between exiting idler photons, enabling photon-number-resolving detection. The counting of idler photons indicates the desired signal photon-number state, which can be released from the cavity ...
... resonance serves as storage for signal photons and the idler-wavelength resonance generates time separation between exiting idler photons, enabling photon-number-resolving detection. The counting of idler photons indicates the desired signal photon-number state, which can be released from the cavity ...
Transformation of Internal Waves at the Bottom Ledge
... h2 /h1 . Similar to surface waves [4, 6], the wavenumber increases when a wave enters into the shallower layer from the deep layer and decreases when a wave enters into the deeper layer from the shallower one. As one can see from figure 2, the longer is the incident wave, the greater is the change o ...
... h2 /h1 . Similar to surface waves [4, 6], the wavenumber increases when a wave enters into the shallower layer from the deep layer and decreases when a wave enters into the deeper layer from the shallower one. As one can see from figure 2, the longer is the incident wave, the greater is the change o ...
Lecture 6: QUANTUM CIRCUITS 1. Simple Quantum Circuits We`ve
... circuits containing the single qubit gates are shown in Figure 4.2. Each line in the circuit represents a wire in the quantum circuit. This wire does not necessarily correspond to a physical wire. Instead, it can correspond simply to the passage of time, or perhaps to a particle such as a photon - a ...
... circuits containing the single qubit gates are shown in Figure 4.2. Each line in the circuit represents a wire in the quantum circuit. This wire does not necessarily correspond to a physical wire. Instead, it can correspond simply to the passage of time, or perhaps to a particle such as a photon - a ...
Spectral Super-Resolution by Understanding Superposition
... Unfortunately, the real world’s observed interaction processes indicate that EM fields cannot be summed as in Eq.6 because they do not operate on each other by themselves even when they are physically superposed within the same space and time domain as we have underscored in the introduction. Someth ...
... Unfortunately, the real world’s observed interaction processes indicate that EM fields cannot be summed as in Eq.6 because they do not operate on each other by themselves even when they are physically superposed within the same space and time domain as we have underscored in the introduction. Someth ...
File
... • Bohr’s model was not considered to be a complete picture of the structure of the atom. – Bohr assumed that electrons do not radiate energy when they are in a stable orbit, but his model offered no explanation for this. – Another problem with Bohr’s model was that it could not explain why electrons ...
... • Bohr’s model was not considered to be a complete picture of the structure of the atom. – Bohr assumed that electrons do not radiate energy when they are in a stable orbit, but his model offered no explanation for this. – Another problem with Bohr’s model was that it could not explain why electrons ...
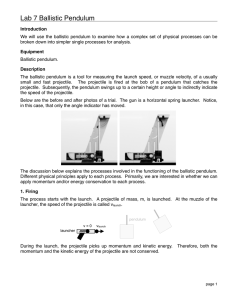
Lab 7 Ballistic Pendulum! !
... a launch angle of ±0.3°. Add this uncertainty to the range uncertainty above. Calculate the initial speed from this data. Include the uncertainty. Analysis Here is a case where two measurements of the same value are done two different ways without an expected value. How do we know if the two experim ...
... a launch angle of ±0.3°. Add this uncertainty to the range uncertainty above. Calculate the initial speed from this data. Include the uncertainty. Analysis Here is a case where two measurements of the same value are done two different ways without an expected value. How do we know if the two experim ...
7. Some Modern Applications of Quantum Mechanics
... Cryptography, the art of encrypting /sending a message and b) crypto analysis, the art of decrypting. In order to do this, an algorithm (also called a cryptosystem or cipher) is utilized for jumbling up a message with what is known as the “key” to produce a cryptogram indecipherable and, therefore, ...
... Cryptography, the art of encrypting /sending a message and b) crypto analysis, the art of decrypting. In order to do this, an algorithm (also called a cryptosystem or cipher) is utilized for jumbling up a message with what is known as the “key” to produce a cryptogram indecipherable and, therefore, ...
View
... A.1. Describe the SI unit system and convert units. A.2. Describe and analyze the translational and rotational motion in terms of inertial frames, position and angular position, inertia, velocity, acceleration, linear and angular momentum, force and torque, free-body diagram technique, and Newton’s ...
... A.1. Describe the SI unit system and convert units. A.2. Describe and analyze the translational and rotational motion in terms of inertial frames, position and angular position, inertia, velocity, acceleration, linear and angular momentum, force and torque, free-body diagram technique, and Newton’s ...
Chapter 7 The Quantum- Mechanical Model of the Atom
... proportional to its frequency. – Inversely proportional to its wavelength – The proportionality constant is called Planck’s Constant, (h), and has the value 6.626 × 10−34 J ∙ s. ...
... proportional to its frequency. – Inversely proportional to its wavelength – The proportionality constant is called Planck’s Constant, (h), and has the value 6.626 × 10−34 J ∙ s. ...
ΟΝ THE WAVE FUNCTION OF THE PHOTON
... It is believed that certain matrix elements of the electromagnetic field operators in quantum electrodynamics, in close analogy with nonrelativistic quantum theory of massive particles, may be treated as photon wave functions. In this paper, I would like to push this interpretation even further by a ...
... It is believed that certain matrix elements of the electromagnetic field operators in quantum electrodynamics, in close analogy with nonrelativistic quantum theory of massive particles, may be treated as photon wave functions. In this paper, I would like to push this interpretation even further by a ...