Sources of water in arid environments
... Mapping tectonic hazard zones Task Using the map below annotate areas of the world that are regularly exposed to tectonic hazards. Create your own key to illustrate each of the hazards. Start off by thinking about events in recent memory and then use the table at the bottom to complete some internet ...
... Mapping tectonic hazard zones Task Using the map below annotate areas of the world that are regularly exposed to tectonic hazards. Create your own key to illustrate each of the hazards. Start off by thinking about events in recent memory and then use the table at the bottom to complete some internet ...
monitor
... Continuously track changes to the information system that may affect security controls and reassess control effectiveness ...
... Continuously track changes to the information system that may affect security controls and reassess control effectiveness ...
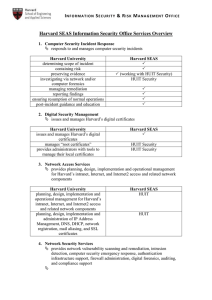
Harvard SEAS Information Security Office Services Overview
... resources notifies user or resource owner and triggers incident response service Inspects network traffic to identify security vulnerabilities in networkconnected systems or devices. monitors, detects and, as necessary, protects High Risk Confidential Information detects and reports on computers tha ...
... resources notifies user or resource owner and triggers incident response service Inspects network traffic to identify security vulnerabilities in networkconnected systems or devices. monitors, detects and, as necessary, protects High Risk Confidential Information detects and reports on computers tha ...
IT2042-UNIT3-Notes
... All information assets in the organization are subject to forces of nature, unless suitable controls are provided. This information asset has little intrinsic value, but other assets protected by this device could be attacked if it is ...
... All information assets in the organization are subject to forces of nature, unless suitable controls are provided. This information asset has little intrinsic value, but other assets protected by this device could be attacked if it is ...
presentation - Corporate Leaders
... What if IT does not provide the appropriate access controls while protecting the businessʼ information and resources ? What if IT does not maintain acceptable performance based on business needs and appropriately accommodate changes in business service volume ? What if IT does not keep systems runni ...
... What if IT does not provide the appropriate access controls while protecting the businessʼ information and resources ? What if IT does not maintain acceptable performance based on business needs and appropriately accommodate changes in business service volume ? What if IT does not keep systems runni ...
Guidelines at a Glance - American Bankers Association
... highlight eight security measures that institutions should consider and adopt if appropriate. The information security program also should include training for staff and regular testing of the key controls, systems, and procedures. The nature and frequency of the tests should be determined by the in ...
... highlight eight security measures that institutions should consider and adopt if appropriate. The information security program also should include training for staff and regular testing of the key controls, systems, and procedures. The nature and frequency of the tests should be determined by the in ...
Estimating Impact and Frequency of Risks to
... information about the existence of the vulnerability. It is evaluated as unconfirmed, uncorroborated (conflicting sources of information) or confirmed. For all three attributes the list of options reflects increasing levels of exploitability. The environmental metrics group quantifies two relevant a ...
... information about the existence of the vulnerability. It is evaluated as unconfirmed, uncorroborated (conflicting sources of information) or confirmed. For all three attributes the list of options reflects increasing levels of exploitability. The environmental metrics group quantifies two relevant a ...
Why we need IT security - Department of Computer Science and
... between communicating applications • TLS works by negotiating a unique encryption algorithm and cryptographic keys between a client and a server before data is exchanged. ...
... between communicating applications • TLS works by negotiating a unique encryption algorithm and cryptographic keys between a client and a server before data is exchanged. ...
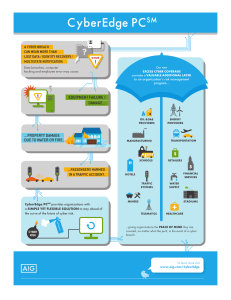
PDF Product Profile CyberEdge PC Overview
... cybersecurity failure. Where underlying insurance has cyber coverage gaps, CyberEdge PC’s difference-in-conditions features can fill in those gaps, and help organizations get the cyber risk protection they need. Additional Layer of Protection • Adds capacity above existing insurance programs solely ...
... cybersecurity failure. Where underlying insurance has cyber coverage gaps, CyberEdge PC’s difference-in-conditions features can fill in those gaps, and help organizations get the cyber risk protection they need. Additional Layer of Protection • Adds capacity above existing insurance programs solely ...
D1S1_TSV404_Course_Intro_2011_v1
... ■ Systems are inconsistently and improperly implementedeven within the same operational environment ■ Many default configurations are still set (CM-6) ■ ‘Least Privilege Principle’ is not appropriately implemented (AC-6) ■ Unsecure protocols like (ftp, telnet) ...
... ■ Systems are inconsistently and improperly implementedeven within the same operational environment ■ Many default configurations are still set (CM-6) ■ ‘Least Privilege Principle’ is not appropriately implemented (AC-6) ■ Unsecure protocols like (ftp, telnet) ...
www.itgovernance.co.uk/training
... People are your weakest link – Strengthen awareness to improve the robustness of your ISMS Training aids are a tool for getting general staff involved in discussing and understanding the sometimes complex data security issues which might impinge on how they work – and to do so in a low impact, low p ...
... People are your weakest link – Strengthen awareness to improve the robustness of your ISMS Training aids are a tool for getting general staff involved in discussing and understanding the sometimes complex data security issues which might impinge on how they work – and to do so in a low impact, low p ...
Frameworks, Standards and Regulations
... Effectiveness and efficiency of operations Reliability of financial reporting Compliance with applicable laws and regulations ...
... Effectiveness and efficiency of operations Reliability of financial reporting Compliance with applicable laws and regulations ...
Cloud Computing Security
... • Shared tenancy of physical storage resources means that sensitive data may leak because data destruction policies may be impossible to implement • Media cannot be physically destroyed because a disk is still being used by another tenant • Customer storage cannot be located or tracked as it moves t ...
... • Shared tenancy of physical storage resources means that sensitive data may leak because data destruction policies may be impossible to implement • Media cannot be physically destroyed because a disk is still being used by another tenant • Customer storage cannot be located or tracked as it moves t ...
Foundations of Information Security Webcast - ABA
... The technology must be put in place to manage and enforce security Management commitment is not difficult… if Metrics: If you can’t measure it, you can’t control it Information security bridges the business and the technology ...
... The technology must be put in place to manage and enforce security Management commitment is not difficult… if Metrics: If you can’t measure it, you can’t control it Information security bridges the business and the technology ...
Foundations of Information Security Webcast
... The technology must be put in place to manage and enforce security Management commitment is not difficult… if Metrics: If you can’t measure it, you can’t control it Information security bridges the business and the technology ...
... The technology must be put in place to manage and enforce security Management commitment is not difficult… if Metrics: If you can’t measure it, you can’t control it Information security bridges the business and the technology ...
The Information Security Jigsaw The Technical Elements
... • Need to communicate means proliferation of external connectivity on a global scale • Greater need to establish the risks • Need for a mix of solutions - this is the technical component! ...
... • Need to communicate means proliferation of external connectivity on a global scale • Greater need to establish the risks • Need for a mix of solutions - this is the technical component! ...
Security Considerations for Health Care Organizations
... followed Provide security agents Automated Continually monitor all systems ...
... followed Provide security agents Automated Continually monitor all systems ...
C.2. Vulnerabilities
... access to scripts for new projects, and digital versions of films in production, including Ocean's 11 at Warner Brothers and The One at Columbia Pictures. The attackers also retrieved and made public executives' e-mail messages. But, as is true of many computer security incidents, at least one attac ...
... access to scripts for new projects, and digital versions of films in production, including Ocean's 11 at Warner Brothers and The One at Columbia Pictures. The attackers also retrieved and made public executives' e-mail messages. But, as is true of many computer security incidents, at least one attac ...
Lecture 11.2
... information system and the potential impact the loss of information or capabilities of a system would have ...
... information system and the potential impact the loss of information or capabilities of a system would have ...
Overview of Knowledge Discovery in Databases Process and Data
... Development of more effective early warning systems (EWSs) for various applications have been possible during the past decade due to advancements in information, detection, data mining (DM) and surveillance technologies. These application areas include economy, banking, finance, health care, bioinfo ...
... Development of more effective early warning systems (EWSs) for various applications have been possible during the past decade due to advancements in information, detection, data mining (DM) and surveillance technologies. These application areas include economy, banking, finance, health care, bioinfo ...
Network Management Session 1 Network Basics
... Why not Risk Management? Time consuming! However, without proper risk management… ...
... Why not Risk Management? Time consuming! However, without proper risk management… ...
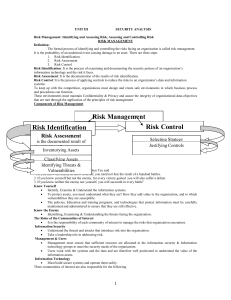
IT risk management

IT risk management is the application of risk management methods to Information technology in order to manage IT risk, i.e.:The business risk associated with the use, ownership, operation, involvement, influence and adoption of IT within an enterprise or organizationIT risk management can be considered a component of a wider enterprise risk management system.The establishment, maintenance and continuous update of an ISMS provide a strong indication that a company is using a systematic approach for the identification, assessment and management of information security risks.Different methodologies have been proposed to manage IT risks, each of them divided in processes and steps.According to Risk IT, it encompasses not just only the negative impact of operations and service delivery which can bring destruction or reduction of the value of the organization, but also the benefit\value enabling risk associated to missing opportunities to use technology to enable or enhance business or the IT project management for aspects like overspending or late delivery with adverse business impact.Because risk is strictly tied to uncertainty, Decision theory should be applied to manage risk as a science, i.e. rationally making choices under uncertainty.Generally speaking, risk is the product of likelihood times impact (Risk = Likelihood * Impact).The measure of an IT risk can be determined as a product of threat, vulnerability and asset values:Risk = Threat * Vulnerability * AssetA more current Risk management framework for IT Risk would be the TIK framework:Risk = ((Vulnerability * Threat) / Counter Measure) * Asset Value at Risk IT Risk