Online dating Virtual gaming Twitter LinkedIn Facebook Google +
... THE RAPID EVOLUTION OF INFORMATION TECHNOLOGY • “The sharing of information, using technology as an enabler, is a culture change that has been fully embraced by political, military, and the business communities.” • “If we do not develop robust capabilities to detect, expose, and hold accountable ...
... THE RAPID EVOLUTION OF INFORMATION TECHNOLOGY • “The sharing of information, using technology as an enabler, is a culture change that has been fully embraced by political, military, and the business communities.” • “If we do not develop robust capabilities to detect, expose, and hold accountable ...
new zealand`s cyber security strategy
... • Increasing use of internet and digital systems • Cyber threats increasing and more sophisticated – no international borders • Threats to: - individuals - government-held information - businesses and intellectual property - critical national infrastructure ...
... • Increasing use of internet and digital systems • Cyber threats increasing and more sophisticated – no international borders • Threats to: - individuals - government-held information - businesses and intellectual property - critical national infrastructure ...
Slide 1
... e-health and e-finance. 3. Legal Basis : Currently finalizing a draft law on Information Technology and Elecronic Transaction (ITET) 4. Technical Realm: Dept of Com and Inf Tech cooperation with INP and Internet Community, establishment of Indonesia Security Incident Response Team on Internet Infras ...
... e-health and e-finance. 3. Legal Basis : Currently finalizing a draft law on Information Technology and Elecronic Transaction (ITET) 4. Technical Realm: Dept of Com and Inf Tech cooperation with INP and Internet Community, establishment of Indonesia Security Incident Response Team on Internet Infras ...
Maritime Cyber Vulnerabilities in the Energy Domain
... Center for Joint Operations of the Sea ODU Maritime Institute Students Crow, Fresco, Lee ...
... Center for Joint Operations of the Sea ODU Maritime Institute Students Crow, Fresco, Lee ...
10 years APCERT - Conferences
... 2. APCERT Drill (Simulation exercise of cyber attacks) APCERT Annual Report http://www.apcert.org/documents/index.html ...
... 2. APCERT Drill (Simulation exercise of cyber attacks) APCERT Annual Report http://www.apcert.org/documents/index.html ...
An example of people trafficking in the news would be the Chinese
... • The drug trade was the first illegal sector to maximise profits in a globalised world. • Drugs are produced cheaply in South America and the Middle East and are transported to the West via ...
... • The drug trade was the first illegal sector to maximise profits in a globalised world. • Drugs are produced cheaply in South America and the Middle East and are transported to the West via ...
Breaking Trust On The Internet
... security specifically related to the Internet, often involving browser security but also network security on a more general level as it applies to other applications or operating systems on a whole. ...
... security specifically related to the Internet, often involving browser security but also network security on a more general level as it applies to other applications or operating systems on a whole. ...
One Team, One Fight
... Dr. Phyllis Schneck Deputy Under Secretary for Cybersecurity and Communications Department of Homeland Security ...
... Dr. Phyllis Schneck Deputy Under Secretary for Cybersecurity and Communications Department of Homeland Security ...
• Overview of Cyber Security & need of cyber security • Introduction
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
6_HighTechBridge_WSIS_2015_IK
... Combating cybercrime: efficiency or effectiveness? World Summit on the Information Society Forum 2015 25th of May 2015 ...
... Combating cybercrime: efficiency or effectiveness? World Summit on the Information Society Forum 2015 25th of May 2015 ...
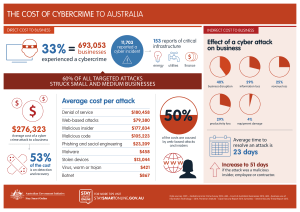
the cost of cybercrime to australia $276323
... if the attack was a malicious insider, employee or contractor. ...
... if the attack was a malicious insider, employee or contractor. ...