Printable
... ◦ We only need to store the currently-searched branch. ◦ This is DFS’ strong point. ◦ In our previous figure, searching to depth 12 would require ...
... ◦ We only need to store the currently-searched branch. ◦ This is DFS’ strong point. ◦ In our previous figure, searching to depth 12 would require ...
Algorithms Lecture 5 Name:___________________________
... Θ(nlog n) “advanced” sorting algorithms: Merge sort and Quick Sort. Consider why a divide-and-conquer sort might be more efficient. Assume that I had a simple Θ(n2) sorting algorithm with n = 100, then there is roughly 1002 / 2 or 5,000 amount of work. Suppose I split the problem down into two small ...
... Θ(nlog n) “advanced” sorting algorithms: Merge sort and Quick Sort. Consider why a divide-and-conquer sort might be more efficient. Assume that I had a simple Θ(n2) sorting algorithm with n = 100, then there is roughly 1002 / 2 or 5,000 amount of work. Suppose I split the problem down into two small ...
Designing and Building an Analytics Library with the Convergence
... which is in principle understood but we find that significant new work is needed compared to basic HPC releases which tend to address point to point communication. • The model size EV-M4 and data volume EV-D4 are important in describing the algorithm performance as just like in simulation problems, ...
... which is in principle understood but we find that significant new work is needed compared to basic HPC releases which tend to address point to point communication. • The model size EV-M4 and data volume EV-D4 are important in describing the algorithm performance as just like in simulation problems, ...
A Data Stream Management System for Network Traffic Management
... • What’s wrong with using a Database Management System (DBMS)? – DBMS expects all data to be managed as persistent data sets – DBMS assumes “one-time” queries against stored and finite data ...
... • What’s wrong with using a Database Management System (DBMS)? – DBMS expects all data to be managed as persistent data sets – DBMS assumes “one-time” queries against stored and finite data ...
Introduction to Computer Concepts
... become blurred. Often the distinction depends upon how the manufacturer wants to market its machines. Organisations may use a mini-computer for such tasks as managing the information in a small financial system or maintaining a small database of information about registrations or applications. Works ...
... become blurred. Often the distinction depends upon how the manufacturer wants to market its machines. Organisations may use a mini-computer for such tasks as managing the information in a small financial system or maintaining a small database of information about registrations or applications. Works ...
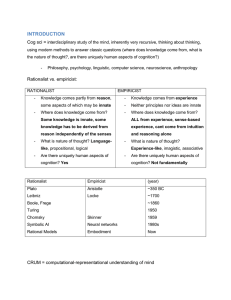
Rationality
... – You want to minimize travelling cost. – Customers have different time availability. In what order should you ...
... – You want to minimize travelling cost. – Customers have different time availability. In what order should you ...
Jan Kriz
... - Level spacing distribution: very good agreement with the RMT predictions => universal behaviour - Number variance: sensitive when the subject is visually stimulated - It is reasonable to assume that also some pathological processes can influence the number variance ...
... - Level spacing distribution: very good agreement with the RMT predictions => universal behaviour - Number variance: sensitive when the subject is visually stimulated - It is reasonable to assume that also some pathological processes can influence the number variance ...
ICDL Module 1 Concepts Information Technology
... the European Computer Driving Licence Foundation Limited in Ireland and other countries. Neither the European Computer Driving Licence Foundation nor the ICDL Foundation warrants that the use of this product will ensure passing the relevant examination. Use of the ECDL-F approved Courseware Logo on ...
... the European Computer Driving Licence Foundation Limited in Ireland and other countries. Neither the European Computer Driving Licence Foundation nor the ICDL Foundation warrants that the use of this product will ensure passing the relevant examination. Use of the ECDL-F approved Courseware Logo on ...
Slides
... • What are the fundamental factors that influence the formation of co-invention relationships? • How to design an interactive mechanism so that the user can provide feedback to the system to refine the recommendations? ...
... • What are the fundamental factors that influence the formation of co-invention relationships? • How to design an interactive mechanism so that the user can provide feedback to the system to refine the recommendations? ...
Near - Consumer Applications - Field Data Collection Checklist
... Before completing this form please check if the intended use is already listed on the gas supplier’s list of nonsupported/prohibited uses or whether it has already been assessed and (a minimum set of)risk management measures (RMM’s) already defined. In the case that RMM’s are already defined, comple ...
... Before completing this form please check if the intended use is already listed on the gas supplier’s list of nonsupported/prohibited uses or whether it has already been assessed and (a minimum set of)risk management measures (RMM’s) already defined. In the case that RMM’s are already defined, comple ...
Large-N Quantum Field Theories and Nonlinear Random Processes
... • Better approximation for real QCD than pure large-N gauge theory: meson decays, deconfinement phase etc. ...
... • Better approximation for real QCD than pure large-N gauge theory: meson decays, deconfinement phase etc. ...
Computational Prototyping Tools and Techniques—J.K. White, L. Daniel, A. Megretski, J. Peraire, B. Tidor, K. Willcox
... combination of top-down or bottom-up decomposition strategies. In a top-down approach, designers decompose their systems into easily understood blocks with well-defined interfaces, and in a bottom-up approach, designers develop a complicated system by combining existing blocks. For designers of syst ...
... combination of top-down or bottom-up decomposition strategies. In a top-down approach, designers decompose their systems into easily understood blocks with well-defined interfaces, and in a bottom-up approach, designers develop a complicated system by combining existing blocks. For designers of syst ...
Week 8 - School of Engineering and Information Technology
... Principles of learning for game design • In practice games developers generally allow factual knowledge acquired during the game to be queried by a process that’s fixed at design-time e.g. with a problem-solving RBS, the rules are learned but the reasoning process is programmed in • Behaviours, on ...
... Principles of learning for game design • In practice games developers generally allow factual knowledge acquired during the game to be queried by a process that’s fixed at design-time e.g. with a problem-solving RBS, the rules are learned but the reasoning process is programmed in • Behaviours, on ...
Theoretical computer science

Theoretical computer science is a division or subset of general computer science and mathematics that focuses on more abstract or mathematical aspects of computing and includes the theory of computation.It is not easy to circumscribe the theory areas precisely and the ACM's Special Interest Group on Algorithms and Computation Theory (SIGACT) describes its mission as the promotion of theoretical computer science and notes:Template:""To this list, the ACM's journal Transactions on Computation Theory adds coding theory, computational learning theory and theoretical computer science aspects of areas such as databases, information retrieval, economic models and networks. Despite this broad scope, the ""theory people"" in computer science self-identify as different from the ""applied people."" Some characterize themselves as doing the ""(more fundamental) 'science(s)' underlying the field of computing."" Other ""theory-applied people"" suggest that it is impossible to separate theory and application. This means that the so-called ""theory people"" regularly use experimental science(s) done in less-theoretical areas such as software system research. It also means that there is more cooperation than mutually exclusive competition between theory and application.