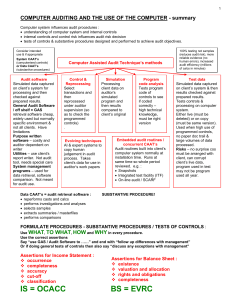
Completeness
... Collection of cash receipts Incoming mail must be opened by a person who does not have access to the A/R ledger Receipts should be listed in detail – A copy & actual receipts sent to the cashier for bank deposit – Another copy to the A/R Dept. for entry in the A/R ledger – Another copy to the accoun ...
... Collection of cash receipts Incoming mail must be opened by a person who does not have access to the A/R ledger Receipts should be listed in detail – A copy & actual receipts sent to the cashier for bank deposit – Another copy to the A/R Dept. for entry in the A/R ledger – Another copy to the accoun ...
1 Exposure Scenario 1: Manufacturing of liquid NaOH
... Workers in the risky process/areas identified should be trained a) to avoid to work without respiratory protection and b) to understand the corrosive properties and, especially, the respiratory inhalation effects of sodium hydroxide and c) to follow the safer procedures instructed by the employer. T ...
... Workers in the risky process/areas identified should be trained a) to avoid to work without respiratory protection and b) to understand the corrosive properties and, especially, the respiratory inhalation effects of sodium hydroxide and c) to follow the safer procedures instructed by the employer. T ...
Breaking the Cycle of Fraud - Financial Executives International
... the onus remains with an organization to explore what can be done to reduce its risk of fraud. This Financial Executive Research Foundation (FERF) report reviews recent major fraud cases to highlight the similarities of what transpired, how these frauds were detected, and what was done in response. ...
... the onus remains with an organization to explore what can be done to reduce its risk of fraud. This Financial Executive Research Foundation (FERF) report reviews recent major fraud cases to highlight the similarities of what transpired, how these frauds were detected, and what was done in response. ...
IFRS 7 Financial Instruments: Disclosures
... Quantitative Quantitative disclosures disclosures Credit risk ...
... Quantitative Quantitative disclosures disclosures Credit risk ...
The Auditor - Whose Agent Is He Anyway
... framework would improve the quality of financial reporting. Failing this framework, Peasnell questions whether the auditing function would be a viable alternative for ‘organising and policing’ corporate disclosure. He describes how there are those who view external auditing as a largely useless lega ...
... framework would improve the quality of financial reporting. Failing this framework, Peasnell questions whether the auditing function would be a viable alternative for ‘organising and policing’ corporate disclosure. He describes how there are those who view external auditing as a largely useless lega ...
A GUIDE TO STATUTORY AUDIT PROCEDURES ON EXPECTED
... IFRS 9 and to specify the appropriate level of documentation to be produced by credit institutions to justify their level of provisioning. The procedures presented primarily concern credit institutions with a high degree of sophistication. Where necessary, they will be adapted for credit institution ...
... IFRS 9 and to specify the appropriate level of documentation to be produced by credit institutions to justify their level of provisioning. The procedures presented primarily concern credit institutions with a high degree of sophistication. Where necessary, they will be adapted for credit institution ...
Comprehensive Case A.1 – Enron
... reliability of various kinds of evidence are subject to important exceptions.” So, the competence of audit evidence refers to the quality of the evidence gathered for a financial statement assertion about a financial statement account balance and/or an economic transaction(s). And, as indicated in ...
... reliability of various kinds of evidence are subject to important exceptions.” So, the competence of audit evidence refers to the quality of the evidence gathered for a financial statement assertion about a financial statement account balance and/or an economic transaction(s). And, as indicated in ...
A FOOL WITH A TOOL IS STILL A FOOL! White Paper
... fully, through the implementation of technology, only to discover that the problem, in some form or another, still remains. Even if the problem does get addressed it is sometimes difficult to realize a return on the investment made in the tools and the effort of the implementation. Quite often, beca ...
... fully, through the implementation of technology, only to discover that the problem, in some form or another, still remains. Even if the problem does get addressed it is sometimes difficult to realize a return on the investment made in the tools and the effort of the implementation. Quite often, beca ...
Legionella Risk Management - Cooling Tower Maintenance Inc
... Chlorine dioxide is also an effective supplemental biocide for process cooling systems where contaminants that increase bacterial growth are present. *Alternative choices of non-oxidizing biocide should be based on RPD results ...
... Chlorine dioxide is also an effective supplemental biocide for process cooling systems where contaminants that increase bacterial growth are present. *Alternative choices of non-oxidizing biocide should be based on RPD results ...
Document
... • Order quantity for next interval? • Suppliers might encourage fixed intervals • May require only periodic checks of inventory levels ...
... • Order quantity for next interval? • Suppliers might encourage fixed intervals • May require only periodic checks of inventory levels ...
Assignment 1 is compulsory and due
... find the last GRN for the year and then search for any GRN number that is higher then that that has been processed (shouldn’t be any) extract and compare all the payments made to suppliers to the purchases in the GL use transaction date in the masterfile to extract a sample of purchase invoice ...
... find the last GRN for the year and then search for any GRN number that is higher then that that has been processed (shouldn’t be any) extract and compare all the payments made to suppliers to the purchases in the GL use transaction date in the masterfile to extract a sample of purchase invoice ...
Dev/ops
... collaboration and communication of both software developers and IT professionals while automating the process of software delivery and infrastructure changes. It aims at establishing a culture and environment where building, testing, and releasing software can happen rapidly, frequently, and more re ...
... collaboration and communication of both software developers and IT professionals while automating the process of software delivery and infrastructure changes. It aims at establishing a culture and environment where building, testing, and releasing software can happen rapidly, frequently, and more re ...
HRT 2010
... Begin HRT at the lowest possible dose and increase at 3/12 intervals if reqd ► Record that the risks of HRT have been explained and that an informed decision has been taken by the patient ► HRT patches last ¾ days or 7 days and are placed below waist and sites rotated ...
... Begin HRT at the lowest possible dose and increase at 3/12 intervals if reqd ► Record that the risks of HRT have been explained and that an informed decision has been taken by the patient ► HRT patches last ¾ days or 7 days and are placed below waist and sites rotated ...
Implementation Tool for Auditors
... To the extent not already done so, obtain an understanding of the entity’s related controls, including control activities, relevant to the identified risk. Once the auditor has concluded that ROMM due to fraud in revenue recognition exists for all or only certain types of revenue and revenue transac ...
... To the extent not already done so, obtain an understanding of the entity’s related controls, including control activities, relevant to the identified risk. Once the auditor has concluded that ROMM due to fraud in revenue recognition exists for all or only certain types of revenue and revenue transac ...
Sensitivity, Specificity, and Useful Measures of Diagnostic Utility
... Do away with “positive” and “negative” Problems with Traditional Indexes Decision Making and Forward Risk Diagnostic Risk Modeling Assessing Diagnostic Yield Summary References ...
... Do away with “positive” and “negative” Problems with Traditional Indexes Decision Making and Forward Risk Diagnostic Risk Modeling Assessing Diagnostic Yield Summary References ...
Bayesian approach for benefit
... variance. βj ; j=1,…,5 are independent normal with means 0, and large variances. The posterior distributions of the probability and the global measures can be derived, and the decision rules can be determined based on the credible intervals. ...
... variance. βj ; j=1,…,5 are independent normal with means 0, and large variances. The posterior distributions of the probability and the global measures can be derived, and the decision rules can be determined based on the credible intervals. ...
documentation of the entity and its environment
... ___ Moderate ___ Limited Ability to prepare: Financial statements: ___ Competent ___ Limited Notes to financial statements: ___ Competent ___ Limited Knowledge of applicable laws and regulations: ___ Extensive ___ Moderate ...
... ___ Moderate ___ Limited Ability to prepare: Financial statements: ___ Competent ___ Limited Notes to financial statements: ___ Competent ___ Limited Knowledge of applicable laws and regulations: ___ Extensive ___ Moderate ...
The Optimal Draw-down for a Charity
... Indeed, in many cases, endowments state in their charter that they are endowed to provide some sort of support in perpetuity. It is interesting that whilst the charity can take a very long-term approach, the needs of their clients, at least in a research context, may be very short-lived indeed, so w ...
... Indeed, in many cases, endowments state in their charter that they are endowed to provide some sort of support in perpetuity. It is interesting that whilst the charity can take a very long-term approach, the needs of their clients, at least in a research context, may be very short-lived indeed, so w ...
Does Fair Value Reporting Affect Risk Management?
... earnings and equity volatility will choose to curtail valuable hedging activities as a result of these rules. Anecdotal evidence suggests that the way in which derivatives are reported is indeed a major driving force of firms’ risk management choices, but academic evidence on this area is scarce.2 T ...
... earnings and equity volatility will choose to curtail valuable hedging activities as a result of these rules. Anecdotal evidence suggests that the way in which derivatives are reported is indeed a major driving force of firms’ risk management choices, but academic evidence on this area is scarce.2 T ...
Postpartum hemorrhage and the B-Lynch technique. Prof Faustino R
... Although uterine atony is the indication for use of modified B-Lynch suture, but it has been shown in many case reports that this suture is also useful in controlling bleeding in cases of placenta previa and placenta accreta. ...
... Although uterine atony is the indication for use of modified B-Lynch suture, but it has been shown in many case reports that this suture is also useful in controlling bleeding in cases of placenta previa and placenta accreta. ...
Risk Analysis - University at Albany
... • Different stakeholders have various perception of risk • Several sources of threats exist simultaneously Sanjay Goel, School of Business/Center for Information Forensics and Assurance University at Albany Proprietary Information ...
... • Different stakeholders have various perception of risk • Several sources of threats exist simultaneously Sanjay Goel, School of Business/Center for Information Forensics and Assurance University at Albany Proprietary Information ...
ORRS 2011 (Text)
... Changes to the Operational Risk reporting standards must be approved by the Board of ORX. The Definitions Working Group has the responsibility for reviewing the Operational Risk Reporting Standards and making recommendations to the Board of ORX. The Definitions Working Group will review requests fro ...
... Changes to the Operational Risk reporting standards must be approved by the Board of ORX. The Definitions Working Group has the responsibility for reviewing the Operational Risk Reporting Standards and making recommendations to the Board of ORX. The Definitions Working Group will review requests fro ...
download
... responsibilities. An effective control environment is an environment where competent people understand their responsibilities, the limits to their authority, and are knowledgeable, mindful, and committed to doing what is right and doing it the right way. They are committed to following an organizati ...
... responsibilities. An effective control environment is an environment where competent people understand their responsibilities, the limits to their authority, and are knowledgeable, mindful, and committed to doing what is right and doing it the right way. They are committed to following an organizati ...
ra-5 vulnerability scanning control
... reporting thereafter that ideally shows remediation progress. While FedRAMP encourages (but does not prescribe) that the CSP and assessors use the same scanning tool, it is imperative that assessment and continuous monitoring results are consistent. In order to achieve these objectives, FedRAMP has ...
... reporting thereafter that ideally shows remediation progress. While FedRAMP encourages (but does not prescribe) that the CSP and assessors use the same scanning tool, it is imperative that assessment and continuous monitoring results are consistent. In order to achieve these objectives, FedRAMP has ...
Competency area - Chartered Institute of Internal Auditors
... Recognises where IT is relevant within an audit assignment (including security of systems involving access control, environmental controls, compliance with IT policies and procedures, and management of the IT activity), and can participate in IT projects and provide input on potential risk exposures ...
... Recognises where IT is relevant within an audit assignment (including security of systems involving access control, environmental controls, compliance with IT policies and procedures, and management of the IT activity), and can participate in IT projects and provide input on potential risk exposures ...