Problem Solving by Search - Cornell Computer Science
... State evaluation function (or utility value) is a very general and useful idea. Example: • In chess, given a board, what would be the perfect evaluation value that you would want to know? (Assume the perspective of White player.) A: f(board) {+1, 0, -1}, with +1 for guaranteed win for White, 0 dr ...
... State evaluation function (or utility value) is a very general and useful idea. Example: • In chess, given a board, what would be the perfect evaluation value that you would want to know? (Assume the perspective of White player.) A: f(board) {+1, 0, -1}, with +1 for guaranteed win for White, 0 dr ...
Automatic Extraction of Efficient Axiom Sets from Large Knowledge
... genls and holdsIn. This makes the search intractable and queries are timed out. Therefore, one possible solution is to prevent the network from having hubs8. We can do this by limiting the maximum out degree of each node in the search space. Let m be the maximum allowed out-degree of each node. If V ...
... genls and holdsIn. This makes the search intractable and queries are timed out. Therefore, one possible solution is to prevent the network from having hubs8. We can do this by limiting the maximum out degree of each node in the search space. Let m be the maximum allowed out-degree of each node. If V ...
A WK-Means Approach for Clustering
... traditionally classified into two groups: Hierarchical clustering and partitional clustering. Hierarchical clustering divides objects into a tree of clusters. Since, this is not the subject of this study, we will not mention it in detail. The partitional method typically categorizes objects into K g ...
... traditionally classified into two groups: Hierarchical clustering and partitional clustering. Hierarchical clustering divides objects into a tree of clusters. Since, this is not the subject of this study, we will not mention it in detail. The partitional method typically categorizes objects into K g ...
Improved Memory-Bounded Dynamic Programming for
... ally not necessary. Consider for example robots navigating in a building. After turning away from the entrance door, the robots are highly unlikely to observe that same door in the next time step. In general, depending on the belief state and the action choice, only a very limited set of observation ...
... ally not necessary. Consider for example robots navigating in a building. After turning away from the entrance door, the robots are highly unlikely to observe that same door in the next time step. In general, depending on the belief state and the action choice, only a very limited set of observation ...
Automatic Composition of Music with Methods of Computational
... methods like Markov chains of different order. A great introduction to the modelling of interrelations in music with statistical methods can be found in [23]. Another important thing to point out is that the implementation is licensed under the Gnu Public Licence1 so that everyone can try out the pr ...
... methods like Markov chains of different order. A great introduction to the modelling of interrelations in music with statistical methods can be found in [23]. Another important thing to point out is that the implementation is licensed under the Gnu Public Licence1 so that everyone can try out the pr ...
Heuristics - UCLA Cognitive Systems Laboratory
... interval between each action. At minimum, they perform a backup for the current state, as defined by Equation (2), which corresponds to a one-step lookahead search; but more extensive search and backups can be performed if there is enough time. They are called “learning” algorithms because they cach ...
... interval between each action. At minimum, they perform a backup for the current state, as defined by Equation (2), which corresponds to a one-step lookahead search; but more extensive search and backups can be performed if there is enough time. They are called “learning” algorithms because they cach ...
artificial intelligence - MET Engineering College
... Game playing: IBM's Deep Blue became the first computer program to defeat the world champion in a chess match when it bested Garry Kasparov by a score of 3.5 to 2.5 in an exhibition match (Goodman and Keene, 1997). Autonomous control: The ALVINN computer vision system was trained to steer a car to k ...
... Game playing: IBM's Deep Blue became the first computer program to defeat the world champion in a chess match when it bested Garry Kasparov by a score of 3.5 to 2.5 in an exhibition match (Goodman and Keene, 1997). Autonomous control: The ALVINN computer vision system was trained to steer a car to k ...
1 managing long linked lists using lock free techniques
... Check-pointing the log is used to decrease the cost of state reconstruction. (Herlihy et al, 1987) also proposed a method for constructing non-blocking data structures using “copying”. Utilizing the ‘Load Linked’ (LL) instruction, a copy of the data structure (or in certain situations, a subset of i ...
... Check-pointing the log is used to decrease the cost of state reconstruction. (Herlihy et al, 1987) also proposed a method for constructing non-blocking data structures using “copying”. Utilizing the ‘Load Linked’ (LL) instruction, a copy of the data structure (or in certain situations, a subset of i ...
Artificial Intelligence and Decision Systems Course notes
... a clear-cut fashion, that would allow us to classify entities as either intelligent or not without a shadow of doubt. Rather, the best we can do is to characterize intelligence as a set of capabilities or skills that intelligent beings possess. These capabilities include problem-solving, reasoning, ...
... a clear-cut fashion, that would allow us to classify entities as either intelligent or not without a shadow of doubt. Rather, the best we can do is to characterize intelligence as a set of capabilities or skills that intelligent beings possess. These capabilities include problem-solving, reasoning, ...
Part I: Heuristics
... action a in state s, which can be positive or negative, γ ∈ (0, 1) denotes a discount factor, and the objective is to maximize expected total discounted reward over an infinite horizon. Interestingly, any discounted infinite-horizon MDP can be reduced to an equivalent stochastic shortest-path proble ...
... action a in state s, which can be positive or negative, γ ∈ (0, 1) denotes a discount factor, and the objective is to maximize expected total discounted reward over an infinite horizon. Interestingly, any discounted infinite-horizon MDP can be reduced to an equivalent stochastic shortest-path proble ...
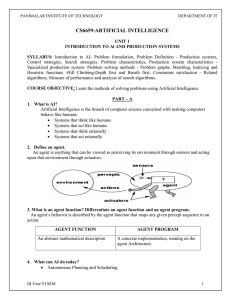
CS6659-ARTIFICIAL INTELLIGENCE
... For example in Figure 2.19,the algorithm first recourses down to the three bottom left nodes,and uses the utitliy function on them to discover that their values are 3,12,and 8 respectively. Then it takes the minimum of these values,3,and returns it as the backed-up value of node B. A similar process ...
... For example in Figure 2.19,the algorithm first recourses down to the three bottom left nodes,and uses the utitliy function on them to discover that their values are 3,12,and 8 respectively. Then it takes the minimum of these values,3,and returns it as the backed-up value of node B. A similar process ...
Potential Search: a Bounded
... It is a binary function, returning 1 if g(n) + h∗ (n) ≤ C and 0 otherwise. Of course, usually, h∗ (n) is not known in advance and the exact potential of a node cannot be calculated. However, we show that it is possible to order the nodes according to their potential even without knowing or calculati ...
... It is a binary function, returning 1 if g(n) + h∗ (n) ≤ C and 0 otherwise. Of course, usually, h∗ (n) is not known in advance and the exact potential of a node cannot be calculated. However, we show that it is possible to order the nodes according to their potential even without knowing or calculati ...