Secure Email
... privacy (only the intended recipient can read the message) and authentication (the recipient can be assured of the identity of the sender). The technical capabilities for these functions has been known for many years, but they have only been applied to Internet mail recently. – Reality Check: Securi ...
... privacy (only the intended recipient can read the message) and authentication (the recipient can be assured of the identity of the sender). The technical capabilities for these functions has been known for many years, but they have only been applied to Internet mail recently. – Reality Check: Securi ...
Module 2
... alone computers that are not part of a domain or when you are authenticating to a server using an IP address. • It also acts a fallback authentication if it cannot complete Kerberos authentication such as being blocked by a firewall. • NTLM uses a challenge-response mechanism for authentication, in ...
... alone computers that are not part of a domain or when you are authenticating to a server using an IP address. • It also acts a fallback authentication if it cannot complete Kerberos authentication such as being blocked by a firewall. • NTLM uses a challenge-response mechanism for authentication, in ...
Securing Distribution Automation
... The issue of field device password management has been identified by the NIST CyberSecurity Coordination Task Group as one of the issues that needs to be addressed for Smart Grid security. While there exist many enterprise-level products for password management, to our knowledge there are none that ...
... The issue of field device password management has been identified by the NIST CyberSecurity Coordination Task Group as one of the issues that needs to be addressed for Smart Grid security. While there exist many enterprise-level products for password management, to our knowledge there are none that ...
Security
... with their private key – Customer decrypts using the merchants public key to prove authenticity of sender – Customer decrypts using their private key to ensure integrity of message ...
... with their private key – Customer decrypts using the merchants public key to prove authenticity of sender – Customer decrypts using their private key to ensure integrity of message ...
Network Security
... PGP (short for Pretty Good Privacy), created by Philip Zimmermann, is the de facto standard program for secure e-mail and file encryption on the Internet. Its public-key cryptography system enables people who have never met to secure transmitted messages against unauthorized reading and to add digit ...
... PGP (short for Pretty Good Privacy), created by Philip Zimmermann, is the de facto standard program for secure e-mail and file encryption on the Internet. Its public-key cryptography system enables people who have never met to secure transmitted messages against unauthorized reading and to add digit ...
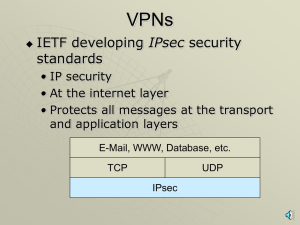
VPNs, PKIs, ISSs, SSLs with narration
... • Webserver authenticates itself • Browser may authenticate itself but rarely does • Browser selects a symmetric session key, sends to webserver • Adds a digital signature and encrypts all messages with the symmetric key ...
... • Webserver authenticates itself • Browser may authenticate itself but rarely does • Browser selects a symmetric session key, sends to webserver • Adds a digital signature and encrypts all messages with the symmetric key ...
Chapter 10: Electronic Commerce Security
... Is a computer with anti-virus software protected from viruses? Why or why not? What are the differences between encryption and ...
... Is a computer with anti-virus software protected from viruses? Why or why not? What are the differences between encryption and ...
security
... users that the public key they are about to accept is authentic • Given by a Certification Authority (CA) e.g.Verisign • Web browsers have a list of trusted CA’s built into them ...
... users that the public key they are about to accept is authentic • Given by a Certification Authority (CA) e.g.Verisign • Web browsers have a list of trusted CA’s built into them ...
Powerpoint Slides
... At the start of an SSL session, the browser sends its public key to the server. Server uses the browser’s public key to encrypt a secret key and sends it to the browser. During the session, the server and browser exchange data via secret key encryption. ...
... At the start of an SSL session, the browser sends its public key to the server. Server uses the browser’s public key to encrypt a secret key and sends it to the browser. During the session, the server and browser exchange data via secret key encryption. ...
Lecture on Security
... Some sort of overhaul is required – So what can we do to avoid shared secret? ...
... Some sort of overhaul is required – So what can we do to avoid shared secret? ...
Rocket® Blue Zone Security Server
... access to host systems, increasing data stream privacy, and strengthening authentication. Rocket® BlueZone Security Server secures confidential information, authenticates users and reinforces network and perimeter security. ...
... access to host systems, increasing data stream privacy, and strengthening authentication. Rocket® BlueZone Security Server secures confidential information, authenticates users and reinforces network and perimeter security. ...
abstract - Chennaisunday.com
... the Internet. To accommodate the scale of transactions across the Internet, some of ...
... the Internet. To accommodate the scale of transactions across the Internet, some of ...
Certificate in Actuarial Science
... The Certificate in Actuarial Science prepares students to pursue employment as an actuary. In addition to the required courses, it is also recommend that students take courses in Linear Algebra, Statistics, and Numerical Methods. Degree Services Validation Office Use Only Date: ...
... The Certificate in Actuarial Science prepares students to pursue employment as an actuary. In addition to the required courses, it is also recommend that students take courses in Linear Algebra, Statistics, and Numerical Methods. Degree Services Validation Office Use Only Date: ...
Web Security
... WWW-Authenticate • Secure Sockets Layer (SSL) – Invented by Netscape and made public domain for everyone’s use – An additional layer to the TCP/IP stack that sits between the Application and Transport layers • ensures that all application data is encrypted but TCP/IP headers are not • usually run o ...
... WWW-Authenticate • Secure Sockets Layer (SSL) – Invented by Netscape and made public domain for everyone’s use – An additional layer to the TCP/IP stack that sits between the Application and Transport layers • ensures that all application data is encrypted but TCP/IP headers are not • usually run o ...
Web Security
... WWW-Authenticate • Secure Sockets Layer (SSL) – Invented by Netscape and made public domain for everyone’s use – An additional layer to the TCP/IP stack that sits between the Application and Transport layers • ensures that all application data is encrypted but TCP/IP headers are not • usually run o ...
... WWW-Authenticate • Secure Sockets Layer (SSL) – Invented by Netscape and made public domain for everyone’s use – An additional layer to the TCP/IP stack that sits between the Application and Transport layers • ensures that all application data is encrypted but TCP/IP headers are not • usually run o ...
Implementing Security for Electronic Commerce
... CA guarantees the authenticity of the organization or individual. ...
... CA guarantees the authenticity of the organization or individual. ...
Java Security
... A public key (or identity) certificate is a binding of a public key to an identity, which is digitally signed by the private key of another entity, often called a Certification Authority (CA). The X.509 standard defines what information can go into a certificate, and describes how to write it down ( ...
... A public key (or identity) certificate is a binding of a public key to an identity, which is digitally signed by the private key of another entity, often called a Certification Authority (CA). The X.509 standard defines what information can go into a certificate, and describes how to write it down ( ...