CHAPTER 4 Number Theory and Cryptography
... we just replace each base-64 digit by its corresponding six bits. For conversions between octal and base 64, we change the binary strings in our table to octal strings, replacing each 6-bit string by its 2-digit octal equivalent, and then follow the same procedures as above, interchanging base-64 di ...
... we just replace each base-64 digit by its corresponding six bits. For conversions between octal and base 64, we change the binary strings in our table to octal strings, replacing each 6-bit string by its 2-digit octal equivalent, and then follow the same procedures as above, interchanging base-64 di ...
Computing the Greatest Common Divisor of - CECM
... · · · + n3t ) time, where t is the number of terms in G when it is written in the collected form in the main variable x1 , and ni ’s are the numbers of terms in the coefficients of x1 . E.g. for the above example, t = 3, n1 = 2, n2 = 2, and n3 = 3. In [4], M. Javadi developed a more efficient method ...
... · · · + n3t ) time, where t is the number of terms in G when it is written in the collected form in the main variable x1 , and ni ’s are the numbers of terms in the coefficients of x1 . E.g. for the above example, t = 3, n1 = 2, n2 = 2, and n3 = 3. In [4], M. Javadi developed a more efficient method ...
Jumping Jiving GCD - the School of Mathematics, Applied
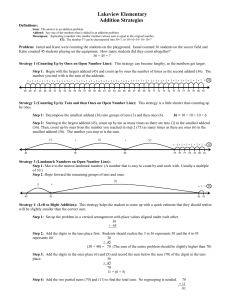
... gcd(50,75) = 25 = 5 × 5, the product of the numbers by which we simplified. That’s because 50 ÷ 5 ÷ 5 = 50 ÷ (5 × 5) = 50 ÷ 25 = 2 and 75 ÷ 5 ÷ 5 = 75 ÷ (5 × 5) = 70 ÷ 25 = 3 and 2 and 3 clearly have no other common divisors. Practice exercise: Use successive simplification to find gcd(60,84). Answe ...
... gcd(50,75) = 25 = 5 × 5, the product of the numbers by which we simplified. That’s because 50 ÷ 5 ÷ 5 = 50 ÷ (5 × 5) = 50 ÷ 25 = 2 and 75 ÷ 5 ÷ 5 = 75 ÷ (5 × 5) = 70 ÷ 25 = 3 and 2 and 3 clearly have no other common divisors. Practice exercise: Use successive simplification to find gcd(60,84). Answe ...
Efficient Pseudorandom Generators Based on the DDH Assumption
... si−1 P , i = 1, 2, . . . , k. The generator outputs k binary strings each string consisting of the 240 least significant bits of the x-coordinate of si Q. The sequence of points si Q is shown to be indistinguishable from the sequence of uniformly random points of the elliptic curve under the assumpt ...
... si−1 P , i = 1, 2, . . . , k. The generator outputs k binary strings each string consisting of the 240 least significant bits of the x-coordinate of si Q. The sequence of points si Q is shown to be indistinguishable from the sequence of uniformly random points of the elliptic curve under the assumpt ...
Best Keyword Cover Search
... In keyword-NNE algorithm, the best-first browsing strategy is applied like BF-baseline but large memory requirement is avoided. For the better explanation, we can imagine all candidate keyword covers generated in BF-baseline algorithm are grouped into independent groups. Each group is associated wit ...
... In keyword-NNE algorithm, the best-first browsing strategy is applied like BF-baseline but large memory requirement is avoided. For the better explanation, we can imagine all candidate keyword covers generated in BF-baseline algorithm are grouped into independent groups. Each group is associated wit ...
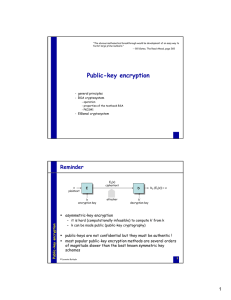
Public-key encryption
... class NP: – problems solvable with an algorithm that is non-deterministic and run in p-time on a non-deterministic machine – problems in NP have no known deterministic p-time algorithms • asymptotic worst case complexity of the most efficient algorithms known is often an exponential function of th ...
... class NP: – problems solvable with an algorithm that is non-deterministic and run in p-time on a non-deterministic machine – problems in NP have no known deterministic p-time algorithms • asymptotic worst case complexity of the most efficient algorithms known is often an exponential function of th ...
Range-Efficient Counting of Distinct Elements in a Massive Data
... 1.1. Our results. We consider the problem of range-efficient computation of F0 , defined as follows. The input stream is R = r1 , r2 , . . . , rm , where each stream element ri = [xi , yi ] ⊂ [1, n] is an interval of integers xi , xi + 1, . . . , yi . The length of an interval ri could be any number be ...
... 1.1. Our results. We consider the problem of range-efficient computation of F0 , defined as follows. The input stream is R = r1 , r2 , . . . , rm , where each stream element ri = [xi , yi ] ⊂ [1, n] is an interval of integers xi , xi + 1, . . . , yi . The length of an interval ri could be any number be ...
Solution
... In the following, use either a direct proof (by giving values for c and n0 in the definition of big-Oh notation) or cite one of the rules given in the book or in the lecture slides. (a) Show that if f(n) is O(g(n)) and d(n) is O(h(n)), then f(n)+d(n) is O(g(n)+ h(n)). Solution Recall the de_nition o ...
... In the following, use either a direct proof (by giving values for c and n0 in the definition of big-Oh notation) or cite one of the rules given in the book or in the lecture slides. (a) Show that if f(n) is O(g(n)) and d(n) is O(h(n)), then f(n)+d(n) is O(g(n)+ h(n)). Solution Recall the de_nition o ...
Sieve of Eratosthenes

In mathematics, the sieve of Eratosthenes (Ancient Greek: κόσκινον Ἐρατοσθένους, kóskinon Eratosthénous), one of a number of prime number sieves, is a simple, ancient algorithm for finding all prime numbers up to any given limit. It does so by iteratively marking as composite (i.e., not prime) the multiples of each prime, starting with the multiples of 2.The multiples of a given prime are generated as a sequence of numbers starting from that prime, with constant difference between them that is equal to that prime. This is the sieve's key distinction from using trial division to sequentially test each candidate number for divisibility by each prime.The sieve of Eratosthenes is one of the most efficient ways to find all of the smaller primes. It is named after Eratosthenes of Cyrene, a Greek mathematician; although none of his works have survived, the sieve was described and attributed to Eratosthenes in the Introduction to Arithmetic by Nicomachus.The sieve may be used to find primes in arithmetic progressions.