Diapositiva 1 - Gaming Standards Association
... G2S Promotes Innovation • G2S allows any authorized server that speaks the protocol to participate in the slot network • Event and Meter subscriptions allow a host to subscribe to specific information • Operators can “try out” new products to see if they like them • Products can compete using the s ...
... G2S Promotes Innovation • G2S allows any authorized server that speaks the protocol to participate in the slot network • Event and Meter subscriptions allow a host to subscribe to specific information • Operators can “try out” new products to see if they like them • Products can compete using the s ...
i - i TNA 102
... (1) As far as is practicable, the Telecom PSTN is compliant with ITU-T (formerly CCITT) Recommendations. Reference is made as appropriate to specific Recommendations throughout this Specification. For convenience, such references indicate the Recommendation current at the date of issue, e.g. 'CCITT ...
... (1) As far as is practicable, the Telecom PSTN is compliant with ITU-T (formerly CCITT) Recommendations. Reference is made as appropriate to specific Recommendations throughout this Specification. For convenience, such references indicate the Recommendation current at the date of issue, e.g. 'CCITT ...
ITE PC v4.0 Chapter 1 - Система е
... Role of the Transport Layer The Transport Layer is responsible for establishing a temporary communication session between two applications and delivering data between them. TCP/IP uses two protocols to achieve this: Transmission Control Protocol (TCP) User Datagram Protocol (UDP) Primary Respons ...
... Role of the Transport Layer The Transport Layer is responsible for establishing a temporary communication session between two applications and delivering data between them. TCP/IP uses two protocols to achieve this: Transmission Control Protocol (TCP) User Datagram Protocol (UDP) Primary Respons ...
ITE PC v4.0 Chapter 1
... Role of the Transport Layer The Transport Layer is responsible for establishing a temporary communication session between two applications and delivering data between them. TCP/IP uses two protocols to achieve this: Transmission Control Protocol (TCP) User Datagram Protocol (UDP) Primary Respons ...
... Role of the Transport Layer The Transport Layer is responsible for establishing a temporary communication session between two applications and delivering data between them. TCP/IP uses two protocols to achieve this: Transmission Control Protocol (TCP) User Datagram Protocol (UDP) Primary Respons ...
CCNA2 Chapter 1 Wide Area Networks and Routers
... WAN – Wide Area Networks WAN is a data communications network that operates beyond a LAN’s geographic scope. ...
... WAN – Wide Area Networks WAN is a data communications network that operates beyond a LAN’s geographic scope. ...
Control System Specification
... 2.30. Point: Group of data, which corresponds to a single hardware input, output, or calculated value. ...
... 2.30. Point: Group of data, which corresponds to a single hardware input, output, or calculated value. ...
CORD Fabric, Overlay Virtualization, and Service Composition
... immaterial. We could have just as well used VLAN tags. However in our experience with current ASICs, it is easier to use labels instead of tags, as they are treated differently in current ASIC pipelines and there are different rules to follow and associated limitations in usage. Furthermore, Seg ...
... immaterial. We could have just as well used VLAN tags. However in our experience with current ASICs, it is easier to use labels instead of tags, as they are treated differently in current ASIC pipelines and there are different rules to follow and associated limitations in usage. Furthermore, Seg ...
Adding Location-Based Services to Existing Architectures
... 1. The “local promotion” application sends a request to the GMLC to locate a particular mobile handset. 2. The application developer’s “GMLC node” queries the HLR to determine the MSC currently visited by the specified mobile handset. The MAP message, Send Routing Info for LCS, is used to request th ...
... 1. The “local promotion” application sends a request to the GMLC to locate a particular mobile handset. 2. The application developer’s “GMLC node” queries the HLR to determine the MSC currently visited by the specified mobile handset. The MAP message, Send Routing Info for LCS, is used to request th ...
EEE449 Computer Networks - Universiti Sains Malaysia
... broad categories: elastic and inelastic. • Elastic traffic – can adjust, over wide ranges, to changes in delay and throughput across an internet and still meet the needs of its applications. – This is the traditional type of traffic supported on TCP/IP-based internets and is the type of traffic for ...
... broad categories: elastic and inelastic. • Elastic traffic – can adjust, over wide ranges, to changes in delay and throughput across an internet and still meet the needs of its applications. – This is the traditional type of traffic supported on TCP/IP-based internets and is the type of traffic for ...
Appraisal Wizard Requirements
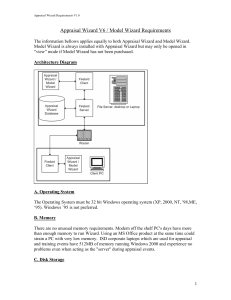
... The processor should be at least a Pentium. Faster is always better, but certainly a 400 MHZ Pentium or better will provide acceptable response. If the PC is also acting as a server for other Appraisal Wizard clients, this could become a factor in performance so a higher processor speed is recommend ...
... The processor should be at least a Pentium. Faster is always better, but certainly a 400 MHZ Pentium or better will provide acceptable response. If the PC is also acting as a server for other Appraisal Wizard clients, this could become a factor in performance so a higher processor speed is recommend ...
1 - City of San Carlos
... databases through a technique called Computer Telephony Integration. They support both analog and digital telephones, although the latter are usually proprietary to a particular vendor platform, (CTI). These systems have a long track record of very stable service with extremely reliable uptime. Conf ...
... databases through a technique called Computer Telephony Integration. They support both analog and digital telephones, although the latter are usually proprietary to a particular vendor platform, (CTI). These systems have a long track record of very stable service with extremely reliable uptime. Conf ...
Related paper.
... level approach for real-time mobile communication. If a mobile terminal roams into a foreign network, the correspondent terminal can get the address of the mobile terminal by requesting to the SIP redirect server using DHCP. By moving the mobility handling to the application layer, they eliminated t ...
... level approach for real-time mobile communication. If a mobile terminal roams into a foreign network, the correspondent terminal can get the address of the mobile terminal by requesting to the SIP redirect server using DHCP. By moving the mobility handling to the application layer, they eliminated t ...
Group 1C
... – If the Honeypot system is broken out of, then what? Is the system compromised again? – Incorrect server architecture may not correctly identify the intruder (for example if an insider can intrude from inside the network, then having a Honeypot on the external or DMZ won’t matter much) ...
... – If the Honeypot system is broken out of, then what? Is the system compromised again? – Incorrect server architecture may not correctly identify the intruder (for example if an insider can intrude from inside the network, then having a Honeypot on the external or DMZ won’t matter much) ...
internet2 network
... The New Internet2 Network • Announced at the SMM, but details had to be withheld • Will be deployed nationally over 13,000 miles of dedicated fiber using Level3 fiber and Infinera optronics across the backbone • 100G capacity to start (10x10G waves) • Sustainable model with clear path forward to 40G ...
... The New Internet2 Network • Announced at the SMM, but details had to be withheld • Will be deployed nationally over 13,000 miles of dedicated fiber using Level3 fiber and Infinera optronics across the backbone • 100G capacity to start (10x10G waves) • Sustainable model with clear path forward to 40G ...
Alhadeff - The Public Voice
... but are bound together by standardized or proprietary technology that enables data and application portability (e.g., cloud bursting for load-balancing between clouds). ...
... but are bound together by standardized or proprietary technology that enables data and application portability (e.g., cloud bursting for load-balancing between clouds). ...
Chapter 10
... Accepts IP datagrams and transmits over a specific network Can be a device driver or a complex subsystem that uses own data link protocol ...
... Accepts IP datagrams and transmits over a specific network Can be a device driver or a complex subsystem that uses own data link protocol ...
Oracle Communications ASAP Product Overview
... and continuously shrinking margins. To be successful in this environment, service providers must be first to market with new, differentiated services; offer instant activation of those services; and reduce operational expenditures by improving the way services are delivered. To do this, you must off ...
... and continuously shrinking margins. To be successful in this environment, service providers must be first to market with new, differentiated services; offer instant activation of those services; and reduce operational expenditures by improving the way services are delivered. To do this, you must off ...
Standards for multimedia communications
... • The audio and video codecs each use a particular compression algorithm which is appropriate for the application and within the bandwidth limits provided by the network. • If the user data is shared between the various members of a conference, the application uses the services provided by a protoco ...
... • The audio and video codecs each use a particular compression algorithm which is appropriate for the application and within the bandwidth limits provided by the network. • If the user data is shared between the various members of a conference, the application uses the services provided by a protoco ...
New Century Network plans to launch network gateway services
... sites from centralized servers. The new NCN gateway site, which is still unnamed, will be promoted nationally on the Web through a mix of search engines and directories, etc., as well as in print. In addition to material from its affiliate sites, the new national service may feature some third-party ...
... sites from centralized servers. The new NCN gateway site, which is still unnamed, will be promoted nationally on the Web through a mix of search engines and directories, etc., as well as in print. In addition to material from its affiliate sites, the new national service may feature some third-party ...
Chapter 1 - UniMAP Portal
... information between users at different locations. Communication services & applications are everywhere. ...
... information between users at different locations. Communication services & applications are everywhere. ...
William Stallings Data and Computer Communications
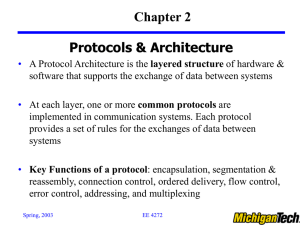
... • A Protocol Architecture is the layered structure of hardware & software that supports the exchange of data between systems • At each layer, one or more common protocols are implemented in communication systems. Each protocol provides a set of rules for the exchanges of data between systems ...
... • A Protocol Architecture is the layered structure of hardware & software that supports the exchange of data between systems • At each layer, one or more common protocols are implemented in communication systems. Each protocol provides a set of rules for the exchanges of data between systems ...