Hands-On Ethical Hacking and Network Security
... Best way to protect a network from SMB attacks ...
... Best way to protect a network from SMB attacks ...
Accepable Use and User Policies - Information Systems and Internet
... http://www.information-security-policies-and-standards.com ...
... http://www.information-security-policies-and-standards.com ...
NT Security Overview
... • Risk assessment is the process of finding out what data you have and how important is it to you. In addition to the importance of the data is the amount of damage you will incur if it is lost or compromised. • Another part of risk assessment deals with who within your organization will have access ...
... • Risk assessment is the process of finding out what data you have and how important is it to you. In addition to the importance of the data is the amount of damage you will incur if it is lost or compromised. • Another part of risk assessment deals with who within your organization will have access ...
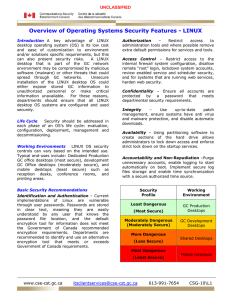
Overview of Operating Systems Security Features
... environment may be compromised by malicious software (malware) or other threats that could spread through GC networks. Unsecure installation of the LINUX desktop OS could either expose stored GC information to unauthorized personnel or make critical information unavailable. For these reasons, depart ...
... environment may be compromised by malicious software (malware) or other threats that could spread through GC networks. Unsecure installation of the LINUX desktop OS could either expose stored GC information to unauthorized personnel or make critical information unavailable. For these reasons, depart ...
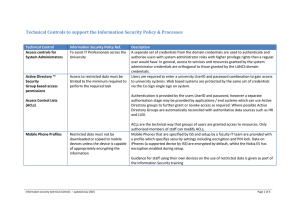
Technical Controls to support the Information
... Directory groups to further grant or revoke access as required. Where possible Active Directory Groups are automatically reconciled with authoritative data sources such as HR and LUSI. ...
... Directory groups to further grant or revoke access as required. Where possible Active Directory Groups are automatically reconciled with authoritative data sources such as HR and LUSI. ...
pps - AquaLab - Northwestern University
... Why does it matter? – Shipley’s ‘98 war dialers – 2.6m calls, 20K comps, 200 w/o security – On the Internet • Ping a range of IP addresses (43-bit, in dotted decimal notation w.x.y.z, each in [0,255]) , try telnet’ing to it • If you are in, get /etc/passwd and build stats on login names EECS 343 Ope ...
... Why does it matter? – Shipley’s ‘98 war dialers – 2.6m calls, 20K comps, 200 w/o security – On the Internet • Ping a range of IP addresses (43-bit, in dotted decimal notation w.x.y.z, each in [0,255]) , try telnet’ing to it • If you are in, get /etc/passwd and build stats on login names EECS 343 Ope ...
Web Application Security
... Attackers can tamper with any part of an HTTP request to try to bypass the site’s security mechanisms URL, query string, headers, cookies, form fields, hidden fields, etc. ...
... Attackers can tamper with any part of an HTTP request to try to bypass the site’s security mechanisms URL, query string, headers, cookies, form fields, hidden fields, etc. ...
Survey of online attacks on E-Commerce sites
... Web based attacks are considered to be the greatest threat to the online business as it is related to confidentiality, availability, and integrity. The motive behind e-commerce attack is significantly different then other attacks; Web based attacks focus on an application itself and functions on lay ...
... Web based attacks are considered to be the greatest threat to the online business as it is related to confidentiality, availability, and integrity. The motive behind e-commerce attack is significantly different then other attacks; Web based attacks focus on an application itself and functions on lay ...
Lecture 16 - Suraj @ LUMS
... something you know (passwords) something you have (smartcard) something you are (fingerprint) something you do (usage signature) ...
... something you know (passwords) something you have (smartcard) something you are (fingerprint) something you do (usage signature) ...
Networking Security
... • Attacker will explore how the Web application interacts with the back-end database by finding a user-supplied input string that will be part of a database query ...
... • Attacker will explore how the Web application interacts with the back-end database by finding a user-supplied input string that will be part of a database query ...
Chapter 4
... 4. Passwords should never be written down but instead must be committed to memory. Passwords must also be of a sufficient length and complexity. This creates the following password paradox: although lengthy and complex passwords should be used and never written down, it is very difficult to memorize ...
... 4. Passwords should never be written down but instead must be committed to memory. Passwords must also be of a sufficient length and complexity. This creates the following password paradox: although lengthy and complex passwords should be used and never written down, it is very difficult to memorize ...
L16_Security
... • Try default password used with standard accounts shipped with computer • Exhaustively try all short passwords • Try words in dictionary or a list of likely passwords • Collect information about users and use these items as passwords ...
... • Try default password used with standard accounts shipped with computer • Exhaustively try all short passwords • Try words in dictionary or a list of likely passwords • Collect information about users and use these items as passwords ...
Student Technologies Quick Start Guide
... To determine your username, go to https://wa.brunswickcc.edu and click on the “Account Information” link in the lower right corner and follow the prompts. Use only the username for all sites except email which requires the full email address. Accounts are created with a temporary password using the ...
... To determine your username, go to https://wa.brunswickcc.edu and click on the “Account Information” link in the lower right corner and follow the prompts. Use only the username for all sites except email which requires the full email address. Accounts are created with a temporary password using the ...
Dashlane -- Fact Sheet Express Login and Security Dashboard: As a
... information, enabling users to transact seamlessly and quickly across the web. Its patented click-to-pay technology – no typing required! – allows consumers to make buying as easy as possible, throughout the web. Dashlane’s check-out product does not require a custom build or partnership with any we ...
... information, enabling users to transact seamlessly and quickly across the web. Its patented click-to-pay technology – no typing required! – allows consumers to make buying as easy as possible, throughout the web. Dashlane’s check-out product does not require a custom build or partnership with any we ...
Security - NYU Stern School of Business
... • If you really want to erase thing: – Reformat the device(not always possible) – Delete files and save useless things until drive is full – Beware when your sell you used computer, there may be traces of sensitive information ...
... • If you really want to erase thing: – Reformat the device(not always possible) – Delete files and save useless things until drive is full – Beware when your sell you used computer, there may be traces of sensitive information ...
Securing the Network - Austin Community College
... On most systems, passwords are processed through an encryption algorithm that generates a one-way hash on passwords. You cannot reverse a one-way hash back to its original text. Most systems do not decrypt the stored password during authentication; they store the one-way hash. During the login proce ...
... On most systems, passwords are processed through an encryption algorithm that generates a one-way hash on passwords. You cannot reverse a one-way hash back to its original text. Most systems do not decrypt the stored password during authentication; they store the one-way hash. During the login proce ...
security
... • Produce fixed-length hash (~32 bits) from variable-length message – It is computationally infeasible to find a message with that hash; in fact one can't determine any usable information about a message with that hash, not even a single bit. – Biometrics usually work the same way! ...
... • Produce fixed-length hash (~32 bits) from variable-length message – It is computationally infeasible to find a message with that hash; in fact one can't determine any usable information about a message with that hash, not even a single bit. – Biometrics usually work the same way! ...
Intruders and password protection
... Proactive password checker techniques Markov model: generation of guessable passwords, this model shows a language consisting of an alphabet of three characters. The state of the system at any time is the identity of the most recent letter. The value on the transition from one state to another rep ...
... Proactive password checker techniques Markov model: generation of guessable passwords, this model shows a language consisting of an alphabet of three characters. The state of the system at any time is the identity of the most recent letter. The value on the transition from one state to another rep ...
Operating System Security Fundamentals
... Always provide a password to an account and force the user to change it at the first logon Protect passwords Do not use default passwords ...
... Always provide a password to an account and force the user to change it at the first logon Protect passwords Do not use default passwords ...
PPT - CS
... • Authentication service, based on a secure authentication server and on encryption • The server knows all passwords, but they are never transmitted across the network • Passwords are used to generate encryption keys. ...
... • Authentication service, based on a secure authentication server and on encryption • The server knows all passwords, but they are never transmitted across the network • Passwords are used to generate encryption keys. ...
Support: Ticket, Process, and Expectations
... Malware and Key Loggers can record keystrokes and report them to a 3rd party ...
... Malware and Key Loggers can record keystrokes and report them to a 3rd party ...
ITS_8_Security Vocab Answers
... are capable of transmitting themselves across networks bypassing many security systems. Password A series of characters that enables a user to access a file, program, or a computer or computer system. Passwords help ensure that unauthorized users do not access the computer. Ideally, the password sho ...
... are capable of transmitting themselves across networks bypassing many security systems. Password A series of characters that enables a user to access a file, program, or a computer or computer system. Passwords help ensure that unauthorized users do not access the computer. Ideally, the password sho ...
Operating System Security Fundamentals
... – Always provide a password to an account and force the user to change it at the first logon – Protect passwords – Do not use default passwords ...
... – Always provide a password to an account and force the user to change it at the first logon – Protect passwords – Do not use default passwords ...
attacks
... ◦ contains hashed representation of the user's password. ◦ a guessed password can be hashed using the same algorithm and compared to the stored hash version of the real password. ...
... ◦ contains hashed representation of the user's password. ◦ a guessed password can be hashed using the same algorithm and compared to the stored hash version of the real password. ...