ing systems were being developed in the
... rebooting the operating system after a crash faster, but does not address the fundamental problem of every line of code being critical. What is required is splitting the core of the operating system functionality—including the file system, process management, and graphics—into multiple processes, pu ...
... rebooting the operating system after a crash faster, but does not address the fundamental problem of every line of code being critical. What is required is splitting the core of the operating system functionality—including the file system, process management, and graphics—into multiple processes, pu ...
Privacy Preserving Data Sharing With Anonymous ID Assignment
... This technique is used iteratively to assign these nodes ID numbers ranging from 1 to N. This assignment is anonymous in that the identities received are unknown to the other members of the group. Resistance to collusion among other members is verified in an information theoretic sense when private ...
... This technique is used iteratively to assign these nodes ID numbers ranging from 1 to N. This assignment is anonymous in that the identities received are unknown to the other members of the group. Resistance to collusion among other members is verified in an information theoretic sense when private ...
Basic Operating System Concepts
... Time sharing: An extension of multiprogramming. After a certain amount of time the CPU is switched to another job regardless of whether the process/thread needs to wait for some operation. Switching between jobs occurs so frequently that the users can interact with each program while it is running. ...
... Time sharing: An extension of multiprogramming. After a certain amount of time the CPU is switched to another job regardless of whether the process/thread needs to wait for some operation. Switching between jobs occurs so frequently that the users can interact with each program while it is running. ...
Module 3: Operating
... Protection refers to a mechanism for controlling access by programs, processes, or users to both system and user resources. The protection mechanism must: – distinguish between authorized and unauthorized usage. – specify the controls to be imposed. – provide a means of enforcement. ...
... Protection refers to a mechanism for controlling access by programs, processes, or users to both system and user resources. The protection mechanism must: – distinguish between authorized and unauthorized usage. – specify the controls to be imposed. – provide a means of enforcement. ...
Moto00 - BNRG - University of California, Berkeley
... “Today, the telecommunications sector is beginning to reshape itself, from a vertically to a horizontally structured industry. … [I]t used to be that new capabilities were driven primarily by the carriers. Now, they are beginning to be driven by the users. … There’s a universe of people out there wh ...
... “Today, the telecommunications sector is beginning to reshape itself, from a vertically to a horizontally structured industry. … [I]t used to be that new capabilities were driven primarily by the carriers. Now, they are beginning to be driven by the users. … There’s a universe of people out there wh ...
N4Less11
... • Some operating systems, such as Windows, enable programs to share information. • You can create data in one program and use it again in other programs without re-creating it. • Windows provides the Clipboard, a special area that stores data cut or copied from one document, so you can re-use it els ...
... • Some operating systems, such as Windows, enable programs to share information. • You can create data in one program and use it again in other programs without re-creating it. • Windows provides the Clipboard, a special area that stores data cut or copied from one document, so you can re-use it els ...
Lecture 2
... tools rather write a new one. 4. Create the design first, then start with a small prototype and add features incrementally. ...
... tools rather write a new one. 4. Create the design first, then start with a small prototype and add features incrementally. ...
Chapter 10.slides
... Redundancy is designed into the IP network by Routes and object references can be replicated its managers, ensuring tolerance of a single n-fold, ensuring tolerance of n failures of nodes router or network connectivity failure. n-fold or connections. replication is costly. Each IP address maps to ex ...
... Redundancy is designed into the IP network by Routes and object references can be replicated its managers, ensuring tolerance of a single n-fold, ensuring tolerance of n failures of nodes router or network connectivity failure. n-fold or connections. replication is costly. Each IP address maps to ex ...
ICS 143 - Introduction to Operating Systems
... Need to understand basic principles in the design of computer systems efficient resource management, security, flexibility ...
... Need to understand basic principles in the design of computer systems efficient resource management, security, flexibility ...
SCADA Systems
... regulators. We need also screen forms process parameters indicators of different types: arrows-based, shift-based, digital indicators, and also alerting tables of different form and contents. Also, we need possibility of creation of archives of events and keep track of variables behavior with time r ...
... regulators. We need also screen forms process parameters indicators of different types: arrows-based, shift-based, digital indicators, and also alerting tables of different form and contents. Also, we need possibility of creation of archives of events and keep track of variables behavior with time r ...
CS423/523
... – Allows multiple processes to share resources of processor fairly – Does this by scheduling processes to get execution time • User Processes • Microsoft Word, Foxfire or Skype • System Processes: • Print spooler, network connections, security accounts manager ... plus many others ...
... – Allows multiple processes to share resources of processor fairly – Does this by scheduling processes to get execution time • User Processes • Microsoft Word, Foxfire or Skype • System Processes: • Print spooler, network connections, security accounts manager ... plus many others ...
Distributed Operating Systems Introduction
... Concurrency Ability to processing multiple tasks at the same time ...
... Concurrency Ability to processing multiple tasks at the same time ...
Communication Layered Protocols
... Let the developer concentrate on only the client- and server-specific code; let the RPC system (generators and libraries) do the rest. ...
... Let the developer concentrate on only the client- and server-specific code; let the RPC system (generators and libraries) do the rest. ...
MultiOS1v6 - Trinity College Dublin
... installed, as though the network interrogation phase never occurred. 2.3 A Special Management Environment which does not use the Local Disk. This special management environment could be a specialised program, or a suite of specialised programs. Many already exist [10, 11, 12], but hardcoded solution ...
... installed, as though the network interrogation phase never occurred. 2.3 A Special Management Environment which does not use the Local Disk. This special management environment could be a specialised program, or a suite of specialised programs. Many already exist [10, 11, 12], but hardcoded solution ...
PPT
... • What an OS can do is dictated, at least in part, by the architecture. • Architecture support can greatly simplify (or complicate) OS tasks • Example: PC operating systems have been primitive, in part because PCs lacked hardware support (e.g., for VM) ...
... • What an OS can do is dictated, at least in part, by the architecture. • Architecture support can greatly simplify (or complicate) OS tasks • Example: PC operating systems have been primitive, in part because PCs lacked hardware support (e.g., for VM) ...
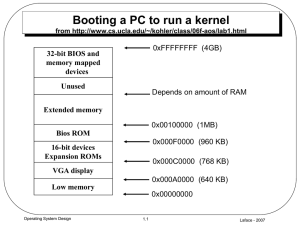
Booting a PC
... The 384KB area from 0x000A0000 through 0x000FFFFF was reserved by the hardware for special uses such as video display buffers and firmware held in nonvolatile memory. The most important part of this reserved area is the Basic Input/Output System (BIOS), which occupies the 64KB region from 0x000F0000 ...
... The 384KB area from 0x000A0000 through 0x000FFFFF was reserved by the hardware for special uses such as video display buffers and firmware held in nonvolatile memory. The most important part of this reserved area is the Basic Input/Output System (BIOS), which occupies the 64KB region from 0x000F0000 ...
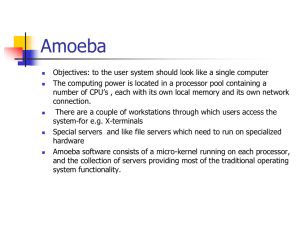
Chorusamoeba
... 80 single-board SPARC computers connected by an Ethernet, forming a powerful processor pool. [Amoeba 1996 ] ...
... 80 single-board SPARC computers connected by an Ethernet, forming a powerful processor pool. [Amoeba 1996 ] ...
Introduction to Object Technology
... • Need for a new operating system – MS-DOS/PC-DOS did not use the full capabilities of the evolving processors: 80286, 80386, 80486 and then Pentium (e.g., extended addressing, memory protection) – To compete with Macintosh, in 1990 Microsoft developed a graphical user interface (GUI), Windows 3.0, ...
... • Need for a new operating system – MS-DOS/PC-DOS did not use the full capabilities of the evolving processors: 80286, 80386, 80486 and then Pentium (e.g., extended addressing, memory protection) – To compete with Macintosh, in 1990 Microsoft developed a graphical user interface (GUI), Windows 3.0, ...
Preface
... hope that practitioners will also find it useful. It provides a clear description of the concepts that underlie operating systems. As prerequisites, we assume that the reader is familiar with basic data structures, computer organization, and a high-level language, such as C or Java. The hardware top ...
... hope that practitioners will also find it useful. It provides a clear description of the concepts that underlie operating systems. As prerequisites, we assume that the reader is familiar with basic data structures, computer organization, and a high-level language, such as C or Java. The hardware top ...
Distributed operating system
A distributed operating system is a software over a collection of independent, networked, communicating, and physically separate computational nodes. Each individual node holds a specific software subset of the global aggregate operating system. Each subset is a composite of two distinct service provisioners. The first is a ubiquitous minimal kernel, or microkernel, that directly controls that node’s hardware. Second is a higher-level collection of system management components that coordinate the node's individual and collaborative activities. These components abstract microkernel functions and support user applications.The microkernel and the management components collection work together. They support the system’s goal of integrating multiple resources and processing functionality into an efficient and stable system. This seamless integration of individual nodes into a global system is referred to as transparency, or single system image; describing the illusion provided to users of the global system’s appearance as a single computational entity.