Homework 1
... 640KB area marked "Low Memory" was the only random-access memory (RAM) that an early PC could use; in fact the very earliest PCs only could be configured with 16KB, 32KB, or 64KB of RAM! The 384KB area from 0x000A0000 through 0x000FFFFF was reserved by the hardware for special uses such as video dis ...
... 640KB area marked "Low Memory" was the only random-access memory (RAM) that an early PC could use; in fact the very earliest PCs only could be configured with 16KB, 32KB, or 64KB of RAM! The 384KB area from 0x000A0000 through 0x000FFFFF was reserved by the hardware for special uses such as video dis ...
Slides - Choong
... Lowest fault rate for any reference string Basically, replace the page that will not be used for the longest time in the future Belady’s Rule is a yardstick We want to find close approximations ...
... Lowest fault rate for any reference string Basically, replace the page that will not be used for the longest time in the future Belady’s Rule is a yardstick We want to find close approximations ...
OS course notes - CS
... machine. It regains control if the user application performs a system call, or if there is a hardware interrupt. Exercise 1 How can the operating system guarantee that there will be a system call or interrupt, so that it will regain control? The operating system is a reactive program Another importa ...
... machine. It regains control if the user application performs a system call, or if there is a hardware interrupt. Exercise 1 How can the operating system guarantee that there will be a system call or interrupt, so that it will regain control? The operating system is a reactive program Another importa ...
Operating System Fundamentals
... some of the critical functions of any operating system. Computer architecture refers to the overall design of the physical parts of the computer. That is, it refers to: what the main parts are; how they are physically connected to each other; and how they work together; Although all of the parts of ...
... some of the critical functions of any operating system. Computer architecture refers to the overall design of the physical parts of the computer. That is, it refers to: what the main parts are; how they are physically connected to each other; and how they work together; Although all of the parts of ...
ppt
... there exist some processes that wish to enter their critical section, then the selection of the processes that will enter the critical section next cannot be postponed indefinitely 3. Bounded Waiting - A bound must exist on the number of times that other processes are allowed to enter their critical ...
... there exist some processes that wish to enter their critical section, then the selection of the processes that will enter the critical section next cannot be postponed indefinitely 3. Bounded Waiting - A bound must exist on the number of times that other processes are allowed to enter their critical ...
operating system design
... Since multiple users can be logged into a computer at the same time, the operating system needs to provide mechanisms to keep them separated. One user may not interfere with another. The process concept is widely used to group resources together for protection purposes. Files and other data structur ...
... Since multiple users can be logged into a computer at the same time, the operating system needs to provide mechanisms to keep them separated. One user may not interfere with another. The process concept is widely used to group resources together for protection purposes. Files and other data structur ...
A Real-Time Linux
... invoke each other until there are no pending interrupts left. On re-enabling software interrupts, all pending ones, of course, should be processed. The code simulates a hardware interrupt. We push the ags and the return address onto the stack, and use S_IRET (see Figure 1). Individual disabling/ena ...
... invoke each other until there are no pending interrupts left. On re-enabling software interrupts, all pending ones, of course, should be processed. The code simulates a hardware interrupt. We push the ags and the return address onto the stack, and use S_IRET (see Figure 1). Individual disabling/ena ...
A Real-Time Linux
... invoke each other until there are no pending interrupts left. On re-enabling software interrupts, all pending ones, of course, should be processed. The code simulates a hardware interrupt. We push the ags and the return address onto the stack, and use S_IRET (see Figure 1). Individual disabling/ena ...
... invoke each other until there are no pending interrupts left. On re-enabling software interrupts, all pending ones, of course, should be processed. The code simulates a hardware interrupt. We push the ags and the return address onto the stack, and use S_IRET (see Figure 1). Individual disabling/ena ...
UWB CSS 430 Operating Systems: Deadlocks
... • Algorithm: dynamically examine the resourceallocation state to ensure no circular wait CSS 430: Operating Systems - Deadlocks ...
... • Algorithm: dynamically examine the resourceallocation state to ensure no circular wait CSS 430: Operating Systems - Deadlocks ...
Appendix C: Windows 2000
... base priority), and an affinity for one or more processors Threads are the unit of execution scheduled by the kernel’s dispatcher Each thread has its own state, including a priority, processor affinity, and ...
... base priority), and an affinity for one or more processors Threads are the unit of execution scheduled by the kernel’s dispatcher Each thread has its own state, including a priority, processor affinity, and ...
PPT - EazyNotes
... The log is stored in the third metadata file at the beginning of the volume The logging functionality is provided by the 2000 log file service ...
... The log is stored in the third metadata file at the beginning of the volume The logging functionality is provided by the 2000 log file service ...
Operating Systems
... Time-Sharing Systems–Interactive Computing The CPU is multiplexed among several jobs that are kept in ...
... Time-Sharing Systems–Interactive Computing The CPU is multiplexed among several jobs that are kept in ...
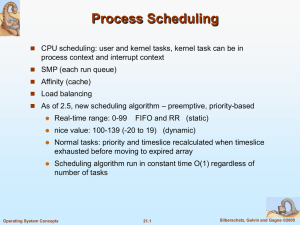
Process Management (Cont.)
... The real-time class contains threads with priorities ranging from 16 to 31 ...
... The real-time class contains threads with priorities ranging from 16 to 31 ...
Figure 5.01
... A signal is generated by the occurrence of a particular event A generated signal is delivered to a process Once delivered, the signal must be handled ...
... A signal is generated by the occurrence of a particular event A generated signal is delivered to a process Once delivered, the signal must be handled ...
Chapter 5 - Process Management
... Resume system normalcy quickly and gracefully and regain the resources ...
... Resume system normalcy quickly and gracefully and regain the resources ...
Peripheral handling
... output time is long, CPU may not need to check the device frequently until an other IRQ is sent by the device. ...
... output time is long, CPU may not need to check the device frequently until an other IRQ is sent by the device. ...
Good practice guide: General advice on securing operating
... that are not required should be disabled. Any services that are required should have the latest security patches applied in accordance with an organisational patching policy. Access to the services should be limited to the minimum number of remote users wherever possible. The same steps should be ap ...
... that are not required should be disabled. Any services that are required should have the latest security patches applied in accordance with an organisational patching policy. Access to the services should be limited to the minimum number of remote users wherever possible. The same steps should be ap ...
The Sprite Network Operating System
... for read-only code. Each process had private data and stack segments, as shown in Figure 1. Since then, extensions to allow read-write memory sharing have been implemented or proposed for several versions of UNIX, including System V, SunOS, Berkeley UNIX, and Mach. There are two reasons for providin ...
... for read-only code. Each process had private data and stack segments, as shown in Figure 1. Since then, extensions to allow read-write memory sharing have been implemented or proposed for several versions of UNIX, including System V, SunOS, Berkeley UNIX, and Mach. There are two reasons for providin ...