Before You Begin: Assign Information Classification
... At a minimum, worms consume bandwidth in a network. A Trojan horse is technically a worm and is named for its method of getting past computer defenses by pretending to be something useful. Anti-virus software is designed to detect, disable, and remove viruses, worms, and Trojan horses before the ...
... At a minimum, worms consume bandwidth in a network. A Trojan horse is technically a worm and is named for its method of getting past computer defenses by pretending to be something useful. Anti-virus software is designed to detect, disable, and remove viruses, worms, and Trojan horses before the ...
ppt
... Jennings argues that... (3/3) • ”the agent-oriented philosophy for dealing with organisational relationships is appropriate for complex systems” Agent-based systems flexibly form and reshape structures Individual agents or groups can be developed separately and incrementally added to the system ...
... Jennings argues that... (3/3) • ”the agent-oriented philosophy for dealing with organisational relationships is appropriate for complex systems” Agent-based systems flexibly form and reshape structures Individual agents or groups can be developed separately and incrementally added to the system ...
Slides.
... • Fortunate side-benefit: scientific methodology sets us apart from standard approach towards algorithm development / optimization in CS & OR. And, we believe this methodology will be very fruitful over the next decade(s). ...
... • Fortunate side-benefit: scientific methodology sets us apart from standard approach towards algorithm development / optimization in CS & OR. And, we believe this methodology will be very fruitful over the next decade(s). ...
Slides - Department of Computer Science
... standard approach towards algorithm development / optimization in CS & OR. And, we believe this methodology will be very fruitful over the next decade(s). ...
... standard approach towards algorithm development / optimization in CS & OR. And, we believe this methodology will be very fruitful over the next decade(s). ...
Document
... Uses appropriate, relevant, and compelling content to illustrate mastery of the subject, conveying the writer's understanding, and shaping the whole work. ...
... Uses appropriate, relevant, and compelling content to illustrate mastery of the subject, conveying the writer's understanding, and shaping the whole work. ...
Introduction
... Highly variable data with same classification. Good feature selection is very important. Speech recognition is often broken into a number of smaller tasks like this. ...
... Highly variable data with same classification. Good feature selection is very important. Speech recognition is often broken into a number of smaller tasks like this. ...
Chapter 1
... The answers to these fill-in-the-blank questions can be found in the list of key terms. 1. According to Aronson, it is generally true that an experiment with __________ realism has more value to science than a study with __________ realism. 2. Near the end of Chapter 1, you learned how Skinner produ ...
... The answers to these fill-in-the-blank questions can be found in the list of key terms. 1. According to Aronson, it is generally true that an experiment with __________ realism has more value to science than a study with __________ realism. 2. Near the end of Chapter 1, you learned how Skinner produ ...
Control-Based Load Shedding in Data Stream - CSE
... queries. These systems are generally built following a query-passive data-active model, in which all data are pushed to the database server for processing and query results are sent to the users continuously. Data processing delay is critical in DSMSs since query results generated from old data are ...
... queries. These systems are generally built following a query-passive data-active model, in which all data are pushed to the database server for processing and query results are sent to the users continuously. Data processing delay is critical in DSMSs since query results generated from old data are ...
Chapter 2 Study Guide Answers (1)
... 12. What is mathematical model? One or more equations that represents the way a system or process works. ...
... 12. What is mathematical model? One or more equations that represents the way a system or process works. ...
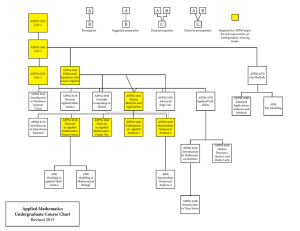
Theoretical computer science

Theoretical computer science is a division or subset of general computer science and mathematics that focuses on more abstract or mathematical aspects of computing and includes the theory of computation.It is not easy to circumscribe the theory areas precisely and the ACM's Special Interest Group on Algorithms and Computation Theory (SIGACT) describes its mission as the promotion of theoretical computer science and notes:Template:""To this list, the ACM's journal Transactions on Computation Theory adds coding theory, computational learning theory and theoretical computer science aspects of areas such as databases, information retrieval, economic models and networks. Despite this broad scope, the ""theory people"" in computer science self-identify as different from the ""applied people."" Some characterize themselves as doing the ""(more fundamental) 'science(s)' underlying the field of computing."" Other ""theory-applied people"" suggest that it is impossible to separate theory and application. This means that the so-called ""theory people"" regularly use experimental science(s) done in less-theoretical areas such as software system research. It also means that there is more cooperation than mutually exclusive competition between theory and application.