Module 3: Operating
... Provision of mechanisms for: process synchronization process communication ...
... Provision of mechanisms for: process synchronization process communication ...
Presentation - The Department of Computer Science
... Writing self-stabilizing software is hard Correct and faultless SW is hard ...
... Writing self-stabilizing software is hard Correct and faultless SW is hard ...
Distributed Operating Systems
... Developed by A.S. Tanenbaum (1983 onwards) as a research tool, it uses a large number of CPUs, . Communication via RPC and provides relatively good distributive transparency, security with efficient communication but suffers from a lack of user control Aim was to develop a transparent distributed op ...
... Developed by A.S. Tanenbaum (1983 onwards) as a research tool, it uses a large number of CPUs, . Communication via RPC and provides relatively good distributive transparency, security with efficient communication but suffers from a lack of user control Aim was to develop a transparent distributed op ...
pps - AquaLab - Northwestern University
... – Block devices – stored info in fixed-size blocks; you can read/write each block independently (e.g. disk) – Character devices – I/O stream of characters (e.g. printers) ...
... – Block devices – stored info in fixed-size blocks; you can read/write each block independently (e.g. disk) – Character devices – I/O stream of characters (e.g. printers) ...
Operating-System Structures
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them ...
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them ...
Week_3 Operating system File
... • Support for threads may be provided either at the user level, for user threads, or by the kernel, for kernel threads. • User threads are supported above the kernel. • Kernel threads are supported and managed directly by the operating system. • There are three ways to establish link between user th ...
... • Support for threads may be provided either at the user level, for user threads, or by the kernel, for kernel threads. • User threads are supported above the kernel. • Kernel threads are supported and managed directly by the operating system. • There are three ways to establish link between user th ...
Operating System Structure
... Chapter 2: Operating-System Structures Operating System Services User Operating System Interface System Calls Types of System Calls System Programs Operating System Design and Implementation Operating System Structure Operating System Debugging Operating System Generation ...
... Chapter 2: Operating-System Structures Operating System Services User Operating System Interface System Calls Types of System Calls System Programs Operating System Design and Implementation Operating System Structure Operating System Debugging Operating System Generation ...
CS 519 -- Operating Systems -
... swaps the position of A and B in the LRU list and places B in a “placeholder” which points to A (kernel’s choice) If the user process misses on B (i.e. it made a bad choice), and B is found in the placeholder, then the block pointed to by the ...
... swaps the position of A and B in the LRU list and places B in a “placeholder” which points to A (kernel’s choice) If the user process misses on B (i.e. it made a bad choice), and B is found in the placeholder, then the block pointed to by the ...
COS 318: Operating Systems I/O Device and Drivers Kai Li Computer Science Department
... A process issues a read call which executes a system call System call code checks for correctness and buffer cache If it needs to perform I/O, it will issues a device driver call Device driver allocates a buffer for read and schedules I/O Controller performs DMA data transfer Block the current proce ...
... A process issues a read call which executes a system call System call code checks for correctness and buffer cache If it needs to perform I/O, it will issues a device driver call Device driver allocates a buffer for read and schedules I/O Controller performs DMA data transfer Block the current proce ...
... + Frequency of job switching is high, enabling the users to interact with each program while it is running. The CPU is multiplexed among several jobs that are kept in memory and on disk (the CPU is allocated to a job only if the job is in memory). A job is swapped in and out of memory to the disk. O ...
lect04
... Timer to prevent infinite loop / process hogging resources Set interrupt after specific period Operating system decrements counter When counter zero generate an interrupt Set up before scheduling process to regain control or terminate program that exceeds allotted time ...
... Timer to prevent infinite loop / process hogging resources Set interrupt after specific period Operating system decrements counter When counter zero generate an interrupt Set up before scheduling process to regain control or terminate program that exceeds allotted time ...
Chapter 7 Deadlocks
... its sequence of activities until the simulation period ends. The following sequence will be carried out by a Philosophers: 1. Check if the index value of the left fork is less then the index value of the right fork, then carry out the Step 2, other wise, carry out the Step 3, then Step 2. 2. Attempt ...
... its sequence of activities until the simulation period ends. The following sequence will be carried out by a Philosophers: 1. Check if the index value of the left fork is less then the index value of the right fork, then carry out the Step 2, other wise, carry out the Step 3, then Step 2. 2. Attempt ...
Slides
... multiple jobs running concurrently, resources must be allocated to each of them Many types of resources - Some (such as CPU cycles, main memory, and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code ...
... multiple jobs running concurrently, resources must be allocated to each of them Many types of resources - Some (such as CPU cycles, main memory, and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code ...
Transparent Process Migration: Design Alternatives and the Sprite Implementation
... into the kernel. In such a system the solution to the transparency problem is not as obvious; in the worst case, every kernel call might have to be specially coded to handle remote processes differently than local ones. We consider this issue in greater depth below. 4. Sprite already provides networ ...
... into the kernel. In such a system the solution to the transparency problem is not as obvious; in the worst case, every kernel call might have to be specially coded to handle remote processes differently than local ones. We consider this issue in greater depth below. 4. Sprite already provides networ ...
an introduction to solaris
... time, SunOS was implemented on Sun’s Motorola 68000-based uniprocessor workstations. SunOS was small and compact, and the workstations had only a few MIPS of processor speed and around one megabyte of memory. In the early to mid-1980s, networked UNIX systems were growing in popularity; networking wa ...
... time, SunOS was implemented on Sun’s Motorola 68000-based uniprocessor workstations. SunOS was small and compact, and the workstations had only a few MIPS of processor speed and around one megabyte of memory. In the early to mid-1980s, networked UNIX systems were growing in popularity; networking wa ...
Complete computer system simulation: the SimOS approach
... computer system complexity has increased, software simulation has become the dominant method of system testing, evaluating, and prototyping. Simulation is used at almost every step of building a computer system: from evaluation of research ideas, to verification of the hardware design, to performanc ...
... computer system complexity has increased, software simulation has become the dominant method of system testing, evaluating, and prototyping. Simulation is used at almost every step of building a computer system: from evaluation of research ideas, to verification of the hardware design, to performanc ...
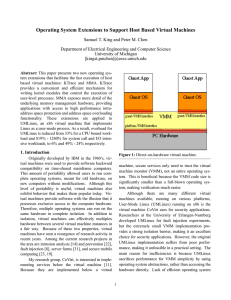
Operating System Extensions to Support Host Based Virtual Machines
... in detail: VMware, Denali, and UMLinux. 2.1. VMware VMware is the most prevalent x86 virtual machine today. By providing a complete implementation of the x86 ISA at the guest-VMM interface, VMware is a useful tool with many different applications. Although this complete guest-VMM interface is extrem ...
... in detail: VMware, Denali, and UMLinux. 2.1. VMware VMware is the most prevalent x86 virtual machine today. By providing a complete implementation of the x86 ISA at the guest-VMM interface, VMware is a useful tool with many different applications. Although this complete guest-VMM interface is extrem ...
CS465 Slides - Regis University: Academic Web Server for Faculty
... User can be very creative (and frustrated). ...
... User can be very creative (and frustrated). ...
Chapter 1: Introduction
... System call – request to the operating system to allow user to wait for I/O completion Device-status table contains entry for each I/O device indicating its type, address, and state Operating system indexes into I/O device table to determine device status and to modify table entry to include int ...
... System call – request to the operating system to allow user to wait for I/O completion Device-status table contains entry for each I/O device indicating its type, address, and state Operating system indexes into I/O device table to determine device status and to modify table entry to include int ...
[slides] Introduction to operating systems
... Wait instruction idles the CPU until the next interrupt Wait loop (contention for memory access) At most one I/O request is outstanding at a time, no simultaneous I/O processing Non-blocking call: After I/O starts, control returns to user program without waiting for I/O completion System c ...
... Wait instruction idles the CPU until the next interrupt Wait loop (contention for memory access) At most one I/O request is outstanding at a time, no simultaneous I/O processing Non-blocking call: After I/O starts, control returns to user program without waiting for I/O completion System c ...
Week 1
... • Term that refers to a computer hardware architecture and also to the OS behavior that exploits that architecture • Several processes can run in parallel • Multiple processors are transparent to the user • these processors share same main memory and I/O facilities • all processors can perform the s ...
... • Term that refers to a computer hardware architecture and also to the OS behavior that exploits that architecture • Several processes can run in parallel • Multiple processors are transparent to the user • these processors share same main memory and I/O facilities • all processors can perform the s ...
1 Introduction C H A P T E R
... of a modern computer and modern operating system. For example, a DECSYSTEM-20 simulator running on Mac OS X can boot TOPS-20, load the source tapes, and modify and compile a new TOPS-20 kernel. An interested student can search the Internet to find the original papers that describe the operating syst ...
... of a modern computer and modern operating system. For example, a DECSYSTEM-20 simulator running on Mac OS X can boot TOPS-20, load the source tapes, and modify and compile a new TOPS-20 kernel. An interested student can search the Internet to find the original papers that describe the operating syst ...
Chapter 13: I/O Systems
... Interrupt mechanisms are used for time-sensitive processing, frequent, must be fast, and manage different ...
... Interrupt mechanisms are used for time-sensitive processing, frequent, must be fast, and manage different ...
What is an Operating System?
... Group identifier (group ID) allows set of users to be defined and controls managed, then also associated with each process, file Privilege escalation allows user to change to effective ID with ...
... Group identifier (group ID) allows set of users to be defined and controls managed, then also associated with each process, file Privilege escalation allows user to change to effective ID with ...
















![[slides] Introduction to operating systems](http://s1.studyres.com/store/data/004490643_1-47ee4d56929de85b34d4b2999d518b36-300x300.png)



