HDD for Operating System Concepts
... Education and Research Department, Infosys Technologies Limited. This document is not for general distribution and is meant for use only for the person they are specifically issued to. This document shall not be loaned to anyone, within or outside Infosys, including its customers. Copying or unautho ...
... Education and Research Department, Infosys Technologies Limited. This document is not for general distribution and is meant for use only for the person they are specifically issued to. This document shall not be loaned to anyone, within or outside Infosys, including its customers. Copying or unautho ...
ch21-The_Linux_System
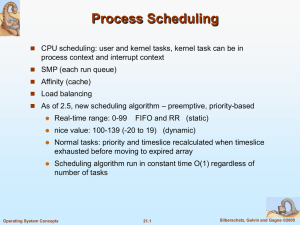
... 1. Normal kernel code is nonpreemptible (until 2.4) – when a time interrupt is received while a process is executing a kernel system service routine, the kernel’s need_resched flag is set so that the scheduler will run once the system call has completed and control is ...
... 1. Normal kernel code is nonpreemptible (until 2.4) – when a time interrupt is received while a process is executing a kernel system service routine, the kernel’s need_resched flag is set so that the scheduler will run once the system call has completed and control is ...
2.01 - Faculty of Computer Science and Information Technology
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them ...
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them ...
Module 3: Operating
... • Program execution – system capability to load a program into memory and to run it. • I/O operations – since user programs cannot execute I/O operations directly, the operating system must provide some means to perform I/O. • File-system manipulation – program capability to read, write, create, and ...
... • Program execution – system capability to load a program into memory and to run it. • I/O operations – since user programs cannot execute I/O operations directly, the operating system must provide some means to perform I/O. • File-system manipulation – program capability to read, write, create, and ...
Process Description and Control
... to keep track of procedure calls and parameter passing between procedures. Finally, each process has associated with it a number of attributes that are used by the operating system for process control. Typically the operating system needs to maintain a structure called process control block (PCB) co ...
... to keep track of procedure calls and parameter passing between procedures. Finally, each process has associated with it a number of attributes that are used by the operating system for process control. Typically the operating system needs to maintain a structure called process control block (PCB) co ...
CIS162AB
... data and check the results. If it was incorrect, we would change the program, run it again, and reenter the data. Depending on the application, it may be more efficient to capture the raw data the first time it is entered and store in a file. A program or many different programs can then read ...
... data and check the results. If it was incorrect, we would change the program, run it again, and reenter the data. Depending on the application, it may be more efficient to capture the raw data the first time it is entered and store in a file. A program or many different programs can then read ...
Evolution of the Windows Kernel Architecture
... Kernel Architect at Microsoft for over 13 years Managed platform-independent kernel development in Win2K/XP Working on multi-core & heterogeneous parallel computing support Architect for UMS in Windows 7 / Windows Server 2008 R2 ...
... Kernel Architect at Microsoft for over 13 years Managed platform-independent kernel development in Win2K/XP Working on multi-core & heterogeneous parallel computing support Architect for UMS in Windows 7 / Windows Server 2008 R2 ...
Lecture 1 Operating System Overview
... Memory management of I/O including buffering (storing data temporarily while it is being transferred), caching (storing parts of data in faster storage for performance), spooling (the overlapping of output of one job with input of other jobs) ...
... Memory management of I/O including buffering (storing data temporarily while it is being transferred), caching (storing parts of data in faster storage for performance), spooling (the overlapping of output of one job with input of other jobs) ...
Introduction to Object Technology
... • Responsible for managing all computer resources • Functions same way as ordinary computer software – It is program that is executed ...
... • Responsible for managing all computer resources • Functions same way as ordinary computer software – It is program that is executed ...
2015 test - Department of Computer Science
... [1 mark] Why were time sharing systems developed? ...
... [1 mark] Why were time sharing systems developed? ...
CS3204 Operating Systems - Spring 2001 Instructor: Dr. Craig A
... (, ) ERROR:
where is the file containing the error (input or job file), is the line number
in the file containing the error, and is a message describing the error
that occurred.
You may assume that each line of the input and job files corresp ...
... (
Last Class: Processes Example Unix Program: Fork
... Scheduling Policies ! Ideally, choose a CPU scheduler that optimizes all criteria simultaneously (utilization, throughput,..), but this is not generally possible Instead, choose a scheduling algorithm based on its ability to satisfy a policy • Minimize average response time - provide output to the ...
... Scheduling Policies ! Ideally, choose a CPU scheduler that optimizes all criteria simultaneously (utilization, throughput,..), but this is not generally possible Instead, choose a scheduling algorithm based on its ability to satisfy a policy • Minimize average response time - provide output to the ...
ppt
... – Cap: Process can pass capability at run time – ACL: Try to get owner to add permission to list? • More common: let other process act under current user • Revocation – ACL: Remove user or group from list – Cap: Try to get capability back from process? • Possible in some systems if appropriate bookk ...
... – Cap: Process can pass capability at run time – ACL: Try to get owner to add permission to list? • More common: let other process act under current user • Revocation – ACL: Remove user or group from list – Cap: Try to get capability back from process? • Possible in some systems if appropriate bookk ...
Slides for Week 1
... Systems in one organisation have to integrate with systems in another Systems are usually developed in complete isolation from each other – often many years apart. They use different data definitions, different coding structures, different data values These systems still have to work together. Week ...
... Systems in one organisation have to integrate with systems in another Systems are usually developed in complete isolation from each other – often many years apart. They use different data definitions, different coding structures, different data values These systems still have to work together. Week ...
an introduction to solaris
... Sun’s UNIX operating environment began life as a port of BSD UNIX to the Sun-1 workstation. The early versions of Sun’s UNIX were known as SunOS, which is the name used for the core operating system component of Solaris. SunOS 1.0 was based on a port of BSD 4.1 from Berkeley labs in 1982. At that ti ...
... Sun’s UNIX operating environment began life as a port of BSD UNIX to the Sun-1 workstation. The early versions of Sun’s UNIX were known as SunOS, which is the name used for the core operating system component of Solaris. SunOS 1.0 was based on a port of BSD 4.1 from Berkeley labs in 1982. At that ti ...
Powerpoint format - Computer and Information Sciences
... scheduling priority of the process. In some systems, several values are required (e.g., default, current, highest-allowable) ••Scheduling-related information: This will depend on the scheduling algorithm used. Examples are the amount of time that the process has been waiting and the amount of time t ...
... scheduling priority of the process. In some systems, several values are required (e.g., default, current, highest-allowable) ••Scheduling-related information: This will depend on the scheduling algorithm used. Examples are the amount of time that the process has been waiting and the amount of time t ...
[slides] Case study: Linux
... specify processes to the operating system when an application makes a system call to signal, modify, or wait for another process Credentials. Each process must have an associated user ID and one or more group IDs that determine the process’s rights to access system resources and files Personalit ...
... specify processes to the operating system when an application makes a system call to signal, modify, or wait for another process Credentials. Each process must have an associated user ID and one or more group IDs that determine the process’s rights to access system resources and files Personalit ...
05_Concurrency-Mutex&Synchronization
... Enforce Single Access • If we enforce a rule that only one process may enter the function at a time then: • P1 & P2 run on separate processors • P1 enters echo first, – P2 tries to enter but is blocked – P2 suspends ...
... Enforce Single Access • If we enforce a rule that only one process may enter the function at a time then: • P1 & P2 run on separate processors • P1 enters echo first, – P2 tries to enter but is blocked – P2 suspends ...
COMP25111: Operating Systems - Lecture 4: Operating System
... For next time Which of the following operations would you expect to be privileged (available only in System mode) & which available in User mode? – halt the processor? – system call? – write an absolute memory location? – load register from memory? – disable interrupts? – load stack pointer? – writ ...
... For next time Which of the following operations would you expect to be privileged (available only in System mode) & which available in User mode? – halt the processor? – system call? – write an absolute memory location? – load register from memory? – disable interrupts? – load stack pointer? – writ ...
Interrupts and Interrupt Handlers
... Top half: alert the kernel to optimize network throughput, latency and avoid timeout. ACK hardware, copy packets to memory and ready network card for more packets ...
... Top half: alert the kernel to optimize network throughput, latency and avoid timeout. ACK hardware, copy packets to memory and ready network card for more packets ...
Introduction
... Answer: It reads commands from the user or from a file of commands and executes them, usually by turning them into one or more system calls. It is usually not part of the kernel since the command interpreter is subject to changes. An user should be able to develop a new command interpreter using the ...
... Answer: It reads commands from the user or from a file of commands and executes them, usually by turning them into one or more system calls. It is usually not part of the kernel since the command interpreter is subject to changes. An user should be able to develop a new command interpreter using the ...
solutions - CIS @ UPenn
... pro - reduces internal fragmentation, better with locality ofreference con - bigger page table, more page faults, overhead in reading/writing of pages 3. Describe the three possible states of a process? Answer: Running: actually using the CPU at that time Ready: runnable; temporarily stopped to let ...
... pro - reduces internal fragmentation, better with locality ofreference con - bigger page table, more page faults, overhead in reading/writing of pages 3. Describe the three possible states of a process? Answer: Running: actually using the CPU at that time Ready: runnable; temporarily stopped to let ...















![[slides] Case study: Linux](http://s1.studyres.com/store/data/008426094_1-33a53a235a0b160ad065c81f93e7bd9c-300x300.png)