Spring 2005 - Computer Science
... sources, those who copy source code from other students, and those students who knowingly or unknowingly allow other students to copy from them will be penalized with a zero on any homework assignments in which this occurs. Due dates for assignments will be enforced. Late assignments will be penaliz ...
... sources, those who copy source code from other students, and those students who knowingly or unknowingly allow other students to copy from them will be penalized with a zero on any homework assignments in which this occurs. Due dates for assignments will be enforced. Late assignments will be penaliz ...
CS311 - NUS School of Computing
... The first machines with real programs were developed in the 1940’s. In those days, the programmer would put his or her name down on a computer time chart (say for an hour), and then would have total control of the machine for that time. The programmer operated the computer, put in a program, debugge ...
... The first machines with real programs were developed in the 1940’s. In those days, the programmer would put his or her name down on a computer time chart (say for an hour), and then would have total control of the machine for that time. The programmer operated the computer, put in a program, debugge ...
Notes for Lecture 12
... All rights reserved. Reproduction or translation of this work beyond that permitted in section 117 of the 1976 United States Copyright Act without express permission of the copyright owner is unlawful. Request for further information should be addressed to the Permissions Department, John Wiley & So ...
... All rights reserved. Reproduction or translation of this work beyond that permitted in section 117 of the 1976 United States Copyright Act without express permission of the copyright owner is unlawful. Request for further information should be addressed to the Permissions Department, John Wiley & So ...
A Deduplication File System & Course Review Kai Li
... Bottleneck in the Data Domain Deduplication File System. In Proceedings of The 6th USENIX Conference on File and Storage ...
... Bottleneck in the Data Domain Deduplication File System. In Proceedings of The 6th USENIX Conference on File and Storage ...
CS-502, Distributed and Multiprocessor Systems
... • Make each frame read-only • On write tell other processors to invalidate page to be written • Write through CS502 Spring 2006 ...
... • Make each frame read-only • On write tell other processors to invalidate page to be written • Write through CS502 Spring 2006 ...
CIS162AB
... data and check the results. If it was incorrect, we would change the program, run it again, and reenter the data. Depending on the application, it may be more efficient to capture the raw data the first time it is entered and store in a file. A program or many different programs can then read ...
... data and check the results. If it was incorrect, we would change the program, run it again, and reenter the data. Depending on the application, it may be more efficient to capture the raw data the first time it is entered and store in a file. A program or many different programs can then read ...
PPT Chapter 02
... • An event is a situation that requires OS’s attention – Designer associates an interrupt with each event • Purpose is to report occurrence of the event to OS and enable it to perform event handling actions ...
... • An event is a situation that requires OS’s attention – Designer associates an interrupt with each event • Purpose is to report occurrence of the event to OS and enable it to perform event handling actions ...
CS-3013 Week 0:- Introduction
... security: how is the integrity of the OS and its resources ensured? protection: how is one user/program protected from another? performance: how do we make it all go fast? reliability: what happens if something goes wrong – hardware or software extensibility: can we add new features? communication: ...
... security: how is the integrity of the OS and its resources ensured? protection: how is one user/program protected from another? performance: how do we make it all go fast? reliability: what happens if something goes wrong – hardware or software extensibility: can we add new features? communication: ...
Virtual Machine Monitors
... Virtualizing the User/Kernel Boundary Both the guest OS and applications run in (physical) user-mode This is necessary so that privileged instructions trap into the VMM ...
... Virtualizing the User/Kernel Boundary Both the guest OS and applications run in (physical) user-mode This is necessary so that privileged instructions trap into the VMM ...
Windows Server 2008
... (HFS+) includes new features: – A case-sensitive format to make the file system more compatible with other UNIX/Linux systems – Journaling – Ability to store up to 16 TB of data ...
... (HFS+) includes new features: – A case-sensitive format to make the file system more compatible with other UNIX/Linux systems – Journaling – Ability to store up to 16 TB of data ...
dsk-07-io
... incoming data two buffers are used (double buffer). – By the time the modem has filled the 2nd buffer, the disk write from the 1st buffer should have completed (emptied), so the modem can switched back to it while the disk writes the 2nd one. ...
... incoming data two buffers are used (double buffer). – By the time the modem has filled the 2nd buffer, the disk write from the 1st buffer should have completed (emptied), so the modem can switched back to it while the disk writes the 2nd one. ...
OPERATING SYSTEMS QUESTIONS
... The system can detect thrashing by evaluating the level of CPU utilization as compared to the level of multiprogramming. It can be eliminated by reducing the level of multiprogramming. 11. What is multi tasking, multi programming, multi threading? - Multi programming: Multiprogramming is the techniq ...
... The system can detect thrashing by evaluating the level of CPU utilization as compared to the level of multiprogramming. It can be eliminated by reducing the level of multiprogramming. 11. What is multi tasking, multi programming, multi threading? - Multi programming: Multiprogramming is the techniq ...
pdf
... • Synchronous I/O: After I/O starts, control returns to user program only upon I/O completion. – wait instruction idles the CPU until the next interrupt – wait loop (contention for memory access). – At most one I/O request is outstanding at a time, no simultaneous I/O processing. ...
... • Synchronous I/O: After I/O starts, control returns to user program only upon I/O completion. – wait instruction idles the CPU until the next interrupt – wait loop (contention for memory access). – At most one I/O request is outstanding at a time, no simultaneous I/O processing. ...
8pp - inst.eecs.berkeley.edu
... values associated with that key • All key-value pairs with the same key are processed together • The reducer yields zero or more values, each associated with that intermediate key a: 4 a: 1 a: 1 ...
... values associated with that key • All key-value pairs with the same key are processed together • The reducer yields zero or more values, each associated with that intermediate key a: 4 a: 1 a: 1 ...
Introduction to Operating Systems
... Write your name/email on the sheet currently going through the room. This way you will receive updates on the lecture ...
... Write your name/email on the sheet currently going through the room. This way you will receive updates on the lecture ...
slides
... directly to the system and the other to another device, or the two ports connect to other devices. The chain usually operates as a bus. ...
... directly to the system and the other to another device, or the two ports connect to other devices. The chain usually operates as a bus. ...
Operating Systems
... —Memory split into two —One for Operating System (monitor) —One for currently executing program ...
... —Memory split into two —One for Operating System (monitor) —One for currently executing program ...
Processes
... program, an operating system creates a number of virtual processors, each one for running a different program. To keep track of these virtual processors, the operating system has a process table, containing entries to store CPU register values, memory maps, open files, accounting information, privil ...
... program, an operating system creates a number of virtual processors, each one for running a different program. To keep track of these virtual processors, the operating system has a process table, containing entries to store CPU register values, memory maps, open files, accounting information, privil ...
1: Welcome and Overview COM S 414
... functional units to carry out tasks • PC = program counter contains memory address of instruction being processed • IR – instruction register – copy of the current instruction ...
... functional units to carry out tasks • PC = program counter contains memory address of instruction being processed • IR – instruction register – copy of the current instruction ...
Linux - Spider
... By 1993 there were 12000 Linux users Today Linux rivals UNIX in stability and ...
... By 1993 there were 12000 Linux users Today Linux rivals UNIX in stability and ...
Lecture 1 - inst.eecs.berkeley.edu
... – Provide illusion of dedicated machine with infinite memory and infinite processors ...
... – Provide illusion of dedicated machine with infinite memory and infinite processors ...
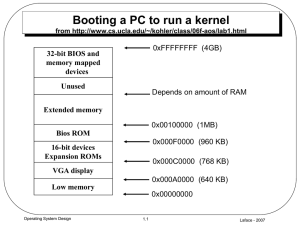
Booting a PC
... Operating system kernels often like to be linked and run at very high virtual address, such as 0xf0100000, in order to leave the lower part of the processor's virtual address space for user programs to use. ...
... Operating system kernels often like to be linked and run at very high virtual address, such as 0xf0100000, in order to leave the lower part of the processor's virtual address space for user programs to use. ...
Best algorithms + best computers = powerful match
... to offer applications a logically shared file system accessed via the Unix file API, and adapts distributed shared memory techniques1 to emulate shared memory for multithreaded applications. Since this emulation is implemented in user space, applications can freely customize it, and runtime bugs can ...
... to offer applications a logically shared file system accessed via the Unix file API, and adapts distributed shared memory techniques1 to emulate shared memory for multithreaded applications. Since this emulation is implemented in user space, applications can freely customize it, and runtime bugs can ...
Os 2marks - Erode Sengunthar Engineering College
... If a process does not have enough memory for its working set, it will thrash. Providing enough frames to each process to avoid thrashing may require process swapping and scheduling 6. What Are The File Attributes? Name, type, location, size, protection, time, date and user identification these are t ...
... If a process does not have enough memory for its working set, it will thrash. Providing enough frames to each process to avoid thrashing may require process swapping and scheduling 6. What Are The File Attributes? Name, type, location, size, protection, time, date and user identification these are t ...