Mathematical Biology - University of Louisville Department of
... because spreading speeds are only asymptotic speeds. That is, a particular component vn (x) need not be zero ahead of its front, but may have a small positive tail. If vn appears as a driving (in-migration) term in the recursion for another component wn , the small value of vn at a point x well beyo ...
... because spreading speeds are only asymptotic speeds. That is, a particular component vn (x) need not be zero ahead of its front, but may have a small positive tail. If vn appears as a driving (in-migration) term in the recursion for another component wn , the small value of vn at a point x well beyo ...
(1-4) Defining Member Functions Member functions can be defined
... Since these functions do not return any value, their return-type is void. The member functions have some special characters that are often used in the program development. • Several different classes can use the same function name. the 'membership label' will resolve their scope. • Member functions ...
... Since these functions do not return any value, their return-type is void. The member functions have some special characters that are often used in the program development. • Several different classes can use the same function name. the 'membership label' will resolve their scope. • Member functions ...
Document
... ground temperature is 20C and the temperature at a height of 1 km is 10C, express the temperature T (in °C) as a function of the height h (in kilometers), assuming that a linear model is appropriate. (b) Draw the graph of the function in part (a). What does the slope represent? (c) What is the tem ...
... ground temperature is 20C and the temperature at a height of 1 km is 10C, express the temperature T (in °C) as a function of the height h (in kilometers), assuming that a linear model is appropriate. (b) Draw the graph of the function in part (a). What does the slope represent? (c) What is the tem ...
a basis for a mathematical theory of computation
... subscripts) for variables and will suppose that there is a notation for constants that does not make expressions ambiguous. (Thus, the decimal notation is allowed for constants when we are dealing with integers.) The class of forms is defined recursively as follows: (i) A variable x with an associat ...
... subscripts) for variables and will suppose that there is a notation for constants that does not make expressions ambiguous. (Thus, the decimal notation is allowed for constants when we are dealing with integers.) The class of forms is defined recursively as follows: (i) A variable x with an associat ...
A Basis for a Mathematical Theory of Computation
... subscripts) for variables and will suppose that there is a notation for constants that does not make expressions ambiguous. (Thus, the decimal notation is allowed for constants when we are dealing with integers.) The class of forms is defined recursively as follows: (i) A variable x with an associat ...
... subscripts) for variables and will suppose that there is a notation for constants that does not make expressions ambiguous. (Thus, the decimal notation is allowed for constants when we are dealing with integers.) The class of forms is defined recursively as follows: (i) A variable x with an associat ...
Chapter 8 Primal-Dual Method and Local Ratio
... By the inductive hypothesis it is 2-approximate with respect to w2. We claim that it is also 2-approximate with respect to w1 . In fact, every feasible solution is 2-approximate with respect to w1 . ...
... By the inductive hypothesis it is 2-approximate with respect to w2. We claim that it is also 2-approximate with respect to w1 . In fact, every feasible solution is 2-approximate with respect to w1 . ...
Optimization Techniques
... The values inside the node show the value of state variable at each stage ...
... The values inside the node show the value of state variable at each stage ...
Unreachable functions
... way: The operations of the algebra are the fundamental operations in the computing device. The elements of the algebra are the values with which the computing device can compute. The bijections are the functions that determine an assignment of the values to storage locations, in a one-to-one correla ...
... way: The operations of the algebra are the fundamental operations in the computing device. The elements of the algebra are the values with which the computing device can compute. The bijections are the functions that determine an assignment of the values to storage locations, in a one-to-one correla ...
Extending Theon`s Ladder to Any Square Root
... vergence of yn /xn to 2 √ is slow. From the above calculations, it appears that we gain an extra decimal digit in 2 after calculating another one or two rungs of the ladder. We will investigate more features of this ladder. We will show how to modify it to calculate the square root of any number, we ...
... vergence of yn /xn to 2 √ is slow. From the above calculations, it appears that we gain an extra decimal digit in 2 after calculating another one or two rungs of the ladder. We will investigate more features of this ladder. We will show how to modify it to calculate the square root of any number, we ...
Inductive datatypes in HOL — lessons learned in Formal
... derived concepts, but also general mechanisms for introducing certain kinds of mathematical objects. A typical example of the latter would be inductive sets and types, together with recursive function definitions. According to folklore, theorem proving is similar to programming, but slightly more di ...
... derived concepts, but also general mechanisms for introducing certain kinds of mathematical objects. A typical example of the latter would be inductive sets and types, together with recursive function definitions. According to folklore, theorem proving is similar to programming, but slightly more di ...
AP Calculus - ceemrr.com
... The limit of a function f ( x) as x approaches some number a is the value the function is getting close to as x gets close to a. It is not necessarily equal to the value of the function when x = a. If it does equal that value, then the function is said to be continuous at x = a. ...
... The limit of a function f ( x) as x approaches some number a is the value the function is getting close to as x gets close to a. It is not necessarily equal to the value of the function when x = a. If it does equal that value, then the function is said to be continuous at x = a. ...
Data Structures - Exercises
... smaller, we can go to the left. If its larger, we need to get the count of the left elements and go to the right. If we find the element, we will return the count of elements, smaller than it. ...
... smaller, we can go to the left. If its larger, we need to get the count of the left elements and go to the right. If we find the element, we will return the count of elements, smaller than it. ...
types of proofs
... formal logic. There are some basic techniques for proving things, on the basis of different ...
... formal logic. There are some basic techniques for proving things, on the basis of different ...
The Utility Frontier
... Any allocation (xi )n1 to a set N = {1, . . . , n} of individuals with utility functions u1 (·), . . . , un (·) yields a profile (u1 , . . . , un ) of resulting utility levels, as depicted in Figure 1 for the case n = 2. (Throughout this set of notes, in order to distinguish between utility function ...
... Any allocation (xi )n1 to a set N = {1, . . . , n} of individuals with utility functions u1 (·), . . . , un (·) yields a profile (u1 , . . . , un ) of resulting utility levels, as depicted in Figure 1 for the case n = 2. (Throughout this set of notes, in order to distinguish between utility function ...
FUNCTIONS TEST STUDY GUIDE Test covers
... Write the inverse of the following functions. State whether the inverse is a function. Explain how you know the inverse of the function is a function. a) f(x) = ...
... Write the inverse of the following functions. State whether the inverse is a function. Explain how you know the inverse of the function is a function. a) f(x) = ...
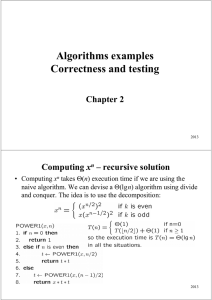
Algorithms examples Correctness and testing
... • Sometimes it is easy to derive an iterative solution from the recursive one. Iterative solutions are in general more efficient than the recursive ones because the recursive calls are avoided. Note that divisibility tests and divisions by 2 can be implemented using bit operations. n is even if its ...
... • Sometimes it is easy to derive an iterative solution from the recursive one. Iterative solutions are in general more efficient than the recursive ones because the recursive calls are avoided. Note that divisibility tests and divisions by 2 can be implemented using bit operations. n is even if its ...
14 - Villanova Computer Science
... classes) that interact by passing messages that transform the state. • Need to know: – Ways of sending messages – Inheritance – Polymorphism ...
... classes) that interact by passing messages that transform the state. • Need to know: – Ways of sending messages – Inheritance – Polymorphism ...
Functions 1 - Portal UniMAP
... A C program is generally formed by a set of functions, which subsequently consist of many programming statements. Using functions, a large computing task can be broken into smaller ones. Functions can be created to execute small, frequently-used tasks. In C, there are predefined functions or sometim ...
... A C program is generally formed by a set of functions, which subsequently consist of many programming statements. Using functions, a large computing task can be broken into smaller ones. Functions can be created to execute small, frequently-used tasks. In C, there are predefined functions or sometim ...
124370-hw2-1-
... 9. [3 pts] Given the following input array [40, 10, 30, 80, 5, 60] show as a “heap” (in binary tree form). Note that this initial “heap” may not satisfy the max-heap property. ...
... 9. [3 pts] Given the following input array [40, 10, 30, 80, 5, 60] show as a “heap” (in binary tree form). Note that this initial “heap” may not satisfy the max-heap property. ...
Substitution method
... We may operate log on both sides (log is a monotonic increasing function and thus we are allowed to do this): log(logn) ≤ ( x 1) log n log c (0.585 ) log n log c Next, we need to find values of c, , n0 , such that: log(logn) ≤ (0.585 ) log n log c Let's choose c=1: log(logn) ...
... We may operate log on both sides (log is a monotonic increasing function and thus we are allowed to do this): log(logn) ≤ ( x 1) log n log c (0.585 ) log n log c Next, we need to find values of c, , n0 , such that: log(logn) ≤ (0.585 ) log n log c Let's choose c=1: log(logn) ...
Math 1100: Quantitative Analysis Limits of Rational Functions Limits of Polynomial Functions
... • If g(x) = 0 and f (x) = 0, then we can factor (x − c) out of the numerator and denominator and proceed with a new function. This case may correspond to a hole in the graph (in which case the limit exists) or to a vertical asymptote (in which case it does not). ...
... • If g(x) = 0 and f (x) = 0, then we can factor (x − c) out of the numerator and denominator and proceed with a new function. This case may correspond to a hole in the graph (in which case the limit exists) or to a vertical asymptote (in which case it does not). ...
Functions
... functions (and avoids state) • Data and programs are represented in the same way • Functions as first-class values – Higher-order functions: functions that operate on, or create, other functions – Functions as components of data structures • Lambda calculus provides a theoretical framework for descr ...
... functions (and avoids state) • Data and programs are represented in the same way • Functions as first-class values – Higher-order functions: functions that operate on, or create, other functions – Functions as components of data structures • Lambda calculus provides a theoretical framework for descr ...
Recursion (computer science)
Recursion in computer science is a method where the solution to a problem depends on solutions to smaller instances of the same problem (as opposed to iteration). The approach can be applied to many types of problems, and recursion is one of the central ideas of computer science.""The power of recursion evidently lies in the possibility of defining an infinite set of objects by a finite statement. In the same manner, an infinite number of computations can be described by a finite recursive program, even if this program contains no explicit repetitions.""Most computer programming languages support recursion by allowing a function to call itself within the program text. Some functional programming languages do not define any looping constructs but rely solely on recursion to repeatedly call code. Computability theory proves that these recursive-only languages are Turing complete; they are as computationally powerful as Turing complete imperative languages, meaning they can solve the same kinds of problems as imperative languages even without iterative control structures such as “while” and “for”.