Click here to access the presentation.
... Data growth occurring at exponential rate Ability to manipulate data sets that exceed ...
... Data growth occurring at exponential rate Ability to manipulate data sets that exceed ...
Overview of Knowledge Discovery in Databases Process and Data
... define knowledge discovery in databases (KDD) process in five steps: Data preparation, data preprocessing, DM, evaluation and interpretation, and implementation. DM is further explained in descriptive and predictive mining categories with their functions and methods used or likely to be used in EWSs ...
... define knowledge discovery in databases (KDD) process in five steps: Data preparation, data preprocessing, DM, evaluation and interpretation, and implementation. DM is further explained in descriptive and predictive mining categories with their functions and methods used or likely to be used in EWSs ...
(Big) Data? - Cloud Security Alliance
... What is Big Data? (Wikipedia) Big data Data sets so large or complex that traditional data processing applications/infrastructure are inadequate. Challenges include analysis, capture, curation, search, sharing, storage, transfer, visualization, and information privacy. The term often refe ...
... What is Big Data? (Wikipedia) Big data Data sets so large or complex that traditional data processing applications/infrastructure are inadequate. Challenges include analysis, capture, curation, search, sharing, storage, transfer, visualization, and information privacy. The term often refe ...
documentstyle[12pt]{article} - Global Knowledge Management
... Students – Wanshiou Yang, National Sun Yat Sen University, Taiwan Charlie Chi, UA- Computer Science ...
... Students – Wanshiou Yang, National Sun Yat Sen University, Taiwan Charlie Chi, UA- Computer Science ...
Chapter 2: Introduction to Microprocessor
... It is composed of collection of files that are linked in such a way that information from one of the files may be combined with information from other files so that a user may receive the exact required information. ...
... It is composed of collection of files that are linked in such a way that information from one of the files may be combined with information from other files so that a user may receive the exact required information. ...
Database Administrator
... Responsible for definition of standards of data dictionaries. May program dictionary analysis and maintenance software. Perform performance tuning. Monitor database performance and space requirements. Schedule and monitor end of day data warehousing jobs. Assist in coordinating software ...
... Responsible for definition of standards of data dictionaries. May program dictionary analysis and maintenance software. Perform performance tuning. Monitor database performance and space requirements. Schedule and monitor end of day data warehousing jobs. Assist in coordinating software ...
Data Confidentiality
... consist of data about each stage of any transaction, logs are maintained automatically by the system allow the network manager to examine patterns of use audit logs track: – who did what, – at which workstation, – when it occurred. ...
... consist of data about each stage of any transaction, logs are maintained automatically by the system allow the network manager to examine patterns of use audit logs track: – who did what, – at which workstation, – when it occurred. ...
POST MASTER DEGREE IN SECURITY IN COMPUTER SYSTEMS
... Frequencies basics, hands on electronics skills. Notes: - a lot of help will be provided to students motivated to learn and build stuff. All required hardware will be purchased/lent. - this project has potential for being published/open sourced ...
... Frequencies basics, hands on electronics skills. Notes: - a lot of help will be provided to students motivated to learn and build stuff. All required hardware will be purchased/lent. - this project has potential for being published/open sourced ...
Seminar Announcement - CS/NVC Home
... technical challenges in dealing with such queries. We will then focus on similarity-based queries on streaming time series. These queries are to flag, on the incoming streaming time series, the appearance of some given patterns. We consider two scenarios. The first is when the number of given patter ...
... technical challenges in dealing with such queries. We will then focus on similarity-based queries on streaming time series. These queries are to flag, on the incoming streaming time series, the appearance of some given patterns. We consider two scenarios. The first is when the number of given patter ...
Distributed Data Dissemination Server
... access from heterogeneous clients Supports Historic & Real-Time Queries Attribute based data discovery Multi-Server capability Client-side libraries available in C, C++, and Java ...
... access from heterogeneous clients Supports Historic & Real-Time Queries Attribute based data discovery Multi-Server capability Client-side libraries available in C, C++, and Java ...
Data management *NEW* M816 Presentation pattern
... Data are often an organisation’s most valuable asset but data require careful management to ensure the maximum benefit is achieved by the organisation. This module covers the data management principles, practices and technologies required to develop policies, procedures and systems that control, pro ...
... Data are often an organisation’s most valuable asset but data require careful management to ensure the maximum benefit is achieved by the organisation. This module covers the data management principles, practices and technologies required to develop policies, procedures and systems that control, pro ...
Computer Components
... Read only memory (ROM) – is a chip on the motherboard that has been prerecorded with data that gives instructions (BIOS or basic input/output system) used to check the computer system’s components to make sure they are working and to activate the essential software that controls the processing funct ...
... Read only memory (ROM) – is a chip on the motherboard that has been prerecorded with data that gives instructions (BIOS or basic input/output system) used to check the computer system’s components to make sure they are working and to activate the essential software that controls the processing funct ...
DataXtend RE (DXRE) enables enterprises to distribute data
... DataXtend RE uses a “net change” model, so only the data that has been updated since the last replication is sent through the network. Additionally, DataXtend RE technology allows you to partition data so that only the information pertinent to that site is sent through the network. ...
... DataXtend RE uses a “net change” model, so only the data that has been updated since the last replication is sent through the network. Additionally, DataXtend RE technology allows you to partition data so that only the information pertinent to that site is sent through the network. ...
QlikView Integration Overview
... • Extensive management API’s exist to allow automation of tasks on a larger scale, or to allow integration with existing centralized application management software • Example: integrating an HR system for employee on-boarding with the QlikView admin tasks to allocate QlikView licenses ...
... • Extensive management API’s exist to allow automation of tasks on a larger scale, or to allow integration with existing centralized application management software • Example: integrating an HR system for employee on-boarding with the QlikView admin tasks to allocate QlikView licenses ...
Endpoint Security Device Control (formerly Sanctuary)
... leakage routes – no file copy limits, no encryption, no audit trails and no central management. The information contained in customer and corporate data, such as personally identifiable information (PII) and intellectual property (IP), is worth billions to some. And the costs for recovery of data an ...
... leakage routes – no file copy limits, no encryption, no audit trails and no central management. The information contained in customer and corporate data, such as personally identifiable information (PII) and intellectual property (IP), is worth billions to some. And the costs for recovery of data an ...
Introduction to Predictive Data Analytics
... Predictive Data Analytics encompasses the business and data processes and computational models that enable a business to make data-driven decisions. ...
... Predictive Data Analytics encompasses the business and data processes and computational models that enable a business to make data-driven decisions. ...
IIDPS: An Internal Intrusion Detection and
... Over the past several years, the Internet environment has become more complex and untrusted. Enterprise networked systems are inevitably exposed to the increasing threats posed by hackers as well as malicious users internal to a network. IDS technology is one of the important tools used now-a-days, ...
... Over the past several years, the Internet environment has become more complex and untrusted. Enterprise networked systems are inevitably exposed to the increasing threats posed by hackers as well as malicious users internal to a network. IDS technology is one of the important tools used now-a-days, ...
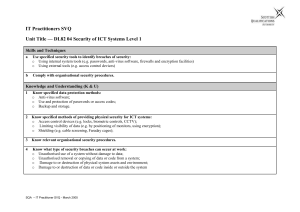
it user svq – level 2
... Know what type of security breaches can occur at work: o Unauthorised use of a system without damage to data; o Unauthorised removal or copying of data or code from a system; o Damage to or destruction of physical system assets and environment; o Damage to or destruction of data or code inside or ou ...
... Know what type of security breaches can occur at work: o Unauthorised use of a system without damage to data; o Unauthorised removal or copying of data or code from a system; o Damage to or destruction of physical system assets and environment; o Damage to or destruction of data or code inside or ou ...
12_hSecurityRequirements
... What You Should Know About Security Requirements Computer and Network Security Requirements It is required by law (The Data Protection Act) that all data held about individuals must be protected from unauthorised access. Confidentiality - All network data must be kept confidential. This can be for c ...
... What You Should Know About Security Requirements Computer and Network Security Requirements It is required by law (The Data Protection Act) that all data held about individuals must be protected from unauthorised access. Confidentiality - All network data must be kept confidential. This can be for c ...
Overview
... management on the card itself rather than on an external device is the only way to achieve very high security, high availability (anywhere, anytime, on any terminal) and acceptable performance. However, smartcards have severe hardware limitations which stem from the obvious constraints of small size ...
... management on the card itself rather than on an external device is the only way to achieve very high security, high availability (anywhere, anytime, on any terminal) and acceptable performance. However, smartcards have severe hardware limitations which stem from the obvious constraints of small size ...
Privacy-Preserving Utility Verification of the Data
... publisher is responsible for aggregating sensitive data from multiple parties and then anonymizing it before publishing for data mining. In such scenarios, the data users may have a strong demand to measure the utility of the published data since most anonymization techniques have side effects on da ...
... publisher is responsible for aggregating sensitive data from multiple parties and then anonymizing it before publishing for data mining. In such scenarios, the data users may have a strong demand to measure the utility of the published data since most anonymization techniques have side effects on da ...
Real Systems - e
... terrorism and criminal activities, data recovery, cyber defense and information DATA VIZUALIZATION: VizKey™ - visual database and analysis environment. The Suite includes database, visualization, analysis methods, visual engines and external data connectivity. Ideal tool for law enforcement institut ...
... terrorism and criminal activities, data recovery, cyber defense and information DATA VIZUALIZATION: VizKey™ - visual database and analysis environment. The Suite includes database, visualization, analysis methods, visual engines and external data connectivity. Ideal tool for law enforcement institut ...
Word
... - What is ________________________ and where it is stored - Virtual memory - OS will send message when RAM is full Provides the interface for storage devices and _____________________________________ on those devices - in charge of formatting disks - creates sectors and clusters - creates F.A.T. or ...
... - What is ________________________ and where it is stored - Virtual memory - OS will send message when RAM is full Provides the interface for storage devices and _____________________________________ on those devices - in charge of formatting disks - creates sectors and clusters - creates F.A.T. or ...




![documentstyle[12pt]{article} - Global Knowledge Management](http://s1.studyres.com/store/data/002138920_1-bd878a9ad97119a4308a7c0b9304567f-300x300.png)