AIX is building momentum as the leading, UNIX operating system for
... A file system is a hierarchical structure (file tree) of files and directories. This type of structure resembles an inverted tree with the roots at the top and branches at the bottom. This file tree uses directories to organize data and programs into groups, allowing the management of several direct ...
... A file system is a hierarchical structure (file tree) of files and directories. This type of structure resembles an inverted tree with the roots at the top and branches at the bottom. This file tree uses directories to organize data and programs into groups, allowing the management of several direct ...
SCADA Systems
... In the case of external interrupts, for example, message came from the network, handler must understand to what thread it is addressed, and deliver it to the address space of the respective thread, perform handshakes protocol with sender, and so on. Such actions may require up to tens of millisecond ...
... In the case of external interrupts, for example, message came from the network, handler must understand to what thread it is addressed, and deliver it to the address space of the respective thread, perform handshakes protocol with sender, and so on. Such actions may require up to tens of millisecond ...
Formatting and Partitioning Hard Drives, and DOS
... Microsoft developed (DOS), in 1981. DOS was designed for the IBM Personal Computer DOS is a collection of programs and commands used to control the overall computer operation in a disk-based system Three sections make up DOS: Boot files File management files Utility files A simple operating sy ...
... Microsoft developed (DOS), in 1981. DOS was designed for the IBM Personal Computer DOS is a collection of programs and commands used to control the overall computer operation in a disk-based system Three sections make up DOS: Boot files File management files Utility files A simple operating sy ...
Chapter 2 Operating Systems Concepts
... Layered OS Architecture • Operating system is composed of several layers starting at the hardware and ending at the user interface • Each layer is a module: – Interface is available to higher-layer implementations – Implementation is defined using lower-layer interfaces • Advantages: – Modularity: l ...
... Layered OS Architecture • Operating system is composed of several layers starting at the hardware and ending at the user interface • Each layer is a module: – Interface is available to higher-layer implementations – Implementation is defined using lower-layer interfaces • Advantages: – Modularity: l ...
What is an Operating System?
... • “Everything a vendor ships when you order an operating system” is a good approximation • but varies wildly • Another definition: The OS is “the one program running at all times on the computer” (the kernel) • everything else is either a system program (ships with the operating system) or an applic ...
... • “Everything a vendor ships when you order an operating system” is a good approximation • but varies wildly • Another definition: The OS is “the one program running at all times on the computer” (the kernel) • everything else is either a system program (ships with the operating system) or an applic ...
Chapter 13 PPT Silberschatz slides (Our Text Book) on I/O systems
... writers (roll your own). Can implement “secret” calls which may not be documented in a users or programming manual ...
... writers (roll your own). Can implement “secret” calls which may not be documented in a users or programming manual ...
Linux Booting Procedure
... intended for normal users. Commands run by LINUX. proc - This filesystem is not on a disk. It is a virtual filesystem that exists in the kernels imagination which is memory ...
... intended for normal users. Commands run by LINUX. proc - This filesystem is not on a disk. It is a virtual filesystem that exists in the kernels imagination which is memory ...
Terminal Control - Utah Valley University
... Moreover, when the program outputs a New Line character, it outputs as a Carriage Return. New Line only move the cursor down one line, it does not move the cursor to the left margin! ...
... Moreover, when the program outputs a New Line character, it outputs as a Carriage Return. New Line only move the cursor down one line, it does not move the cursor to the left margin! ...
CENG334 Introduction to Operating Systems
... From the user point of view, file is the only unit through which data can be written onto storage devices. The information in a file as well as the attributes of the file is determined by its creator. ...
... From the user point of view, file is the only unit through which data can be written onto storage devices. The information in a file as well as the attributes of the file is determined by its creator. ...
theGuard! ApplicationManager System Windows Data
... increase the performance and stability of business-critical applications without having to invest in additional hardware (processors, RAM, disk space). A number of data collectors have been developed for theGuard! ApplicationManager that provide comprehensive monitoring and generate detailed data an ...
... increase the performance and stability of business-critical applications without having to invest in additional hardware (processors, RAM, disk space). A number of data collectors have been developed for theGuard! ApplicationManager that provide comprehensive monitoring and generate detailed data an ...
Discovering Computers Fundamentals 3rd Edition
... What are other program management features of operating systems? multiprocessing Can support two or more processors running programs at same time ...
... What are other program management features of operating systems? multiprocessing Can support two or more processors running programs at same time ...
Operating Systems and File Management
... Boot and Recovery Disks • You can create a custom recovery CD that contains your computer’s current settings and device drivers • Norton Ghost is a product of Symantec, which also provides a more specialized recovery disk called the Symantec Recovery Disk • Certain PC manufacturers have pre-install ...
... Boot and Recovery Disks • You can create a custom recovery CD that contains your computer’s current settings and device drivers • Norton Ghost is a product of Symantec, which also provides a more specialized recovery disk called the Symantec Recovery Disk • Certain PC manufacturers have pre-install ...
Operating Systems
... o virtual address (Pentium logical address) segment reference 2-bit protection mechanism 14-bit segment specification offset 32-bit o unsegmented memory virtual memory = 232 bytes, i.e., 4 GBytes o segmented memory virtual memory = 246 bytes, i.e., 64 TBytes ½ virtual address space == ...
... o virtual address (Pentium logical address) segment reference 2-bit protection mechanism 14-bit segment specification offset 32-bit o unsegmented memory virtual memory = 232 bytes, i.e., 4 GBytes o segmented memory virtual memory = 246 bytes, i.e., 64 TBytes ½ virtual address space == ...
Module 3: Operating
... • Resource allocation – allocating resources to multiple users or multiple jobs running at the same time. • Accounting – keep track of and record which users use how much and what kinds of computer resources for account billing or for accumulating usage statistics. • Protection – ensuring that all a ...
... • Resource allocation – allocating resources to multiple users or multiple jobs running at the same time. • Accounting – keep track of and record which users use how much and what kinds of computer resources for account billing or for accumulating usage statistics. • Protection – ensuring that all a ...
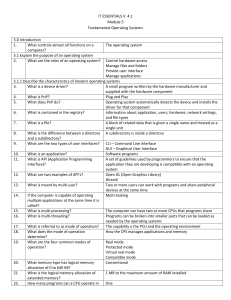
IT ESSENTIALS V. 4.1 Module 5 Fundamental Operating Systems
... Operating system setup CDs and DVDs It is logically divided into one or more areas The first partition Up to 4 The partition used by the operating system to boot the computer ...
... Operating system setup CDs and DVDs It is logically divided into one or more areas The first partition Up to 4 The partition used by the operating system to boot the computer ...
Module 3: Operating
... • Resource allocation – allocating resources to multiple users or multiple jobs running at the same time. • Accounting – keep track of and record which users use how much and what kinds of computer resources for account billing or for accumulating usage statistics. • Protection – ensuring that all a ...
... • Resource allocation – allocating resources to multiple users or multiple jobs running at the same time. • Accounting – keep track of and record which users use how much and what kinds of computer resources for account billing or for accumulating usage statistics. • Protection – ensuring that all a ...
ppt - Courses
... • Allows a process to run even if the full amount of needed memory is not currently available. – Swapping • Moving a page from memory to disk, and vice versa • Can also refer to moving an entire process into or out of RAM memory • A page fault has to be handled by the Scheduler – so slow (accessing ...
... • Allows a process to run even if the full amount of needed memory is not currently available. – Swapping • Moving a page from memory to disk, and vice versa • Can also refer to moving an entire process into or out of RAM memory • A page fault has to be handled by the Scheduler – so slow (accessing ...
IT ESSENTIALS V. 4.1 Module 5 Fundamental Operating Systems 5
... Operating system setup CDs and DVDs It is logically divided into one or more areas The first partition Up to 4 The partition used by the operating system to boot the computer ...
... Operating system setup CDs and DVDs It is logically divided into one or more areas The first partition Up to 4 The partition used by the operating system to boot the computer ...
Chapter 2: Operating-System Structures Silberschatz, Galvin and Gagne ©2013 – 9
... Operating System Concepts – 9th Edition ...
... Operating System Concepts – 9th Edition ...
Operating Systems (Linux), 27/10/08
... Architecture (arch) – a family of microprocessors that can be used to build complete and compatible(!) computer systems. ...
... Architecture (arch) – a family of microprocessors that can be used to build complete and compatible(!) computer systems. ...
Unit 10 Final Project Kaplan University Unit 10 Project Julee
... devices, and files, and in that same remembrance threads claim scheduling/execution. It is the responsibility of the operating system to make sure that there is a balance between the ownership/process and scheduling/execution/threads, so that the process and thread interaction is managed for the gre ...
... devices, and files, and in that same remembrance threads claim scheduling/execution. It is the responsibility of the operating system to make sure that there is a balance between the ownership/process and scheduling/execution/threads, so that the process and thread interaction is managed for the gre ...
Lecture 6: Kernel Structures and Threading
... Portable, threading library provides as utilities. Blocking call in a thread can block all threads in the same processes. Multithreaded application cannot take advantage of multiprocessing. ...
... Portable, threading library provides as utilities. Blocking call in a thread can block all threads in the same processes. Multithreaded application cannot take advantage of multiprocessing. ...