IT ESSENTIALS V. 4.1 Module 5 Fundamental Operating Systems
... The source code can be distributed and changed by anyone as a free download or from other developers 1. Supports multiple users 2. Runs multi-user applications 3. Is robust and redundant 4. Provides increased security A detailed inventory of hardware that has been tested and is known to work with th ...
... The source code can be distributed and changed by anyone as a free download or from other developers 1. Supports multiple users 2. Runs multi-user applications 3. Is robust and redundant 4. Provides increased security A detailed inventory of hardware that has been tested and is known to work with th ...
Document
... file system that provides many improvements over the old FAT file system, such as better security, extensions, longer names, etc. FAT: File Allocation Table use to be the defacto standard for all operating systems and is still supported by practically all. FAT can make due as a relatively easy to su ...
... file system that provides many improvements over the old FAT file system, such as better security, extensions, longer names, etc. FAT: File Allocation Table use to be the defacto standard for all operating systems and is still supported by practically all. FAT can make due as a relatively easy to su ...
Design of MS-DOS
... - Basis of many other Disk(based) Operating Systems. • The first personal computer DOS, called Personal Computer Disk Operating System, was developed for IBM by Microsoft Corporation. • MS retained the rights to market a Microsoft version, called MS-DOS. PC-DOS and MS-DOS are almost identical and mo ...
... - Basis of many other Disk(based) Operating Systems. • The first personal computer DOS, called Personal Computer Disk Operating System, was developed for IBM by Microsoft Corporation. • MS retained the rights to market a Microsoft version, called MS-DOS. PC-DOS and MS-DOS are almost identical and mo ...
Operating System
... Able to define and explain the major concepts which builds up an operating system ...
... Able to define and explain the major concepts which builds up an operating system ...
Example Sheet for Operating Systems I (Part IA)
... in terms of the fetch-execute cycle, including the ways in which arithmetic instructions, memory accesses and control flow instructions are handled. 4. System calls are part of most modern operating systems. (a) What is the purpose of a system call? (b) What mechanism is typically used to implement ...
... in terms of the fetch-execute cycle, including the ways in which arithmetic instructions, memory accesses and control flow instructions are handled. 4. System calls are part of most modern operating systems. (a) What is the purpose of a system call? (b) What mechanism is typically used to implement ...
Operating Systems: Principles and Practice, Introduction
... • Setup done for all collectively • Software doing this called Input/Output System – the first operating system ...
... • Setup done for all collectively • Software doing this called Input/Output System – the first operating system ...
ppt - Dave Reed`s
... job corruption handled by modes (user vs. monitor), I/O limited to monitor mode monitor corruption handled using memory protection infinite loops handled by job execution timer ...
... job corruption handled by modes (user vs. monitor), I/O limited to monitor mode monitor corruption handled using memory protection infinite loops handled by job execution timer ...
ppt - Dave Reed
... job corruption handled by modes (user vs. monitor), I/O limited to monitor mode monitor corruption handled using memory protection infinite loops handled by job execution timer ...
... job corruption handled by modes (user vs. monitor), I/O limited to monitor mode monitor corruption handled using memory protection infinite loops handled by job execution timer ...
Chapter 2 Operating System Overview
... program attempts to make use of a shared resource at the same time only one routine at at time allowed to perform an update against a given file ...
... program attempts to make use of a shared resource at the same time only one routine at at time allowed to perform an update against a given file ...
Chapter 6 An Introduction to System Software and
... Batch operating system Computer operator groups the programs into a “batch” After a few programs were collected, the operator would carry this batch of cards to a small I/O computer that would put these programs on tape. These tapes would be carried into the machine room and loaded onto the “big” co ...
... Batch operating system Computer operator groups the programs into a “batch” After a few programs were collected, the operator would carry this batch of cards to a small I/O computer that would put these programs on tape. These tapes would be carried into the machine room and loaded onto the “big” co ...
Chapter 6 An Introduction to System Software
... Batch operating system Computer operator groups the programs into a “batch” After a few programs were collected, the operator would carry this batch of cards to a small I/O computer that would put these programs on tape. These tapes would be carried into the machine room and loaded onto the “big” co ...
... Batch operating system Computer operator groups the programs into a “batch” After a few programs were collected, the operator would carry this batch of cards to a small I/O computer that would put these programs on tape. These tapes would be carried into the machine room and loaded onto the “big” co ...
System Structures
... To describe the services an operating system provides to users, processes, and other systems To discuss the various ways of structuring an operating system To explain how operating systems are installed and customized and how they boot ...
... To describe the services an operating system provides to users, processes, and other systems To discuss the various ways of structuring an operating system To explain how operating systems are installed and customized and how they boot ...
資工系網媒所NEWS實驗室Chapter 2
... Accounting - To keep track of which users use how much and what kinds of computer resources Protection and security - The owners of information stored in a multiuser or networked computer system may want to control use of that information, concurrent processes should not interfere with each other Pr ...
... Accounting - To keep track of which users use how much and what kinds of computer resources Protection and security - The owners of information stored in a multiuser or networked computer system may want to control use of that information, concurrent processes should not interfere with each other Pr ...
Operating systems and security
... vulnerability also, for much the same reason. – When a machine hibernates, entire contents (including any sensitive information) are stored to a file for quick recovery ...
... vulnerability also, for much the same reason. – When a machine hibernates, entire contents (including any sensitive information) are stored to a file for quick recovery ...
tbc 302 operating systems
... paging, page replacement and page replacement algorithms, allocation of frames, thrashing. File System: File supports, access methods, allocation methods-contiguous, linked and index allocation, directory system – single level, tree structured, acyclic graph and general graph directory, file protect ...
... paging, page replacement and page replacement algorithms, allocation of frames, thrashing. File System: File supports, access methods, allocation methods-contiguous, linked and index allocation, directory system – single level, tree structured, acyclic graph and general graph directory, file protect ...
Operating Systems
... 28. What is multi tasking, multi programming, multi threading? MultiTasking : It is a logical extension of Multi programming, multiple jobs are executed by the CPU switching between them, but the switching occurs soo frequently that the user may interact with the each program while it is running. Mu ...
... 28. What is multi tasking, multi programming, multi threading? MultiTasking : It is a logical extension of Multi programming, multiple jobs are executed by the CPU switching between them, but the switching occurs soo frequently that the user may interact with the each program while it is running. Mu ...
Best-Effort Multimedia Networking Outline
... Memory Management CPU Scheduling Process Management Device Management Hardware ...
... Memory Management CPU Scheduling Process Management Device Management Hardware ...
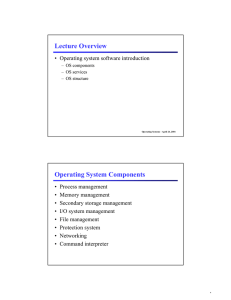
Lecture Overview Operating System Components
... extended machine with a convenient interface; it is possible to separate these two functions • A virtual machine provides multiprogramming only by providing an exact virtual copies of the bare hardware • The operating system creates the illusion of multiple processes, each executing on its own proce ...
... extended machine with a convenient interface; it is possible to separate these two functions • A virtual machine provides multiprogramming only by providing an exact virtual copies of the bare hardware • The operating system creates the illusion of multiple processes, each executing on its own proce ...
Operating Systems
... program (or OS) what to do next. Command Line Interfaces The GUI has become the standard, for years however computer OS used command line interfaces which are environments that use typewritten commands rather than graphical objects to execute tasks and process data. During the 1980s the most popular ...
... program (or OS) what to do next. Command Line Interfaces The GUI has become the standard, for years however computer OS used command line interfaces which are environments that use typewritten commands rather than graphical objects to execute tasks and process data. During the 1980s the most popular ...
PPT
... Load into memory and execute By who? People = Operators How? By mechanical switches at first, then punch cards Just one application at a time so no need for protection and no need for sharing No virtual memory; either the entire program fit into memory or programmers handled moving sections of t ...
... Load into memory and execute By who? People = Operators How? By mechanical switches at first, then punch cards Just one application at a time so no need for protection and no need for sharing No virtual memory; either the entire program fit into memory or programmers handled moving sections of t ...
OS 2200

OS 2200 is the operating system for the Unisys ClearPath Dorado family of mainframe systems. The operating system kernel of OS 2200 is a lineal descendant of Exec 8 for the UNIVAC 1108. Documentation and other information on current and past Unisys systems can be found on the Unisys public support website.See Unisys 2200 Series system architecture for a description of the machine architecture and its relationship to the OS 2200 operating system.