Document
... provides supports for other programs. For example, it is responsible for loading other programs into memory for execution. However, the operating system itself is a program that needs to be loaded into the memory and be run. How is this dilemma solved? The solution is a two-stage process. A very sma ...
... provides supports for other programs. For example, it is responsible for loading other programs into memory for execution. However, the operating system itself is a program that needs to be loaded into the memory and be run. How is this dilemma solved? The solution is a two-stage process. A very sma ...
Computer & Network Technology Advisory Committee Meeting 3/24/2015 Minutes
... i. Discuss revision of Information Systems It was noted by a parent in the group, that the selection of courses in the high school is very broad. Some of the concepts we are looking at in the revised information systems course may be an overlap/rehash of material that they have already had in other ...
... i. Discuss revision of Information Systems It was noted by a parent in the group, that the selection of courses in the high school is very broad. Some of the concepts we are looking at in the revised information systems course may be an overlap/rehash of material that they have already had in other ...
Operating System
... Multitasking refers to term where multiple jobs are executed by the CPU simultaneously by switching between them.Switches occur so frequently that the users may interact with each program while it is running. Operating system does the following activities related to multitasking. ...
... Multitasking refers to term where multiple jobs are executed by the CPU simultaneously by switching between them.Switches occur so frequently that the users may interact with each program while it is running. Operating system does the following activities related to multitasking. ...
MBG404_LS_02
... Search for runClass (name of the file without .class) The part ‘mbg404/’ in front of the first ‘runClass’ entry, you find, is the package (folder/directory) it must be in so you are able to run the class • Create a folder mbg404 ...
... Search for runClass (name of the file without .class) The part ‘mbg404/’ in front of the first ‘runClass’ entry, you find, is the package (folder/directory) it must be in so you are able to run the class • Create a folder mbg404 ...
Chapter 9 Linux Installation Procedures
... • RPM is the most popular type of package. • It provides the necessary tools such as package databases that are needed to install and remove programs, however, not all applications or programs use RPM. • The difference between Debian and RPM packages is that they are not interchangeable. • Debian co ...
... • RPM is the most popular type of package. • It provides the necessary tools such as package databases that are needed to install and remove programs, however, not all applications or programs use RPM. • The difference between Debian and RPM packages is that they are not interchangeable. • Debian co ...
operating system
... system’s command line interface Look at how MS Windows has developed from MS-DOS ...
... system’s command line interface Look at how MS Windows has developed from MS-DOS ...
Operating Systems Principles Lecture 1: Introduction
... User Space (compilers, programs, data, etc.) ...
... User Space (compilers, programs, data, etc.) ...
Operating Systems
... For each user, the computer or network administrator establishes a user account, which enables a user to access, or log on to, a computer or a network. Each user account typically consists of a user name and password A user name, or user ID, is a unique combination of characters, such as letters ...
... For each user, the computer or network administrator establishes a user account, which enables a user to access, or log on to, a computer or a network. Each user account typically consists of a user name and password A user name, or user ID, is a unique combination of characters, such as letters ...
Operating Systems
... For each user, the computer or network administrator establishes a user account, which enables a user to access, or log on to, a computer or a network. Each user account typically consists of a user name and password A user name, or user ID, is a unique combination of characters, such as letters ...
... For each user, the computer or network administrator establishes a user account, which enables a user to access, or log on to, a computer or a network. Each user account typically consists of a user name and password A user name, or user ID, is a unique combination of characters, such as letters ...
Memory Protection
... • For each file/directory – Can specify RWX permissions for one owner, one group, and one other ...
... • For each file/directory – Can specify RWX permissions for one owner, one group, and one other ...
Program
... • [File Name].[Extension] – the extension, (usually 3 letters long), describes the type of program used for that file » doc(Word), xls(Excel), ppt(PowerPoint) ...
... • [File Name].[Extension] – the extension, (usually 3 letters long), describes the type of program used for that file » doc(Word), xls(Excel), ppt(PowerPoint) ...
Document
... computers and IBM developed the MVS, VM and other operating systems for their mainframe series of computers. Comp 1001: IT & Architecture - Joe Carthy ...
... computers and IBM developed the MVS, VM and other operating systems for their mainframe series of computers. Comp 1001: IT & Architecture - Joe Carthy ...
Introduction
... • [File Name].[Extension] – the extension, (usually 3 letters long), describes the type of program used for that file » doc(Word), xls(Excel), ppt(PowerPoint) ...
... • [File Name].[Extension] – the extension, (usually 3 letters long), describes the type of program used for that file » doc(Word), xls(Excel), ppt(PowerPoint) ...
PPT - CS
... The hard disk can write and read information to and from the main memory. The access speed of main memory is much faster than a hard disk. • Programs are stored on the disk until they are loaded into memory, and then use the disk as both the source and destination of the information for their proces ...
... The hard disk can write and read information to and from the main memory. The access speed of main memory is much faster than a hard disk. • Programs are stored on the disk until they are loaded into memory, and then use the disk as both the source and destination of the information for their proces ...
Operating system
... switches jobs so frequently that users can interact with each job while it is running, creating interactive computing – Response time should be < 1 second – Each user has at least one program executing in memory process – If several jobs ready to run at the same time CPU scheduling – If processes ...
... switches jobs so frequently that users can interact with each job while it is running, creating interactive computing – Response time should be < 1 second – Each user has at least one program executing in memory process – If several jobs ready to run at the same time CPU scheduling – If processes ...
Microkernels
... Constructing Address Spaces grant: remove page from your address space and give to another consenting process. map: share page with another process. demap: remove page from all other processes that received it directly or indirectly from demapper. ...
... Constructing Address Spaces grant: remove page from your address space and give to another consenting process. map: share page with another process. demap: remove page from all other processes that received it directly or indirectly from demapper. ...
Module Operating Systems (Server)
... 1. Understand and explain the concurrency and deadlock issues, which arise in modern multi-programmed operating systems on uni-processor and multi-processor/multicore systems. 2. Explain different types of operating systems structures 3. Compare and contrast single-threaded and multi-threaded proces ...
... 1. Understand and explain the concurrency and deadlock issues, which arise in modern multi-programmed operating systems on uni-processor and multi-processor/multicore systems. 2. Explain different types of operating systems structures 3. Compare and contrast single-threaded and multi-threaded proces ...
Test1: Spring 2017 (Hint)
... Or, Q3B. A DMA scheme provides one approach to do I/O by device controllers. What is DMA? How is it distinguished from the other possible ways of doing I/O? Ans. A DMA is used when a device controller directly dumps input from an external source into a specific location in RAM, or directly output fr ...
... Or, Q3B. A DMA scheme provides one approach to do I/O by device controllers. What is DMA? How is it distinguished from the other possible ways of doing I/O? Ans. A DMA is used when a device controller directly dumps input from an external source into a specific location in RAM, or directly output fr ...
CSS430: Introduction - UW Faculty Web Server
... Memory Protection: A region from the base to the limit register allowed to use CPU Protection: CPU allowed to use until the timer gets 0. CSS430 Introduction ...
... Memory Protection: A region from the base to the limit register allowed to use CPU Protection: CPU allowed to use until the timer gets 0. CSS430 Introduction ...
Chapter 8 Operating Systems and Utility Programs
... Foreground contains application you are using ...
... Foreground contains application you are using ...
Chapter 2.pdf
... • Interface between OS and user programs (to perform privileged operations) • Programming interface to the services provided by the OS – i.e. interface provided to applications • Are called by a running program to get services • Typically written in a high-level language (C or C++) • Machine depende ...
... • Interface between OS and user programs (to perform privileged operations) • Programming interface to the services provided by the OS – i.e. interface provided to applications • Are called by a running program to get services • Typically written in a high-level language (C or C++) • Machine depende ...
OPERATING SYSTEM
... Both of these machines are very huge and people need small machines. IBM produced the System/360 to solve these problems. All the machines had the same architecture and instruction set, programs written for one machine could run on all the others. Furthermore, the 360 was designed to handle both sci ...
... Both of these machines are very huge and people need small machines. IBM produced the System/360 to solve these problems. All the machines had the same architecture and instruction set, programs written for one machine could run on all the others. Furthermore, the 360 was designed to handle both sci ...
Operating Systems Principles Lecture 1: Introduction
... User Space (compilers, programs, data, etc.) ...
... User Space (compilers, programs, data, etc.) ...
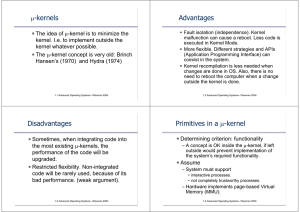
μ-kernels Advantages Disadvantages Primitives in a μ
... The µ-kernel design is extensively depending on the CPU structure. The only µ-kernel feature that can be portable is the scheduler. Large monolithic kernel can have many more portable features. In the early 70's, large portions of the kernel have been started to be written in C, so they could be por ...
... The µ-kernel design is extensively depending on the CPU structure. The only µ-kernel feature that can be portable is the scheduler. Large monolithic kernel can have many more portable features. In the early 70's, large portions of the kernel have been started to be written in C, so they could be por ...