ppt - Purdue University :: Computer Science
... / - Root Directory /etc OS Configuration files /etc/passwd – User information /etc/groups – Group information /etc/inetd.conf – Configuration of Internet Services (deamons) /etc/rc.*/ - OS initialization scripts for different services. ...
... / - Root Directory /etc OS Configuration files /etc/passwd – User information /etc/groups – Group information /etc/inetd.conf – Configuration of Internet Services (deamons) /etc/rc.*/ - OS initialization scripts for different services. ...
Example Sheet for Operating Systems I (Part IA)
... (b) A Unix system administrator decides to make a ‘versioned’ file-system in which there are a number of directories called /root-dd-mm-yyyy, each of which holds a copy of the file-system on day dd, month mm and year yyyy. The idea is that at any particular time only the most recent snapshot will be ...
... (b) A Unix system administrator decides to make a ‘versioned’ file-system in which there are a number of directories called /root-dd-mm-yyyy, each of which holds a copy of the file-system on day dd, month mm and year yyyy. The idea is that at any particular time only the most recent snapshot will be ...
Operating Systems 2
... decompress data, software for presenting multimedia presentation, software for handling network communication. ...
... decompress data, software for presenting multimedia presentation, software for handling network communication. ...
Employee exit checklist
... You can use this checklist to help you conduct an efficient exit process when an employee is leaving your business. Tick when Tasks complete Arrange for the person to do a formal handover to someone within the business or to write procedures explaining any complicated parts of their job Conduct an e ...
... You can use this checklist to help you conduct an efficient exit process when an employee is leaving your business. Tick when Tasks complete Arrange for the person to do a formal handover to someone within the business or to write procedures explaining any complicated parts of their job Conduct an e ...
Security - NYU Stern School of Business
... Your antivirus program from yesterday is useless for today’s virus! • Stern approach: Every time the user logs in to his machine the computer downloads the most current version of antivirus software from the network ...
... Your antivirus program from yesterday is useless for today’s virus! • Stern approach: Every time the user logs in to his machine the computer downloads the most current version of antivirus software from the network ...
OS Components and Structure
... Realize that it’s never as simple as it looks. These basic concepts exist in some form in all systems, however each system implements them in a slightly different way. Also, the divisions between components may not be as clean in the real world as in the model ...
... Realize that it’s never as simple as it looks. These basic concepts exist in some form in all systems, however each system implements them in a slightly different way. Also, the divisions between components may not be as clean in the real world as in the model ...
2.01
... Protection and security - The owners of information stored in a multiuser or networked computer system may want to control use of that information, concurrent processes should not interfere with each other ...
... Protection and security - The owners of information stored in a multiuser or networked computer system may want to control use of that information, concurrent processes should not interfere with each other ...
Lecture 22 File-System Interface
... collection of similar records treated as a single entity have unique file names may restrict access ...
... collection of similar records treated as a single entity have unique file names may restrict access ...
Operating System - GCG-42
... Over the years the Microsoft have evolved various versions of Windows. Win95, Win98, Win2000, Win ME, Win NT, Win XP. It gives user a handy environment where he doesn’t have to remember and learn the syntaxes of various commands as is the case in DOS. The user can just point and click on the I ...
... Over the years the Microsoft have evolved various versions of Windows. Win95, Win98, Win2000, Win ME, Win NT, Win XP. It gives user a handy environment where he doesn’t have to remember and learn the syntaxes of various commands as is the case in DOS. The user can just point and click on the I ...
Operating Systems Course Outline
... Rationale: Operating systems are central to computing activities. An operating system is a program that acts as an intermediary between a user of a computer and the computer hardware. Two primary aims of an operating systems are to manage resources (e.g. CPU time, memory) and to control users and so ...
... Rationale: Operating systems are central to computing activities. An operating system is a program that acts as an intermediary between a user of a computer and the computer hardware. Two primary aims of an operating systems are to manage resources (e.g. CPU time, memory) and to control users and so ...
Chap-2-Architecture
... single hierarchical structure. – Can be moved from one place to another – It considers even directories and devices as a single file system The Process is an entity, name given to a file wen its executed as a program – IT also belongs to a separate hierarchical tree structure ...
... single hierarchical structure. – Can be moved from one place to another – It considers even directories and devices as a single file system The Process is an entity, name given to a file wen its executed as a program – IT also belongs to a separate hierarchical tree structure ...
lecture notes
... Other operating system services: Inter-Process Communications (IPC) ▪ Processes exchange information via shared memory, message passing, sockets, pipes, files, etc. ▪ Often spans multiple computers and networks Error detection and recovery ▪ Detect errors in CPU, memory, I/O devices, processes, ...
... Other operating system services: Inter-Process Communications (IPC) ▪ Processes exchange information via shared memory, message passing, sockets, pipes, files, etc. ▪ Often spans multiple computers and networks Error detection and recovery ▪ Detect errors in CPU, memory, I/O devices, processes, ...
Overview of Operating Systems Security Features
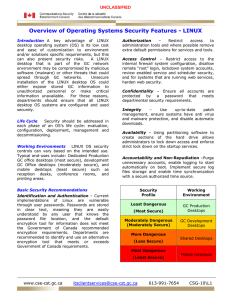
... Overview of Operating Systems Security Features - LINUX Introduction A key advantage of LINUX desktop operating system (OS) is its low cost and ease of customization to environment and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the G ...
... Overview of Operating Systems Security Features - LINUX Introduction A key advantage of LINUX desktop operating system (OS) is its low cost and ease of customization to environment and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the G ...
2.4 The service and functions provided by an operating system can
... has several advantages. The system is easier to debug and modify because changes affect only limited sections of the system rather than touching all sections of the operating system. Information is kept only where it is needed and is accessible only within a defined and restricted area, so any bugs ...
... has several advantages. The system is easier to debug and modify because changes affect only limited sections of the system rather than touching all sections of the operating system. Information is kept only where it is needed and is accessible only within a defined and restricted area, so any bugs ...
Firewall Configuration
... Configuring a firewall can be difficult to maintain. This is because if you want to filter each packet of ...
... Configuring a firewall can be difficult to maintain. This is because if you want to filter each packet of ...
History of Operating Systems
... Small, cheap PCs resulted in a move away from a centralized environment to a distributed environment. Shared peripherals, email and networks lead to new operating systems, ones that supported local computation and remote access (for users and resources) Network operating systems ...
... Small, cheap PCs resulted in a move away from a centralized environment to a distributed environment. Shared peripherals, email and networks lead to new operating systems, ones that supported local computation and remote access (for users and resources) Network operating systems ...
Basic System Administration
... Security Network Performance – CPU, memory, disk, network Application installation, configuration and maintenance System software installation, configuration and maintenance OS installation, configuration and maintenance Virtualization Storage/Backup/Restore Hardware selection and design Architectur ...
... Security Network Performance – CPU, memory, disk, network Application installation, configuration and maintenance System software installation, configuration and maintenance OS installation, configuration and maintenance Virtualization Storage/Backup/Restore Hardware selection and design Architectur ...
Computer Science 101
... – Hardware bereft of any helpful user-oriented features – Data as well as instructions must be represented in binary ...
... – Hardware bereft of any helpful user-oriented features – Data as well as instructions must be represented in binary ...
Chapter 1: Welcome to Linux - Business and Computer Science
... – Most mainframes had less computing power than a calculator on the shelf at Wal-Mart ...
... – Most mainframes had less computing power than a calculator on the shelf at Wal-Mart ...
CUSTOMER_CODE SMUDE DIVISION_CODE SMUDE
... There are two types of devices in UNIX- block-oriented devices which transfer data in blocks and character – oriented devices that transfer data on a byte-by – byte basis. ii.Links: A link is a pointer to another file. There are two types of links – ahard link to a file is indistinguishable from the ...
... There are two types of devices in UNIX- block-oriented devices which transfer data in blocks and character – oriented devices that transfer data on a byte-by – byte basis. ii.Links: A link is a pointer to another file. There are two types of links – ahard link to a file is indistinguishable from the ...
Slides. - Department of Computer Science and Information Systems
... 5. Input/output 6. File systems 7. Multimedia operating systems 8. Multiple processor systems 9. Security UNIX and Windows are to be used as running case studies. ...
... 5. Input/output 6. File systems 7. Multimedia operating systems 8. Multiple processor systems 9. Security UNIX and Windows are to be used as running case studies. ...
Controls
... Password management routines such as requiring periodic password changes, quality passwords, longer passwords, etc. ...
... Password management routines such as requiring periodic password changes, quality passwords, longer passwords, etc. ...