Operating Systems Should Provide Transactions
... of updates at commit. This atomic write could be implemented with journaling, copy-on-write semantics, or a transactional file system [11, 20]. Conflict detection and object versioning occur in common code shared by all file systems. Because the implementation of durability is the most thoroughly st ...
... of updates at commit. This atomic write could be implemented with journaling, copy-on-write semantics, or a transactional file system [11, 20]. Conflict detection and object versioning occur in common code shared by all file systems. Because the implementation of durability is the most thoroughly st ...
COS 318: Operating Systems OS Structures and System Calls Kai Li
... Privileged instructions Can be executed only When current privileged Level (CPR) is 0 ...
... Privileged instructions Can be executed only When current privileged Level (CPR) is 0 ...
Chapter 8 – Operating Systems
... Step 7: Operating system loads configuration information and displays desktop on screen Operating system executes programs in StartUp folder click Start to display list of ...
... Step 7: Operating system loads configuration information and displays desktop on screen Operating system executes programs in StartUp folder click Start to display list of ...
Proceedings of The National Conference
... As a starting point, an initial default installation of Red Hat Linux 7.3 served to reveal and even answer some of the problems associated with the project’s requirements and design. Red Hat 7.3 was readily available at the USMA Information and Technology Operations Center (ITOC) and seemed to be a ...
... As a starting point, an initial default installation of Red Hat Linux 7.3 served to reveal and even answer some of the problems associated with the project’s requirements and design. Red Hat 7.3 was readily available at the USMA Information and Technology Operations Center (ITOC) and seemed to be a ...
Operating Systems
... • e.g. linux is a “kernel”, but has kernel modules and certain servers. • e.g. Windows NT was originally microkernel (3.5), but now (4.0 onwards) pushed lots back into kernel for performance. • Still not clear what the best OS structure is, or how much it really matters. . . ...
... • e.g. linux is a “kernel”, but has kernel modules and certain servers. • e.g. Windows NT was originally microkernel (3.5), but now (4.0 onwards) pushed lots back into kernel for performance. • Still not clear what the best OS structure is, or how much it really matters. . . ...
15 - Web Services Overview
... to prevent CPU throughput from being limited by device speed (for slow devices) to prevent I/O throughput from being limited by speed (for fast devices) to achieve good utilization of CPU and I/O devices to meet the real-time requirements of devices ...
... to prevent CPU throughput from being limited by device speed (for slow devices) to prevent I/O throughput from being limited by speed (for fast devices) to achieve good utilization of CPU and I/O devices to meet the real-time requirements of devices ...
From Russia with Love: Behind the Trend Micro
... wanted the experiment to be performed on new gadgets with no security or software updates. The decision to not put basic precautions in place was made because we were supposed to be regular users in Russia for the Sochi Olympics and wanted to understand the threats attendees who do not take proper p ...
... wanted the experiment to be performed on new gadgets with no security or software updates. The decision to not put basic precautions in place was made because we were supposed to be regular users in Russia for the Sochi Olympics and wanted to understand the threats attendees who do not take proper p ...
OPERATING SYSTEMS:
... and others from malicious or ignorant users. The User/Supervisor Mode and privileged instructions. Concurrent threads might interfere with others. This leads to protection of resources by user/supervisor mode. These resources include: I/O Define I/O instructions as privileged; they can be executed o ...
... and others from malicious or ignorant users. The User/Supervisor Mode and privileged instructions. Concurrent threads might interfere with others. This leads to protection of resources by user/supervisor mode. These resources include: I/O Define I/O instructions as privileged; they can be executed o ...
CS502 Course Introduction (Spring 2006)
... Term Project (1- 3 person teams) – 25% Class participation – 5% ...
... Term Project (1- 3 person teams) – 25% Class participation – 5% ...
Unit C: Computer Software
... more computer programs to run simultaneously. Microsoft Windows is installed on over 80% of the world’s PCs. Mac OS The UNIX operating system was developed in 1969 at AT&T’s Bell Labs. It gained a good reputation for its dependability in multi-user environments. In 1991, Linus Torvalds developed the ...
... more computer programs to run simultaneously. Microsoft Windows is installed on over 80% of the world’s PCs. Mac OS The UNIX operating system was developed in 1969 at AT&T’s Bell Labs. It gained a good reputation for its dependability in multi-user environments. In 1991, Linus Torvalds developed the ...
Current Issues in Maintaining a Secure System
... • One analogy is that of a locked store front door with a mail slot. The mail slot is exposed and accessible to the public; its location (the street address) is in essence the public key. Anyone knowing the street address can go to the door and drop a written message through the slot. However, only ...
... • One analogy is that of a locked store front door with a mail slot. The mail slot is exposed and accessible to the public; its location (the street address) is in essence the public key. Anyone knowing the street address can go to the door and drop a written message through the slot. However, only ...
Firewalls: An Effective Solution for Internet Security
... which the connection has originated. By sending these packets to the destination host, the originating host's connection is dropped, and the attacker picks up the connection. Another Internet security threat is network snooping, in which attackers install programs that copy packets traversing networ ...
... which the connection has originated. By sending these packets to the destination host, the originating host's connection is dropped, and the attacker picks up the connection. Another Internet security threat is network snooping, in which attackers install programs that copy packets traversing networ ...
University of Arizona
... to extensive press coverage. • What is a virus? – Computer programs that are written by devious programmers and are designed to replicate themselves and infect computers when triggered by a specific event. • Example - Macro viruses attach themselves to files that contain macro instructions (routines ...
... to extensive press coverage. • What is a virus? – Computer programs that are written by devious programmers and are designed to replicate themselves and infect computers when triggered by a specific event. • Example - Macro viruses attach themselves to files that contain macro instructions (routines ...
Computer Network and Infrastructure
... performs but how a class of processes associated with one user application performs. User’s application runs as a collection of processes (threads) User is concerned about the performance of the application Need to make scheduling decisions based on process sets Eg. If a larger number of emplo ...
... performs but how a class of processes associated with one user application performs. User’s application runs as a collection of processes (threads) User is concerned about the performance of the application Need to make scheduling decisions based on process sets Eg. If a larger number of emplo ...
6 - Department of Accounting and Information Systems ACIS | Pamplin
... Circuit gateway firewall operates at transport layer Prevent direct connections between one network and another ...
... Circuit gateway firewall operates at transport layer Prevent direct connections between one network and another ...
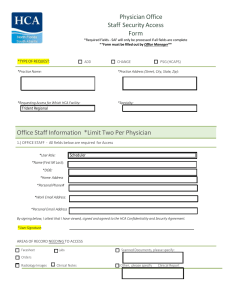
Physician Office Staff Security Access Form Office Staff Information
... b. Allow another individual to use my digital identity (e.g., 3-4 User ID) to access, modify, or delete data and/or use a computer system. c. Use tools or techniques to break/exploit security measures. d. Connect unauthorized systems or devices to the Company network. 22. I will practice good workst ...
... b. Allow another individual to use my digital identity (e.g., 3-4 User ID) to access, modify, or delete data and/or use a computer system. c. Use tools or techniques to break/exploit security measures. d. Connect unauthorized systems or devices to the Company network. 22. I will practice good workst ...
Intrusion Prevention System (IPS)
... If ETS or JDL alerts a TLC to a security problem, please address the issue promptly. Notify ETS when complete. ...
... If ETS or JDL alerts a TLC to a security problem, please address the issue promptly. Notify ETS when complete. ...
Forcepoint™ Stonesoft Next Generation Firewall
... supports transparent failover for multiple software and hardware versions within the same cluster. Forcepoint Multi-Link: Extends high availability coverage to network and IPsec VPN connections. Provides the confidence of non-stop security along with high performance for every deployment. ...
... supports transparent failover for multiple software and hardware versions within the same cluster. Forcepoint Multi-Link: Extends high availability coverage to network and IPsec VPN connections. Provides the confidence of non-stop security along with high performance for every deployment. ...
SANDS CORP CYBER JOB
... works closely with the other members of the cyber security team in support of a comprehensive cyber security program. This role is an entry level analyst that is responsible for monitoring various cyber security appliances to identify events that require escalated analysis. The SOC cyber security an ...
... works closely with the other members of the cyber security team in support of a comprehensive cyber security program. This role is an entry level analyst that is responsible for monitoring various cyber security appliances to identify events that require escalated analysis. The SOC cyber security an ...
CS350-01-intro - dforeman.cs.bingh
... get more work done in a fixed time allow multiple users on 1 computer allow programs to interact with each other maximize memory and CPU utilization reduce the need for device handling allow programs' parts to be shared make the system more usable (friendlier?) make system faster ...
... get more work done in a fixed time allow multiple users on 1 computer allow programs to interact with each other maximize memory and CPU utilization reduce the need for device handling allow programs' parts to be shared make the system more usable (friendlier?) make system faster ...
linux: a product of the internet
... inexpensive memory; and lower-priced hard-disk storage have allowed manufacturers to install multi-user operating systems on microcomputers. Second, with the cost of hardware continually dropping, hardware manufactures can no longer afford to develop and support proprietary operating systems. A prop ...
... inexpensive memory; and lower-priced hard-disk storage have allowed manufacturers to install multi-user operating systems on microcomputers. Second, with the cost of hardware continually dropping, hardware manufactures can no longer afford to develop and support proprietary operating systems. A prop ...
File System Management
... The file system is used not only to store users’ programs and data, but also to support and represent significant portions of the operating system itself. Stallings introduces the traditional file system concepts of: fields represent the smallest logical item of data “understood” by a file-system: e ...
... The file system is used not only to store users’ programs and data, but also to support and represent significant portions of the operating system itself. Stallings introduces the traditional file system concepts of: fields represent the smallest logical item of data “understood” by a file-system: e ...
NP11_IM_Chapter04
... dramatic aid to help students visualize the structure of files on a disk. Use the cardboard box analogy: Each directory is a box. Each box has a name. Boxes can contain papers (files) or folders (subdirectories). Once students understand the idea of directories, explain that files are not physic ...
... dramatic aid to help students visualize the structure of files on a disk. Use the cardboard box analogy: Each directory is a box. Each box has a name. Boxes can contain papers (files) or folders (subdirectories). Once students understand the idea of directories, explain that files are not physic ...