COS 338_day17
... Client Generates Random Session Key Client Sends to Server Encrypted by Merchant’s Public Key ...
... Client Generates Random Session Key Client Sends to Server Encrypted by Merchant’s Public Key ...
Public Presentation - Academic Conferences
... Vendor downloadable product subverted “Cracker gained user-level access to modify the download file. . . . you pray never happens, but it did.” – WordPress, reported on wordpress.org, March 2, 2007 ...
... Vendor downloadable product subverted “Cracker gained user-level access to modify the download file. . . . you pray never happens, but it did.” – WordPress, reported on wordpress.org, March 2, 2007 ...
Dr. Clifford Neuman University of Southern California Information
... – Confidentiality not needed for public key – Solves n2 problem • Performance – Slower than conventional cryptography – Implementations use for key distribution, then use conventional crypto for data encryption • Trusted third party still needed – To certify public key – To manage revocation – In so ...
... – Confidentiality not needed for public key – Solves n2 problem • Performance – Slower than conventional cryptography – Implementations use for key distribution, then use conventional crypto for data encryption • Trusted third party still needed – To certify public key – To manage revocation – In so ...
PPT - Purdue Computer Science
... – key transport: one party creates, and securely transfers it to the other(s). – key agreement: key establishment technique in which a shared secret is derived by two (or more) parties ...
... – key transport: one party creates, and securely transfers it to the other(s). – key agreement: key establishment technique in which a shared secret is derived by two (or more) parties ...
Module 7 Active Directory and Account Management
... • Network traffic due to replications is reduced by: – Replicating individual properties instead of entire accounts – Replicating based on the speed of the network link • Replicate more frequently over a LAN than a WAN ...
... • Network traffic due to replications is reduced by: – Replicating individual properties instead of entire accounts – Replicating based on the speed of the network link • Replicate more frequently over a LAN than a WAN ...
Organizations That Use TLS/SSL
... authority that can attest to the identity of the certificate owner. Organizations will also need a system or network administrator who is familiar with whichever client-server applications need to be secured to enable TLS/SSL encryption. If an organization purchases a certificate from a trusted CA, ...
... authority that can attest to the identity of the certificate owner. Organizations will also need a system or network administrator who is familiar with whichever client-server applications need to be secured to enable TLS/SSL encryption. If an organization purchases a certificate from a trusted CA, ...
03-WAS Common Threats - Professional Data Management
... These kind of attacks involves sending overly long input streams to the attacked server, causing the server to overflow parts of the memory and either crash the system or execute the attackers arbitrary code as if it was part of the servers code. The attackers code can inject a backdoor code as well ...
... These kind of attacks involves sending overly long input streams to the attacked server, causing the server to overflow parts of the memory and either crash the system or execute the attackers arbitrary code as if it was part of the servers code. The attackers code can inject a backdoor code as well ...
Public Key Encryption and Digital Signatures
... problems with allowable exports, and are not always allowed to talk about their work. • Is it desirable to have government able to crack all codes? • What is the tradeoff between privacy of law abiding citizens vs. the ability of terrorists and drug traffickers to communicate in secret? ...
... problems with allowable exports, and are not always allowed to talk about their work. • Is it desirable to have government able to crack all codes? • What is the tradeoff between privacy of law abiding citizens vs. the ability of terrorists and drug traffickers to communicate in secret? ...
IPSEC Presentation
... – To protect IP packets – To provide defense against network attacks 1: From wikipedia.org ...
... – To protect IP packets – To provide defense against network attacks 1: From wikipedia.org ...
Security Features in Windows CE
... surface of vulnerability. Examples of client applications are browsers, email clients and FTP clients. Servers are more exposed because they wait to receive requests from clients on the network. Requests can come from anywhere in the network. When the server is exposed to the public interface, the s ...
... surface of vulnerability. Examples of client applications are browsers, email clients and FTP clients. Servers are more exposed because they wait to receive requests from clients on the network. Requests can come from anywhere in the network. When the server is exposed to the public interface, the s ...
Lock down security exposures in your Domino web
... Name and password access • User submits name and password, which Domino compares to Person document in a Domino directory or to a record in an LDAP directory • Easy to set up and administer. Just create Person and Group documents. • Problem: Name and password cross network as plain text with every U ...
... Name and password access • User submits name and password, which Domino compares to Person document in a Domino directory or to a record in an LDAP directory • Easy to set up and administer. Just create Person and Group documents. • Problem: Name and password cross network as plain text with every U ...
CIT 016 Review for Final
... Operating systems are intended to be dynamic As users’ needs change, new hardware is introduced, and more sophisticated attacks are unleashed, operating systems must be updated on a regular basis However, vendors release a new version of an operating system every two to four years Vendors use certai ...
... Operating systems are intended to be dynamic As users’ needs change, new hardware is introduced, and more sophisticated attacks are unleashed, operating systems must be updated on a regular basis However, vendors release a new version of an operating system every two to four years Vendors use certai ...
Slides on Security
... • A digital certificate contains a user’s public key along with some information about the user, such as their email address. • The digital certificate is digitally signed by a Certificate Authority. • Certificate Authorities are venders of digital certificates. • Clients must know the public key of ...
... • A digital certificate contains a user’s public key along with some information about the user, such as their email address. • The digital certificate is digitally signed by a Certificate Authority. • Certificate Authorities are venders of digital certificates. • Clients must know the public key of ...
Edgenuity SSL Protocols
... protocols when using a media appliance. By using SSL and HTTPS protocols, Edgenuity can provide a level of security and confidence within the information being exchanged with our users. Additional configuration will be required for customers using an Edgenuity Media Appliance. Instructions for deplo ...
... protocols when using a media appliance. By using SSL and HTTPS protocols, Edgenuity can provide a level of security and confidence within the information being exchanged with our users. Additional configuration will be required for customers using an Edgenuity Media Appliance. Instructions for deplo ...
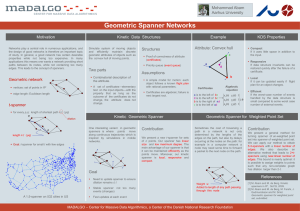
Geometric spanner for weighted point set, submitted.
... the design of good networks is therefore an important topic of study. In general, a good network has certain desirable properties while not being too expensive. In many applications this means one wants a network providing short paths between its nodes, while not containing too many edges. This lead ...
... the design of good networks is therefore an important topic of study. In general, a good network has certain desirable properties while not being too expensive. In many applications this means one wants a network providing short paths between its nodes, while not containing too many edges. This lead ...
Chapter X Slides
... Digital Signature continued: Uses a set of complimentary algorithms for signing and for verification • Digital signatures provide authentication • Digital signatures provide message integrity • Each signature is appended to the message in clear text ...
... Digital Signature continued: Uses a set of complimentary algorithms for signing and for verification • Digital signatures provide authentication • Digital signatures provide message integrity • Each signature is appended to the message in clear text ...
KaranOberoi
... Sub-Domain must be added to RootDomain – otherwise there will be no tree adiscon.com ...
... Sub-Domain must be added to RootDomain – otherwise there will be no tree adiscon.com ...
DNS
... Solution: The Name Server for the domain up contains records for when something like this would happen – njit.edu would contain a record indicating the IP Address for derp.my.njit.edu Problem 2: When propagating DNS changes, sometimes extra data is sent outside of the request. Regrettably some imple ...
... Solution: The Name Server for the domain up contains records for when something like this would happen – njit.edu would contain a record indicating the IP Address for derp.my.njit.edu Problem 2: When propagating DNS changes, sometimes extra data is sent outside of the request. Regrettably some imple ...
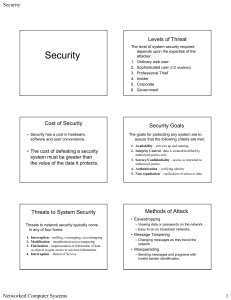
Security - The University of Texas at Dallas
... • You hear them murmur, "Let's see you use that VISA card now, Professor "I-Don't-Give-A's-To Any MBA Candidate!" ...
... • You hear them murmur, "Let's see you use that VISA card now, Professor "I-Don't-Give-A's-To Any MBA Candidate!" ...
PowerPoint
... • People can extract information about you and your customers by reading your zones ...
... • People can extract information about you and your customers by reading your zones ...
DNS Session 5 Additional Topics
... • People can extract information about you and your customers by reading your zones ...
... • People can extract information about you and your customers by reading your zones ...
XML: Part - Houston Community College System
... who they claim to be – The message was not altered – It cannot be denied the message was sent Security+ Guide to Network Security Fundamentals, 2e ...
... who they claim to be – The message was not altered – It cannot be denied the message was sent Security+ Guide to Network Security Fundamentals, 2e ...