Tracking and Mitigation of Malicious Remote Control
... goal of the attacker is to compromise the victim’s machine and obtain control over it. This machine is then used to carry out denial-of-service attacks, to send out spam mails, or for other nefarious purposes. From an attacker’s point of view, this kind of attack is even more efficient if she manage ...
... goal of the attacker is to compromise the victim’s machine and obtain control over it. This machine is then used to carry out denial-of-service attacks, to send out spam mails, or for other nefarious purposes. From an attacker’s point of view, this kind of attack is even more efficient if she manage ...
Security+Certification
... effective. To others, a hacker is someone who breaks security on an automated information system or a network. This type of hacker (also known as a cracker) is typically doing something mischievous or malicious, and although they might be trying to break into a system for what they consider a good a ...
... effective. To others, a hacker is someone who breaks security on an automated information system or a network. This type of hacker (also known as a cracker) is typically doing something mischievous or malicious, and although they might be trying to break into a system for what they consider a good a ...
- University of Huddersfield Repository
... The best possible performance of a musical work could arguably be called a faultless performance, where according to Herbert Henck, a fault is defined as ‘any moment, where intention and doing fall apart’.1 In a music performance, this does not only include manifest mistakes like wrong notes, but al ...
... The best possible performance of a musical work could arguably be called a faultless performance, where according to Herbert Henck, a fault is defined as ‘any moment, where intention and doing fall apart’.1 In a music performance, this does not only include manifest mistakes like wrong notes, but al ...
Course Syllabus for Advanced PC Configuration
... Make a paper record of what the BIOS settings are for each sub-section of the setup program BEFORE you begin tinkering with the settings. At least this way, you will be able to get back to square one if you make any mistakes in working with the setup program. You may be able to print out a copy of e ...
... Make a paper record of what the BIOS settings are for each sub-section of the setup program BEFORE you begin tinkering with the settings. At least this way, you will be able to get back to square one if you make any mistakes in working with the setup program. You may be able to print out a copy of e ...
Observations on Operating System Security Vulnerabilities
... Computer systems and especially their protection mechanisms must be penetration resistant. However, most, or perhaps all, current systems have security holes which make them vulnerable. As long as vulnerabilities remain in a system, the security may be circumvented. It is thus not difficult to under ...
... Computer systems and especially their protection mechanisms must be penetration resistant. However, most, or perhaps all, current systems have security holes which make them vulnerable. As long as vulnerabilities remain in a system, the security may be circumvented. It is thus not difficult to under ...
Plan de projet
... 6.12.11.3.1 Physical robustness of the user facing devices. ......................................................................................... 61 6.12.11.3.2 Security of physical connectivity between authentication points and the host system. ............................. 61 6.12.11.3.3 Secur ...
... 6.12.11.3.1 Physical robustness of the user facing devices. ......................................................................................... 61 6.12.11.3.2 Security of physical connectivity between authentication points and the host system. ............................. 61 6.12.11.3.3 Secur ...
Network Firewalls - Department of Computer Science
... attacker did, learning from these actions, and alerting system administrators of the networks from where the attacks were originating. Such incidents clearly signaled the end of an open and benign Internet. By 1992 Steve Bellovin described a collection of attacks that he had noticed while monitoring ...
... attacker did, learning from these actions, and alerting system administrators of the networks from where the attacks were originating. Such incidents clearly signaled the end of an open and benign Internet. By 1992 Steve Bellovin described a collection of attacks that he had noticed while monitoring ...
Internet Techniques
... Professor for Communications Systems at the FernUniversität Hagen Main interests: Communications Systems, Networks and Protocols; Network Security ...
... Professor for Communications Systems at the FernUniversität Hagen Main interests: Communications Systems, Networks and Protocols; Network Security ...
Untitled - International Journal of Interactive Multimedia and Artificial
... This Special Issue tries to show some of the latest researches related to IoT with special emphasis on the basic components of IoT [2], some of the major applications in which researchers and practitioners are working [3] and especially in aspects related to security, one of the main areas of resear ...
... This Special Issue tries to show some of the latest researches related to IoT with special emphasis on the basic components of IoT [2], some of the major applications in which researchers and practitioners are working [3] and especially in aspects related to security, one of the main areas of resear ...
Information Systems Ethics Policy
... User refers to any person, whether authorized or not, who makes any use of any Information Systems from any location. Information Systems includes, but is not limited to, computers, terminals, servers, printers, networks, data, modem banks, online and off-line storage media, access card systems, com ...
... User refers to any person, whether authorized or not, who makes any use of any Information Systems from any location. Information Systems includes, but is not limited to, computers, terminals, servers, printers, networks, data, modem banks, online and off-line storage media, access card systems, com ...
CSCE 790 – Secure Database Systems
... against a Member of the United Nations, until the Security Council has taken measures necessary to maintain international peace and security. Measures taken by Members in the exercise of this right of self-defense shall be immediately reported to the Security Council and shall not in any way affect ...
... against a Member of the United Nations, until the Security Council has taken measures necessary to maintain international peace and security. Measures taken by Members in the exercise of this right of self-defense shall be immediately reported to the Security Council and shall not in any way affect ...
Part A
... computer defined as a person who performs calculations! Prior to 1940, machines designed to perform calculations were referred to as calculators and tabulators, not computers. The modern definition and use of the term “computer” emerged in the 1940s, when the first electronic computing devices were ...
... computer defined as a person who performs calculations! Prior to 1940, machines designed to perform calculations were referred to as calculators and tabulators, not computers. The modern definition and use of the term “computer” emerged in the 1940s, when the first electronic computing devices were ...
Information Technology Competency Model of Core Learning
... of settings. This is achieved in large measure by defining specific curricular content in terms of measurable student learning outcomes accompanied by detailed rubrics for effective assessment of student learning. While some specific implementation aspects of these resources may be more prominent in ...
... of settings. This is achieved in large measure by defining specific curricular content in terms of measurable student learning outcomes accompanied by detailed rubrics for effective assessment of student learning. While some specific implementation aspects of these resources may be more prominent in ...
RFC 2196 - Helpdesk
... The "Internet" is a collection of thousands of networks linked by a common set of technical protocols which make it possible for users of any one of the networks to communicate with, or use the services located on, any of the other networks (FYI4, RFC 1594). The term "administrator" is used to cove ...
... The "Internet" is a collection of thousands of networks linked by a common set of technical protocols which make it possible for users of any one of the networks to communicate with, or use the services located on, any of the other networks (FYI4, RFC 1594). The term "administrator" is used to cove ...
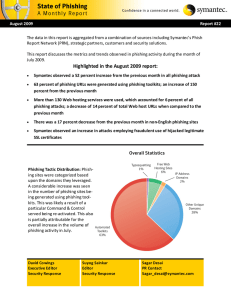
Highlighted in the August 2009 report
... the previous month continued to primarily target a social networking site popular in the United States. This toolkit attack is in all likelihood related to a specific Command & Control server being reactivated. These attacks targeted towards the information services sector, facilitates attackers in ...
... the previous month continued to primarily target a social networking site popular in the United States. This toolkit attack is in all likelihood related to a specific Command & Control server being reactivated. These attacks targeted towards the information services sector, facilitates attackers in ...
Lab # 05: Building IP internetwork
... This section contains a summary on Domains and Workgroups. There are many ways in which computers can provide services, and manage users into logical groups. This section looks at some of those approaches. ...
... This section contains a summary on Domains and Workgroups. There are many ways in which computers can provide services, and manage users into logical groups. This section looks at some of those approaches. ...
Document
... A CPU that uses microcode generally takes several clock cycles to execute a single instruction, one clock cycle for each step in the microprogram for that instruction. Some Complex instruction set computer|CISC processors include instructions that can take a very long time to execute. Such variation ...
... A CPU that uses microcode generally takes several clock cycles to execute a single instruction, one clock cycle for each step in the microprogram for that instruction. Some Complex instruction set computer|CISC processors include instructions that can take a very long time to execute. Such variation ...
David Cuacos Masther Thesis - e-Archivo Principal
... technology promotes greater independence for people with disabilities by enabling them to perform tasks that they were formerly unable to accomplish, or had great difficulty accomplishing, by providing enhancements to or changed methods of interacting with the technology needed to accomplish such ta ...
... technology promotes greater independence for people with disabilities by enabling them to perform tasks that they were formerly unable to accomplish, or had great difficulty accomplishing, by providing enhancements to or changed methods of interacting with the technology needed to accomplish such ta ...
conklin_4e_PPT_ch11
... accounting, referred to as AAA. • Authentication is the matching of user-supplied credentials to previously stored credentials on a host machine, and it usually involves an account username and password. • Authorization is the granting of specific permissions based on the privileges held by the acco ...
... accounting, referred to as AAA. • Authentication is the matching of user-supplied credentials to previously stored credentials on a host machine, and it usually involves an account username and password. • Authorization is the granting of specific permissions based on the privileges held by the acco ...
THESIS NAVAL POSTGRADUATE SCHOOL Monterey, California
... without any sort of training and certification on the security aspects and potential risks associated with their use. When these assets are attacked, damaged or threatened, the confidentiality, integrity and availability (CIA) of our data and the proper operation of the RSNF may be interrupted. The ...
... without any sort of training and certification on the security aspects and potential risks associated with their use. When these assets are attacked, damaged or threatened, the confidentiality, integrity and availability (CIA) of our data and the proper operation of the RSNF may be interrupted. The ...
prise 2007
... Anyway, such archives, due to laws protecting users' right to privacy, cannot be distributed as-is. To address this problem, some approaches propose methods aimed at avoiding the distribution of the traces, totally preventing information leakage [1]. These approaches, however, cannot by followed if ...
... Anyway, such archives, due to laws protecting users' right to privacy, cannot be distributed as-is. To address this problem, some approaches propose methods aimed at avoiding the distribution of the traces, totally preventing information leakage [1]. These approaches, however, cannot by followed if ...
Approved 400-Level courses to count towards CSE Graduate
... Approved 400-Level courses to count towards CSE Graduate Program IMPORTANT: Students who have taken any of the 4XX courses listed below as 598, cannot take the same class at the 400-level. CSE 408 Multimedia Information Systems CSE 412 Database Management CSE 414 Advanced Database Concepts CSE 432 O ...
... Approved 400-Level courses to count towards CSE Graduate Program IMPORTANT: Students who have taken any of the 4XX courses listed below as 598, cannot take the same class at the 400-level. CSE 408 Multimedia Information Systems CSE 412 Database Management CSE 414 Advanced Database Concepts CSE 432 O ...
Data security - E
... federal government and related contractors have contributed more recently to the theory and practice of IT management at the federal level than public administration. This chapter analyzes federal IT management literature from several academic disciplines and government documents. The analysis compa ...
... federal government and related contractors have contributed more recently to the theory and practice of IT management at the federal level than public administration. This chapter analyzes federal IT management literature from several academic disciplines and government documents. The analysis compa ...
doc.gold.ac.uk
... • Today’s computing – Requires comprehensive computer security plans Electronic Commerce, Tenth Edition ...
... • Today’s computing – Requires comprehensive computer security plans Electronic Commerce, Tenth Edition ...
dranzer v2
... A first attempt to mitigate stack-based buffer overflows came out in June, 1997, when Solar Designer released the Non-Executable Stack patch for Linux [98, 96]. The idea was simple and intuitive: make the stack area non-executable. In theory, doing so renders most of the buffer overflow vulnerabilit ...
... A first attempt to mitigate stack-based buffer overflows came out in June, 1997, when Solar Designer released the Non-Executable Stack patch for Linux [98, 96]. The idea was simple and intuitive: make the stack area non-executable. In theory, doing so renders most of the buffer overflow vulnerabilit ...