Blackbox on Sokoban problems
... BLACKBOX, IPP, and FF are state of the art planners. Within the past two years, they have all been entered in the yearly international planning competitions AIPS and ICAPS. During these competitions each planner is run on several different domains and the results of the planners are compared. One pr ...
... BLACKBOX, IPP, and FF are state of the art planners. Within the past two years, they have all been entered in the yearly international planning competitions AIPS and ICAPS. During these competitions each planner is run on several different domains and the results of the planners are compared. One pr ...
AANA Journal Course, AANA Journal, August 1998
... The periosteum of the femur is innervated primarily by the femoral nerve. The distal and proximal portions of the femur contain contributing innervation from the obturator nerve and sciatic nerve. Although other analgesic and anesthetic techniques could be utilized for femur fractures, the femoral n ...
... The periosteum of the femur is innervated primarily by the femoral nerve. The distal and proximal portions of the femur contain contributing innervation from the obturator nerve and sciatic nerve. Although other analgesic and anesthetic techniques could be utilized for femur fractures, the femoral n ...
Chapter 1 Security Problems in Computing
... Popular Encryption Algorithms – Merkle-Hellman Knapsacks – RSA Encryption – El Gamal Algorithms – DES Hashing Algorithms ...
... Popular Encryption Algorithms – Merkle-Hellman Knapsacks – RSA Encryption – El Gamal Algorithms – DES Hashing Algorithms ...
Ch08
... Handling an exception: responding to an exception by executing a part of the program specifically written for the exception » also called catching an exception The normal case is handled in a try block The exceptional case is handled in a catch block The catch block takes a parameter of type Excepti ...
... Handling an exception: responding to an exception by executing a part of the program specifically written for the exception » also called catching an exception The normal case is handled in a try block The exceptional case is handled in a catch block The catch block takes a parameter of type Excepti ...
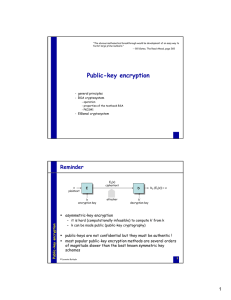
Public-key encryption
... – assume that the attacker wants to decrypt c = me mod n intended for Alice – assume that Alice will decrypt arbitrary ciphertext for the attacker, except c – the attacker can select a random number r and submit c⋅re mod n to Alice for decryption – since (c⋅re)d ≡ cd⋅red ≡ m⋅r (mod n), the attacker ...
... – assume that the attacker wants to decrypt c = me mod n intended for Alice – assume that Alice will decrypt arbitrary ciphertext for the attacker, except c – the attacker can select a random number r and submit c⋅re mod n to Alice for decryption – since (c⋅re)d ≡ cd⋅red ≡ m⋅r (mod n), the attacker ...
CICLOTOM: A computer approach to generalized modal music
... instrumentation and tempo used. Using KYKLOS' graphic interface, a composer could explore many aspects of modal music in real time that, eventually, never were explored before in this sonic context. The result of this process is called here Polymodal Music. ...
... instrumentation and tempo used. Using KYKLOS' graphic interface, a composer could explore many aspects of modal music in real time that, eventually, never were explored before in this sonic context. The result of this process is called here Polymodal Music. ...
30. basic pediatric regional anesthesia
... pediatric patients while delivering medical care in the field. The application of regional anesthesia in children can be extremely useful in austere situations, particularly when limited resources are available (eg, scarce oxygen supply, lack of postoperative analgesics, insufficient postoperative n ...
... pediatric patients while delivering medical care in the field. The application of regional anesthesia in children can be extremely useful in austere situations, particularly when limited resources are available (eg, scarce oxygen supply, lack of postoperative analgesics, insufficient postoperative n ...
ppt presentation
... while x’.target != w do x1 = x’.next y = x’.pointer While y.pred.key k do y= y.pred return y ...
... while x’.target != w do x1 = x’.next y = x’.pointer While y.pred.key k do y= y.pred return y ...
How to Encrypt with the LPN Problem
... in this field has concentrated on studying various operating modes to use with a secure block cipher [2]. Departing from this approach, we will construct a symmetric encryption scheme that does not appeal to any assumption regarding the pseudorandomness of a block cipher, and whose security can dire ...
... in this field has concentrated on studying various operating modes to use with a secure block cipher [2]. Departing from this approach, we will construct a symmetric encryption scheme that does not appeal to any assumption regarding the pseudorandomness of a block cipher, and whose security can dire ...
Composing semantic Web services under constraints
... Composing semantic Web services under constraints E.Karakoc, P.Senkul Journal: Expert Systems with Applications ...
... Composing semantic Web services under constraints E.Karakoc, P.Senkul Journal: Expert Systems with Applications ...
PH2150 Scientific Computing Skills
... • In general, statements are executed sequentially, top to bottom. • There are many instances when you want to break away from this e.g, • Branch point: choose to go in one direction or another based on meeting some condition. • Repeat: You may want to execute a block of code several times. • Progra ...
... • In general, statements are executed sequentially, top to bottom. • There are many instances when you want to break away from this e.g, • Branch point: choose to go in one direction or another based on meeting some condition. • Repeat: You may want to execute a block of code several times. • Progra ...
ABSOLUTE DEPENDENT MOTION ANALYSIS OF TWO
... heavy objects. The total lifting force required from the truck depends on the acceleration of the cabinet. How can we determine the acceleration and velocity of the cabinet if the acceleration of the truck is known? ...
... heavy objects. The total lifting force required from the truck depends on the acceleration of the cabinet. How can we determine the acceleration and velocity of the cabinet if the acceleration of the truck is known? ...
View File - University of Engineering and Technology, Taxila
... Block Codes • Block coding involves coding a block of bits into another block of bits with some redundancy to combat errors • single parity bit --- even parity code – Valid codewords should always have even number of 1’s – Add a parity bit=1 if number of 1’s in data is odd add parity bit=0 if numbe ...
... Block Codes • Block coding involves coding a block of bits into another block of bits with some redundancy to combat errors • single parity bit --- even parity code – Valid codewords should always have even number of 1’s – Add a parity bit=1 if number of 1’s in data is odd add parity bit=0 if numbe ...
QuestionFile3Cryptography
... a length of 200 decimal digits. Assume that you have sufficient secondary storage for them and that you can discount paging costs because you can prefetch the primes in order as needed. Then for some n <= 400 decimal digits in length, what would a simple brute force attack on an RSA encryption schem ...
... a length of 200 decimal digits. Assume that you have sufficient secondary storage for them and that you can discount paging costs because you can prefetch the primes in order as needed. Then for some n <= 400 decimal digits in length, what would a simple brute force attack on an RSA encryption schem ...
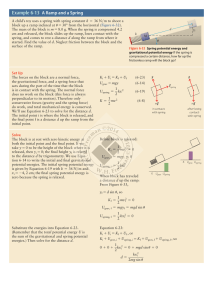
Example 6-13 A Ramp and a Spring
... In our solution we assumed that the final spring potential energy is zero, which means that the spring ends up neither compressed nor stretched. In other words, we assumed that the block moves so far up the ramp that it loses contact with the spring. That’s consistent with our result: The block move ...
... In our solution we assumed that the final spring potential energy is zero, which means that the spring ends up neither compressed nor stretched. In other words, we assumed that the block moves so far up the ramp that it loses contact with the spring. That’s consistent with our result: The block move ...
Devireddy
... Wired Equivalent Privacy (WEP), a security protocol for wireless local area networks (WLANs) defined in the 802.11b standard. LANs are more secure than WLANs. WLANs, which are over radio waves are more vulnerable to tampering. WEP provides security by encrypting data ...
... Wired Equivalent Privacy (WEP), a security protocol for wireless local area networks (WLANs) defined in the 802.11b standard. LANs are more secure than WLANs. WLANs, which are over radio waves are more vulnerable to tampering. WEP provides security by encrypting data ...
Section2.3
... Practice HW from Barr Textbook (not to hand in) p. 92 # 1, 2 # 3-5 (Use Internet Site) ...
... Practice HW from Barr Textbook (not to hand in) p. 92 # 1, 2 # 3-5 (Use Internet Site) ...
Cryptanalysis of Stream Cipher
... larger state: 5 x 128 bits but simpler operation: 1 AES round still easy to analyze create stream cipher from MAC ...
... larger state: 5 x 128 bits but simpler operation: 1 AES round still easy to analyze create stream cipher from MAC ...
On-line activities – build “George Boole May I
... create a “not” procedure and call it in a run-once block. Finally, create a combination of “and”, “or”, and “not” statements in a single procedure (named complex) and call that in a run once loop. The “say” block from the text drawer will make the variable visible in SpaceLand as the turtles move. ...
... create a “not” procedure and call it in a run-once block. Finally, create a combination of “and”, “or”, and “not” statements in a single procedure (named complex) and call that in a run once loop. The “say” block from the text drawer will make the variable visible in SpaceLand as the turtles move. ...
Bio-Block - Cartier Environmental Services Inc.
... ~ Natural Solutions For Our Environment ~ Bio-Block (Lift Stations Treatment) Bio-Block is a bacterial laden block for use in degrading organic in higher flow systems such as lift stations, wet wells, etc. The safe, natural occurring bacteria are present in high numbers to handle difficult organic p ...
... ~ Natural Solutions For Our Environment ~ Bio-Block (Lift Stations Treatment) Bio-Block is a bacterial laden block for use in degrading organic in higher flow systems such as lift stations, wet wells, etc. The safe, natural occurring bacteria are present in high numbers to handle difficult organic p ...
Lecture 25 - Data Encryption
... decode a cipher text by brute force, by trying all possible keys (a computer makes that easy) • Caesar cipher is a stream/substitution cipher, wherein each letter of plain text generates a letter of cipher text • The structure of the plain text is preserved in the structure of the cipher text ...
... decode a cipher text by brute force, by trying all possible keys (a computer makes that easy) • Caesar cipher is a stream/substitution cipher, wherein each letter of plain text generates a letter of cipher text • The structure of the plain text is preserved in the structure of the cipher text ...