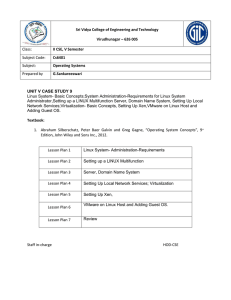
PowerPoint
... z Some synchronization methods are needed for threads accessing shared data, because if a thread modifies a global variable in a process, the changes are visible to other threads in the same process. ...
... z Some synchronization methods are needed for threads accessing shared data, because if a thread modifies a global variable in a process, the changes are visible to other threads in the same process. ...
Department of Computer Science and Engineering
... monolithic kernel, the Linux kernel, which handles process control, networking, and peripheral and file system access. Device drivers are either integrated directly with the kernel or added as modules loaded while the system is running.[45] ...
... monolithic kernel, the Linux kernel, which handles process control, networking, and peripheral and file system access. Device drivers are either integrated directly with the kernel or added as modules loaded while the system is running.[45] ...
A Taxonomy of Computer Program Security Flaws, with Examples
... This experience led researchers to seek better ways of building systems to meet security requirements in the first place instead of attempting to mend the flawed systems already installed. Although some success has been attained in identifying better strategies for building systems [12,13], these te ...
... This experience led researchers to seek better ways of building systems to meet security requirements in the first place instead of attempting to mend the flawed systems already installed. Although some success has been attained in identifying better strategies for building systems [12,13], these te ...
VirtualMachines
... – Each guest OS maintains own set of page tables. – Guest OS translates virtual memory locations to real memory locations (“physical memory” of VM.) – Guest OS has swap space on virtual disk. ...
... – Each guest OS maintains own set of page tables. – Guest OS translates virtual memory locations to real memory locations (“physical memory” of VM.) – Guest OS has swap space on virtual disk. ...
Chapter 4 - Angelfire
... multiple threads of execution within a single process Single threading: when the OS does not recognize the concept of thread MS-DOS support a single user process and a single thread UNIX supports multiple user processes but only supports one thread per process Solaris, Linux, Windows NT and 2000, ...
... multiple threads of execution within a single process Single threading: when the OS does not recognize the concept of thread MS-DOS support a single user process and a single thread UNIX supports multiple user processes but only supports one thread per process Solaris, Linux, Windows NT and 2000, ...
z/VM Conversational Monitor System (CMS)
... Files are stored in file pools A user can be given an amount of file space in a pool The files in a file space are organized in directories A file can be placed in more than one directory ...
... Files are stored in file pools A user can be given an amount of file space in a pool The files in a file space are organized in directories A file can be placed in more than one directory ...
A. Windows Networking – (Supplementary/Advanced)
... Using the Windows memory management APIs, multiple processes can share memory by mapping their virtual address spaces to the same file. This works nicely for processes running on the same machine. However, the Windows API provides additional constructs for interprocess communication (IPC) between pr ...
... Using the Windows memory management APIs, multiple processes can share memory by mapping their virtual address spaces to the same file. This works nicely for processes running on the same machine. However, the Windows API provides additional constructs for interprocess communication (IPC) between pr ...
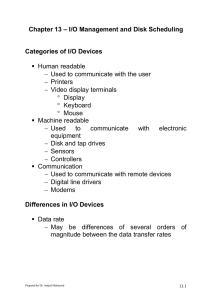
Chapter 13
... Arm only goes as far as the last request in each direction, then reverses direction immediately, without first going all the way to the end of the disk. ...
... Arm only goes as far as the last request in each direction, then reverses direction immediately, without first going all the way to the end of the disk. ...
Configuring Input and Output Devices_PPT_ch06
... – Ensure that the upgrade did not change any settings or move/remove files or programs – You may need a week or longer to get through tests – It is better to find out during a test that an OS upgrade/migration will not work for you – Test results may also be used to explain to management why an upgr ...
... – Ensure that the upgrade did not change any settings or move/remove files or programs – You may need a week or longer to get through tests – It is better to find out during a test that an OS upgrade/migration will not work for you – Test results may also be used to explain to management why an upgr ...
Chapter 4: Threads
... The image cannot be displayed. Your computer may not have enough memory to open the image, or the image may have been corrupted. Restart your computer, and then open the file again. If the red x still appears, you may have to delete the image and then ...
... The image cannot be displayed. Your computer may not have enough memory to open the image, or the image may have been corrupted. Restart your computer, and then open the file again. If the red x still appears, you may have to delete the image and then ...
Scheduling
... Each process equal CPU time. Interrupt every 10 msec and select another in a round-robin fashion. Works if processes are compute-bound. What if a process waits for I/O? How long quantum? is 10 msec the right answer? Shorter quantum => better interactive , but lower throughput. What if the environmen ...
... Each process equal CPU time. Interrupt every 10 msec and select another in a round-robin fashion. Works if processes are compute-bound. What if a process waits for I/O? How long quantum? is 10 msec the right answer? Shorter quantum => better interactive , but lower throughput. What if the environmen ...
Sistemas Operativos
... – Single user cannot keep CPU and I/O devices busy at all times – Multiprogramming organizes jobs (code and data) so CPU always has one to execute – A subset of total jobs in system is kept in memory – One job selected and run via job scheduling – When it has to wait (for I/O for example), OS switch ...
... – Single user cannot keep CPU and I/O devices busy at all times – Multiprogramming organizes jobs (code and data) so CPU always has one to execute – A subset of total jobs in system is kept in memory – One job selected and run via job scheduling – When it has to wait (for I/O for example), OS switch ...
Module 4: Processes
... Job queue – set of all processes in the system. Ready queue – set of all processes residing in main memory, ready and waiting to execute. –Linked List Device queues – set of processes waiting for an I/O device.—A device queue for each device Monitor, HDD, Floppy and other I/O devices have separa ...
... Job queue – set of all processes in the system. Ready queue – set of all processes residing in main memory, ready and waiting to execute. –Linked List Device queues – set of processes waiting for an I/O device.—A device queue for each device Monitor, HDD, Floppy and other I/O devices have separa ...
Week_3 Operating system File
... A thread is a basic unit of CPU utilization; it comprises a thread ID, a program counter, a register set, and a stack. If a process has multiple threads of control, it can perform more than one task at a time. In certain situations, a single application may be required to perform several simil ...
... A thread is a basic unit of CPU utilization; it comprises a thread ID, a program counter, a register set, and a stack. If a process has multiple threads of control, it can perform more than one task at a time. In certain situations, a single application may be required to perform several simil ...
The Case for VOS: The Vector Operating System Abstract Carnegie Mellon University,
... 1. Application-agnostic changes: One way to provide opportunities for making vector calls without application support is to introduce system call queues to coalesce similar requests. An application issues a system call through libc, which inserts the call into a syscall queue while the application w ...
... 1. Application-agnostic changes: One way to provide opportunities for making vector calls without application support is to introduce system call queues to coalesce similar requests. An application issues a system call through libc, which inserts the call into a syscall queue while the application w ...
Virtual Ghost: Protecting Applications from Hostile Operating Systems
... code in order to ensure that the compiler instrumentation of kernel code is not bypassed. CFI automatically defeats control-flow hijacking attacks, including the latter class of external exploits. Together, these protections provide an additional layer of defense for secure applications on potential ...
... code in order to ensure that the compiler instrumentation of kernel code is not bypassed. CFI automatically defeats control-flow hijacking attacks, including the latter class of external exploits. Together, these protections provide an additional layer of defense for secure applications on potential ...
Abstract
... Hotplug to attach new devices. Several classes of device support hotplug, meaning that they can be inserted or removed from a running system, and Linux will discover and configure the new device. The system can therefore transition hotplug-capable devices from physical to virtual hardware by virtual ...
... Hotplug to attach new devices. Several classes of device support hotplug, meaning that they can be inserted or removed from a running system, and Linux will discover and configure the new device. The system can therefore transition hotplug-capable devices from physical to virtual hardware by virtual ...
ch9
... Dynamic Storage-Allocation Problem How to satisfy a request of size n from a list of free holes ? First-fit: Allocate the first hole that is big enough Best-fit: Allocate the smallest hole that is big enough; ...
... Dynamic Storage-Allocation Problem How to satisfy a request of size n from a list of free holes ? First-fit: Allocate the first hole that is big enough Best-fit: Allocate the smallest hole that is big enough; ...
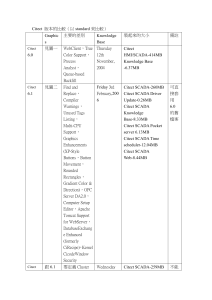
Integrate all your facilities systems with CitectFacilities V7.0
... driver are checked on load up to ensure that they were compiled against the same variable tag database. If the variable tag database has changed, the page will not be opened and a hardware alarm will be generated. This avoids the situation where the tags on a newly compiled page could be incompatibl ...
... driver are checked on load up to ensure that they were compiled against the same variable tag database. If the variable tag database has changed, the page will not be opened and a hardware alarm will be generated. This avoids the situation where the tags on a newly compiled page could be incompatibl ...
Intro to Linux Slides - Raspberry PI Summer Camp at IPFW
... support for all common and most uncommon network protocols. The standard UNIX networking tools are provided in each distribution. Next to those, most distributions offer tools for easy network installation and management. Linux is well known as a stable platform for running various Internet servic ...
... support for all common and most uncommon network protocols. The standard UNIX networking tools are provided in each distribution. Next to those, most distributions offer tools for easy network installation and management. Linux is well known as a stable platform for running various Internet servic ...
第十三章
... character device state 核心保存着I/O组件的状态,包 括打开文件表,网络连接,字符设备状态 Many, many complex data structures to track buffers, memory allocation, “dirty” blocks 许多的数据结构是为了记录缓冲、内存分配和“脏”块 Some use object-oriented methods and message passing to implement I/O 有些OS用面向对象的方法和消息机制来实现I/O ...
... character device state 核心保存着I/O组件的状态,包 括打开文件表,网络连接,字符设备状态 Many, many complex data structures to track buffers, memory allocation, “dirty” blocks 许多的数据结构是为了记录缓冲、内存分配和“脏”块 Some use object-oriented methods and message passing to implement I/O 有些OS用面向对象的方法和消息机制来实现I/O ...
Multiprocessing with the Exokernel Operating System - PDOS
... applications can use. While these abstractions provide a portable and protected view of the system, they only approximate what applications need. Often they provide either too much or not enough functionality, thus hinder certain application’s performance. The exokernel operating system addresses th ...
... applications can use. While these abstractions provide a portable and protected view of the system, they only approximate what applications need. Often they provide either too much or not enough functionality, thus hinder certain application’s performance. The exokernel operating system addresses th ...
What is an Operating System? - Sekolah Tinggi Teknik Surabaya
... switches jobs so frequently that users can interact with each job while it is running, creating interactive computing ...
... switches jobs so frequently that users can interact with each job while it is running, creating interactive computing ...
Figure 5.01 - UCSB Computer Science
... Create a number of threads in a pool where they await work Advantages: ...
... Create a number of threads in a pool where they await work Advantages: ...