Exam2-1010-S13-LinearAlgebra.pdf
... Exam 2, 10:10 am, March 12, 2013 [5] Let V be the vector space of all polynomials of degree 6 3 in the variable x with coefficients in R. Let W be the subspace of polynomials satisfying f(0) = f 0 (0) = 0. Find an orthogonal basis for W with respect to the inner product ...
... Exam 2, 10:10 am, March 12, 2013 [5] Let V be the vector space of all polynomials of degree 6 3 in the variable x with coefficients in R. Let W be the subspace of polynomials satisfying f(0) = f 0 (0) = 0. Find an orthogonal basis for W with respect to the inner product ...
Algebra 2 - TeacherWeb
... 27. Use a graphing calculator to find the relative minimum, relative maximum, and zeros of . If necessary, round to the nearest hundredth. 28. The volume in cubic feet of a workshop’s storage chest can be expressed as the product of its three dimensions: . The depth is x + 1. ...
... 27. Use a graphing calculator to find the relative minimum, relative maximum, and zeros of . If necessary, round to the nearest hundredth. 28. The volume in cubic feet of a workshop’s storage chest can be expressed as the product of its three dimensions: . The depth is x + 1. ...
DS Lecture 9
... Statement: Any number n 2 is expressible as a unique product of 1 or more prime numbers. (Note: prime numbers are considered to be “products” of 1 prime. We’ll need induction and some more number theory tools to prove this). ...
... Statement: Any number n 2 is expressible as a unique product of 1 or more prime numbers. (Note: prime numbers are considered to be “products” of 1 prime. We’ll need induction and some more number theory tools to prove this). ...
Computing Greatest Common Divisors and Factorizations in
... as small as possible; neither can this reduce the number of divisions needed, nor does there exist even a single input ( ρ 0, ρ1) for which the computation of GCD( ρ 0, ρ1) succeeds by choosing a non-minimal remainder at some stage, but does not succeed otherwise. It has previously been shown for ce ...
... as small as possible; neither can this reduce the number of divisions needed, nor does there exist even a single input ( ρ 0, ρ1) for which the computation of GCD( ρ 0, ρ1) succeeds by choosing a non-minimal remainder at some stage, but does not succeed otherwise. It has previously been shown for ce ...
Generic Linear Algebra and Quotient Rings in Maple - CECM
... The algorithms for linear algebra in the Magma and Axiom computer algebra systems work over an arbitrary ring. For example, the implementation of Gaussian elimination for reducing a matrix to (reduced) row Echelon form works over any field that the user constructs. In contrast, Maple’s facilities fo ...
... The algorithms for linear algebra in the Magma and Axiom computer algebra systems work over an arbitrary ring. For example, the implementation of Gaussian elimination for reducing a matrix to (reduced) row Echelon form works over any field that the user constructs. In contrast, Maple’s facilities fo ...
Shiftless Decomposition and Polynomial
... It is well known that the size of R may be exponentially large as a function of the size of F . Consider the case K = . The algorithm we present here is distinguished from previous algorithms because it always returns a compact representation of R in time polynomial in the input size. For example, i ...
... It is well known that the size of R may be exponentially large as a function of the size of F . Consider the case K = . The algorithm we present here is distinguished from previous algorithms because it always returns a compact representation of R in time polynomial in the input size. For example, i ...
Elementary Number Theory
... discovered, is the fastest known algorithm for computing the gcd of any two given numbers. It has a surprising number of applications to computer science, and is extremely useful in cryptography. As an application of the Euclidean algorithm we have the following important result. A.6. Theorem. Let a ...
... discovered, is the fastest known algorithm for computing the gcd of any two given numbers. It has a surprising number of applications to computer science, and is extremely useful in cryptography. As an application of the Euclidean algorithm we have the following important result. A.6. Theorem. Let a ...
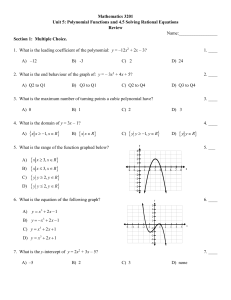
Algebra II (10) Semester 2 Exam Outline – May 2015 Unit 1
... Algebra II (10) Semester 2 Exam Outline – May 2015 Unit 1: Polynomial Functions Identify, evaluate, add and subtract polynomials. (6.1) Classify and graph polynomials. (6.1) Multiply polynomials, use binomial expansion to expand binomial expressions that are raised to positive integer powers. ...
... Algebra II (10) Semester 2 Exam Outline – May 2015 Unit 1: Polynomial Functions Identify, evaluate, add and subtract polynomials. (6.1) Classify and graph polynomials. (6.1) Multiply polynomials, use binomial expansion to expand binomial expressions that are raised to positive integer powers. ...