Beginners Guide to EDI X12 (including HIPAA)
... These are segment identifiers. Based on those we can have basic idea what data is contained in the segment. ...
... These are segment identifiers. Based on those we can have basic idea what data is contained in the segment. ...
Powering Your Organization's Web Applications with SAS® Software
... Organizations that do not license SAS/IntrNet software can still use the power of SAS to create content for their Internet and intranet web applications. However, it will not be as dynamic as when using SAS/IntrNet. That is; when SAS/IntrNet is executed, any web pages that are created exist for a br ...
... Organizations that do not license SAS/IntrNet software can still use the power of SAS to create content for their Internet and intranet web applications. However, it will not be as dynamic as when using SAS/IntrNet. That is; when SAS/IntrNet is executed, any web pages that are created exist for a br ...
files - prace
... Parallel I/O How to convert internal structures and domains to files which are a streams of bytes? How to get the data efficiently from hundreds to thousands of nodes on the supercomputer to physical ...
... Parallel I/O How to convert internal structures and domains to files which are a streams of bytes? How to get the data efficiently from hundreds to thousands of nodes on the supercomputer to physical ...
Backup types and strategies
... operation. The archive bit is turned off (cleared) after some backup operations. This indicates to future backup operations that the file has been backed up. As soon as the file is modified or any new files are created the archive bit is turned on. This indicates to future backup operations that the ...
... operation. The archive bit is turned off (cleared) after some backup operations. This indicates to future backup operations that the file has been backed up. As soon as the file is modified or any new files are created the archive bit is turned on. This indicates to future backup operations that the ...
BizPro Consulting Services
... (i.e., IBM’s IMS) Relational (i.e., MS Access, MS SQL Server, IBM DB2) QuickBooks has been relational since 2007 File = Table, Record = Row, Field = Column ...
... (i.e., IBM’s IMS) Relational (i.e., MS Access, MS SQL Server, IBM DB2) QuickBooks has been relational since 2007 File = Table, Record = Row, Field = Column ...
Quick Start Guide
... 3. Do not perform any disk/volume operations while running other software that has low-level disk access. Acronis Disk Director must obtain exclusive access to the target disk/volume. This means no other disk management utilities (such as the Windows Disk Management utility) can access it at that ti ...
... 3. Do not perform any disk/volume operations while running other software that has low-level disk access. Acronis Disk Director must obtain exclusive access to the target disk/volume. This means no other disk management utilities (such as the Windows Disk Management utility) can access it at that ti ...
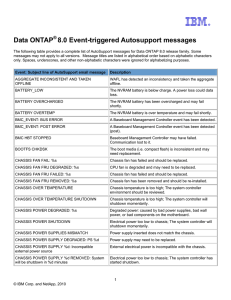
Data ONTAP® 8.0 Event-triggered Autosupport messages
... The following table provides a complete list of AutoSupport messages for Data ONTAP 8.0 release family. Some messages may not apply to all versions. Message titles are listed in alphabetical order based on alphabetic characters only. Spaces, underscores, and other non-alphabetic characters were igno ...
... The following table provides a complete list of AutoSupport messages for Data ONTAP 8.0 release family. Some messages may not apply to all versions. Message titles are listed in alphabetical order based on alphabetic characters only. Spaces, underscores, and other non-alphabetic characters were igno ...
for COBOL
... can still take advantage of these indexes to retrieve records, while not using them for sorting. This is an architectural limitation, however, in practice does not have significant impact as the SQL engine is able to build temporary index files on the fly when necessary and use dynamic index techniq ...
... can still take advantage of these indexes to retrieve records, while not using them for sorting. This is an architectural limitation, however, in practice does not have significant impact as the SQL engine is able to build temporary index files on the fly when necessary and use dynamic index techniq ...
5th unit OS Notes
... also use some advanced techniques in I/O programming to make file processing more efficient. Two such techniques are buffering and blocking of records. Buffering of Records The access method reads records of an input file ahead of the time when they are needed by a process and holds them temporarily ...
... also use some advanced techniques in I/O programming to make file processing more efficient. Two such techniques are buffering and blocking of records. Buffering of Records The access method reads records of an input file ahead of the time when they are needed by a process and holds them temporarily ...
Acronis Disk Director Suite
... password is required every time the computer is booted) to each boot configuration. You can also set a special administration password (this one is required to start Setup or Disk Administrator). Of course, this protection is not absolute, and it is better to use it along with other protection means ...
... password is required every time the computer is booted) to each boot configuration. You can also set a special administration password (this one is required to start Setup or Disk Administrator). Of course, this protection is not absolute, and it is better to use it along with other protection means ...
PowerPoint **
... • The exchange of data blocks between the host system and storage is governed by the SCSI protocol. • The SCSI protocol is implemented in a client/server model. • The SCSI protocol is responsible for block exchange but does not define how data blocks will be placed on disk. • Multiple instances of S ...
... • The exchange of data blocks between the host system and storage is governed by the SCSI protocol. • The SCSI protocol is implemented in a client/server model. • The SCSI protocol is responsible for block exchange but does not define how data blocks will be placed on disk. • Multiple instances of S ...
sosftp - SOS
... A jump host is located in the DMZ, therefore it can access servers at customer sites via the internet. Local servers quite often are excluded from internet access for security concerns. Jump hosts are used in order to store files temporarily and to forward them to the final destination which is ...
... A jump host is located in the DMZ, therefore it can access servers at customer sites via the internet. Local servers quite often are excluded from internet access for security concerns. Jump hosts are used in order to store files temporarily and to forward them to the final destination which is ...
Chapter 7 File system data structures
... larger caches and faster disks use more efficient in-memory data structures. The disk structure, however, with its inodes and direct blocks and indirect blocks, has been remarkably persistent. BSD’s UFS/FFS and Linux’s ext2/ext3 use essentially the same data structures. The most inefficient part of ...
... larger caches and faster disks use more efficient in-memory data structures. The disk structure, however, with its inodes and direct blocks and indirect blocks, has been remarkably persistent. BSD’s UFS/FFS and Linux’s ext2/ext3 use essentially the same data structures. The most inefficient part of ...
Chapter 7 File system data structures
... Xv6’s file system implementation assumes that disk operations are far more expensive than computation. It uses an efficient tree structure on disk but comparatively inefficient linear scans in the inode and buffer cache. The caches are small enough and disk accesses expensive enough to justify this ...
... Xv6’s file system implementation assumes that disk operations are far more expensive than computation. It uses an efficient tree structure on disk but comparatively inefficient linear scans in the inode and buffer cache. The caches are small enough and disk accesses expensive enough to justify this ...
DANS: Preferred formats
... considered to be very large because such languages are not expected to become obsolete. dBase, HDF5 and Microsoft Access are alternative database formats that can be considered acceptable, although it is better to convert them to more sustainable formats. The dBase Table File Format (.dbf) is a prop ...
... considered to be very large because such languages are not expected to become obsolete. dBase, HDF5 and Microsoft Access are alternative database formats that can be considered acceptable, although it is better to convert them to more sustainable formats. The dBase Table File Format (.dbf) is a prop ...
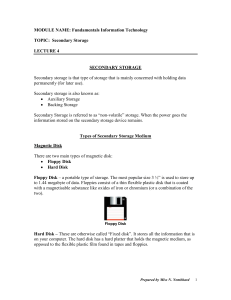
Types of Secondary Storage Medium
... Track - The path on a tape, disk or drum on which data are stored. On a disk these paths are concentric circles; on a tape there are several tracks parallel to the edge of the tape; on a drum there are bands of equal size along the circumference of the drum. A track is a ring on a disk where data ca ...
... Track - The path on a tape, disk or drum on which data are stored. On a disk these paths are concentric circles; on a tape there are several tracks parallel to the edge of the tape; on a drum there are bands of equal size along the circumference of the drum. A track is a ring on a disk where data ca ...
Elixir Repertoire Runtime
... process, the amount of report that can renders concurrently is dependent on the system resources. The report rendering threads and number in queue is in turned controlled by the licensing. It will not exceed this amount. The default runtime license sets the number of threads to one. Please contact E ...
... process, the amount of report that can renders concurrently is dependent on the system resources. The report rendering threads and number in queue is in turned controlled by the licensing. It will not exceed this amount. The default runtime license sets the number of threads to one. Please contact E ...
Defeating Encrypted and Deniable File Systems
... a convenient way to access files and folders. Shortcuts can be created in multiple ways, including by users and by programs. Perhaps surprisingly, Windows automatically creates shortcuts to files as they are used, and in Vista these shortcuts are stored in a folder called Recent Items that is locate ...
... a convenient way to access files and folders. Shortcuts can be created in multiple ways, including by users and by programs. Perhaps surprisingly, Windows automatically creates shortcuts to files as they are used, and in Vista these shortcuts are stored in a folder called Recent Items that is locate ...
Defeating Encrypted and Deniable File Systems
... Shortcuts can be created in multiple ways, including by users and by programs. Perhaps surprisingly, Windows automatically creates shortcuts to files as they are used, and in Vista these shortcuts are stored in a folder called Recent Items that is located in C:\User\UserName\AppData\Roaming\ Microso ...
... Shortcuts can be created in multiple ways, including by users and by programs. Perhaps surprisingly, Windows automatically creates shortcuts to files as they are used, and in Vista these shortcuts are stored in a folder called Recent Items that is located in C:\User\UserName\AppData\Roaming\ Microso ...
Fundamentals of Database Systems
... the disk surface and cannot be changed. One type of sector organization calls a portion of a track that subtends a fixed angle at the center as a sector. A track is divided into blocks. The block size B is fixed for each system. Typical block sizes range from B=512 bytes to B=4096 bytes. Whole blo ...
... the disk surface and cannot be changed. One type of sector organization calls a portion of a track that subtends a fixed angle at the center as a sector. A track is divided into blocks. The block size B is fixed for each system. Typical block sizes range from B=512 bytes to B=4096 bytes. Whole blo ...
disk scheduling - Orgfree.com
... that the disk sector may be bad. The ECC is an error-correcting code because it contains enough information that if only 1 or 2 bits of data have been corrupted, the controller can identify which bits have changed, and can calculate what their correct values should be. The ECC processing is done aut ...
... that the disk sector may be bad. The ECC is an error-correcting code because it contains enough information that if only 1 or 2 bits of data have been corrupted, the controller can identify which bits have changed, and can calculate what their correct values should be. The ECC processing is done aut ...
Secondary Storage - Information Technology
... Although both floppies and hard disk use random access or direct access (this moves to any point on the disk surface almost instantly), the platter in the hard disk rotates approximately twenty times faster than that of a floppy disk. As a result the hard disk is considered on of the fastest seconda ...
... Although both floppies and hard disk use random access or direct access (this moves to any point on the disk surface almost instantly), the platter in the hard disk rotates approximately twenty times faster than that of a floppy disk. As a result the hard disk is considered on of the fastest seconda ...
Chapter 11: I/O Management and Disk Scheduling
... to a wide variety of devices and applications ...
... to a wide variety of devices and applications ...
Chapter 11 I/O Management and Disk Scheduling Scheduling
... to a wide variety of devices and applications ...
... to a wide variety of devices and applications ...