Plan 9 from Bell Labs
... machines over different networks, but by making the name space equivalent in all win dows, this is transparent: the same commands and resources are available, with the same names, wherever the computation is performed. The command set of Plan 9 is similar to that of UNIX. The commands fall into sev ...
... machines over different networks, but by making the name space equivalent in all win dows, this is transparent: the same commands and resources are available, with the same names, wherever the computation is performed. The command set of Plan 9 is similar to that of UNIX. The commands fall into sev ...
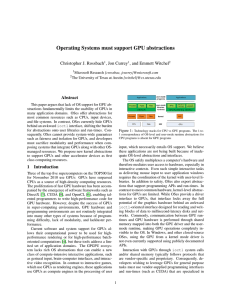
Operating Systems must support GPU abstractions
... reasonable share of its computational bandwidth. Not all ptasks have all of these scheduling requirements. A typical CUDA program does not care about low latency scheduling. Gestural interfaces require all of these mechanisms. While a ptask can exist without a dedicated user-mode host process to man ...
... reasonable share of its computational bandwidth. Not all ptasks have all of these scheduling requirements. A typical CUDA program does not care about low latency scheduling. Gestural interfaces require all of these mechanisms. While a ptask can exist without a dedicated user-mode host process to man ...
time - Computer Science and Engineering
... can pass data. Two types of semantics: blocking: sending process waits for response; non-blocking: sending process continues. ...
... can pass data. Two types of semantics: blocking: sending process waits for response; non-blocking: sending process continues. ...
SanOS - jbox.dk
... What is a jbox? • A server appliance for Java programs – Requires only power and a network connection – No monitor, keyboard, or mouse ...
... What is a jbox? • A server appliance for Java programs – Requires only power and a network connection – No monitor, keyboard, or mouse ...
Operating System Services
... Internal structure of different Operating Systems can vary widely Start the design by defining goals and specifications Affected by choice of hardware, type of system User goals and System goals User goals – operating system should be convenient to use, easy to learn, reliable, safe, and f ...
... Internal structure of different Operating Systems can vary widely Start the design by defining goals and specifications Affected by choice of hardware, type of system User goals and System goals User goals – operating system should be convenient to use, easy to learn, reliable, safe, and f ...
64-BIT TECHNOLOGY
... operating systems must be extensively modified to take advantage of the new architecture. Other software must also be ported to use the new capabilities; older software is usually supported through either a hardware compatibility mode (in which the new processors support an older 32-bit instruction ...
... operating systems must be extensively modified to take advantage of the new architecture. Other software must also be ported to use the new capabilities; older software is usually supported through either a hardware compatibility mode (in which the new processors support an older 32-bit instruction ...
Chapter 3: Operating Systems
... out operations on the peripheral devices. – translates generic requests into the more technical steps required by the device – e.g., reading and decoding a printer’s status word as well as all the other handshaking details ...
... out operations on the peripheral devices. – translates generic requests into the more technical steps required by the device – e.g., reading and decoding a printer’s status word as well as all the other handshaking details ...
UNIX-like Operating Systems
... user had sole use of the machine, program was loaded into the machine and the machine set to work, task is responsible for everything, task totaly determines behavior of computer. machines came with libraries of support code which were linked to the user’s program to assist in operations such as inp ...
... user had sole use of the machine, program was loaded into the machine and the machine set to work, task is responsible for everything, task totaly determines behavior of computer. machines came with libraries of support code which were linked to the user’s program to assist in operations such as inp ...
No Slide Title - ECE Users Pages
... - STREAM head interfaces with the user process - driver end interfaces with the device - zero or more STREAM modules between them. Each module contains a read queue and a write queue ...
... - STREAM head interfaces with the user process - driver end interfaces with the device - zero or more STREAM modules between them. Each module contains a read queue and a write queue ...
Chapter 4: Threads
... Useful when you do not have control over the thread creation process (i.e., when using a thread pool)" ...
... Useful when you do not have control over the thread creation process (i.e., when using a thread pool)" ...
Colin Roby and Jaewook Kim - WindowsThread
... Detecting multicore cpu and hardware thread Window relied on threading packages provided by processor manufactures to detect the number of cpu cores and available hardware Detect the cpu core topology – how many real hardware threads exist Detect the relationship between the hardware threads ...
... Detecting multicore cpu and hardware thread Window relied on threading packages provided by processor manufactures to detect the number of cpu cores and available hardware Detect the cpu core topology – how many real hardware threads exist Detect the relationship between the hardware threads ...
Operating system
... Clustered systems differ from multiprocessor systems, in that they are composed of two or more individual ...
... Clustered systems differ from multiprocessor systems, in that they are composed of two or more individual ...
Silberschatz, Galvin and Gagne ©2013 Operating System Concepts
... Provide details of the performance aspects of I/O hardware and software ...
... Provide details of the performance aspects of I/O hardware and software ...
Ch4-Threads - Columbus State University
... Each user-level thread kernel thread Creating a user-level thread creates a kernel thread More concurrency than many-to-one # threads per process sometimes restricted due to overhead ...
... Each user-level thread kernel thread Creating a user-level thread creates a kernel thread More concurrency than many-to-one # threads per process sometimes restricted due to overhead ...
Silberschatz, Galvin and Gagne ©2009 Operating System Concepts
... Provide details of the performance aspects of I/O hardware and software ...
... Provide details of the performance aspects of I/O hardware and software ...
TPM: A More Trustworthy Solution to Computer Security
... TCB to be built. The second generation of microkernels provided a suitable platform for secure systems to be built. But they have a slight overhead when compared to the monolithic systems as they communicate using IPC which requires switching from user privilege level to kernel privilege level and t ...
... TCB to be built. The second generation of microkernels provided a suitable platform for secure systems to be built. But they have a slight overhead when compared to the monolithic systems as they communicate using IPC which requires switching from user privilege level to kernel privilege level and t ...
Abstract- This paper presents an introduction to the technology of
... resources, in whole or in part, for use by clients. The individual resources could be ordered in some structure as a single virtual resource – for example the Network File System (NFS). The individual resources are pooled in no particular order and assigned jobs as they become available – for ex ...
... resources, in whole or in part, for use by clients. The individual resources could be ordered in some structure as a single virtual resource – for example the Network File System (NFS). The individual resources are pooled in no particular order and assigned jobs as they become available – for ex ...
Singularity: Rethinking the Software Stack
... decisions and increasingly obvious shortcomings of existing systems and software stacks. These shortcomings include: widespread security vulnerabilities; unexpected interactions among applications; failures caused by errant extensions, plug-ins, and drivers, and a perceived lack of robustness. We be ...
... decisions and increasingly obvious shortcomings of existing systems and software stacks. These shortcomings include: widespread security vulnerabilities; unexpected interactions among applications; failures caused by errant extensions, plug-ins, and drivers, and a perceived lack of robustness. We be ...
Singularity: Rethinking the Software Stack
... decisions and increasingly obvious shortcomings of existing systems and software stacks. These shortcomings include: widespread security vulnerabilities; unexpected interactions among applications; failures caused by errant extensions, plug-ins, and drivers, and a perceived lack of robustness. We be ...
... decisions and increasingly obvious shortcomings of existing systems and software stacks. These shortcomings include: widespread security vulnerabilities; unexpected interactions among applications; failures caused by errant extensions, plug-ins, and drivers, and a perceived lack of robustness. We be ...
CS 519: Operating System Theory
... instruction which cannot be executed Modify fetch-decode-execute loop to jump to a known location in the OS when an exception happens Different errors jump to different places in the OS (are "vectored" in OS speak) ...
... instruction which cannot be executed Modify fetch-decode-execute loop to jump to a known location in the OS when an exception happens Different errors jump to different places in the OS (are "vectored" in OS speak) ...
Chapter 3 Operating-System Structures 2
... Operating System Services • Program execution – system capability to load a program into memory and to run it. • I/O operations – since user programs cannot execute I/O operations directly, the operating system must provide some means to perform I/O. • File-system manipulation – program capability ...
... Operating System Services • Program execution – system capability to load a program into memory and to run it. • I/O operations – since user programs cannot execute I/O operations directly, the operating system must provide some means to perform I/O. • File-system manipulation – program capability ...
Abstract View of System Components
... the hardware among the various application programs for the various users. 3. Applications programs – define the ways in which the system resources are used to solve the computing problems of the users (compilers, database systems, ...
... the hardware among the various application programs for the various users. 3. Applications programs – define the ways in which the system resources are used to solve the computing problems of the users (compilers, database systems, ...