Document - Oman College of Management & Technology
... Main memory is a volatile storage device. It loses its contents in the case of system failure. The operating system is responsible for the following activities in connections with memory management: Keep track of which parts of memory are currently being ...
... Main memory is a volatile storage device. It loses its contents in the case of system failure. The operating system is responsible for the following activities in connections with memory management: Keep track of which parts of memory are currently being ...
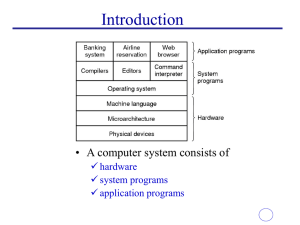
General overview of the System
... The Unix file system is characterized by : 1. A hierarchical structure – as a tree with a root 2. Consistent treatment of file data – unformatted stream of bytes 3. The ability to create and delete files 4. Dynamic growth of files 5. The protection of file data – access permissions for three classes ...
... The Unix file system is characterized by : 1. A hierarchical structure – as a tree with a root 2. Consistent treatment of file data – unformatted stream of bytes 3. The ability to create and delete files 4. Dynamic growth of files 5. The protection of file data – access permissions for three classes ...
Traditional UNIX kernels
... • Syntax: man topic • man provides online documentation on nearly every standard command and configuration file. • Optional Syntax: man -k keyword • man man for more details ...
... • Syntax: man topic • man provides online documentation on nearly every standard command and configuration file. • Optional Syntax: man -k keyword • man man for more details ...
2. OS Components
... One of the most important systems programs for an operating system is the command interpreter, which is the interface between the user and the operating system. Some operating systems include the command interpreter in the kernel. Other operating systems, such as MS-DOS and UNIX, treat the command i ...
... One of the most important systems programs for an operating system is the command interpreter, which is the interface between the user and the operating system. Some operating systems include the command interpreter in the kernel. Other operating systems, such as MS-DOS and UNIX, treat the command i ...
Operating System Overview: Part 1 1 Objectives and functions
... With multiprogramming, the overall system is quite efficient. However a problem remains. That is those jobs that come late in the batch job list won’t get chance to run until the jobs before them have completed, thus their users have to wait a long time to obtain the results. Some programs may even ...
... With multiprogramming, the overall system is quite efficient. However a problem remains. That is those jobs that come late in the batch job list won’t get chance to run until the jobs before them have completed, thus their users have to wait a long time to obtain the results. Some programs may even ...
Operating System
... System Calls • Load registers/ variables with arguments • TRAP instruction • Generates an interrupt • Automatic switch to kernel mode • Arguments tell OS what to do • Afterwards • “return” as from a function call • Force return to user mode ...
... System Calls • Load registers/ variables with arguments • TRAP instruction • Generates an interrupt • Automatic switch to kernel mode • Arguments tell OS what to do • Afterwards • “return” as from a function call • Force return to user mode ...
Introduction to Operating Systems - Seneca
... Let more than one program run at once Support multiple users Make hardware transparent so that all disk drives look alike even if made by different companies ...
... Let more than one program run at once Support multiple users Make hardware transparent so that all disk drives look alike even if made by different companies ...
Structure of Operating Systems
... Processes from Each Other • Problem: Run multiple applications in such a way that they are protected from one another ...
... Processes from Each Other • Problem: Run multiple applications in such a way that they are protected from one another ...
Operating System Structure
... Security manager • The Security manager provides a mechanism for controlling access by programs, processes, or users to both system and user resources • The protection mechanism must: – distinguish between authorized and unauthorized usage – specify the controls to be imposed – provide a means of e ...
... Security manager • The Security manager provides a mechanism for controlling access by programs, processes, or users to both system and user resources • The protection mechanism must: – distinguish between authorized and unauthorized usage – specify the controls to be imposed – provide a means of e ...
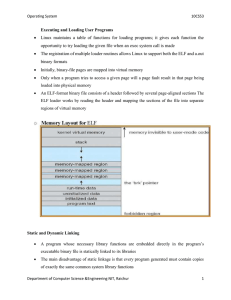
Operating System 10CS53 Executing and Loading User Programs
... o PAM is based on a shared library that can be used by any system component that needs to authenticate users o Access control under UNIX systems, including Linux, is performed through the ...
... o PAM is based on a shared library that can be used by any system component that needs to authenticate users o Access control under UNIX systems, including Linux, is performed through the ...
1 - Erode Sengunthar Engineering College
... 11.What is the need of mode bit ? In which architecture this mode bit is not applicable? To protect OS from user programs , and from shared resources , hardware support is essential. It is given by mode bit. This bit is added to the hardware of the computer to indicate the current mode If Mode bit=1 ...
... 11.What is the need of mode bit ? In which architecture this mode bit is not applicable? To protect OS from user programs , and from shared resources , hardware support is essential. It is given by mode bit. This bit is added to the hardware of the computer to indicate the current mode If Mode bit=1 ...
Operating-System Structures - Stanford Computer Graphics
... Additional functions exist not for helping the user, but rather for ensuring efficient system operations: ...
... Additional functions exist not for helping the user, but rather for ensuring efficient system operations: ...
File management
... OS keeps track of memory for each program One program runs until it needs data from the user, then the OS switches to the other program ...
... OS keeps track of memory for each program One program runs until it needs data from the user, then the OS switches to the other program ...
OS Services #1 File
... Certain systems allow system calls to be made directly from a higher level language program, in which case the calls normally resemble predefined function or subroutine calls. As an example of how system calls are used, consider writing a simple program to read data from one file and to copy them to ...
... Certain systems allow system calls to be made directly from a higher level language program, in which case the calls normally resemble predefined function or subroutine calls. As an example of how system calls are used, consider writing a simple program to read data from one file and to copy them to ...
virtual machine
... • Another set of OS functions exists for ensuring the efficient operation of the system itself via resource sharing – Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them – Accounting - To keep track of which users use how much ...
... • Another set of OS functions exists for ensuring the efficient operation of the system itself via resource sharing – Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them – Accounting - To keep track of which users use how much ...
Sec (3.2)
... The another component of kernel, which are the software units that communicates with the controllers to carry out operations on the peripheral devices attached to the machine. Each device driver is uniquely designed for its particular type of device (printer, disk drive, monitor) and translate gener ...
... The another component of kernel, which are the software units that communicates with the controllers to carry out operations on the peripheral devices attached to the machine. Each device driver is uniquely designed for its particular type of device (printer, disk drive, monitor) and translate gener ...
Operating Systems - Villanova Computer Science
... Virtual Memory - addresses the problem of a program being too big to fit into the available RAM. • The operating system divides the program into pieces. • The pieces are stored on the hard disk as if it were additional RAM memory needed by the program. • The pieces are retrieved into RAM as needed. ...
... Virtual Memory - addresses the problem of a program being too big to fit into the available RAM. • The operating system divides the program into pieces. • The pieces are stored on the hard disk as if it were additional RAM memory needed by the program. • The pieces are retrieved into RAM as needed. ...
Introduction to Computer Science
... message. The transport layer address is the process identification, called a port number. 5. What are the components of an operating system? (10%) Components of an operating systems are user interface, memory manager, process manager, device manager, and file manager. 6. How is demand paging more ef ...
... message. The transport layer address is the process identification, called a port number. 5. What are the components of an operating system? (10%) Components of an operating systems are user interface, memory manager, process manager, device manager, and file manager. 6. How is demand paging more ef ...
CSC 150 UNGRADED QUIZ - Concordia University Wisconsin
... Four main Types of command: A. Resident / internal commands. -- Always in RAM. -- Protected from being overwritten. -- Frequently used or essential. E.g. everything necessary to list directories or print. ...
... Four main Types of command: A. Resident / internal commands. -- Always in RAM. -- Protected from being overwritten. -- Frequently used or essential. E.g. everything necessary to list directories or print. ...
Document
... • No need to take out the current OS, but simply install VM. (then test and develop) • Programs cannot distinguish between execution on real or virtual hardware ...
... • No need to take out the current OS, but simply install VM. (then test and develop) • Programs cannot distinguish between execution on real or virtual hardware ...
Lecture 1: Overview - City University of New York
... Need additional hardware features to support the batch OS: ...
... Need additional hardware features to support the batch OS: ...
Chapter2
... Services provided by the O.S. • Program Creation --- editors, debuggers, ... etc.. These are in the forms of utility programs that are not actually part of the O.S. but are accessible through the O.S. • Program Execution --- to execute a program, instructions and data must be loaded into the main m ...
... Services provided by the O.S. • Program Creation --- editors, debuggers, ... etc.. These are in the forms of utility programs that are not actually part of the O.S. but are accessible through the O.S. • Program Execution --- to execute a program, instructions and data must be loaded into the main m ...