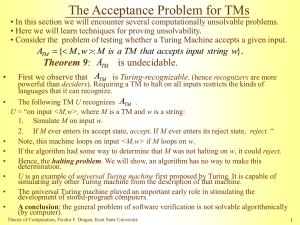
Full text
... in the sense that the algorithm takes the longest possible number of iterations to terminate, is when the sequence a > r1 > r2 > ••• > vn = 0 decreases to 0 as slowly as possible. The smallest pairs (b9a) for which this happens are found by choosing each quotient q^ to be 1 except the last one, wher ...
... in the sense that the algorithm takes the longest possible number of iterations to terminate, is when the sequence a > r1 > r2 > ••• > vn = 0 decreases to 0 as slowly as possible. The smallest pairs (b9a) for which this happens are found by choosing each quotient q^ to be 1 except the last one, wher ...
Randomized local-spin mutual exclusion
... MX lock. Then spin trying to capture node lock. • In addition to randomized and deterministic promotion, an exiting process promotes also the process that holds the MX lock, if any. ...
... MX lock. Then spin trying to capture node lock. • In addition to randomized and deterministic promotion, an exiting process promotes also the process that holds the MX lock, if any. ...
ppt
... We will use some of the formal constructs of computer languages—such as assignment statements, loops, and so forth—but we will ignore the more technical details, such as the requirement for explicit end-of-statement delimiters, the range of integer values available on a particular installation, and ...
... We will use some of the formal constructs of computer languages—such as assignment statements, loops, and so forth—but we will ignore the more technical details, such as the requirement for explicit end-of-statement delimiters, the range of integer values available on a particular installation, and ...
Some Functions Computable with a Fused-mac
... will return a NaN. Hence, our algorithm for succ(x) is always correct, unless x is a subnormal number. Function pred(x) cannot generate an overflow, correctly propagates NaNs, and correctly signal underflows, however, it does not work correctly if x is a subnormal number: that (rare) case should be ha ...
... will return a NaN. Hence, our algorithm for succ(x) is always correct, unless x is a subnormal number. Function pred(x) cannot generate an overflow, correctly propagates NaNs, and correctly signal underflows, however, it does not work correctly if x is a subnormal number: that (rare) case should be ha ...
mining on car database employing learning and clustering algorithms
... the existing volume of data which is quite large.Data mining algorithms are of various types of which clustering algorithms are also one of the type .Basically, Clustering can be considered the most important unsupervised learning problem; so, it deals with finding a structure in a collection of unl ...
... the existing volume of data which is quite large.Data mining algorithms are of various types of which clustering algorithms are also one of the type .Basically, Clustering can be considered the most important unsupervised learning problem; so, it deals with finding a structure in a collection of unl ...
Hierarchy of Languages
... • Generator: Write a program to accept A & B as input then compute the sum A+B • Recognizer: Write a program to accept A & B & C as input then determine if A+B = C We usually write Generators! But when would an Recognizer be an appropriate solution? ...
... • Generator: Write a program to accept A & B as input then compute the sum A+B • Recognizer: Write a program to accept A & B & C as input then determine if A+B = C We usually write Generators! But when would an Recognizer be an appropriate solution? ...