SASEC2015 Third Southern African Solar Energy Conference 11 – 13 May 2015
... such as analytical, heuristic, meta-heuristic, etc. As DG placement problem is a mixed integer, non-linear, highly complex combinatorial optimization problem where certain operational and network constraints are to be satisfied, so modern meta-heuristic methods have more potential to solve this prob ...
... such as analytical, heuristic, meta-heuristic, etc. As DG placement problem is a mixed integer, non-linear, highly complex combinatorial optimization problem where certain operational and network constraints are to be satisfied, so modern meta-heuristic methods have more potential to solve this prob ...
Document
... technology to disseminate computational tasks over multiple clients; peers do not have a direct connection to one another. ...
... technology to disseminate computational tasks over multiple clients; peers do not have a direct connection to one another. ...
ppt
... The ability to distinguish between data and programs is a useful security feature, providing a basis for protecting programs from modification. ...
... The ability to distinguish between data and programs is a useful security feature, providing a basis for protecting programs from modification. ...
Korea Univ Real-Time Systems
... Embedded versions of Linux are designed for devices with relatively limited resources, such as cell phones and set-top boxes Due to concerns such as cost and size, embedded devices usually have much less RAM and secondary storage than desktop computers, and are likely to use flash memory instead ...
... Embedded versions of Linux are designed for devices with relatively limited resources, such as cell phones and set-top boxes Due to concerns such as cost and size, embedded devices usually have much less RAM and secondary storage than desktop computers, and are likely to use flash memory instead ...
Operating System
... This shell is a hit with those who are seriously into Unix programming. It was created by Bill Joy, then pursuing his graduation at the University of California at Berkeley. It has two advantages over the Bourne ...
... This shell is a hit with those who are seriously into Unix programming. It was created by Bill Joy, then pursuing his graduation at the University of California at Berkeley. It has two advantages over the Bourne ...
Abstract - Chennai Sunday
... for fast re-route in the event of an arc failure, which is the target application, c_(i, j) represents the shortest path cost before the IGP has reconverged in response to the link failure. Multipath Routing: Multipath routing is a promising routing scheme to accommodate these requirements by using ...
... for fast re-route in the event of an arc failure, which is the target application, c_(i, j) represents the shortest path cost before the IGP has reconverged in response to the link failure. Multipath Routing: Multipath routing is a promising routing scheme to accommodate these requirements by using ...
- Mitra.ac.in
... journaling file systems are also typically faster than non-journaling systems, as updates proceed much faster when they are applied to the in-memory journal rather than directly to the on-disk data structures. ...
... journaling file systems are also typically faster than non-journaling systems, as updates proceed much faster when they are applied to the in-memory journal rather than directly to the on-disk data structures. ...
Chap 01 -Tbook.Ver.9
... temporarily while it is being transferred), caching (storing parts of data in faster storage for performance), spooling (the overlapping of output of one job with input of other jobs) ...
... temporarily while it is being transferred), caching (storing parts of data in faster storage for performance), spooling (the overlapping of output of one job with input of other jobs) ...
Operating Systems (G53OPS) - Examination Question 1 Operating
... Note: Stallings distinguishes general devices, communication devices and file systems. Each has a hardware, a scheduling and controlling and a device I/O layer (driver). The top layer is always “user processes”. The one layer in between is different in the three cases: “logical I/O”, “Communication ...
... Note: Stallings distinguishes general devices, communication devices and file systems. Each has a hardware, a scheduling and controlling and a device I/O layer (driver). The top layer is always “user processes”. The one layer in between is different in the three cases: “logical I/O”, “Communication ...
2000 - 2001
... Note: Stallings distinguishes general devices, communication devices and file systems. Each has a hardware, a scheduling and controlling and a device I/O layer (driver). The top layer is always “user processes”. The one layer in between is different in the three cases: “logical I/O”, “Communication ...
... Note: Stallings distinguishes general devices, communication devices and file systems. Each has a hardware, a scheduling and controlling and a device I/O layer (driver). The top layer is always “user processes”. The one layer in between is different in the three cases: “logical I/O”, “Communication ...
CER04-slide
... 2: Energy of non-active nodes in passive state 3: Energy consumed in sleep state ...
... 2: Energy of non-active nodes in passive state 3: Energy consumed in sleep state ...
I/O Systems - Ubiquitous Computing Lab
... • Arm only goes as far as the last request in each direction, then reverses direction immediately, without first going all the way to the end of the disk. ...
... • Arm only goes as far as the last request in each direction, then reverses direction immediately, without first going all the way to the end of the disk. ...
Basic Concepts of Real Time Operating Systems
... to be applied. In principle scheduling is an on-line algorithm. Under certain assumptions large parts of scheduling can be done off-line. Generating static cyclic schedules may serve as an example. In any case all exact or heuristic algorithms should have very low complexity. In principle scheduling ...
... to be applied. In principle scheduling is an on-line algorithm. Under certain assumptions large parts of scheduling can be done off-line. Generating static cyclic schedules may serve as an example. In any case all exact or heuristic algorithms should have very low complexity. In principle scheduling ...
PPT - Surendar Chandra
... File Sharing – Consistency Semantics Consistency semantics specify how multiple users are to access a shared file simultaneously Similar to Ch 7 process synchronization algorithms ...
... File Sharing – Consistency Semantics Consistency semantics specify how multiple users are to access a shared file simultaneously Similar to Ch 7 process synchronization algorithms ...
Operating System
... Operating system (OS) (sometimes called the platform) coordinates all activities among computer hardware resources ...
... Operating system (OS) (sometimes called the platform) coordinates all activities among computer hardware resources ...
Active Scanning Example - IEEE 802 LAN/MAN Standards Committee
... • 802.11 provides for an Authentication mechanism – To aid in access control. – Has provisions for “OPEN”, “Shared Key” or proprietary authentication extensions. ...
... • 802.11 provides for an Authentication mechanism – To aid in access control. – Has provisions for “OPEN”, “Shared Key” or proprietary authentication extensions. ...
Identifying Security Risks
... • In practice, almost every resource in the computer, such as the memory and the microprocessor (central processing unit or CPU), is managed by the operating system • One of the major reasons for giving operating systems so much control over resources is to facilitate multitasking, a technique that ...
... • In practice, almost every resource in the computer, such as the memory and the microprocessor (central processing unit or CPU), is managed by the operating system • One of the major reasons for giving operating systems so much control over resources is to facilitate multitasking, a technique that ...
U N I T
... For data grids: • The ability to integrate multiple distributed, heterogeneous, and independently managed data sources. • The ability to provide efficient data transfer mechanisms to provide data where the computation will take place. • The ability to provide necessary data discovery mechanism, whic ...
... For data grids: • The ability to integrate multiple distributed, heterogeneous, and independently managed data sources. • The ability to provide efficient data transfer mechanisms to provide data where the computation will take place. • The ability to provide necessary data discovery mechanism, whic ...
Chapter 17 Network Management
... Configuration and Name Management Overview • Choose appropriate software and attributes and values (e.g., a transport layer retransmission timer) for device depending on function(s) • Initializing network and gracefully shutting down • Maintaining, adding, and updating relationships ...
... Configuration and Name Management Overview • Choose appropriate software and attributes and values (e.g., a transport layer retransmission timer) for device depending on function(s) • Initializing network and gracefully shutting down • Maintaining, adding, and updating relationships ...
Distributed operating system
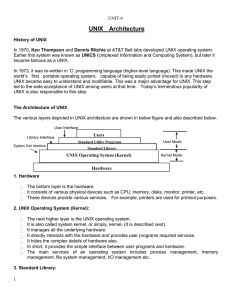
A distributed operating system is a software over a collection of independent, networked, communicating, and physically separate computational nodes. Each individual node holds a specific software subset of the global aggregate operating system. Each subset is a composite of two distinct service provisioners. The first is a ubiquitous minimal kernel, or microkernel, that directly controls that node’s hardware. Second is a higher-level collection of system management components that coordinate the node's individual and collaborative activities. These components abstract microkernel functions and support user applications.The microkernel and the management components collection work together. They support the system’s goal of integrating multiple resources and processing functionality into an efficient and stable system. This seamless integration of individual nodes into a global system is referred to as transparency, or single system image; describing the illusion provided to users of the global system’s appearance as a single computational entity.