Week 2
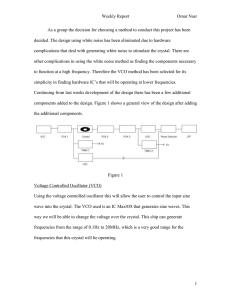
... As a group the decision for choosing a method to conduct this project has been decided. The design using white noise has been eliminated due to hardware complications that deal with generating white noise to stimulate the crystal. There are other complications in using the white noise method as find ...
... As a group the decision for choosing a method to conduct this project has been decided. The design using white noise has been eliminated due to hardware complications that deal with generating white noise to stimulate the crystal. There are other complications in using the white noise method as find ...
Multiplexing and Demultiplexing
... to have no input data the selected output will be high, the others low This can be used to activate a control pin on the selected part of circuit ...
... to have no input data the selected output will be high, the others low This can be used to activate a control pin on the selected part of circuit ...
Node Voltage with Thevenin Equivalent
... several types of simulations by adding the appropriate sources in your schematic and in your simulation profile? – For example: If you include a Vsin and a Vac in your circuit, you can chose to simulate either the AC or Transient response when you run the simulation. • Note: The additional sources m ...
... several types of simulations by adding the appropriate sources in your schematic and in your simulation profile? – For example: If you include a Vsin and a Vac in your circuit, you can chose to simulate either the AC or Transient response when you run the simulation. • Note: The additional sources m ...
Lecture 9 - Welcome to Nyssen Central!
... We already saw that the Memory Address Register points to the correct location in RAM. This particular register is connected to the RAM by the address bus. The address bus carries binary signals which are then interpreted as address numbers, preparing the correct cell to send or receive data. ...
... We already saw that the Memory Address Register points to the correct location in RAM. This particular register is connected to the RAM by the address bus. The address bus carries binary signals which are then interpreted as address numbers, preparing the correct cell to send or receive data. ...
Enphase M215 Microinverter
... The DC circuit meets the requirements for ungrounded PV arrays in NEC 690.35. Equipment ground is provided in the Engage Cable. No additional GEC or ground is required. Ground fault protection (GFP) is integrated into the microinverter. ...
... The DC circuit meets the requirements for ungrounded PV arrays in NEC 690.35. Equipment ground is provided in the Engage Cable. No additional GEC or ground is required. Ground fault protection (GFP) is integrated into the microinverter. ...
Presentations 2 &3 : MICRO 2003 Review, by Theo Theocharides
... Estimated AVFs using a novel approach that tracks bits required for architecturally correct execution (ACE) and unACE bits Computed the AVF for the instruction queue and execution units of an Itanium2®-like IA64 processor. Further refinement could further lower the AVF estimates but expect the ...
... Estimated AVFs using a novel approach that tracks bits required for architecturally correct execution (ACE) and unACE bits Computed the AVF for the instruction queue and execution units of an Itanium2®-like IA64 processor. Further refinement could further lower the AVF estimates but expect the ...
Presentation Title Here
... Operate at higher voltage level at Server Input Operate at higher voltage level at Server Input reduces the current requirement, this will reduces the losses. ...
... Operate at higher voltage level at Server Input Operate at higher voltage level at Server Input reduces the current requirement, this will reduces the losses. ...
LVR125S
... 1. Users should independently evaluate the suitability of and test each product selected for their own application. 2. This product should not be used in an application where the maximum interrupt voltage or maximum interrupt current can be exceeded in a fault condition. Operation beyond the maximum ...
... 1. Users should independently evaluate the suitability of and test each product selected for their own application. 2. This product should not be used in an application where the maximum interrupt voltage or maximum interrupt current can be exceeded in a fault condition. Operation beyond the maximum ...
Cricket_project_brl4..
... capacitor voltage and when it reaches 2/3Vcc (threshold), the output becomes low and the discharge pin is connected to 0V. • The capacitor discharges with current flowing through RB into the discharge pin. When the voltage falls to 1/3Vcc (trigger) the output becomes high again and the discharge pin ...
... capacitor voltage and when it reaches 2/3Vcc (threshold), the output becomes low and the discharge pin is connected to 0V. • The capacitor discharges with current flowing through RB into the discharge pin. When the voltage falls to 1/3Vcc (trigger) the output becomes high again and the discharge pin ...
Capacitor
... voltage sensor, decade resistance box, light bulb, knife-switch, and connecting wires (4). Theory: The capacitance (C) of a capacitor is given by, where Q is the charge stored and V is the potential difference. C ...
... voltage sensor, decade resistance box, light bulb, knife-switch, and connecting wires (4). Theory: The capacitance (C) of a capacitor is given by, where Q is the charge stored and V is the potential difference. C ...
P 1 - 123SeminarsOnly.com
... will be read from in Internal RAM. If you push a value onto the stack, the value will be written to the address of SP + 1. That is to say, if SP holds the value 07h, a PUSH instruction will push the value onto the stack at address 08h. This SFR is modified by all instructions which modify the stack, ...
... will be read from in Internal RAM. If you push a value onto the stack, the value will be written to the address of SP + 1. That is to say, if SP holds the value 07h, a PUSH instruction will push the value onto the stack at address 08h. This SFR is modified by all instructions which modify the stack, ...
The Microprocessor
... • Wanted to make the 286 backward compatible with the 8088’s. • So had 2 modes: – Real mode-less powerful – Protected mode-very powerful • Could access up to 16 mb of memory • Needed a special operating system • But most users only had DOS ...
... • Wanted to make the 286 backward compatible with the 8088’s. • So had 2 modes: – Real mode-less powerful – Protected mode-very powerful • Could access up to 16 mb of memory • Needed a special operating system • But most users only had DOS ...
SET-276. Power factor correction and alerts through the
... involves using a piecewise-polynomial analog computer (AC) to compute power transistor on-times in accordance with separate polynomial transfer functions for powerfactor control and peak-current-linking using as inputs current representations of line input voltage (VLN), load output voltage (VLD), a ...
... involves using a piecewise-polynomial analog computer (AC) to compute power transistor on-times in accordance with separate polynomial transfer functions for powerfactor control and peak-current-linking using as inputs current representations of line input voltage (VLN), load output voltage (VLD), a ...
Electronic Instrumentation - Rensselaer Polytechnic Institute
... Function Generator: 50 ohms ‘Scope: 1Meg ohms DMM (DC voltage): 10Meg ohms DMM (AC voltage): 1Meg ohms DMM (DC current): 5 ohms (negligible) ...
... Function Generator: 50 ohms ‘Scope: 1Meg ohms DMM (DC voltage): 10Meg ohms DMM (AC voltage): 1Meg ohms DMM (DC current): 5 ohms (negligible) ...
Concept Development - EDGE - Rochester Institute of Technology
... Electronic Circuitry between the low power “control electronics” and the input and output devices. ...
... Electronic Circuitry between the low power “control electronics” and the input and output devices. ...
Static RAM (SRAM)
... A RAM constitutes the internal memory of the CPU for storing data, program and program result. It is read/write memory. It is called random access memory (RAM). Since access time in RAM is independent of the address to the word that is, each storage location inside the memory is as easy to reach as ...
... A RAM constitutes the internal memory of the CPU for storing data, program and program result. It is read/write memory. It is called random access memory (RAM). Since access time in RAM is independent of the address to the word that is, each storage location inside the memory is as easy to reach as ...
Lior - Test Receiver
... challenges, they may come up with somewhat different solutions. This can lead to ‘single-source’ problems. ...
... challenges, they may come up with somewhat different solutions. This can lead to ‘single-source’ problems. ...