lect3_classicsystems..
... basic mathematical skills, Cognitive Science, 2, pp.155-192 Brown, J.S. & VanLehn, K. (1980). Repair theory: A generative theory of bugs in procedural skills. Cognitive Science, 4, 379-426. Burton, R.R. (1982) Diagnosing bugs in a simple procedural skill, in (eds.) D.Sleeman and J.S.Brown, Intellige ...
... basic mathematical skills, Cognitive Science, 2, pp.155-192 Brown, J.S. & VanLehn, K. (1980). Repair theory: A generative theory of bugs in procedural skills. Cognitive Science, 4, 379-426. Burton, R.R. (1982) Diagnosing bugs in a simple procedural skill, in (eds.) D.Sleeman and J.S.Brown, Intellige ...
Data Averaging and Data Snooping
... Blum & Rivest 1992), i.e. in general, there is no algorithm capable of finding the optimal set of parameters which has computation time that is bounded by a polynomial in + , the input dimension. A typical compromise is to use an iterative optimization technique such as backpropagation (BP). In most ...
... Blum & Rivest 1992), i.e. in general, there is no algorithm capable of finding the optimal set of parameters which has computation time that is bounded by a polynomial in + , the input dimension. A typical compromise is to use an iterative optimization technique such as backpropagation (BP). In most ...
Nonnegative Matrix Factorization with Sparseness Constraints
... How can we combine these ideas? ...
... How can we combine these ideas? ...
Bayesian Spiking Neurons II: Learning
... more (or less) probable than average was xt when a spike was received from that synapse. Thus, the weights are positively or negatively incremented depending on whether the probability of xt tends to be larger or smaller than its running average at the moment of the synaptic input. Similarly, learni ...
... more (or less) probable than average was xt when a spike was received from that synapse. Thus, the weights are positively or negatively incremented depending on whether the probability of xt tends to be larger or smaller than its running average at the moment of the synaptic input. Similarly, learni ...
COMPRESSED SENSING WITH SEQUENTIAL OBSERVATIONS Massachusetts Institute of Technology
... solving (1) recovers the signal x∗ with high probability. This requires the knowledge of K, which may not be available, and only rough bounds on the scaling constants are known. Our approach is different - we compare the solutions at step M and M + 1, and if they agree, we declare correct recovery. ...
... solving (1) recovers the signal x∗ with high probability. This requires the knowledge of K, which may not be available, and only rough bounds on the scaling constants are known. Our approach is different - we compare the solutions at step M and M + 1, and if they agree, we declare correct recovery. ...
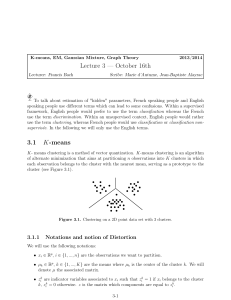
Lecture 3 — October 16th 3.1 K-means
... The intuition behind this approach is that it is a clever thing to well spread out the K initial cluster centers. At each iteration of the algorithm we will build a new center. We will repeat the algorithm until we have K centers. Here are the steps of the algorithm : • Step 0 : First initiate the a ...
... The intuition behind this approach is that it is a clever thing to well spread out the K initial cluster centers. At each iteration of the algorithm we will build a new center. We will repeat the algorithm until we have K centers. Here are the steps of the algorithm : • Step 0 : First initiate the a ...
ppt - MSDL
... SILK Pattern Recognition Engine (cont.) • Then the system looks for spatial relationships between the new component and other components in the sketch. • Finally, the result is passed to a rule system which tries to form a more complex widget. ...
... SILK Pattern Recognition Engine (cont.) • Then the system looks for spatial relationships between the new component and other components in the sketch. • Finally, the result is passed to a rule system which tries to form a more complex widget. ...
Transfer Learning using Computational Intelligence
... considered to be multi-task learning. If it optimizes performance on one domain, given training data that is from a different but related domain, it is considered to be transductive transfer learning or domain adaptation. Transfer learning and transductive transfer learning have often been used inte ...
... considered to be multi-task learning. If it optimizes performance on one domain, given training data that is from a different but related domain, it is considered to be transductive transfer learning or domain adaptation. Transfer learning and transductive transfer learning have often been used inte ...
Diagnosis of Pulmonary Embolism Using Fuzzy Inference System
... • Despite its name Fuzzy Logic is not nebulous, cloudy or vague. • It provides a very precise approach for dealing with uncertainty which is derived from complex human behavior. • Fuzzy Logic is so powerful, mainly because it does not require a deep understanding of a system or exact and precise num ...
... • Despite its name Fuzzy Logic is not nebulous, cloudy or vague. • It provides a very precise approach for dealing with uncertainty which is derived from complex human behavior. • Fuzzy Logic is so powerful, mainly because it does not require a deep understanding of a system or exact and precise num ...
Maclennan-chap7-Ada.ppt
... package Stack1 is new Stack(100); package Stack2 is new Stack(64); Now we can have as many stacks as we like, in whatever size we like. But what if you need a stack of characters instead of a stack of ...
... package Stack1 is new Stack(100); package Stack2 is new Stack(64); Now we can have as many stacks as we like, in whatever size we like. But what if you need a stack of characters instead of a stack of ...