Chapter 10 Introduction to MAN and WAN
... requires both sender and receiver to create a connection before any data is transferred. Applications such as large file transfers and sensitive transactions such as banking and business are typically connection-oriented. can operate over both a circuit-switched network or a packetswitched network. ...
... requires both sender and receiver to create a connection before any data is transferred. Applications such as large file transfers and sensitive transactions such as banking and business are typically connection-oriented. can operate over both a circuit-switched network or a packetswitched network. ...
Secure Distance-Based Localization in the
... Although the analytical results and bounds presented here are ...
... Although the analytical results and bounds presented here are ...
In PDF
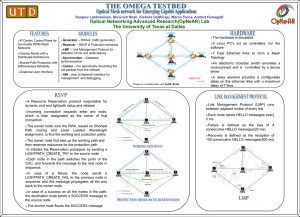
... Every HELLO_INTERVAL mili-seconds, a node sends a hello packet to all of its neighbors. When a host receives a HELLO packet, it records the link as operational. If no HELLO packet has been received from a neighboring host in the past DEAD_INTERVAL mili-seconds, it assumes the link (or host) has fail ...
... Every HELLO_INTERVAL mili-seconds, a node sends a hello packet to all of its neighbors. When a host receives a HELLO packet, it records the link as operational. If no HELLO packet has been received from a neighboring host in the past DEAD_INTERVAL mili-seconds, it assumes the link (or host) has fail ...
CoolStreaming,_DONet_A_Data-driven_Overlay_Network_for_Peer
... Resort a simple heuristic of fast response time ...
... Resort a simple heuristic of fast response time ...
Broadcast-and-select networks
... • Estimates the round trip delay • A node transmits the information one round trip delay prior to the estimated time of arrival. ...
... • Estimates the round trip delay • A node transmits the information one round trip delay prior to the estimated time of arrival. ...
System Model
... making process is determined by a random number. Nodes in our network are selfish and rational which means they all want to get the maximum revenue in the network and when their utility is less than zero, they will give up the opportunity to use the ...
... making process is determined by a random number. Nodes in our network are selfish and rational which means they all want to get the maximum revenue in the network and when their utility is less than zero, they will give up the opportunity to use the ...
Abstract
... The evolution of the Internet towards ubiquity, mobility and wireless requires revising routing for such “large” dynamic clouds. Routing is obviously a critical network functionality, but, it has not evolved much since long. Routing has a strong impact on the architecture, as it is tightly associate ...
... The evolution of the Internet towards ubiquity, mobility and wireless requires revising routing for such “large” dynamic clouds. Routing is obviously a critical network functionality, but, it has not evolved much since long. Routing has a strong impact on the architecture, as it is tightly associate ...
mat379.sp05.ExamAnswers
... 10. (10 points) Border Gateway Protocol i. Mention and briefly describe two features of the Border Gateway Protocol (BGP) that make it more suitable for routing in the global Internet than either the Routing Information Protocol (RIP) or the Open Shortest Path First (OSPF) Protocol. BGP allows polic ...
... 10. (10 points) Border Gateway Protocol i. Mention and briefly describe two features of the Border Gateway Protocol (BGP) that make it more suitable for routing in the global Internet than either the Routing Information Protocol (RIP) or the Open Shortest Path First (OSPF) Protocol. BGP allows polic ...
Integrated Telecommunication Networks I
... 1. Assume that the distance-vector routing protocol with poison reverse is used on the network depicted on the right to generate the routing tables. The network consists of five routers (A to E) interconnected by the seven connections represented. a) Calculate the content of the distance vectors sen ...
... 1. Assume that the distance-vector routing protocol with poison reverse is used on the network depicted on the right to generate the routing tables. The network consists of five routers (A to E) interconnected by the seven connections represented. a) Calculate the content of the distance vectors sen ...
Chapter 5 - CMPE150, Winter 17, Section 01
... that take place, starting from powering on your PC to getting the Web page? Assume there is nothing in our DNS or browser caches when you power on your PC. (Hint: the steps include the use of Ethernet, DHCP, ARP, DNS, TCP, and HTTP protocols.) Explicitly indicate in your steps how you obtain the IP ...
... that take place, starting from powering on your PC to getting the Web page? Assume there is nothing in our DNS or browser caches when you power on your PC. (Hint: the steps include the use of Ethernet, DHCP, ARP, DNS, TCP, and HTTP protocols.) Explicitly indicate in your steps how you obtain the IP ...
Here is the Power Point Presentation on Chord
... The later peer-to-peer networks, like Gnutella, are fully distributed, but don’t have the guarantees Napster had for finding files If a file lay beyond your number of hops on the network, you might not find it ...
... The later peer-to-peer networks, like Gnutella, are fully distributed, but don’t have the guarantees Napster had for finding files If a file lay beyond your number of hops on the network, you might not find it ...
Network Layer
... Link State Routing Algorithm 1. Each router is responsible for meeting its neighbors and learning their names. 2. Each router constructs a link state packet (LSP) which consists of a list of names and cost for each of its neighbors. 3. The LSP is transmitted to all other routers. Each router stores ...
... Link State Routing Algorithm 1. Each router is responsible for meeting its neighbors and learning their names. 2. Each router constructs a link state packet (LSP) which consists of a list of names and cost for each of its neighbors. 3. The LSP is transmitted to all other routers. Each router stores ...
related work
... Roofnet's design assumes that a small fraction of Roofnet users will voluntarily share their wired Internet access links On start-up, each Roofnet node checks to see if it can reach the Internet through its Ethernet port If this succeeds, the node advertises itself to Roofnet as an Internet gate ...
... Roofnet's design assumes that a small fraction of Roofnet users will voluntarily share their wired Internet access links On start-up, each Roofnet node checks to see if it can reach the Internet through its Ethernet port If this succeeds, the node advertises itself to Roofnet as an Internet gate ...
L h
... RIP (Routing information Protocol 路由信息协议 ) is a distance-vector protocol that allows routers to exchange information about destinations for computing routes throughout the network. OSPF (Open Shortest Path First 开放最短路径优先) is a dynamic routing protocol for use in Internet Protocol (IP) networks. ...
... RIP (Routing information Protocol 路由信息协议 ) is a distance-vector protocol that allows routers to exchange information about destinations for computing routes throughout the network. OSPF (Open Shortest Path First 开放最短路径优先) is a dynamic routing protocol for use in Internet Protocol (IP) networks. ...
Homework 6
... Give a formula for the expected number of nodes with no in-coming links in a network grown randomly according to this model. (Again, specify this using an expression without large summations.) (2) (KT Exercise 13.15) Suppose you are presented with a very large set S of real numbers, and you’d like ...
... Give a formula for the expected number of nodes with no in-coming links in a network grown randomly according to this model. (Again, specify this using an expression without large summations.) (2) (KT Exercise 13.15) Suppose you are presented with a very large set S of real numbers, and you’d like ...
Abstract - Chennai Sunday
... reconvergence of an Interior Gateway Protocol (IGP) (e.g., OSPF or IS-IS) can take hundreds of milliseconds, there is a need for a method that will find an alternate path in less time than this. The target application is a small (up to tens of nodes) access subnetwork of a service provider’s network ...
... reconvergence of an Interior Gateway Protocol (IGP) (e.g., OSPF or IS-IS) can take hundreds of milliseconds, there is a need for a method that will find an alternate path in less time than this. The target application is a small (up to tens of nodes) access subnetwork of a service provider’s network ...
route1
... • One of the oldest algorithm for routing • Finds SP by developing paths in order of increasing length – Requires each node to have complete information about the network – Nodes exchange information with all other nodes in the network – Known to converge quickly under static conditions – Does not g ...
... • One of the oldest algorithm for routing • Finds SP by developing paths in order of increasing length – Requires each node to have complete information about the network – Nodes exchange information with all other nodes in the network – Known to converge quickly under static conditions – Does not g ...
GPSR: Greedy Perimeter Stateless Routing for Wireless Networks
... x) is y. Even though there are other neighboring nodes with in x’s radio range closer to x than y, none of them are as close to D as y is and therefore x will send its information to y, which will use the greedy forwarding algorithm to send it to the next node until the information reaches the final ...
... x) is y. Even though there are other neighboring nodes with in x’s radio range closer to x than y, none of them are as close to D as y is and therefore x will send its information to y, which will use the greedy forwarding algorithm to send it to the next node until the information reaches the final ...